网络安全-防御 第三次作业(图像配置和拓扑测试后续)
一、拓扑搭建
在eNSP软件中,进行如下操作搭建拓扑:
-
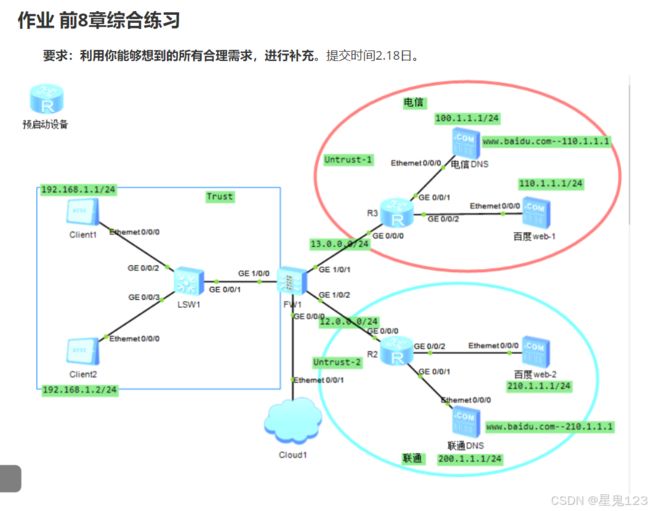
设备选取与放置:
从设备库拖出1台预启动路由器(R)放于左上角;
1台交换机(LSW1)置于中部偏左,用于连接内网客户端;
1台防火墙(FW1)在交换机右侧,作为网络安全隔离核心;
2台路由器(R2、R3),R3在右上角连接电信网络部分,R2在右中部连接联通网络部分;
6台PC,分别为Client1、Client2、电信DNS模拟机、联通DNS模拟机、百度web - 1模拟机、百度web - 2模拟机,按对应关系连接到交换机或路由器接口。
-
设备连接:
Client1的Ethernet0/0/0连交换机LSW1的Ethernet0/0/2;
Client2的Ethernet0/0/0连交换机LSW1的Ethernet0/0/3;
交换机LSW1的GE1/0/0连防火墙FW1的GE1/0/0;
防火墙FW1的GE1/0/1连路由器R3的GE0/0/0,GE1/0/2连路由器R2的GE0/0/0,GE0/0/1连Cloud1;
路由器R3的GE0/0/1连电信DNS模拟机的Ethernet0/0/0,GE0/0/2连百度web - 1模拟机的Ethernet0/0/0;
路由器R2的GE0/0/1连联通DNS模拟机的Ethernet0/0/0,GE0/0/2连百度web - 2模拟机的Ethernet0/0/0。
二、设备基础配置
(1),指令配置
- Client1:设置IP为192.168.1.1/24,网关192.168.1.254。
- Client2:设置IP为192.168.1.2/24,网关192.168.1.254。
- 交换机(LSW1):
system - view
vlan 10
interface Ethernet0/0/2
port link - type access
port default vlan 10
quit
interface Ethernet0/0/3
port link - type access
port default vlan 10
quit
interface GigabitEthernet1/0/0
port link - type trunk
port trunk allow - pass vlan 10
quit
interface Vlanif10
ip address 192.168.1.254 255.255.255.0
quit
- 防火墙(FW1):
system - view
interface GigabitEthernet1/0/0
ip address 192.168.1.253 255.255.255.0
quit
interface GigabitEthernet1/0/1
ip address 13.0.0.1 255.255.255.0
quit
interface GigabitEthernet1/0/2
ip address 12.0.0.1 255.255.255.0
quit
firewall zone trust
add interface GigabitEthernet1/0/0
quit
firewall zone untrust
add interface GigabitEthernet1/0/1
add interface GigabitEthernet1/0/2
quit
security - policy
rule name trust_to_untrust
source - zone trust
destination - zone untrust
source - address 192.168.1.0 0.0.0.255
action permit
quit
nat address - group 1
address 13.0.0.10 13.0.0.20
quit
acl number 2000
rule 5 permit source 192.168.1.0 0.0.0.255
quit
nat outbound 2000 address - group 1
- 路由器(R3):
system - view
interface GigabitEthernet0/0/0
ip address 13.0.0.2 255.255.255.0
quit
interface GigabitEthernet0/0/1
ip address 110.1.1.2 255.255.255.0
quit
interface GigabitEthernet0/0/2
ip address 110.1.1.2 255.255.255.0
quit
ip route - static 110.1.1.0 255.255.255.0 GigabitEthernet0/0/2
ip route - static 100.1.1.0 255.255.255.0 GigabitEthernet0/0/1
- 路由器(R2):
system - view
interface GigabitEthernet0/0/0
ip address 12.0.0.2 255.255.255.0
quit
interface GigabitEthernet0/0/1
ip address 280.1.1.2 255.255.255.0
quit
interface GigabitEthernet0/0/2
ip address 210.1.1.2 255.255.255.0
quit
ip route - static 210.1.1.0 255.255.255.0 GigabitEthernet0/0/2
ip route - static 280.1.1.0 255.255.255.0 GigabitEthernet0/0/1
- 电信DNS模拟机:IP设为110.1.1.1/24,网关110.1.1.2。
- 联通DNS模拟机:IP设为280.1.1.1/24,网关280.1.1.2。
- 百度web - 1模拟机:IP设为110.1.1.1/24,网关110.1.1.2。
- 百度web - 2模拟机:IP设为210.1.1.1/24,网关210.1.1.2。
三、需求补充配置
- 端口映射:假设Client2为Web服务器,在防火墙FW1配置:
interface GigabitEthernet1/0/1
nat server protocol tcp global current - interface 8080 inside 192.168.1.2 80
quit
- 访问控制列表(ACL)细化:在防火墙FW1限制Client1只能访问电信DNS,不能访问联通DNS:
