oracle数据库防火墙配置,Linux防火墙配置 – 提供7*24专业数据库(Oracle,SQL Server,MySQL等)恢复和Oracle技术服务@Tel:+86 13429648788 -...
一、Linux防火墙基础知识
1、常用命令
查看配置 iptables -L -n
修改配置 iptables -A INPUT -p tcp -s 192.168.1.12 –dport 22 -j ACCEPT
保存修改 /etc/init.d/iptables save
开启/关闭/重启/状态 /etc/init.d/iptables start/stop/restart/status
2、常用参数
–append -A chain Append to chain
–in-interface -i [!] input name[+] network interface name ([+] for wildcard)
–proto -p [!] proto protocol: by number or name, eg. `tcp’
–source -s [!] address[/mask] source specification
–destination -d [!] address[/mask] destination specification
–jump -j target target for rule (may load target extension)
–dport 目标端端口
–sport 源端端口
二、Liunx防火墙配置方法
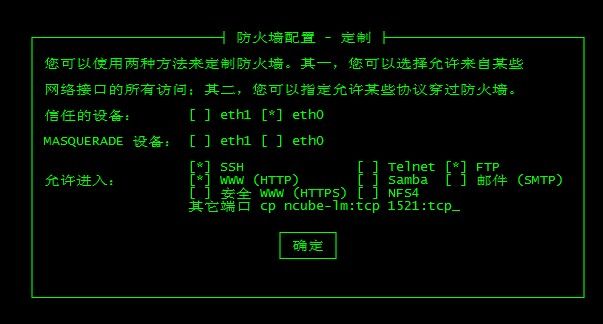
1、setup配置
注意INPUT/FORWARD/OUTPUT设置
2、vi修改/etc/sysconfig/iptables
# Firewall configuration written by system-config-securitylevel
# Manual customization of this file is not recommended.
*filter
#表示进入服务器包,一般情况下修改为DROP
:INPUT ACCEPT [0:0]
#表示转发包,根据实际情况
:FORWARD ACCEPT [0:0]
#表示从服务器发出包,一般设置为ACCEPT
:OUTPUT ACCEPT [0:0]
#不清楚该含义
:RH-Firewall-1-INPUT – [0:0]
-A INPUT -j RH-Firewall-1-INPUT
-A FORWARD -j RH-Firewall-1-INPUT
-A RH-Firewall-1-INPUT -i lo -j ACCEPT
#表示所有eth1/eth0网卡包都可以被允许
-A RH-Firewall-1-INPUT -i eth1 -j ACCEPT
-A RH-Firewall-1-INPUT -i eth0 -j ACCEPT
-A RH-Firewall-1-INPUT -p icmp –icmp-type any -j ACCEPT
-A RH-Firewall-1-INPUT -p 50 -j ACCEPT
-A RH-Firewall-1-INPUT -p 51 -j ACCEPT
-A RH-Firewall-1-INPUT -p udp –dport 5353 -d 224.0.0.251 -j ACCEPT
-A RH-Firewall-1-INPUT -p udp -m udp –dport 631 -j ACCEPT
-A RH-Firewall-1-INPUT -p tcp -m tcp –dport 631 -j ACCEPT
-A RH-Firewall-1-INPUT -m state –state ESTABLISHED,RELATED -j ACCEPT
-A RH-Firewall-1-INPUT -m state –state NEW -m tcp -p tcp –dport 1521 -j ACCEPT
-A RH-Firewall-1-INPUT -m state –state NEW -m tcp -p tcp –dport 3306 -j ACCEPT
-A RH-Firewall-1-INPUT -m state –state NEW -m tcp -p tcp –dport 22 -j ACCEPT
-A RH-Firewall-1-INPUT -m state –state NEW -m tcp -p tcp –dport 25 -j ACCEPT
-A RH-Firewall-1-INPUT -m state –state NEW -m tcp -p tcp –dport 80 -j ACCEPT
-A RH-Firewall-1-INPUT -m state –state NEW -m tcp -p tcp –dport 21 -j ACCEPT
-A RH-Firewall-1-INPUT -m state –state NEW -m tcp -p tcp –dport 443 -j ACCEPT
-A RH-Firewall-1-INPUT -j REJECT –reject-with icmp-host-prohibited
COMMIT
service iptables restart
3、iptables命令配置
#注意是否已经配置了相关策略,不然可能导致ssh不能访问
iptables -P INPUT DROP
iptables -P OUTPUT DROP
#慎重,要不你的ssh也失去链接了
iptables -P FORWARD DROP
#如果iptables -P OUTPUT DROP配置,一定需要类此这两条配合
iptables -A INPUT -p tcp –dport 22 -j ACCEPT
iptables -A OUTPUT -p tcp –sport 22 -j ACCEPT
iptables -A INPUT -p tcp -s 10.218.32.153 –dport 1521 -j ACCEPT
iptables -A OUTPUT -p tcp -d 10.218.32.153 –sport 1521 -j ACCEPT
/etc/init.d/iptables save
service iptables restart