- 无铅压电陶瓷研究进展:技术突破与产业升级路径
莱歌数字
数字化转型#职场经验#结构热设计科技热设计CAE散热能源
作者简介:科技自媒体优质创作者个人主页:莱歌数字-CSDN博客公众号:莱歌数字个人微信:yanshanYH211、985硕士,职场15年+从事结构设计、热设计、售前、产品设计、项目管理等工作,涉足消费电子、新能源、医疗设备、制药信息化、核工业等领域涵盖新能源车载与非车载系统、医疗设备软硬件、智能工厂等业务,带领团队进行多个0-1的产品开发,并推广到多个企业客户现场落地实施。专题课程Flotherm
- 华为路由器典型配置(附案例)
normanhere
华为智能路由器iphone
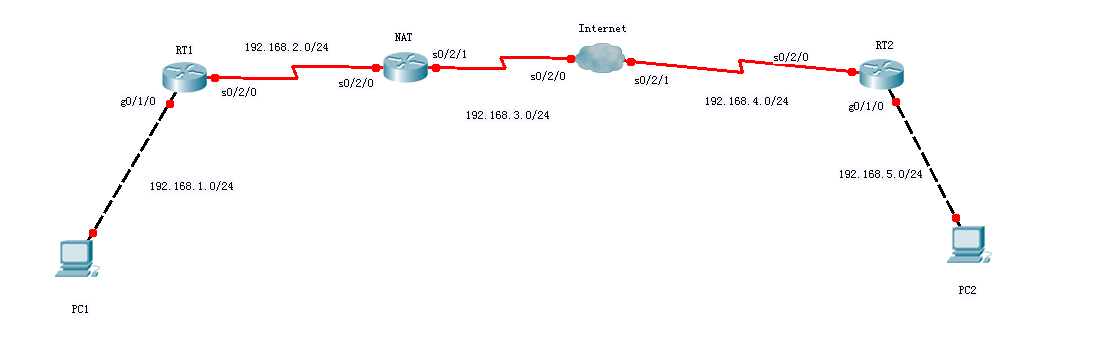
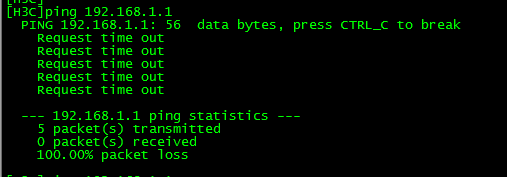
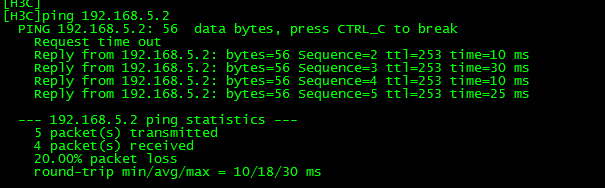
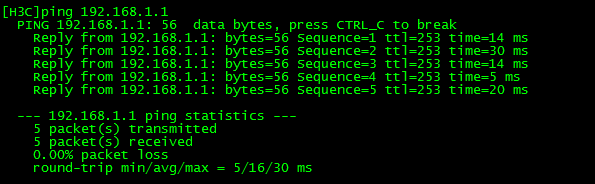
案例拓扑:#主用路由器R_ShenZhen_1配置displaycurrent-configurationsysnameR_ShenZhen_1#SNAT调用,将IPSEC流量排除aclnumber3000rule5denyipsource10.2.0.00.0.255.255destination10.4.0.00.0.255.255rule10permitipsource10.0.0.00.2
- DeepSeek:AI驱动的效率革命与实战案例解
weixin_45788582
人工智能aiDeepSeek
在人工智能技术的浪潮中,DeepSeek作为一款专注实现AGI(通用人工智能)的先锋工具,正通过其强大的自然语言处理(NLP)与分布式计算能力,重新定义高效办公的边界。以下通过技术解析与实战案例,展现DeepSeek如何赋能个人与企业,开启职场效率革命。一、技术革新:DeepSeek的核心竞争力深度学习赋能DeepSeek的技术架构基于BERT、Transformer等先进深度学习模型,通过构建复
- 【HarmonyOS next】ArkUI-X休闲娱乐搞笑日历【基础】
harmonyos-next
引言在跨平台应用开发中,网络图片在不同设备上的适配展示是常见挑战。本文将基于HarmonyOSnext的ArkUI-X框架,通过一个休闲娱乐日历应用,展示如何实现网络图片在华为和iOS设备上的完美适配。应用每日通过API获取搞笑日历图片,并在不同设备上智能适配显示。开发环境操作系统:macOS开发工具:DevEcoStudio5.0.4测试设备:华为Nova12Ultra、iPhone13Pro开
- 【HarmonyOS next】ArkUI-X休闲益智记忆翻牌【进阶】
harmonyos-next
本文通过记忆翻牌游戏实现,揭秘网络图片在HarmonyOS与iOS设备上的渲染差异,并提供专业级优化方案。基于ArkUI-X的Web组件技术,我们实现了一套代码双端运行的混合架构。一、跨平台实现架构//ArkTS核心实现importweb_webviewfrom'@ohos.web.webview';@Entry@ComponentstructIndex{controller:web_webvie
- 【HarmonyOS Next】ArkUI-X休闲益智接水果【进阶】
harmonyos-next
本文通过ArkUI-X实现跨平台接水果游戏,深入探究网络图片在HarmonyOS与iOS设备上的渲染差异,并提供专业级优化方案。基于WebView的混合架构,我们实现了单代码库双端适配的高效开发模式。一、跨平台架构设计//ArkTS核心实现importweb_webviewfrom'@ohos.web.webview';@Entry@ComponentstructIndex{controller:
- 【HarmonyOS next】ArkUI-X休闲益智儿童拼图【进阶】
harmonyos-next
【HarmonyOSnext】ArkUI-X休闲益智儿童拼图【进阶】一、前言:当拼图遇上跨端开发最近在开发一款跨平台的儿童拼图游戏时,我深刻体会到了ArkUI-X框架的威力——同一套代码竟能同时在华为Mate60Pro和iPhone15上流畅运行!这不仅节省了开发成本,更重要的是确保了多端用户体验的一致性。今天我们就来聊聊这个项目的核心技术点,特别是拖动坐标计算和图片剪影生成这两个让人"又爱又恨"
- 软件测试从业者必备的SQL知识
十二测试录
数据库sql数据库
作为职场人,学一门技能是用来解决日常工作问题的,没必要从头到尾把这块知识弄透,没那么多时间。基于此,十二根据自己的经验,把软件测试从业者需要掌握的SQL知识,整理如下;只要跟着这个顺序,从头到尾执行即可。前置准备事项:1、在自己电脑上安装一个mysql数据库,文章见->虚拟机Centos下安装Mysql完整过程(图文详解)_虚拟机安装mysql-CSDN博客2、找一个mysql客户端链接工具:初学
- 英国留学生顺利拿到offer!博士学历+微软MOS国际认证加buff!
全球认证考试中心
microsoft
在全球化职场竞争日益激烈的当下,英国留学生若想提升自身竞争力,考取高含金量的国际证书是一条有效途径。MicrosoftOfficeSpecialist(MOS)国际认证作为微软官方推出的办公软件专业认证,在全球168个国家和地区得到认可,每年吸引近百万人次报考,已成为众多外企筛选人才的重要标准。正值暑假,不少同学计划利用这段时间备考MOS,本文将结合实际经验,为大家提供一套系统的备考方案。一、为何
- 【策划所需编程知识】
叫我六胖子
笔记游戏
1、TCP与UDP名称TCPUDP方式先奏后斩先斩后奏优点防外挂,慢但不出错用户体验好常用游戏MMORPGFPS、MOBA、IO类2、弱联网与实时联网名称弱联网实时联网方式只在必要时链接频率很高特点频率低频率高特点对宽带要求不高对宽带要求高常用游戏卡牌、放置挂机、轻度休闲、SLGFPS、MOBA、IO类
- 【AIGC-ChatGPT提示词】心灵笔记:打造温暖治愈的职场年终回顾系统
AI小欧同学
AIGCchatgpt笔记
感谢信任,专栏出现0-1的历史突破❤️❤️好了,开始今天的内容今天继续回馈大家,最近都是可以在自媒体上使用的提示词。提示词在最下方引言在每年岁末时分,我们都期待着对过去一年进行总结与回顾。然而,传统的工作总结往往过于注重数据和绩效,容易忽视个人的情感体验和内心成长。"心灵笔记"系统正是为了解决这一痛点而设计,它致力于将冰冷的职场经历转化为温暖治愈的内心独白,帮助人们以更有温度的方式记录自己的职业生
- “苏超”拉动周末消费,抖音生活服务:比赛城市迎来普遍消费上涨
大力财经
生活
“苏超”爆火,有力拉升了紧随赛程的周末消费。抖音生活服务数据显示,刚刚过去的周末(6月21日至22日),江苏商圈休闲运动团购订单消费环比增长225%,到店消费金额环比增长181%。虽然几个比赛城市周末天气欠佳,相关抖音团购订单仍迎来显著上涨,例如南京团购到店消费环比增长21%,其中户外玩乐、运动户外用品订单消费环比增长超150%。6月21日,苏超南京队4:0战胜常州队,常州赛场失意却成为城市消费赢
- 创客匠人揭秘长红 IP 的三力模型:从 193 万发售看 IP 变现本质
创小匠
tcp/ip网络协议网络
在知识付费下半场,为何有的IP昙花一现,而张值符老师能通过创客匠人陪跑实现单场193万变现?其核心在于构建了“愿力、产品力、商业力”的三力模型。一、愿力:IP长红的底层燃料张老师“解决生死困惑”的发心,使其内容天然具备穿透力。创客匠人研究发现,明确“为谁请命”的IP,粉丝粘性比泛领域高2.6倍。某母婴IP将定位从“育儿知识”聚焦到“职场妈妈背奶困境”,内容打开率提升40%,付费转化率达行业均值的3
- eclipse远程连接linux,c - 使用Eclipse通过SSH处理远程项目
燕衔泥PPT
c-使用Eclipse通过SSH处理远程项目我有以下方框:带有EclipseCDT的Windows框,一个Linux机器,只能通过SSH访问我。构建和运行我的项目所需的编译器和硬件都只在机器B上。我想使用EclipseCDT从该项目的Windows框中“透明地”工作,并能够在IDE中远程构建,运行和调试项目。我如何设置:大楼会起作用吗?任何比编写本地makefile更简单的解决方案,然后调用一个远
- 〖Python APP 自动化测试实战篇④〗- 通过 appium 驱动夜神模拟器完成第一个自动化脚本 - 查看通讯录
哈哥撩编程
#④-自动化测试实战篇Python全栈白宝书appiumappium驱动夜神模拟器pythonAPP自动化测试实战
>【易编橙·终身成长社群,相遇已是上上签!】-点击跳转~<作者:哈哥撩编程(视频号、B站、抖音同名)图书作者:程序员职场效能宝典博客专家:全国博客之星第四名超级个体:COC上海社区主理人特约讲师:谷歌亚马逊分享嘉宾
- 《2025年AI工程师生存报告:掌握Agent开发薪资涨65%》——500家科技企业招聘数据揭示的职场进化法则
知识产权13937636601
计算机人工智能科技
当大模型吞噬基础编码岗位,2025年掌握AI智能体(Agent)开发的工程师薪资中位数突破¥92万/年,较普通AI岗位高出65%。本文基于阿里、腾讯、微软等头部企业招聘数据,首次披露:技能断层危机:传统算法工程师简历淘汰率达73%能力跃迁公式:智能体架构+领域模型=薪资溢价150%职业生存矩阵:30岁未掌握AutoFlow开发面临40%裁员风险数据显示:具备多智能体协同架构能力者晋升总监级时间缩短
- 毕业一年,想转行,在IT方向(大数据分析)与财务(注会)间犹豫,不知哪个更有发展前景?
cda2024
数据分析数据挖掘
毕业一年,职场新人往往会面临职业发展的关键选择。如果你正在IT方向(大数据分析)与财务(注会)之间犹豫,不知道哪个更有发展前景,那么这篇文章或许能为你提供一些有价值的参考。本文将从行业趋势、职业发展路径、技能需求等方面进行深入分析,帮助你在两个方向中做出更明智的选择。行业趋势大数据分析随着信息技术的飞速发展,大数据已经渗透到各个领域,成为推动企业创新和增长的重要力量。根据IDC的预测,全球大数据市
- 趣说IT职场23:写代码容易,把需求写清楚才是地狱难度!
