ssh-key免密钥认证实战
ssh-key免密钥认证
环境:
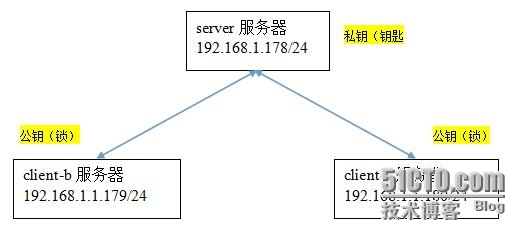
server 服务器192.168.1.178/24
client-b服务器192.168.1.1.179/24
client-c服务器192.168.1.1.180/24
这三台机器都禁止root的远程登录,并且把ssh的默认访问端口22改成5201端口
这三台机器都创建了crazy普通用户,密码123456
需求:实现server端通过SSH通道可以免密码访问client-b主机和client-c主机
拓扑图:
实战操作:
在server服务器使用crazy普通用户创建一对密钥,默认生成并且存放在家目录下:
[crazy@server ~]$ ssh-keygen -t dsa #生成一对dsa类型的密钥对
Generating public/private dsa key pair.
Enter file in which to save the key (/home/crazy/.ssh/id_dsa): #直接回车默认存放路径,路径不存的自动创建
Created directory '/home/crazy/.ssh'. #自动在家目录下创建.ssh目录
Enter passphrase (empty for no passphrase): #直接回车
Enter same passphrase again: #直接回车
Your identification has been saved in /home/crazy/.ssh/id_dsa.
Your public key has been saved in /home/crazy/.ssh/id_dsa.pub.
The key fingerprint is:
d8:2f:27:3e:92:18:1d:2a:8b:92:59:37:71:2f:e2:f6 crazy@server
[crazy@server ~]$ ls -al /home/crazy/.ssh/
total 16
drwx------ 2 crazy crazy 4096 Oct 26 04:25 .
drwx------ 4 crazy crazy 4096 Oct 26 04:24 ..
-rw------- 1 crazy crazy 672 Oct 26 04:25 id_dsa #创建的私钥(钥匙)
-rw-r--r-- 1 crazy crazy 602 Oct 26 04:25 id_dsa.pub #创建的公钥(锁)
使用 ssh-copy-id -i /home/crazy/.ssh/id_dsa.pub '-p5201 [email protected]'
ssh-copy-id -i /home/crazy/.ssh/id_dsa.pub '-p5201 [email protected]'
ssh-copy-id -i 这个是ssh的内置一个命令脚本
把公钥推送到192.168.1.179/24和192.168.1.180/24主机crazy用户的家目录下.ssh目录下存放
[crazy@server ~]$ ssh-copy-id -i /home/crazy/.ssh/id_dsa.pub '-p5201 [email protected]'
27
The authenticity of host '192.168.1.179 (192.168.1.179)' can't be established.
RSA key fingerprint is 1d:8e:6d:4e:63:41:8f:19:c0:dd:7e:1d:c4:dd:9c:8d.
Are you sure you want to continue connecting (yes/no)? yes #第一次连接需要把RSA认证加入本地
Warning: Permanently added '192.168.1.179' (RSA) to the list of known hosts.
[email protected]'s password: #输入对方crazy的用户密码
Now try logging into the machine, with "ssh '-p5201 [email protected]'", and check in:
.ssh/authorized_keys #推送的公钥,然后在对方家目录下创建.ssh目录,把公钥改名为authorized_keys
to make sure we haven't added extra keys that you weren't expecting.
[crazy@server ~]$ ssh-copy-id -i /home/crazy/.ssh/id_dsa.pub '-p5201 [email protected]'
27
The authenticity of host '192.168.1.180 (192.168.1.180)' can't be established.
RSA key fingerprint is 1d:8e:6d:4e:63:41:8f:19:c0:dd:7e:1d:c4:dd:9c:8d.
Are you sure you want to continue connecting (yes/no)? yes #第一次连接需要把RSA认证加入本地
Warning: Permanently added '192.168.1.180' (RSA) to the list of known hosts.
[email protected]'s password: #输入对方crazy的用户密码
Now try logging into the machine, with "ssh '-p5201 [email protected]'", and check in:
.ssh/authorized_keys #推送的公钥,然后在对方家目录下创建.ssh目录,把公钥改名为authorized_keys
to make sure we haven't added extra keys that you weren't expecting.
