华为防火墙实验基础篇-1
拓扑图
实验需求
0)部署接口与安全区域
- 连接PC1,web-manager的接口位于trust区域
- Server1位于DMZ区域,连接AR1的接口部署为untrust区域
- 防火墙所有地址为.12
1)防火墙远程登录
- 部署SSH登录,实现通过公网能够登录防火墙
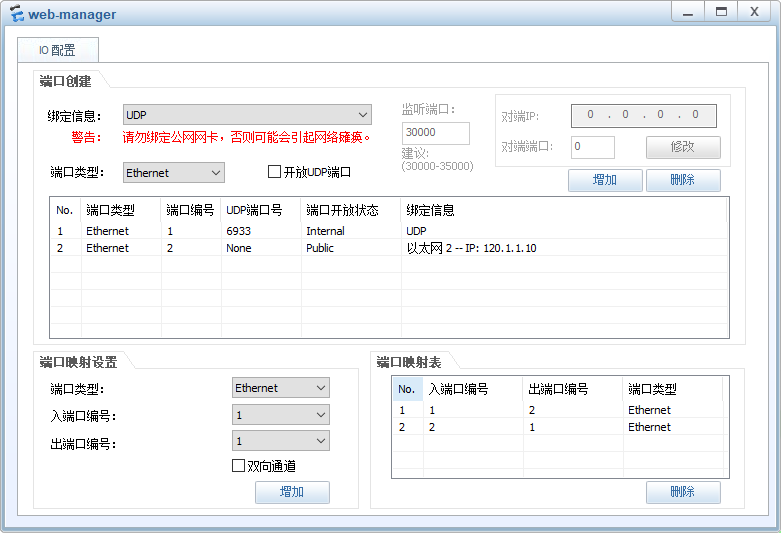
- 部署防火墙实现通过本机web方式登录防火墙
2)防火墙网络服务
- 配置FW-1作为DHCP服务器,对PC1分配地址
- 其中PC1的MAC地址为AABB-CC00-0001,总是获取10.1.12.10/24,DNS为150.1.1.10
- 配置FW-1作为PPPoE客户端,AR1作为PPPoE服务端
3)防火墙安全策略与ASPF
- 保障防火墙发起的任何连接都不受限
- 调整安全策略实现
- 除PC1以外,其他10.1.12.0/24网段内主机只能通过HTTP或FTP访问DMZ主机
- 采用地址组与服务组的方式实现
- 全局关闭ASPF,在特定区域激活ASPF
4)防火墙地址转换
- FW-1添加NAT地址池(155.1.121.11-155.1.121.20)
- 部署NAPT实现
- 内网10.1.12.0/24能够访问互联网
- 部署NAT-Server实现,公网用户Client1访问DMZ的服务器的FTP与HTTP服务
- 其中映射地址为155.1.121.10
- 对于内网主机能够通过155.1.121.10,访问DMZ服务器
- 安全策略精确到端口级
5)防火墙本地portal认证
- 对于PC1访问公网不受限
- 对于win主机访问互联网,需要通过本地Portal认证
- 登录账户(USER/huawei@123)
配置
0)部署接口与安全区域
- 连接PC1,web-manager的接口位于trust区域
- Server1位于DMZ区域,连接AR1的接口部署为untrust区域
- 防火墙所有地址为.12
FW的G1/0/0接口绑定dialer,目前无需配置地址
sysname FW1 # interface GigabitEthernet0/0/0 ip address 120.1.1.12 255.255.255.0 service-manage https permit service-manage ping permit # interface GigabitEthernet1/0/1 undo shutdown ip address 10.1.12.12 255.255.255.0 # interface GigabitEthernet1/0/2 undo shutdown ip address 10.0.0.12 255.255.255.0 # firewall zone trust set priority 85 add interface GigabitEthernet0/0/0 add interface GigabitEthernet1/0/1 # firewall zone dmz set priority 50 add interface GigabitEthernet1/0/2 #
1)防火墙远程登录
- 部署SSH登录,实现通过公网能够登录防火墙
- 部署防火墙实现通过本机web方式登录防火墙
注意:防火墙默认加密安全级别高较高,需要调整为aes128_cbc,不然无法成功ssh
web登录方式可修改默认端口号
由于拨号接口未配置,目前无法测试ssh
web-manager security version tlsv1 tlsv1.1 tlsv1.2 # 修改端口 web-manager security enable port 10443 # 修改超时时间 web-manager timeout 1440 #关闭配置向导 undo web-manager config-guide enable # # 创建用户 aaa manager-user USER password cipher huawei@123 service-type web ssh level 15 bind manager-user USER role system-admin # stelnet server enable ssh user USER ssh user USER authentication-type password ssh user USER service-type stelnet # 修改加密算法 ssh server cipher aes128_cbc # user-interface vty 0 4 authentication-mode aaa protocol inbound ssh # rsa local-key-pair create