欢乐熊嵌入式编程
趣说IT职场职场码农产品经理项目需求产品策划
写代码容易,把需求写清楚才是地狱难度!你以为你在写代码,其实你在靠意念解谜。“这个需求很简单,你搞一下。”“功能逻辑很清晰的,我都和产品说好了。”“就照原型做,没啥细节啦。”你点头接单,打开文档,心里默念:“兄弟,文档没细节,UI只画个框,你让我拿什么‘搞一下’?”于是开始了你每天的高难度挑战:写代码?不,是开天眼看需求?不,是读心术推进项目?不,是解诅咒!一、需求不是不写,是写得像谜语人你有没
- 2025.6.24总结
天真小巫
职场发展
今天发生了两件事,这每件事情都足以影响我的工作状态。1.团队中有人要转岗这算是最让我有些小震惊的事件了。我不明白,那个同事干得好好的,为啥会转岗,为啥会被调到其他团队。虽然团队有正编,有od,但我自始自终觉得,就是一个团队,一起战斗过的战友,兄弟。他从测试岗调去了鸿蒙开发岗,听说是测试科目四没考过,这也让我有些危机感,同样是还没考过,他却先我一步调走了,问起原因,只因我工号是00。职场重来不是谈感
- 量贩零食上云,原生的最划算
点击此处查看视频!继现制茶饮、咖啡、餐饮等行业后,量贩零食成为消费领域又一个跑出万店的赛道,这些线下零售起家的连锁企业,正以另一种范式诠释着什么是后互联网时代的新零售。本文整理自鸣鸣很忙集团数字化中心总经理孙浩和运维服务部经理黄奖的视频采访稿。鸣鸣很忙集团是中国最大的休闲食品饮料连锁零售商,亦是中国食品饮料量贩模式的引领者,旗下现有“零食很忙”、“赵一鸣零食”两大品牌。截至2024年12月31日,
- 职场沟通(下对上【不立即反对】、平级【尽量帮】、上对下【脸色和蔼】)
学博成
职场职场和发展
下对上:【先讲对方,想听的东西、合理坚持、不立即反对】下对上:不能请示太多,需要上级的支持(对上级,礼让三分)1、除非上级想听,才讲(化解心结)2、事实还是你的看法,站在他的立场来思考,先讲对方,想听的东西,随机应变(人重要先讲人,事重要先讲事)例子:打招呼,还要提供情报对上线的不同的意见,要【合理】几分把握几分坚持对上面立即反应就是顶撞,你回去后,十分钟后你在再来立即反应是最愚蠢的人,上级面前绝
- Wordvice AI:Wordvice 推出的免费,基于先进的 AI 技术帮助用户提升英文写作质量
NetX行者
AI工具介绍人工智能AI工具
WordviceAI:智能写作助手,助力高效英文写作在当今全球化时代,英文写作已成为众多学生、研究人员、职场人士必备技能。然而,语法错误、表达不流畅、词汇匮乏等问题常困扰着大家。别担心,今天就来给大家介绍一款强大的免费AI智能写作助手——WordviceAI。一、功能强大,满足多样写作需求(一)全面语法检查WordviceAI能自动检测并修正语法、拼写和标点错误,确保文本准确无误。无论是学术论文、
- Java后端开发岗高频面试题及答案(面试必看)
禅与Bug的修复艺术
Java面试java面试开发语言Java面试Java后端后端开发程序员
Java面试随着时间的改变而改变。在过去的日子里,当你知道String和StringBuilder的区别就能让你直接进入第二轮面试,但是现在问题变得越来越高级,面试官问的问题也更深入。在我初入职场的时候,类似于Vector与Array的区别、HashMap与Hashtable的区别是最流行的问题,只需要记住它们,就能在面试中获得更好的机会,但这种情形已经不复存在。如今,你将会被问到许多Java程序
- AI会让我们变“笨“吗?MIT重磅研究敲响的警钟
攻城狮7号
AI前沿技术要闻深度学习人工智能chatgptAI大模型
目录前言一、一场关于"思考"的对决:MIT如何设计实验?二、惊人发现:当大脑开始"偷懒"2.1发现一:"大脑在省电"2.2发现二:记忆凭空消失2.3发现三:所有权的丧失三、"认知负债":正在透支未来的思考能力四、从实验室到现实:对教育和工作的深远影响4.1对教育的警钟4.2对职场的冲击五、AI并非猛虎:如何成为一个聪明的"AI使用者"?结语:选择权在我们手中攻城狮7号:个人主页个人专栏:《AI前沿
