PatentTips - Maintaining shadow page tables in a sequestered memory region
BACKGROUND
Malicious code, known as malware, which includes viruses, worms, adware, etc., may attack core components of the operating system to compromise key applications, including critical applications that operate in the operating system kernel, such as security, firewall and anti-virus agents. One concern is that malware may attack page tables maintained by the operating system to perform address translation for critical security applications. The malware may modify the references in the page table to point to pages of the malware code that when invoked by the security agent performs malicious operations.
FIG. 1, panel 2 shows that prior to the attack, the critical agent, e.g., security or anti-virus application, references good pages of critical agent code. Panel 4 shows that prior to the attack the malware application page tables reference malicious pages of malicious malware code. Panel 6 shows that after the attack, the critical agent's page tables are modified to point to malicious pages. By referencing the malware page as shown in panels 6 and 8, address translation for the critical agent may cause the critical agent to execute the malware code in malicious page 1, panel 8. The executed malware code may provide the malware access to critical agent data structures to allow the malware to orchestrate a malicious attack on the system.
DETAILED DESCRIPTION
FIG. 2 illustrates a computing environment used with the described embodiments. A computer 2 includes a host processor 4 and service processor 6. The host processor 4 includes microcode 24 implementing the host processor 4 platform and architecture. The host 4 and service 6 processors may be implemented in separate processor devices. For instance, the host processor 4 may be implemented in a central processing unit (CPU) and the service processor 6 may be implemented in a chipset, comprising one or more integrated circuit devices. The chipset in which service processor 6 may be implemented may be directly attached to the motherboard or implemented on an expansion card. Alternatively, the host 4 and service 6 processors may be implemented on separate CPU devices. Still further, the host 4 and service 6 processors may be implemented as separate virtual machines implemented in a single processor device. Virtual machines may be implemented in a single processor device using a virtualization monitor.
The host 4 and service 6 processors execute different operating systems 14 and 38, respectively, and maintain separate operating system data structures to independently execute applications and perform operations. The computer 2 further includes a basic input/output system (BIOS) 8 including code executed by the host processor 4 to initialize and control various computer 2 components (e.g., the keyboard, display screen, disk drives, serial communications, etc.) during a boot sequence. The BIOS 8 may be implemented in firmware in a non-volatile memory device on the computer 2motherboard, such as a Flash memory, Read Only Memory (ROM), Programmable ROM (PROM), etc. The BIOS 8 code indicates the sequence of the boot operations.
The computer 2 includes a memory 10, comprising one or more memory devices, configured to include a host memory 12 in which an operating system14 executed by the host processor 4 is loaded. One or more applications 16, having application code 18 and data structures 20, are loaded into the operating system 14 environment implemented in the host memory 12 to execute. In certain embodiments, the applications 16 may include device drivers loaded in the kernel space of the operating system 14. The operating system 14 may comprise an operating system known in the art, such as a Microsoft® Windows® operating system, Linux™, etc. (Microsoft and Windows are registered trademarks of Microsoft Corporation and Linux is a trademark of Linus Torvalds).
During initialization, the BIOS 8 may configure a sequestered memory region 22 that is inaccessible to processes controlled by the operating system14, but is accessible to the operating system 38 and applications 40 executed by the service processor 6.
Page tables 28 in the host memory 12 are created for the application 16. Page tables 28 have entries for virtual addresses used by the application 16that map to physical addresses referencing physical locations in pages 30 in the host memory 12. Page tables 28 in the host memory 12 are accessible to the operating system 14 and applications 16 executing therein. Additionally, shadow page tables 32 are created for the application 16 in the sequestered memory region 22 having entries for virtual addresses that map to physical addresses referencing locations in pages 30 in the host memory 12.
A sequestered memory flag 26 implemented in the host processor 4 platform, such as the host processor 4 circuitry or chipset, indicates whether the host processor 4 may access the sequestered memory region 22. In normal operating mode, the host processor 4 and applications 16 running in the host memory 12 do not access the sequestered memory region 22. However, while performing address translations using shadow page tables 32, the host processor 4 requires access to the sequestered memory region 22 which hosts the shadow page tables 32. For the duration of such access, the host processor 4 configures the sequestered memory flag 26 to enable access to the sequestered memory region 22. Once the address translations using the shadow page tables 32 complete, the flag 26 is set to disable host processor 4 access to the sequestered memory region 22.
The sequestered memory region 22 may further include sequestered code 34 loaded into the sequestered memory region 22 by the BIOS 8 during the boot sequence that is inaccessible to processes operating under the operating system 14. This sequestered code 34 comprises code associated with the sequestered memory region 22 and may comprise special firmware code that may be executed in a special operating mode, i.e., sequestered mode, of the processor platform in which the host processor 4 process has exclusive access to all of platform hardware resources. In other words, this sequestered operating mode of the platform provides an isolated environment independent of the host operating system 14.
In certain embodiments, the host processor 4 may execute a special interrupt, which instruction is recognized by the host processor 4 platform and causes the host processor 4 to save the host processor 4 state information and enter the sequestered mode to execute the sequestered code 34loaded by the BIOS 8 in the sequestered memory region 22. Upon processing the special interrupt, the host processor 4 executes special handlers to execute the sequestered code 34 to perform various system management operations.
In one embodiment, the sequestered code 34 may comprise System Management Mode (SMM) code included in Intel Corporation's ("Intel") processor architecture. On Intel architectures, the sequestered operating mode is referred to as System Management Mode (SMM) and the special interrupt to invoke the SMI mode is referred to as a System Management Interrupt (SMI). Further details of the SMM mode are described in the publication from Intel entitled "Intel Architecture Software Developer's Manual, Volume 3: System Programming" (Copyright Intel, 1999). In additional embodiments, the sequestered mode, sequestered code 34, and special interrupt may be implemented in processor architectures from different processor vendors.
The memory 10 may further implement a service processor memory region 36 accessible to the service processor 6, but not to the host processor 4. The service processor 6 executes an operating system 38. The service processor 6 may execute a shadow page table agent 40 that manages shadow page tables 32 in the sequestered memory region 22 for the host applications 16. In one embodiment, the service processor 6 has access to the sequestered memory region 22.
References in FIG. 2 to single instances of certain components, such as the page table 28, application 16, memory pages 30, shadow page table 32, etc. may refer to multiple instances of these components.
FIG. 3 illustrates operations to implement an address translation table for the application 16 as a shadow page table 32 in the sequestered memory region 22. Control begins at block 100 with the host processor 4 executing the host operating system 14 to load the application 16. The host processor4 executes code in the application 16 to invoke (at block 102) a second processor, e.g., service processor 6, to create shadow page table(s) 32 in the sequestered memory region 22 for the application 16. The developer of the application 16 may include code to create shadow page tables 32 in the sequestered memory region 22 to use for address translation. Blocks 104 through 122 provide an embodiment of how the service processor 6 is invoked to create shadow page tables 32. While executing the application 16, the host processor 4 executes (at block 104) the special interrupt (which in an Intel SMM embodiment, comprises an SMI interrupt) to cause the host processor 4 to execute in the sequestered mode, e.g., service management mode (SMM), to register a shadow page table 32. Other programming techniques may be used to cause the host processor 4 to execute in sequestered mode. As discussed, in this sequestered mode, the host processor 4 does not execute the loaded operating system 14 code (which is executed when operating in the operating system mode), but instead executes the sequestered code 34 (to execute in the sequestered or second mode) which may have been loaded into the sequestered memory region 22 during system initialization. The sequestered memory region 22 is inaccessible to the operating system 14. The host processor 4 may execute (at block 106) a sequestered mode routine, which is part of the special interrupt handler, to call a shadow page table (SPT) agent 40 executed by the service processor 6.
The SPT agent 40, executed by the service processor 6, may pin (at block 108) the memory pages 30 in the host memory 12 referenced by the entries in the shadow page table 32. Pinning the memory pages 30 in the host memory 12 prevents the pages from being swapped to disk. Further, when pinning the memory pages 30, the pinned memory pages 30 are not moved once allocated and the shadow page table 32 protects those pinned pages30. The SPT agent 40 further validates (at block 110) the application 16 from which the call to register shadow page tables 32 was made. To validate the application 16, the SPT agent 40 may determine whether the application 16 is indicated in a list as an acceptable application type or whether the application 16 is indicated in a list indicating malicious application types which are not permitted to register shadow page tables 32. Alternatively, the application 16 may be digitally signed by a trusted entity, indicating that the application 16 is allowed to register with the SPT agent 40. In one embodiment, the call to register the shadow page tables 32, e.g., the special interrupt, may indicate the location of the application 16 in host physical memory 12 to provide to the service processor 6. To verify the image and validate the application 16, the SPT agent 40 may scan the image of the application 16 at the location indicated in the call and compute a hash of the image to compare with pre-configured hashes of acceptable images.
If (at block 112) the application 16 from which the call was made to register shadow page tables 32 is not validated, then the SPT agent 40 fails (at block 114) the registration process, which may involve returning an error to the special interrupt executed by first processor and generate a platform alert. The host processor 4 exits (at block 116) the sequestered mode and returns to host operating system mode to execute the host operating system14 code and application code 16. The host processor 4 may exit the sequestered mode by executing an exit instruction. In SMM embodiments, the exit instruction may comprise the RESUME (RSM) instruction executed in the system management mode (SMM). Upon exiting the sequestered mode in the event of a failure, the host processor 4 unloads (at block 118) the application 16. Further, the pinned memory pages may be unpinned.
If (at block 112) the application 16 registering the shadow page table 32 is validated, then the SPT agent 40 creates (at block 120) the shadow page table 32 to provide address translation from virtual to physical addresses for a virtual address range used by the application 14. Upon the SPT agent 40notifying (at block 122) the host processor 4 of completing the shadow page tables 32, the host processor 4 exits (at block 124) the sequestered mode operations and returns to host operating system mode to execute the host operating system 14 and the applications 16.
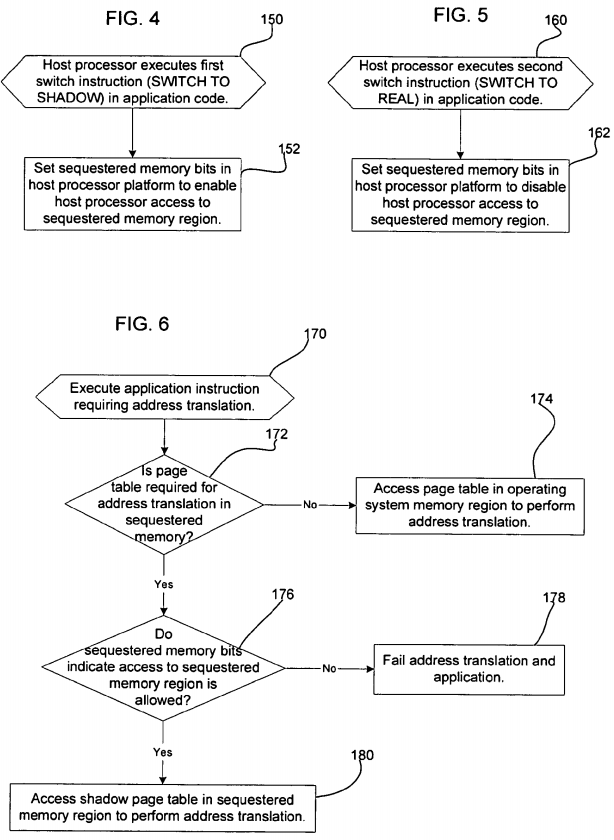
FIGS. 4, 5, and 6 illustrate an embodiment of operations implemented in the host processor microcode 24 to perform page table related operations when executing application code 18. With respect to FIG. 4, when the host processor 4 executes (at block 150) a first switch instruction (e.g., SWITCH_TO_SHADOW) in the application code 18, the host processor 4 configures (at block 152) the host processor 4 to set the sequestered memory flag 26 to enable the host processor access to the sequestered memory region 22. In certain embodiments, the host processor microcode 24will only allow the host processor 4 access to the sequestered memory region 22 if the sequestered memory flag 26 is set to enabled. Further, the configuration of the sequestered memory flag 26 may allow the host processor read/write access to the sequestered memory region 22, or could restrict this access to read-only. Also, in certain embodiments, the host processor 4 may be allowed to perform certain privileged operations only when the sequestered memory flag 26 is set to enabled. Such operations, for example, could include writing to specific I/O ports, writing to certain memory regions, executing certain instructions, reading/modifying certain processor registers, etc. Yet further, the host processor 4 may encounter an exception when processing one switch instruction in the application if the sequestered memory region does not include one shadow page table for the application being processed.
After executing the first switch instruction, the host processor 4 accesses the shadow page tables 32 to perform address translation for application code 18 instructions between the first switch instruction and a second switch instruction (e.g., SWITCH_TO_REAL). With respect to FIG. 5, when the host processor 4 executes (at block 160) a second switch instruction (e.g., SWITCH_TO_REAL) in the application code 18, the host processor 4configures (at block 162) the sequestered memory flag 26 to disable the host processor 4 access to the sequestered memory region 22.
