anolis 8.9安装k8s
关闭防火墙
systemctl disable firewalld --now
关闭 selinux
setenforce 0
sudo sed -i 's/^SELINUX=.*/SELINUX=disabled/g' /etc/selinux/config
关闭 swap
sudo swapoff -a
sudo sed -ri 's/.*swap.*/#&/' /etc/fstab
配置内核参数
sudo tee /etc/sysctl.d/k8s.conf <<EOF
net.bridge.bridge-nf-call-ip6tables = 1
net.bridge.bridge-nf-call-iptables = 1
EOF
#配置k8s的yum源
sudo tee /etc/yum.repos.d/kubernetes.repo <<EOF
[kubernetes]
name=Kubernetes
baseurl=https://mirrors.aliyun.com/kubernetes/yum/repos/kubernetes-el7-x86_64/
enabled=1
gpgcheck=0
EOF
添加主机域名映射
sudo nano /etc/hosts
192.168.6.10 k8s-master-10
192.168.6.12 k8s-node-12
192.168.6.13 k8s-node-13
yum install -y yum-utils device-mapper-persistent-data lvm2
yum-config-manager --add-repo http://mirrors.aliyun.com/docker-ce/linux/centos/docker-ce.repo
sudo yum -y install docker-ce-20.10.9 docker-ce-cli-20.10.9 containerd.io docker-compose-plugin
配置docker命令补全
yum install -y bash-completion
source /usr/share/bash-completion/completions/docker
#重新打开shell 终端
nano /etc/docker/daemon.json
{
"registry-mirrors": ["https://docker.anyhub.us.kg"],
"exec-opts": ["native.cgroupdriver=systemd"],
"log-driver": "json-file",
"log-opts": {
"max-size": "100m"
},
"storage-driver": "overlay2"
}
加载 Docker 配置
sudo systemctl daemon-reload
systemctl start docker
Docker 服务开机启动
sudo systemctl enable docker --now
3、安装kubectl、kubelet、kubeadm(所有节点)
安装kubectl、kubelet、kubeadm
sudo yum install -y kubelet-1.23.17 kubeadm-1.23.17 kubectl-1.23.17
设置 kubelet 开机启动
sudo systemctl enable kubelet --now
systemctl start kubelet
systemctl enable kubelet
部署k8s的master和node节点
部署master节点,在192.168.6.10执行
初始化master节点
kubeadm init --apiserver-advertise-address=192.168.6.10 --image-repository registry.aliyuncs.com/google_containers --kubernetes-version v1.16.0 --service-cidr=10.140.0.0/16 --pod-network-cidr=10.240.0.0/16
master下执行:
mkdir -p $HOME/.kube
cp -i /etc/kubernetes/admin.conf $HOME/.kube/config
chown $(id -u):$(id -g) $HOME/.kube/config
安装 calico 网络(主节点)
下载配置文件
curl https://docs.projectcalico.org/v3.15/manifests/calico.yaml -O
调整为自己的网络配置
nano calico.yaml
找到3590行
# - name: CALICO_IPV4POOL_CIDR
# value: "192.168.0.0/16"
改为
- name: CALICO_IPV4POOL_CIDR
value: "10.240.0.0/16"
应用部署
kubectl apply -f calico.yaml
8、安装 dashboard(主节点)
下载配置文件
curl https://raw.githubusercontent.com/kubernetes/dashboard/v2.0.0-rc7/aio/deploy/recommended.yaml -O
调整配置
nano recommended.yaml
————————————————
找到
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
Spec:
ports:
- port: 443
targetPort: 8443
spec-ports段中增加为:
spec:
type: NodePort
ports:
- port: 443
targetPort: 8443
nodePort: 30000
应用配置
kubectl apply -f recommended.yaml
创建 dashboard 用户
nano dashboard-user.yaml
将以下内容写入文件
apiVersion: v1
kind: ServiceAccount
metadata:
name: admin-user
namespace: kubernetes-dashboard
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: admin-user
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: admin-user
namespace: kubernetes-dashboard
应用配置
kubectl apply -f dashboard-user.yaml
登录 dashboard
在浏览其中输入https://192.168.6.10:30000/
kubectl -n kubernetes-dashboard get svc
获取登录 token
#kubectl -n kubernetes-dashboard get secret $(kubectl -n kubernetes-dashboard get sa/admin-user -o jsonpath="{.secrets[0].name}") -o go-template="{{.data.token | base64decode}}"
kubectl -n kubernetes-dashboard describe secret $(kubectl -n kubernetes-dashboard get secret | grep admin-user | awk '{print $1}')
输入token,登录
2024.10.18更新,比较绕的过程,原因是又另建了一个环境,发现k8s版本不一样,和官方文档的一些说发不一样:
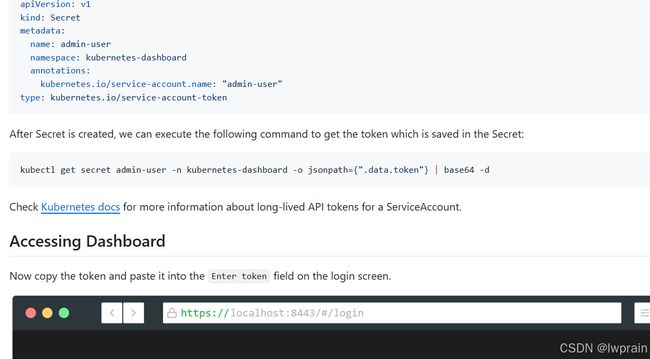
目前发现,在我用的k8s版本:1.20.4以及1.23.17
dashboard版本:2.0.0.rc7和2.4.0中,获取kubenetes-dashboard登录token的方法,着重说,不是加集群的token,一步一步来的话,其实是这样的:
kubectl -n kubernetes-dashboard get secret
结果如下:
NAME TYPE DATA AGE
admin-user-token-gdbrc kubernetes.io/service-account-token 3 62m
然后再次用命令:
kubectl -n kubernetes-dashboard describe secrets admin-user-token-gdbrc
获取这个token,拿着这个token登录dashboard就可以。
在官方的项目说明文档中:
https://github.com/kubernetes/dashboard/blob/master/docs/user/access-control/creating-sample-user.md
某个时间点,把老的方法该部分相关的内容删除了。
------------ tips结束
可能会提示:你的连接不是专用连接怎么解决(你的连接不是专用连接)
当遇到浏览器显示’你的连接不是专用连接’时,可通过启用Windows Defender防火墙或者在英文输入状态下,按thisisunsafe组合键来解决。此方法利用了Chromium内建的安全后门,用于忽略证书错误。
部署node节点,在192.168.6.12和13执行
wugv28.gipgeggf7g3p56o3过期的话:
在master执行
kubeadm token create
,将新的token替换进原来的kubeadm join中
没过期:
kubeadm token list
获取
获取ca证书hash:
openssl x509 -pubkey -in /etc/kubernetes/pki/ca.crt | openssl rsa -pubin -outform der 2>/dev/null | openssl dgst -sha256 -hex | sed 's/^.* //'
kubeadm join 192.168.6.10:6443 --token mm1mey.txyjlvet070knjlh --discovery-token-ca-cert-hash sha256:5d562dd49412a9e24b6e97363facf82293ddd16cc9fd23d239f4fd1de71550c9 --v=2
kubectl get nodes
查看集群状态 ,master中执行。
kubectl delete pod coredns-58cc8c89f4-rd9lz -n kube-system
在Kubernetes集群中创建一个pod,验证是否正常运行
创建一个pod,开放对外端口访问,这里会随机映射一个端口
kubectl create deployment nginx --image=nginx
kubectl expose deployment nginx --port=80 --type=NodePort
kubectl get pod,svc
已经可以看到nginx以NodePort的形式部署
如例子:80:30287/tcp
可以在http://192.168.6.12:30287或者 http://192.168.6.13:30287 访问nginx站点了