- AI时代的弯道超车之第五章:实用AI工具箱
Hebron_Deb
AI时代-弯道超车-逆袭人生人工智能
在这个AI重塑世界的时代,你还在原地观望吗?是时候弯道超车,抢占先机了!李尚龙倾力打造——《AI时代的弯道超车:用人工智能逆袭人生》专栏,带你系统掌握AI知识,从入门到实战,全方位提升认知与竞争力!**内容亮点:**AI基础+核心技术讲解职场赋能+创业路径揭秘打破信息差+预测行业未来第五章:实用AI工具箱欢迎来到第五课!今天我们聊得轻松一点,带大家认识一些日常生活和工作中都能用上的AI工具。AI真
- AI时代的弯道超车之第九章:AI如何改变传统教育模式
Hebron_Deb
AI时代-弯道超车-逆袭人生人工智能
在这个AI重塑世界的时代,你还在原地观望吗?是时候弯道超车,抢占先机了!李尚龙倾力打造——《AI时代的弯道超车:用人工智能逆袭人生》专栏,带你系统掌握AI知识,从入门到实战,全方位提升认知与竞争力!内容亮点:AI基础+核心技术讲解职场赋能+创业路径揭秘打破信息差+预测行业未来第九章:AI如何改变传统教育模式这章的标题可能有点惊人:“知识不重要了”。但我要说的,是人工智能正在深刻地改变我们对“教育”
- LinkedIn求职神器[特殊字符]AI驱动搜索让你轻松找到心仪工作!
人工智能我来了
人工智能AI人工智能
在当今竞争激烈的职场环境中,求职者们常常为找到合适的工作而感到困惑。复杂的搜索引擎常常需要用户输入精准的关键词,但这些关键词往往难以完全表达求职者的真实需求。为了改善这一现状,LinkedIn近期推出了一项全新的AI驱动求职搜索功能。这一功能通过利用提炼和微调的大型语言模型,在提升求职者求职体验上迈出了重要的一步。这项新功能让LinkedIn用户可以通过自然语言来进行职位搜索。例如,以往用户在输入
- 针对防火墙IPSec业务不通或业务丢包问题,防火墙如何做流量统计、远程抓包、报文示踪
ICT系统集成阿祥
一周学会防火墙技术-网络安全网络
问题描述针对防火墙IPSec业务不通或业务丢包问题,防火墙如何做流量统计、远程抓包、报文示踪解决方案1)配置流统和远程抓包用的ACL;system[sysname] acl 3555[sysname-acl-adv-3555] rule permit icmp source 10.82.100.215 0 destination 10.65.32.204 0 [sysname-acl-adv-35
- Android Studio 修改 JDK 版本的方法
奔跑吧邓邓子
必备核心技能androidstudioJDK修改方法
提示:“奔跑吧邓邓子”的必备核心技能专栏聚焦计算机技术与职场场景,拆解程序员、产品经理等技术从业者的核心能力图谱。内容涵盖编程思维、算法实战、项目管理、技术架构等硬核技能,结合案例解析代码优化、跨团队协作等落地方法论。定期更新前沿技术趋势与避坑指南,助你突破技能瓶颈,从执行层进阶到技术核心圈,成为职场中不可替代的复合型人才。目录一、AndroidStudio版本信息二、修改方法1.进入File->
- Android Studio 打 APK 包报错 Invalid keystore format 的解决方法
奔跑吧邓邓子
必备核心技能androidstudioideAPK打包invalid解决方法
提示:“奔跑吧邓邓子”的必备核心技能专栏聚焦计算机技术与职场场景,拆解程序员、产品经理等技术从业者的核心能力图谱。内容涵盖编程思维、算法实战、项目管理、技术架构等硬核技能,结合案例解析代码优化、跨团队协作等落地方法论。定期更新前沿技术趋势与避坑指南,助你突破技能瓶颈,从执行层进阶到技术核心圈,成为职场中不可替代的复合型人才。目录一、问题描述二、解决方法1.修改JDK版本2.使用第三方工具生成证书三
- 多线程编程之卫生间
周凡杨
java并发卫生间线程厕所
