jee6 学习笔记 12: Securing Application Component with JAAS api
In "jee6 学习笔记 11", we explored the JAAS configuration for a JSF2.0 application with JBoss7.1, so far so good.
This article would explore the JAAS APIs that enable further control on application component. We are going to explore two topics: "Hiding the navigation urls from the web app menu" and "Control access to EJB methods".
1. Hiding menu items for users that have no access to them
Now that we secure the web application based on the security domain configured in JBoss and the roles we defined in our database. We want to hide menu items that user has no access to.
For instance, in our example, user "jason" only has role "usr" allocated to him, such that "jason" has no access to resources like "/student/*". Therefore, "jason" should not see menu items "Student" at all after he logged in.
To achieve this, we can use JAAS api which is made available by HttpServletRequest (Servlet3.0). We can actually use EL directly in the menu page as "rendered=#{request.isUserInRole('admin')}" :
<p:submenu label="#{msgs.student}">
<p:menuitem value="#{msgs.studentSearch}" url="/student/studentSearch.jsf"
rendered="#{request.isUserInRole('admin')}" />
<p:menuitem value="#{msgs.studentNew}" url="/student/studentDetails.jsf"
rendered="#{request.isUserInRole('admin')}"/>
<p:separator/>
<p:menuitem value="#{msgs.blah}" url="#"/>
</p:submenu>
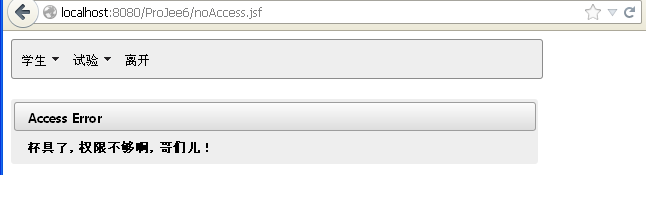
With this in place, "jason" would not see menu items that are not accessible. However, if he is naughty and figured out our url patterns, he still can manually enters the url in his browser. That's no problem, he'll get the no access error page, like this screen shot:
This is the Chinese version of it (-;
2. Control access to EJB methods
Here's the JAAS api to use for different context:
| EJB | javax.ejb.EJBContext.isCallerInRole(role) |
| Servlet | javax.servlet.http.HttpServletRequest.isUserInRole(role) |
| Web Service | javax.xml.ws.WebServiceContext.isUserInRole(role) |
Access control to EJB methods can be achieved by using annotation @javax.annotation.security.RolesAllowed, But it's also necessary to let the EJB know our security domain, which was configured in JBoss. We need to use JBoss specific annotation to do this: @org.jboss.ejb3.annotation.SecurityDomain. This annotation can be found in JBoss ("C:\jboss-as-7.1.1\modules\org\jboss\ejb3\main") and you need to add it to your project class path for compilation.
Here's the test ejb "JaasEjbTest.java":
package test.jxee.ejb;
import javax.annotation.PostConstruct;
import javax.annotation.Resource;
import javax.annotation.security.RolesAllowed;
import javax.ejb.SessionContext;
import javax.ejb.Stateless;
import org.apache.log4j.Logger;
import org.jboss.ejb3.annotation.SecurityDomain;
@Stateless
@SecurityDomain("jwSecureTest") // our security domain configured in JBoss
public class JaasEjbTest {
private static final Logger log = Logger.getLogger(JaasEjbTest.class);
@Resource
private SessionContext sc; // for testing only
@PostConstruct
public void init() {
log.debug(">>> ejb post inited: " + this);
}
@RolesAllowed({"admin"}) // this method requires "admin" role to access
public String getMessage() {
boolean callerInRole = sc.isCallerInRole("admin"); // test JAAS api
log.debug(">>> caller in role ? " + callerInRole);
return "-- hello from JAAS ejb test --";
}
}
Here's the backing bean:
package test.jxee.action;
import java.io.Serializable;
import javax.ejb.EJB;
import javax.faces.bean.ManagedBean;
import org.apache.log4j.Logger;
import test.jxee.ejb.JaasEjbTest;
@ManagedBean(name="jaasTest")
public class JaasTestBean implements Serializable {
private static final Logger log = Logger.getLogger(JaasTestBean.class);
@EJB private JaasEjbTest jtest;
public String getMsg() {
try {
return jtest.getMessage();
}
catch(javax.ejb.EJBAccessException eae) {
log.warn("### Unauthorized access to ejb: " + JaasEjbTest.class.toString());
}
return "-- You have no access to the EJB --";
}
}
Here's the jsf page:
<ui:composition xmlns="http://www.w3.org/1999/xhtml"
xmlns:h="http://java.sun.com/jsf/html"
xmlns:f="http://java.sun.com/jsf/core"
xmlns:ui="http://java.sun.com/jsf/facelets"
xmlns:p="http://primefaces.org/ui"
template="/template/template1.xhtml">
<ui:define name="title">Test JAAS</ui:define>
<ui:define name="content">
<h:form>
<p:panel header="JAAS api test on EJB method" toggleable="true" style="width:60%">
<h:panelGrid columns="1">
<h:outputText id="output" value="#{jaasTest.msg}" escape="false"/>
</h:panelGrid>
</p:panel>
</h:form>
</ui:define>
</ui:composition>
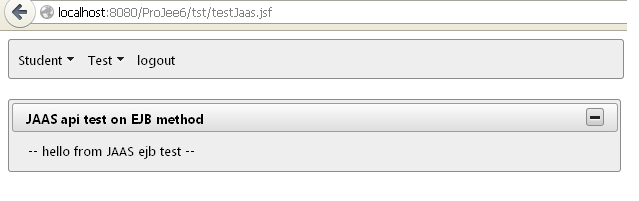
Screen shot of the page, when user "j2ee"(roles: admin/usr) logged in and try to access the ejb:
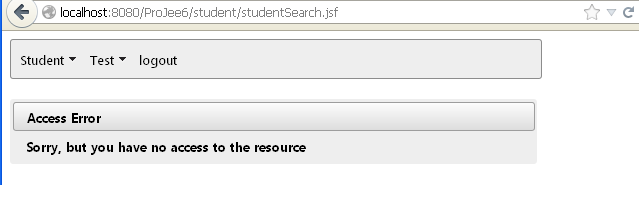
Screen shot of the page, when user "jason"(roles: usr) logged in and try to access the ejb: