OpenVAS漏洞扫描基础教程之OpenVAS概述及安装及配置OpenVAS服务
OpenVAS漏洞扫描基础教程之OpenVAS概述及安装及配置OpenVAS服务
OpenVAS基础知识
OpenVAS(Open Vulnerability Assessment System)是开放式漏洞评估系统,其核心部分是一个服务器。该服务器包括一套网络漏洞测试程序,可以检测远程系统和应用程序中的安全问题。OpenVAS不同与传统的漏洞扫描软件。所有的OpenVAS软件都是免费的,而且还采用了Nessus(一款强大的网络扫描工具)较早版本的一些开放插件。虽然Nessus很强大,但是该工具不开源,而且免费版的功能又比较局限。所以,本章将对OpenVAS工具进行详细介绍。
OpenVAS概述
OpenVAS是开放式漏洞评估系统,也可以说它是一个包含着相关工具的网络扫描器。本节将对OpenVAS的概念及架构做一个简单介绍。
什么是OpenVAS
OpenVAS是一款开放式的漏洞评估工具,主要用来检测目标网络或主机的安全性。该工具是基于C/S(客户端/服务器),B/S(浏览器/服务器)架构进行工作,用户通过浏览器或者专用客户端程序来下达扫描任务,服务器端负载授权,执行扫描操作并提供扫描结果。
OpenVAS的架构
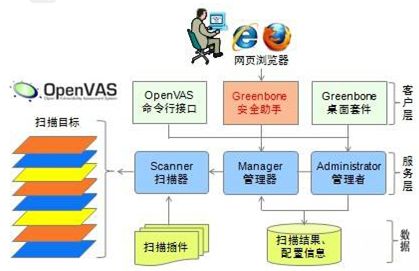
一套完整的OpenVAS系统包括服务器端和端口端的多个组件,如图1.1所示。
图1.1 OpenVAS的架构
上图就是OpenVAS系统的一个架构。下面分别介绍服务器层和客户层,分别所需安装的组件。如下所示:
1.服务器层组件(建议都安装)
q openvas-scanner(扫描器):负责调用各种漏洞检测插件,完成实际的扫描操作。
q openvas-manager(管理器):负责分配扫描任务,并根据扫描结果生产评估报告。
q openvas-administrator(管理者):负责管理配置信息,用户授权等相关工作。
2.客户层组件(任选其一即可)
q openvas-cli(命令行接口):负责提供从命令行访问OpenVAS服务层程序。
q greenbone-security-assistant(安装助手):负责提供访问OpenVAS服务层的Web接口,便于通过浏览器来建立扫描任务,是使用最简便的客户层组件。
q Greenbone-Desktop-Suite(桌面套件):负责提供访问OpenVAS服务层的图形程序界面,主要允许在Windows客户机中。
提示:OpenVAS服务器端仅支持安装Linux操作系统中。但是,客户端安装在Windows和Linux系统均可。
安装及配置OpenVAS服务
当对OpenVAS工具了解后,就可以来使用该工具了。在使用该工具之前,首先介绍下它的安装方法。
安装OpenVAS
OpenVAS工具的安装比较简单,而且在OpenVAS官网提供了在各种操作系统中的安装方法。其下载地址为http://www.openvas.org/install-packages.html。但是,如果用户在安装时,可能会出现很多依赖包需要手动解决。如果不能够很好的解决依赖关系包,将无法成功安装OpenVAS工具。所以,为了方便用户使用,Kali Linux系统中已经默认安装了该工具,用户可以直接使用。
如果用户发现自己系统中安装的OpenVAS不是最新版本的话,可以通过以下方法安装最新版的OpenVAS工具。具体方法如下所示:
(1)更新软件包列表。执行命令如下所示:
root@Kali :~# apt-get update
执行以上命令后,将会获取最近的软件包列表。
(2)获取到最新的软件包,。执行命令如下所示:
root@Kali :~# apt-get dist-upgrade
执行以上命令后,将会对有更新的包进行下载并安装。
(3)重新安装OpenVAS工具。执行命令如下所示:
root@Kali :~# apt-get install openvas
执行以上命令后,如果没有报错,则说明已成功安装OpenVAS工具。如果当前系统中已经安装了最新版的OpenVAS软件,将会显示以下类似信息:
正在读取软件包列表... 完成
正在分析软件包的依赖关系树
正在读取状态信息... 完成
openvas 已经是最新的版本了。
下列软件包是自动安装的并且现在不需要了:
firmware-mod-kit libafpclient0 libhackrf liblzma-dev libmozjs22d libnet-daemon-perl libnfc3 libplrpc-perl
libruby libtsk3-3 libwireshark2 libwiretap2 libwsutil2 openjdk-7-jre-lib python-apsw python-utidylib
ruby-crack ruby-diff-lcs ruby-rspec ruby-rspec-core ruby-rspec-expectations ruby-rspec-mocks ruby-simplecov
ruby-simplecov-html unrar-free xulrunner-22.0
Use 'apt-get autoremove' to remove them.