查看client-b服务器192.168.1.1.179/24和client-c服务器192.168.1.1.180/24
[crazy@client-B ~]$ tree -a #client-b服务器192.168.1.1.179/24
.
|-- .bash_history
|-- .bash_logout
|-- .bash_profile
|-- .bashrc
|-- .emacs
|-- .lesshst
|-- .mozilla
| |-- extensions
| `-- plugins
|-- .viminfo
`-- .zshrc
3 directories, 8 files
[crazy@client-B ~]$ tree -a
.
|-- .bash_history
|-- .bash_logout
|-- .bash_profile
|-- .bashrc
|-- .emacs
|-- .lesshst
|-- .mozilla
| |-- extensions
| `-- plugins
|-- .ssh #新创建的目录
| `-- authorized_keys #公钥(锁)的名称
|-- .viminfo
`-- .zshrc
4 directories, 9 files
[crazy@client-C ~]$ tree #client-c服务器192.168.1.1.180/24
.
|-- .bash_history
|-- .bash_logout
|-- .bash_profile
|-- .bashrc
|-- .emacs
|-- .mozilla
| |-- extensions
| `-- plugins
|-- .zshrc
`-- abcde
3 directories, 7 files
[crazy@client-C ~]$ tree -a
.
|-- .bash_history
|-- .bash_logout
|-- .bash_profile
|-- .bashrc
|-- .emacs
|-- .mozilla
| |-- extensions
| `-- plugins
|-- .ssh #新创建的目录
| `-- authorized_keys #公钥(锁)的名称
|-- .zshrc
`-- abcde
4 directories, 8 files
公钥(锁)分发完成后在server服务器使用ssh查看远程查看内存,不再提示输入密码
[crazy@server ~]$ ssh -p5201 [email protected] free #查看内存client-b服务器192.168.1.1.179/24
total used free shared buffers cached
Mem: 60528 28212 32316 0 1172 13364
-/+ buffers/cache: 13676 46852
Swap: 265064 132 264932
[crazy@server ~]$ ssh -p5201 [email protected] free #查看内存client-c服务器192.168.1.1.180/24
total used free shared buffers cached
Mem: 60528 27076 33452 0 1128 13060
-/+ buffers/cache: 12888 47640
Swap: 265064 224 264840
在sever端查看密钥对的权限,看出ssh免密钥认证对私钥权限控制的比较严格,公钥没有那么严格控制
[crazy@server .ssh]$ ls -l
total 12
-rw------- 1 crazy crazy 672 Oct 26 04:25 id_dsa #默认权限是600
-rw-r--r-- 1 crazy crazy 602 Oct 26 04:25 id_dsa.pub #默认权限是644
-rw-r--r-- 1 crazy crazy 790 Oct 26 05:20 known_hosts
改变权限测试:
[crazy@server .ssh]$ chmod 300 id_dsa #权限改成300
[crazy@server .ssh]$ ll
total 12
--wx------ 1 crazy crazy 672 Oct 26 04:25 id_dsa #权限改成300,无法验证通过
-rw-r--r-- 1 crazy crazy 602 Oct 26 04:25 id_dsa.pub
-rw-r--r-- 1 crazy crazy 790 Oct 26 05:20 known_hosts
[crazy@server .ssh]$ ssh -p5201 [email protected] free
Enter passphrase for key '/home/crazy/.ssh/id_dsa':
[email protected]'s password: #提示输入密码
[crazy@server .ssh]$ chmod 710 id_dsa #权限改成710
[crazy@server .ssh]$ ll
total 12
-rwx--x--- 1 crazy crazy 672 Oct 26 04:25 id_dsa #权限改成710,无法验证通过
-rw-r--r-- 1 crazy crazy 602 Oct 26 04:25 id_dsa.pub
-rw-r--r-- 1 crazy crazy 790 Oct 26 05:20 known_hosts
[crazy@server .ssh]$ ssh -p5201 [email protected] free
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: UNPROTECTED PRIVATE KEY FILE! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
Permissions 0710 for '/home/crazy/.ssh/id_dsa' are too open. ##权限改成710,提示权限too open
It is recommended that your private key files are NOT accessible by others.
This private key will be ignored.
bad permissions: ignore key: /home/crazy/.ssh/id_dsa
Enter passphrase for key '/home/crazy/.ssh/id_dsa':
[email protected]'s password: #提示输入密码
[crazy@server .ssh]$ chmod 400 id_dsa #权限改成400,验证可以通过
[crazy@server .ssh]$ ssh -p5201 [email protected] free
total used free shared buffers cached
Mem: 60528 27332 33196 0 1352 13076
-/+ buffers/cache: 12904 47624
Swap: 265064 224 264840
[crazy@server .ssh]$ chmod 700 id_dsa #权限改成700,验证可以通过
[crazy@server .ssh]$ ssh -p5201 [email protected] free
total used free shared buffers cached
Mem: 60528 27368 33160 0 1384 13076
-/+ buffers/cache: 12908 47620
Swap: 265064 224 264840
结论:
经过测试,私钥文件的权限改成400,500,600,700都能通过验证,其他的权限无法通过验证
本文出自 “疯狂的日子” 博客,转载请与作者联系!