OpenLDAP Installation&Configuration Guide
OpenLDAP Installation&Configuration Guide
Install the openldap
# yum -y install openldap.x86_64 openldap-clients.x86_64 openldap-devel.x86_64 openldap-servers.x86_64
Configure the openldap
Generate the olcRootPW:
# slappasswd
New password: qazwsx
Re-enter new password: qazwsx
{SSHA}nnrYPYMtry/sPDUilclaQOp2u4/m5xZL
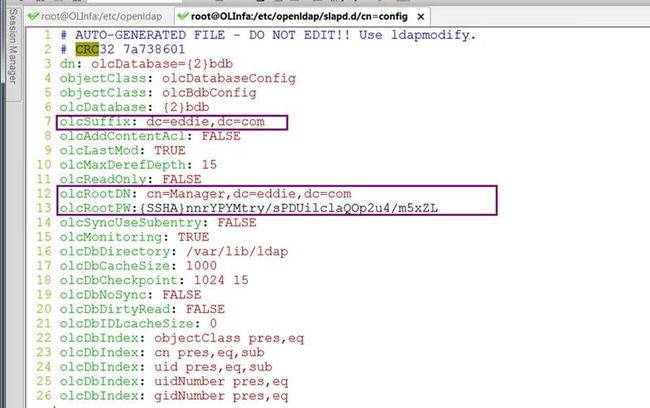
Modify the olcDatabase={2}bdb.ldif
Modify the olcDatabase={2}bdb.ldif file, and change the olcRootDN and olcSuffix entries. The following is the default entry.
# grep olcRootDN /etc/openldap/slapd.d/cn=config/olcDatabase=\{2\}bdb.ldif
olcRootDN: cn=Manager,dc=my-domain,dc=com
# grep olcSuffix /etc/openldap/slapd.d/cn\=config/olcDatabase\=\{2\}bdb.ldif
olcSuffix: dc=my-domain,dc=com
Change the above line to your domain component. For example, eddie.
olcRootDN: cn=Manager,dc=eddie,dc=com
Appending these two lines into the olcDatabase\=\{2\}bdb.ldif file enables that the user can change their password, and should be authenticated.
olcAccess: {0}to attrs=userPassword by self write by dn.base="cn=Manager,dc=eddie,dc=com" write by anonymous auth by * none
olcAccess: {1}to * by dn.base="cn=Manager,dc=eddie,dc=com" write by self write by * read
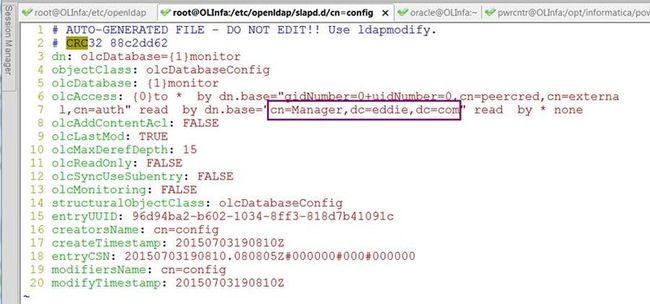
Modify the olcDatabase={1}monitor.ldif
Modify the olcDatabase\=\{1\}monitor.ldif , change the dn.base to your right one, for example, cn=Manager,dc=eddie,dc=com
Verify the configuration files
Execute the command to verify the configuration:
[root@OLInfa ~]# slaptest -u
559a89a8 ldif_read_file: checksum error on "/etc/openldap/slapd.d/cn=config/olcDatabase={1}monitor.ldif"
559a89a8 ldif_read_file: checksum error on "/etc/openldap/slapd.d/cn=config/olcDatabase={2}bdb.ldif"
config file testing succeeded
Please ignore the checksum error.
Start the openldap service
Start the openldap automatically when the OS starts[level 2,3,4,5].
# chkconfig slapd on
Start the openldap service now.
# service slapd start
Configure the initial ldif file
Create an initial ldif file: eddie.ldif
[root@OLInfa ~]# cat eddie.ldif
dn: dc=eddie,dc=com
objectClass: dcObject
objectClass: organization
dc: eddie
o: eddie
Import the initial ldif file
ldapadd -x -W -D "cn=Manager,dc=eddie,dc=com" -f eddie.ldif
Enter LDAP Password:
adding new entry "dc=eddie,dc=com"
Verify the base structure
# ldapsearch -x -W -D "cn=Manager,dc=eddie,dc=com" -b "dc=eddie,dc=com" "(objectclass=*)"
Enter LDAP Password:
# extended LDIF
#
# LDAPv3
# base <dc=eddie,dc=com> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# eddie.com
dn: dc=eddie,dc=com
objectClass: dcObject
objectClass: organization
dc: eddie
o: eddie
……
Now you can use other ldap clients to manage it.