升级了 0 个软件包,新安装了 0 个软件包,要卸载 0 个软件包,有 20 个软件包未被升级。
从以上输出信息中,可以看到OpenVAS已经是最新版本了。
配置OpenVAS服务
OpenVAS工具安装成功后,还需要进行一些配置才可以使用。例如,初始化服务、同步插件及启动服务等。下面将介绍在Kali Linux中配置OpenVAS服务的方法。
【示例1-1】配置OpenVAS服务。具体操作步骤如下所示:
(1)下载并更新OpenVAS库。执行命令如下所示:
root@Kali :~# openvas-setup
/var/lib/openvas/private/CA created
/var/lib/openvas/CA created #创建证书
[i] This script synchronizes an NVT collection with the 'OpenVAS NVT Feed'.
[i] The 'OpenVAS NVT Feed' is provided by 'The OpenVAS Project'.
[i] Online information about this feed: 'http://www.openvas.org/openvas-nvt-feed.html'.
[i] NVT dir: /var/lib/openvas/plugins
[w] Could not determine feed version.
[i] rsync is not recommended for the initial sync. Falling back on http.
[i] Will use wget
[i] Using GNU wget: /usr/bin/wget
[i] Configured NVT http feed: http://www.openvas.org/openvas-nvt-feed-current.tar.bz2
[i] Downloading to: /tmp/openvas-nvt-sync.QH0Vl5ckzd/openvas-feed-2015-07-28-23736.tar.bz2
--2015-07-28 09:53:24-- http://www.openvas.org/openvas-nvt-feed-current.tar.bz2
正在解析主机 www.openvas.org (www.openvas.org)... 5.9.98.186
正在连接 www.openvas.org (www.openvas.org)|5.9.98.186|:80... 已连接。
已发出 HTTP 请求,正在等待回应... 200 OK
长度:17065793 (16M) [application/x-bzip2]
正在保存至: “/tmp/openvas-nvt-sync.QH0Vl5ckzd/openvas-feed-2015-07-28-23736.tar.bz2”
100%[======================================================================>] 17,065,793 337K/s 用时 34s
2015-07-28 09:54:09 (484 KB/s) - 已保存 “/tmp/openvas-nvt-sync.QH0Vl5ckzd/openvas-feed-2015-07-28-23736.tar.bz2” [17065793/17065793])
2008/
2008/deb_008_1.nasl #同步NVT库
...... Please report synchronization problems to [email protected].
If you have any other questions, please use the OpenVAS mailing lists
or the OpenVAS IRC chat. See http://www.openvas.org/ for details.
receiving incremental file list
./
COPYING
1493 100% 1.42MB/s 0:00:00 (xfer#1, to-check=63/65)
COPYING.asc
198 100% 193.36kB/s 0:00:00 (xfer#2, to-check=62/65)
nvdcve-2.0-2002.xml
19454677 100% 224.29kB/s 0:01:24 (xfer#3, to-check=61/65)
nvdcve-2.0-2002.xml.asc
198 100% 0.44kB/s 0:00:00 (xfer#4, to-check=60/65)
nvdcve-2.0-2003.xml
5691998 100% 266.11kB/s 0:00:20 (xfer#5, to-check=59/65)
nvdcve-2.0-2003.xml.asc
198 100% 7.73kB/s 0:00:00 (xfer#6, to-check=58/65)
......
Country Name (2 letter code) [DE]:State or Province Name (full name) [Some-State]:Locality Name (eg, city) []:Organization Name (eg, company) [Internet Widgits Pty Ltd]:Organizational Unit Name (eg, section) []:Common Name (eg, your name or your server's hostname) []:Email Address []:Using configuration from /tmp/openvas-mkcert-client.24593/stdC.cnf
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
countryName :PRINTABLE:'DE' #国家名
localityName :PRINTABLE:'Berlin' #本地名
commonName :PRINTABLE:'om' #普通名
Certificate is to be certified until Jul 27 03:02:02 2016 GMT (365 days)
Write out database with 1 new entries
Data Base Updated
Stopping OpenVAS Manager: openvasmd.
Stopping OpenVAS Scanner: openvassd.
Starting OpenVAS Scanner: openvassd.
Starting OpenVAS Manager: openvasmd.
Restarting Greenbone Security Assistant: gsad. #OpenVAS服务已启动
User created with password '4b44aa5b-5535-4525-b1db-d87c9b5d81cd'. #创建的用户密码
以上就是更新OpenVAS库的一个过程。从输出的信息中,可以看到在该过程中创建了证书、下载及更新了所有的扫描插件等。在该更新过程中,将会创建一个名为admin的用户,并且自动生成了一个密码。在本例中,生成的密码为4b44aa5b-5535-4525-b1db-d87c9b5d81cd。在该过程中输出的信息较多,由于篇幅的原因,中间部分内容使用省略号(......)取代了。由于此过程会下载大量的插件,所以该过程大概需要半个小时的时间。不过,再次进行同步时,时间就快了。
提示:在更新插件时主要是看用户的网速。如果网速好的话,可能不需要很长时间。但是,如果网速不好的话,需要的时间会很长,请用户耐心等待。而且,在该过程中用户不需要进行任何操作。
(2)在更新OpenVAS库时,自动为admin用户创建了一个密码。但是,该密码比较长,所以不容易记忆。为了方便用户记忆和输入,可以使用openvasmd命令修改该密码。其中,执行命令如下所示:
root@Kali:~# openvasmd --user=admin --new-password=123456
执行以上命令后,将不会输出任何信息。以上命令中,--user选项指定的是修改密码的用户为admin,--new-password选项指定将admin用户的密码修改为“123456”。
(3)为了确认OpenVAS是否安装完成,可以使用openvas-check-setup对该服务进行检查。如下所示:
root@Kali:~# openvas-check-setup
openvas-check-setup 2.3.0
Test completeness and readiness of OpenVAS-8
(add '--v6' or '--v7' or '--9'
if you want to check for another OpenVAS version)
Please report us any non-detected problems and
help us to improve this check routine:
http://lists.wald.intevation.org/mailman/listinfo/openvas-discuss
Send us the log-file (/tmp/openvas-check-setup.log) to help analyze the problem.
Use the parameter --server to skip checks for client tools
like GSD and OpenVAS-CLI.
Step 1: Checking OpenVAS Scanner ...
OK: OpenVAS Scanner is present in version 5.0.1.
OK: OpenVAS Scanner CA Certificate is present as /var/lib/openvas/CA/cacert.pem.
OK: OpenVAS Scanner server certificate is valid and present as /var/lib/openvas/CA/servercert.pem.
OK: NVT collection in /var/lib/openvas/plugins contains 40087 NVTs.
WARNING: Signature checking of NVTs is not enabled in OpenVAS Scanner.