桥接配置:
测试
目前只能测试web登录,ssh在PPPoE配置后测试
2)防火墙网络服务
- 配置FW-1作为DHCP服务器,对PC1分配地址
- 其中PC1的MAC地址为AABB-CC00-0001,总是获取10.1.12.10/24,DNS为150.1.1.10
- 配置FW-1作为PPPoE客户端,AR1作为PPPoE服务端
sysname AR1 # aaa local-user user password cipher huawei@123 local-user user service-type ppp # interface Virtual-Template1 ppp authentication-mode chap remote address 155.1.121.12 # 为对端分配IP地址时,不允许对端使用自行配置的IP地址 ppp ipcp remote-address forced ip address 155.1.121.1 255.255.255.0 # interface GigabitEthernet0/0/0 pppoe-server bind Virtual-Template 1 # interface GigabitEthernet0/0/1 ip address 155.1.1.1 255.255.255.0 # interface GigabitEthernet0/0/2 ip address 150.1.1.1 255.255.255.0 # # 第一次连接ssh需配置 ssh client first-time enable #
# 拨号规则,可选配置 dialer-rule 1 ip permit # dhcp enable # interface Dialer1 link-protocol ppp ppp chap user USER ppp chap password cipher huawei@123 ip address ppp-negotiate dialer user TEST dialer bundle 1 # dialer-group 数字需与dialer-rule一致 dialer-group 1 service-manage ssh permit # interface GigabitEthernet1/0/0 pppoe-client dial-bundle-number 1 # interface GigabitEthernet1/0/1 undo shutdown ip address 10.1.12.12 255.255.255.0 dhcp select interface dhcp server static-bind ip-address 10.1.12.10 mac-address aabb-cc00-0001 description PC1 dhcp server dns-list 150.1.1.10 # firewall zone untrust set priority 5 add interface Dialer1 # ip route-static 0.0.0.0 0.0.0.0 Dialer1 #
修改PC1的MAC地址
PC1获取到绑定的地址
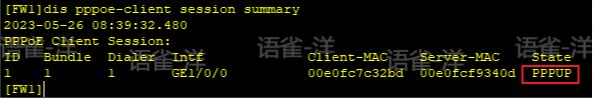
FW1查看PPPoE状态
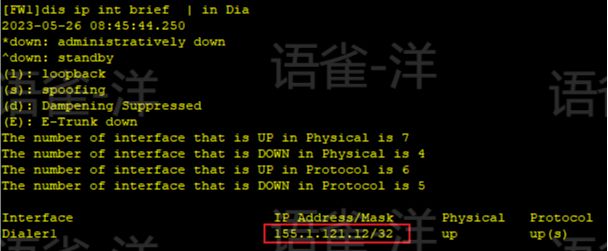
查看Dialer接口的IP地址
测试ssh,可以正常登录
3)防火墙安全策略与ASPF
- 保障防火墙发起的任何连接都不受限
-
- 调整安全策略实现
- 除PC1以外,其他10.1.12.0/24网段内主机只能通过HTTP或FTP访问DMZ主机
-
- 采用地址组与服务组的方式实现
- 全局关闭ASPF,在特定区域激活ASPF
-
- FTP为双通道协议,需开启ASPF
# 配置地址组和服务组 ip address-set PC1 type object description IP_10.1.12.10 address 0 10.1.12.10 mask 32 # ip address-set inside_net type group address 0 10.1.12.0 mask 24 # ip service-set http&ftp type group 0 service 0 service-set http service 1 service-set ftp # security-policy rule name local->any source-zone local action permit rule name trust->dmz source-zone trust destination-zone dmz source-address address-set inside_net source-address-exclude address-set PC1 service http&ftp action permit rule name PC1->dmz source-zone trust destination-zone dmz source-address address-set PC1 action permit # # 关闭ftp的全局ASPF undo firewall detect ftp # # 针对trust,dmz区域开启ftp的ASPF firewall interzone trust dmz detect ftp #
内网服务器配置
测试访问FTP与HTTP
4)防火墙地址转换
- FW-1添加NAT地址池(155.1.121.11-155.1.121.20)
- 部署NAPT实现
- 内网10.1.12.0/24能够访问互联网
-
- 配置安全策略
- 部署NAT-Server实现,公网用户Client1访问DMZ的服务器的FTP与HTTP服务
- 其中映射地址为155.1.121.10
-
- 注意no-reverse和unr-route两个参数的使用
-
-
- no-reverse:server-map不生成反向表项,可以使用一个映射地址做多个映射
- unr-route:下发UNR路由,防止路由环路,如果nat server的地址与出接口不在同一网段,一定要配置
-
-
- 配置安全策略
- 配置untrust与dmz区域的ASPF
- 对于内网主机能够通过155.1.121.10,访问DMZ服务器
- 安全策略精确到端口级
-
- 可以配置目的NAT,实际上由于匹配server-map表项,目的NAT可不必配置
nat server 0 protocol tcp global 155.1.121.10 www inside 10.0.0.10 www no-reverse unr-route nat server 1 protocol tcp global 155.1.121.10 ftp inside 10.0.0.10 ftp no-reverse unr-route # nat address-group nat_pool 0 mode pat section 0 155.1.121.11 155.1.121.20 # nat-policy rule name snat source-zone trust destination-zone untrust source-address address-set inside_net action source-nat address-group nat_pool # security-policy rule name trust->untrust source-zone trust destination-zone untrust source-address address-set inside_net action permit rule name untrust->dmz source-zone untrust destination-zone dmz service ftp service http action permit # firewall interzone untrust dmz detect ftp #
client1配置
公网服务器配置,配置为DNS服务器与HTTP服务器
查看server-map表项,未生成反向表项
查看防环路由
测试
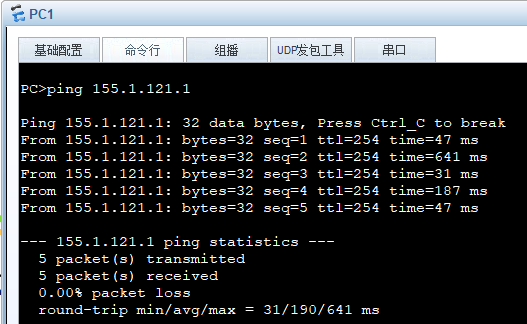
内网PC访问互联网,ping域名可解析为IP地址,内网地址转换成155.1.121.18
公网用户访问内网服务器FTP与HTTP,正常访问
内网主机通过公网地址155.1.121.10访问DMZ的服务器
5)防火墙本地portal认证
- 对于PC1访问公网不受限
- 对于win主机访问互联网,需要通过本地Portal认证
- 登录账户(USER/huawei@123)
-
- 该账号不会保存,重新打开ensp后需要配置
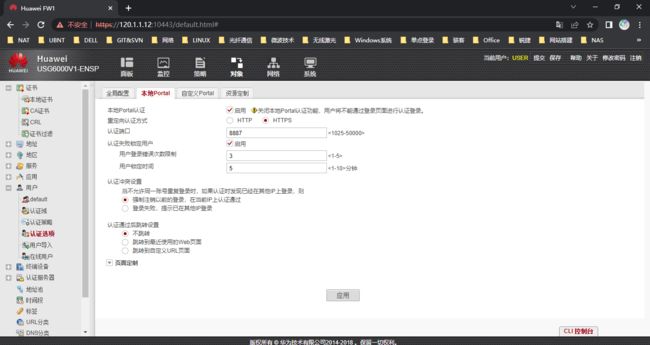
- 配置安全策略,trust->local目的端口为8887
security-policy rule name trust->local source-zone trust destination-zone local service protocol tcp destination-port 8887 action permit #
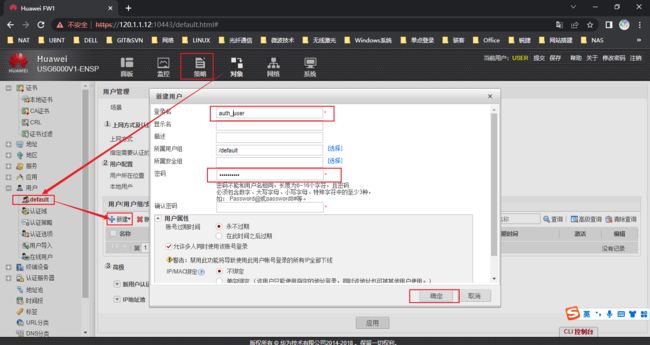
通过web页面配置
可选配置,如认证后自动跳转页面,认证页面端口号
补充:命令行配置Portal认证
aaa domain default service-type internetaccess internet-access mode password reference user current-domain # auth-policy rule name Internet_access source-zone trust destination-zone untrust source-address address-set inside_net source-address-exclude address-set PC1 action auth # user-manage user auth_user password huawei@123 parent-group /default bind mode unidirectional multi-ip online enable #
测试
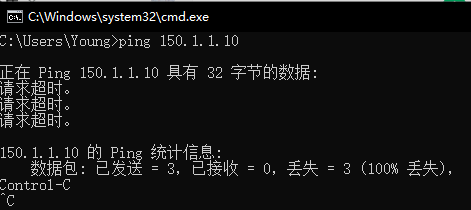
此时client2在未认证情况下,无法ping通公网服务器
PC1可以访问公网不受影响
为了测试Portal认证,使用了vmware的虚拟网卡(如果没有安装vmware,可创建环回网卡),桥接网卡配置(也可以自动获取到10.1.12.0网段的地址),使用真实的笔记本充当内网PC,系统Win10
禁用其他网卡,保证PC默认路由走桥接的网卡,查看路由命令route print -4(不禁用网卡的情况下,也可手动配置默认路由,保证跃点数最小)
未认证情况下,不可访问互联网
在浏览器中输入150.1.1.10,会跳转到认证页面,输入账号,密码登录
认证成功
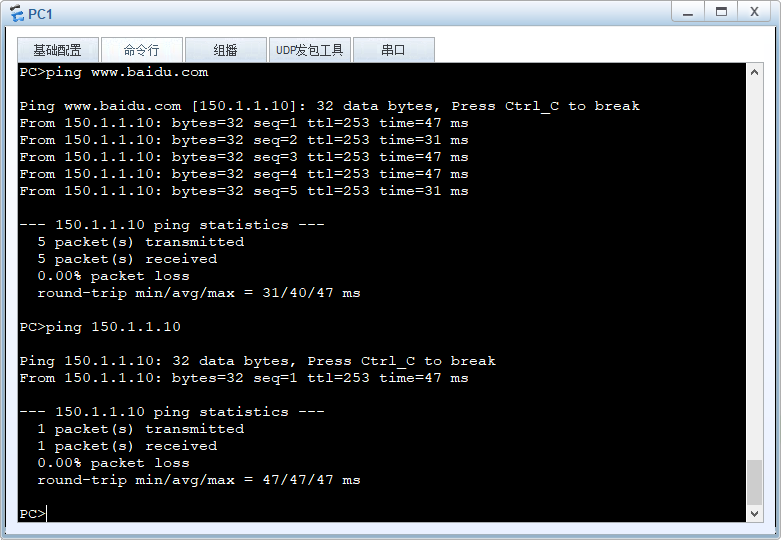
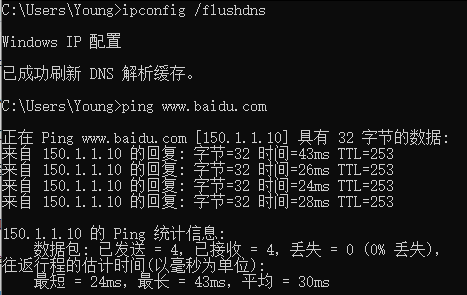
ping www.baidu.com或访问150.1.1.10,均可访问
补充细节
如果AR1上配置G0/0/0接口地址,VT接口借用G0/0/0口地址,会发现内网访问公网不通,公网client访问内网服务器155.1.121.10的FTP,HTTP也无法正常访问
interface Virtual-Template1 undo ip add # interface GigabitEthernet0/0/0 ip address 155.1.121.1 255.255.255.0 # interface Virtual-Template1 ip address unnumbered interface GigabitEthernet0/0/0 #
内网主机无法访问公网
查看防火墙会话表,地址已进行转换
原因:AR1的路由表去往155.1.121.0/24的出接口为G0/0/0,没有通过VT接口,走物理接口,数据会封装成以太网2的格式,AR1会发送ARP请求155.1.121.18的MAC,FW1收到ARP请求,由于没有配置此IP,不会应答,由于没有MAC地址,AR1无法完成封装,丢包
解决:配置静态路由155.1.121.0/27出接口VT接口
ip route-static 155.1.121.0 27 Virtual-Template 1 #
返回的数据会通过VT接口封装为PPPoE的帧,发送回防火墙,匹配会话表,PC1正常访问互联网
区别在于手动配置VT接口的IP地址,直接会生成关于155.1.121.0/24的路由出接口为VT接口