acl number 3000
rule 5 permit ip source 192.168.1.1 0 destination 110.1.1.1 0
rule 10 deny ip source 192.168.1.1 0 destination 280.1.1.1 0
quit
security - policy
rule name acl_test
source - zone trust
destination - zone untrust
source - address 192.168.1.1 0
destination - address 110.1.1.1 0 280.1.1.1 0
action permit
rule - name - reference acl 3000
quit
- 流量统计:在防火墙FW1统计内网到外网流量:
acl number 2001
rule 5 permit source 192.168.1.0 0.0.0.255
quit
traffic - statistic enable
interface GigabitEthernet1/0/1
traffic - statistic inbound acl 2001
traffic - statistic outbound acl 2001
quit
- 高级安全策略配置
- 应用层过滤:在防火墙FW1限制内网访问危险网站:
acl number 3001
rule 5 deny url - category 1001 destination - zone untrust
quit
security - policy
rule name app_filter
source - zone trust
destination - zone untrust
source - address 192.168.1.0 0.0.0.255
action deny
rule - name - reference acl 3001
quit
- IPS(入侵防御系统)配置:在防火墙FW1启用IPS检测攻击:
ips - policy name my_ips_policy
rule 1001 signature - id 1000001 action block
quit
security - policy
rule name ips_protection
source - zone trust
destination - zone untrust
source - address 192.168.1.0 0.0.0.255
action permit
ips - policy my_ips_policy
quit
- QoS(服务质量)配置
- 带宽限制:在防火墙FW1限制内网访问外网总带宽:
qos car - outbound interface GigabitEthernet1/0/1 cir 1024000 cbs 1024000
qos car - outbound interface GigabitEthernet1/0/2 cir 1024000 cbs 1024000
- 优先级设置:在交换机LSW1和防火墙FW1为视频会议(端口5000 - 5010)设高优先级:
交换机LSW1:
acl number 3002
rule 5 permit tcp destination - port range 5000 5010
quit
qos car - inbound acl 3002 cir 512000 cbs 512000 priority 7
防火墙FW1:
acl number 3003
rule 5 permit tcp destination - port range 5000 5010
quit
qos car - inbound acl 3003 cir 512000 cbs 512000 priority 7
- VPN(虚拟专用网络)配置:在防火墙FW1配置IPSec VPN供远程办公访问内网:
ike proposal 10
encryption - algorithm aes - 256
authentication - algorithm sha2 - 256
dh group14
authentication - method pre - shared - key
integrity - algorithm hmac - sha2 - 256
prf hmac - sha2 - 256
quit
ike peer my_ike_peer
exchange - mode main
pre - shared - key cipher mypassword
ike - proposal 10
remote - address 200.200.200.200
quit
ipsec proposal my_ipsec_proposal
encapsulation - mode tunnel
transform - protocol esp
esp encryption - algorithm aes - 256
esp authentication - algorithm sha2 - 256
quit
ipsec policy my_ipsec_policy 10 isakmp
security acl 3004
ike - peer my_ike_peer
proposal my_ipsec_proposal
quit
acl number 3004
rule 5 permit ip source 192.168.1.0 0.0.0.255 destination 10.0.0.0 0.0.0.255
quit
interface GigabitEthernet1/0/1
ipsec policy my_ipsec_policy
quit
- 日志与审计配置:在防火墙FW1开启日志,发送到日志服务器192.168.1.250:
info - center enable
info - center loghost 192.168.1.250
info - center source default channel 1 log level warning
(2)图形配置
四、验证测试
- 连通性测试:在Client1和Client2用ping命令测到各模拟机连通性,模拟机反向ping内网客户端。
- 服务访问测试:在Client1和Client2浏览器访问百度web - 1和百度web - 2模拟机,模拟视频会议测流畅性。
- 安全功能测试:访问被过滤危险网站,用模拟攻击工具测试IPS功能。
- VPN功能测试:模拟远程办公连VPN,测能否访问内网资源。