如大家所知,火车上车厢的卫生间很小,每次只能容纳一个人,一个车厢只有一个卫生间,这个卫生间会被多个人同时使用,在实际使用时,当一个人进入卫生间时则会把卫生间锁上,等出来时打开门,下一个人进去把门锁上,如果有一个人在卫生间内部则别人的人发现门是锁的则只能在外面等待。问题分析:首先问题中有两个实体,一个是人,一个是厕所,所以设计程序时就可以设计两个类。人是多数的,厕所只有一个(暂且模拟的是一个车厢)。
- How to Install GUI to Centos Minimal
sunjing
linuxInstallDesktopGUI
http://www.namhuy.net/475/how-to-install-gui-to-centos-minimal.html
I have centos 6.3 minimal running as web server. I’m looking to install gui to my server to vnc to my server. You can insta
- Shell 函数
daizj
shell函数
Shell 函数
linux shell 可以用户定义函数,然后在shell脚本中可以随便调用。
shell中函数的定义格式如下:
[function] funname [()]{
action;
[return int;]
}
说明:
1、可以带function fun() 定义,也可以直接fun() 定义,不带任何参数。
2、参数返回
- Linux服务器新手操作之一
周凡杨
Linux 简单 操作
1.whoami
当一个用户登录Linux系统之后,也许他想知道自己是发哪个用户登录的。
此时可以使用whoami命令。
[ecuser@HA5-DZ05 ~]$ whoami
e
- 浅谈Socket通信(一)
朱辉辉33
socket
在java中ServerSocket用于服务器端,用来监听端口。通过服务器监听,客户端发送请求,双方建立链接后才能通信。当服务器和客户端建立链接后,两边都会产生一个Socket实例,我们可以通过操作Socket来建立通信。
首先我建立一个ServerSocket对象。当然要导入java.net.ServerSocket包
ServerSock
- 关于框架的简单认识
西蜀石兰
框架
入职两个月多,依然是一个不会写代码的小白,每天的工作就是看代码,写wiki。
前端接触CSS、HTML、JS等语言,一直在用的CS模型,自然免不了数据库的链接及使用,真心涉及框架,项目中用到的BootStrap算一个吧,哦,JQuery只能算半个框架吧,我更觉得它是另外一种语言。
后台一直是纯Java代码,涉及的框架是Quzrtz和log4j。
都说学前端的要知道三大框架,目前node.
- You have an error in your SQL syntax; check the manual that corresponds to your
林鹤霄
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near 'option,changed_ids ) values('0ac91f167f754c8cbac00e9e3dc372
- MySQL5.6的my.ini配置
aigo
mysql
注意:以下配置的服务器硬件是:8核16G内存
[client]
port=3306
[mysql]
default-character-set=utf8
[mysqld]
port=3306
basedir=D:/mysql-5.6.21-win
- mysql 全文模糊查找 便捷解决方案
alxw4616
mysql
mysql 全文模糊查找 便捷解决方案
2013/6/14 by 半仙
[email protected]
目的: 项目需求实现模糊查找.
原则: 查询不能超过 1秒.
问题: 目标表中有超过1千万条记录. 使用like '%str%' 进行模糊查询无法达到性能需求.
解决方案: 使用mysql全文索引.