FIG. 6 illustrates an embodiment of operations implemented in the host processor microcode 24 to perform address translation when executing the application code 18. Upon executing (at block 170) application code 18 instructions requiring address translation, the host processor 4 determines (at block 172) whether the page table required for address translation is a shadow page table 32 in the sequestered memory region 22. If not, then the host processor 4 accesses (at block 174) the page table 28 in the operating system 14 memory region in the host memory 12 to perform address translation for the processed instruction. Otherwise, if (at block 172) the shadow page table 32 is used for the specific address translation, then the host processor4 determines (at block 176) whether the sequestered memory flag 26 indicates that access to the sequestered memory region 2 is allowed. If (at block176) access is not allowed, then the address translation fails (at block 178) and the application 16 may also fail. Otherwise, if (at block 176) access to the sequestered memory region 22 is permitted, then the host processor 4 accesses (at block 180) the shadow page table 32 for the address to translate in the sequestered memory region 32 to perform address translation.
With the described embodiments of FIGS. 4, 5, and 6, malicious code cannot modify critical page tables implemented as shadow page tables 32 for a critical application 16 because the page tables required for address translation for these critical addresses comprise shadow page tables 32 in a sequestered memory region 22 that is inaccessible to the malicious code and which cannot be altered by the malicious code. For instance, once the shadow page table 32 is registered and loaded into the sequestered memory region 22 by the shadow page table agent 40, the application 16 shadow page table 32 cannot be modified to point to pages having code for the malicious application.
In certain embodiments, when the host processor 4 is executing application code 18 between the two switch statements, the host processor 4 may disable interrupts and not execute any other code other than the application code 18 between the switch statements while access to the sequestered memory region 22 is enabled until the second switch statement disables access to the sequestered memory region 22.
FIG. 7 illustrates an embodiment of operations performed to deregister and remove shadow page tables 32 for the application 16 from the sequestered memory region 22 when unloading the application 16 from the host memory 12. Control begins at block 200 with the host processor 4 executing the host operating system 14 to unload the application 16. The host processor 4 invokes (at block 202) a service processor 6 to remove specified shadow page table(s) 32 in the sequestered memory region 22 for the application 16. The service processor 6 may be invoked by executing application code 18 for unloading the application 16. Blocks 204 through 218 provide an embodiment of how the service processor 6 is invoked to de-register and remove shadow page tables 32. While executing the application code 18 to unload the application 16, the host processor 4 executes (at block 204) a special interrupt, such as a Service Mode Interrupt (SMI), in the application code 18 to cause the host processor 4 to execute in the sequestered mode to register a page table. As discussed, in this sequestered mode, the host processor 4 does not execute the loaded operating system 14 code (in a host operating system mode), but instead executes sequestered code 34 (to execute in the sequestered mode) which may have been loaded by the BIOS 8into the sequestered memory region 22 during system initialization. The host processor 4 may execute a sequestered mode routine, which is part of a handler, in the sequestered mode to call (at block 206) the shadow page table (SPT) agent 40 executed by the service processor 6.
The SPT agent 40, executed by the service processor 6 validates (at block 208) the source (agent) from which the un-register call was made. To validate the source of the call, the sequestered code 34 handling the special interrupt can determine that the source of the call is from a registered agent. The sequestered code 34 for handling interrupts may consult with the service processor 6 to obtain a list of registered agents permitted to make such calls to unregister applications.
If (at block 210) the source of the call to unregister shadow page tables 32 is not validated, then the SPT agent 40 fails (at block 212) the unregistration process, which may involve returning an error to the special interrupt executed by the host processor 4 and generate a platform alert. The host processor 4 exits (at block 214) the sequestered mode in response to the returned error and returns to host operating system mode to execute the host operating system 14 code and application 16. The host processor 4 may exit the sequestered mode by executing an exit instruction.
If (at block 210) the source of the call to unregister is validated, then the SPT agent 40 removes (at block 216) the shadow page table 32 from the sequestered memory region 22. After the requested shadow page tables 32 for the application 16 are removed from the sequestered memory region22, the host processor 4 exits (at block 218) the sequestered mode and returns to host operating system mode to execute the host operating system14 and continue unloading the application 16.
With the described embodiment of FIG. 7, the application communicates with the SPT agent 40 to remove shadow page tables 32 from the sequestered memory region 22.
Described embodiments utilize a sequestered memory region 22 to maintain certain application page tables used for address translation to protect these shadow page tables from malicious modifications from malware executing in the operating system. Applications executing in the operating system environment are not able to access the sequestered memory region 22 to modify the references in the shadow page table 32 to point to pages of malicious code in the host memory 12, such as shown in panel 6 in FIG. 1. The shadow page tables 32 protected in the sequestered memory region 22may include critical application code used for maintaining security in the system 2. Further, if the operating system 14 crashes, the shadow page tables32 in the sequestered memory region 22 can be retrieved to access application memory pages 30 in the memory 14 for afterlife diagnosis.