SUGGEST: Enable signature checking (see http://www.openvas.org/trusted-nvts.html).
OK: The NVT cache in /var/cache/openvas contains 40087 files for 40087 NVTs.
OK: redis-server is present in version 2.4.14.
OK: scanner (kb_location setting) is configured properly using the redis-server socket: /var/lib/redis/redis.sock
OK: redis-server is running and listening on socket: /var/lib/redis/redis.sock.
OK: redis-server configuration is OK and redis-server is running.
Step 2: Checking OpenVAS Manager ...
OK: OpenVAS Manager is present in version 6.0.1.
OK: OpenVAS Manager client certificate is valid and present as /var/lib/openvas/CA/clientcert.pem.
OK: OpenVAS Manager database found in /var/lib/openvas/mgr/tasks.db.
OK: Access rights for the OpenVAS Manager database are correct.
OK: At least one user exists.
OK: sqlite3 found, extended checks of the OpenVAS Manager installation enabled.
OK: OpenVAS Manager database is at revision 146.
OK: OpenVAS Manager expects database at revision 146.
OK: Database schema is up to date.
OK: OpenVAS Manager database contains information about 40087 NVTs.
OK: OpenVAS SCAP database found in /var/lib/openvas/scap-data/scap.db.
OK: OpenVAS CERT database found in /var/lib/openvas/cert-data/cert.db.
OK: xsltproc found.
Step 3: Checking user configuration ...
WARNING: Your password policy is empty.
SUGGEST: Edit the /etc/openvas/pwpolicy.conf file to set a password policy.
Step 4: Checking Greenbone Security Assistant (GSA) ...
OK: Greenbone Security Assistant is present in version 6.0.1.
Step 5: Checking OpenVAS CLI ...
OK: OpenVAS CLI version 1.4.0.
Step 6: Checking Greenbone Security Desktop (GSD) ...
SKIP: Skipping check for Greenbone Security Desktop.
Step 7: Checking if OpenVAS services are up and running ...
OK: netstat found, extended checks of the OpenVAS services enabled.
OK: OpenVAS Scanner is running and listening only on the local interface.
OK: OpenVAS Scanner is listening on port 9391, which is the default port.
WARNING: OpenVAS Manager is running and listening only on the local interface.
This means that you will not be able to access the OpenVAS Manager from the
outside using GSD or OpenVAS CLI.
SUGGEST: Ensure that OpenVAS Manager listens on all interfaces unless you want
a local service only.
OK: OpenVAS Manager is listening on port 9390, which is the default port.
OK: Greenbone Security Assistant is listening on port 9392, which is the default port.
Step 8: Checking nmap installation ...
WARNING: Your version of nmap is not fully supported: 6.47
SUGGEST: You should install nmap 5.51 if you plan to use the nmap NSE NVTs.
Step 10: Checking presence of optional tools ...
OK: pdflatex found.
OK: PDF generation successful. The PDF report format is likely to work.
OK: ssh-keygen found, LSC credential generation for GNU/Linux targets is likely to work.
WARNING: Could not find rpm binary, LSC credential package generation for RPM and DEB based targets will not work.
SUGGEST: Install rpm.
WARNING: Could not find makensis binary, LSC credential package generation for Microsoft Windows targets will not work.
SUGGEST: Install nsis.
It seems like your OpenVAS-8 installation is OK.
If you think it is not OK, please report your observation
and help us to improve this check routine:
http://lists.wald.intevation.org/mailman/listinfo/openvas-discuss
Please attach the log-file (/tmp/openvas-check-setup.log) to help us analyze the problem.
从以上输出信息中,可以看到以上过程进行了九步检查。检查完后,看到“It seems like your OpenVAS-7 installation is OK.”信息,则表示OpenVAS安装成功。接下来,用户就可以使用OpenVAS工具实施扫描了。
本文选自:OpenVAS漏洞扫描基础教程大学霸内部资料,转载请注明出处,尊重技术尊重IT人!