1.全文索引 : MySQL支持全文索引和搜索功能。MySQL中的全文索
- 自定义数据结构 链表(单项 ,双向,环形)
百合不是茶
单项链表双向链表
链表与动态数组的实现方式差不多, 数组适合快速删除某个元素 链表则可以快速的保存数组并且可以是不连续的
单项链表;数据从第一个指向最后一个
实现代码:
//定义动态链表
clas
- threadLocal实例
bijian1013
javathreadjava多线程threadLocal
实例1:
package com.bijian.thread;
public class MyThread extends Thread {
private static ThreadLocal tl = new ThreadLocal() {
protected synchronized Object initialValue() {
return new Inte
- activemq安全设置—设置admin的用户名和密码
bijian1013
javaactivemq
ActiveMQ使用的是jetty服务器, 打开conf/jetty.xml文件,找到
<bean id="adminSecurityConstraint" class="org.eclipse.jetty.util.security.Constraint">
<p
- 【Java范型一】Java范型详解之范型集合和自定义范型类
bit1129
java
本文详细介绍Java的范型,写一篇关于范型的博客原因有两个,前几天要写个范型方法(返回值根据传入的类型而定),竟然想了半天,最后还是从网上找了个范型方法的写法;再者,前一段时间在看Gson, Gson这个JSON包的精华就在于对范型的优雅简单的处理,看它的源代码就比较迷糊,只其然不知其所以然。所以,还是花点时间系统的整理总结下范型吧。
范型内容
范型集合类
范型类
- 【HBase十二】HFile存储的是一个列族的数据
bit1129
hbase
在HBase中,每个HFile存储的是一个表中一个列族的数据,也就是说,当一个表中有多个列簇时,针对每个列簇插入数据,最后产生的数据是多个HFile,每个对应一个列族,通过如下操作验证
1. 建立一个有两个列族的表
create 'members','colfam1','colfam2'
2. 在members表中的colfam1中插入50*5
- Nginx 官方一个配置实例
ronin47
nginx 配置实例
user www www;
worker_processes 5;
error_log logs/error.log;
pid logs/nginx.pid;
worker_rlimit_nofile 8192;
events {
worker_connections 4096;}
http {
include conf/mim
- java-15.输入一颗二元查找树,将该树转换为它的镜像, 即在转换后的二元查找树中,左子树的结点都大于右子树的结点。 用递归和循环
bylijinnan
java
//use recursion
public static void mirrorHelp1(Node node){
if(node==null)return;
swapChild(node);
mirrorHelp1(node.getLeft());
mirrorHelp1(node.getRight());
}
//use no recursion bu
- 返回null还是empty
bylijinnan
javaapachespring编程
第一个问题,函数是应当返回null还是长度为0的数组(或集合)?
第二个问题,函数输入参数不当时,是异常还是返回null?
先看第一个问题
有两个约定我觉得应当遵守:
1.返回零长度的数组或集合而不是null(详见《Effective Java》)
理由就是,如果返回empty,就可以少了很多not-null判断:
List<Person> list
- [科技与项目]工作流厂商的战略机遇期
comsci
工作流
在新的战略平衡形成之前,这里有一个短暂的战略机遇期,只有大概最短6年,最长14年的时间,这段时间就好像我们森林里面的小动物,在秋天中,必须抓紧一切时间存储坚果一样,否则无法熬过漫长的冬季。。。。
在微软,甲骨文,谷歌,IBM,SONY
- 过度设计-举例
cuityang
过度设计
过度设计,需要更多设计时间和测试成本,如无必要,还是尽量简洁一些好。
未来的事情,比如 访问量,比如数据库的容量,比如是否需要改成分布式 都是无法预料的
再举一个例子,对闰年的判断逻辑:
1、 if($Year%4==0) return True; else return Fasle;
2、if ( ($Year%4==0 &am
- java进阶,《Java性能优化权威指南》试读
darkblue086
java性能优化
记得当年随意读了微软出版社的.NET 2.0应用程序调试,才发现调试器如此强大,应用程序开发调试其实真的简单了很多,不仅仅是因为里面介绍了很多调试器工具的使用,更是因为里面寻找问题并重现问题的思想让我震撼,时隔多年,Java已经如日中天,成为许多大型企业应用的首选,而今天,这本《Java性能优化权威指南》让我再次找到了这种感觉,从不经意的开发过程让我刮目相看,原来性能调优不是简单地看看热点在哪里,
- 网络学习笔记初识OSI七层模型与TCP协议
dcj3sjt126com
学习笔记
协议:在计算机网络中通信各方面所达成的、共同遵守和执行的一系列约定 计算机网络的体系结构:计算机网络的层次结构和各层协议的集合。 两类服务: 面向连接的服务通信双方在通信之前先建立某种状态,并在通信过程中维持这种状态的变化,同时为服务对象预先分配一定的资源。这种服务叫做面向连接的服务。 面向无连接的服务通信双方在通信前后不建立和维持状态,不为服务对象
- mac中用命令行运行mysql
dcj3sjt126com
mysqllinuxmac
参考这篇博客:http://www.cnblogs.com/macro-cheng/archive/2011/10/25/mysql-001.html 感觉workbench不好用(有点先入为主了)。
1,安装mysql
在mysql的官方网站下载 mysql 5.5.23 http://www.mysql.com/downloads/mysql/,根据我的机器的配置情况选择了64
- MongDB查询(1)——基本查询[五]
eksliang
mongodbmongodb 查询mongodb find
MongDB查询
转载请出自出处:http://eksliang.iteye.com/blog/2174452 一、find简介
MongoDB中使用find来进行查询。
API:如下
function ( query , fields , limit , skip, batchSize, options ){.....}
参数含义:
query:查询参数
fie
- base64,加密解密 经融加密,对接
y806839048
经融加密对接
String data0 = new String(Base64.encode(bo.getPaymentResult().getBytes(("GBK"))));
String data1 = new String(Base64.decode(data0.toCharArray()),"GBK");
// 注意编码格式,注意用于加密,解密的要是同
- JavaWeb之JSP概述
ihuning
javaweb
什么是JSP?为什么使用JSP?
JSP表示Java Server Page,即嵌有Java代码的HTML页面。使用JSP是因为在HTML中嵌入Java代码比在Java代码中拼接字符串更容易、更方便和更高效。
JSP起源
在很多动态网页中,绝大部分内容都是固定不变的,只有局部内容需要动态产生和改变。
如果使用Servl
- apple watch 指南
啸笑天
apple
1. 文档
WatchKit Programming Guide(中译在线版 By @CocoaChina) 译文 译者 原文 概览 - 开始为 Apple Watch 进行开发 @星夜暮晨 Overview - Developing for Apple Watch 概览 - 配置 Xcode 项目 - Overview - Configuring Yo
- java经典的基础题目
macroli
java编程
1.列举出 10个JAVA语言的优势 a:免费,开源,跨平台(平台独立性),简单易用,功能完善,面向对象,健壮性,多线程,结构中立,企业应用的成熟平台, 无线应用 2.列举出JAVA中10个面向对象编程的术语 a:包,类,接口,对象,属性,方法,构造器,继承,封装,多态,抽象,范型 3.列举出JAVA中6个比较常用的包 Java.lang;java.util;java.io;java.sql;ja
- 你所不知道神奇的js replace正则表达式
qiaolevip
每天进步一点点学习永无止境纵观千象regex
var v = 'C9CFBAA3CAD0';
console.log(v);
var arr = v.split('');
for (var i = 0; i < arr.length; i ++) {
if (i % 2 == 0) arr[i] = '%' + arr[i];
}
console.log(arr.join(''));
console.log(v.r
- [一起学Hive]之十五-分析Hive表和分区的统计信息(Statistics)
superlxw1234
hivehive分析表hive统计信息hive Statistics
关键字:Hive统计信息、分析Hive表、Hive Statistics
类似于Oracle的分析表,Hive中也提供了分析表和分区的功能,通过自动和手动分析Hive表,将Hive表的一些统计信息存储到元数据中。
表和分区的统计信息主要包括:行数、文件数、原始数据大小、所占存储大小、最后一次操作时间等;
14.1 新表的统计信息
对于一个新创建
- Spring Boot 1.2.5 发布
wiselyman
spring boot
Spring Boot 1.2.5已在7月2日发布,现在可以从spring的maven库和maven中心库下载。
这个版本是一个维护的发布版,主要是一些修复以及将Spring的依赖提升至4.1.7(包含重要的安全修复)。
官方建议所有的Spring Boot用户升级这个版本。
项目首页 | 源