NAT WAN
部署NAT的目的就是为了让后数据包的返回有“表“可依
拓扑表:
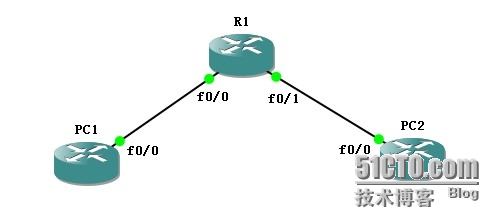
静态NAT配置:
interface f0/0
ip address 192.168.1.1 255.255.255.0
ip nat inside
interface f0/1
ip address 100.1.1.1 255.255.255.0
ip nat outside
ip nat inside source static 192.168.1.2 100.1.1.3
show ip nat translations 查看NAT表,静态表项一直存在的一条表
R1#show ip nat translations
Pro Inside global Inside local Outside local Outside global
--- 100.1.1.3 192.168.1.2 --- ---
PC1 ping PC2后 查看表
Pro Inside global Inside local Outside local Outside global
icmp 100.1.1.3:0 192.168.1.2:0 100.1.1.2:0 100.1.1.2:0
--- 100.1.1.3 192.168.1.2 --- ---
多出了一条,呵呵,其实还算是动态的啦!
从这里,我可以把需要的进行下总结:
inside 源IP outside目的IP
local转换前 global转换后
动态NAT配置
interface f0/0
ip address 192.168.1.1 255.255.255.0
ip nat inside
no shutdown
interface f0/1
ip address 100.1.1.1 255.255.255.0
ip nat outside
no shutdown
access-list 10 permit 192.168.1.0 0.0.0.255
ip nat pool test 100.1.1.3 100.1.1.100 prefix-length 24
ip nat inside source list 10 pool test
show ip nat translations 查看表项什么都没有
只有在ping 之后才能出现,相关表项
Pro Inside global Inside local Outside local Outside global
icmp 100.1.1.3:1 192.168.1.2:1 100.1.1.2:1 100.1.1.2:1
--- 100.1.1.3 192.168.1.2 --- ---
PAT:基本配置已配好
1、第一种方式
access-list 10 permit 192.168.1.0 0.0.0.255
ip nat pool test 100.1.1.3 100.1.1.3 prefix-length 24
ip nat inside source list 10 pool test overload
2、第二种方式
access-list 10 permit 192.168.1.0 0.0.0.255
ip nat inside source list 10 interface f0/1 overload
总结:如果是定义nat pool的话,里面的IP地址是不能用过的。
PAT是支持四层的,引用端口号的,在ICMP的负载里类似有端口号字段
也就是TCP,UDP,ICMP可以进行PAT
NAT的原则:
1、待转换的IP地址与接口IP在同一个网段
2、先查表,后NAT
PPP:公有协议,支持AAA协议
flag+address+control+protocol+data+fcs+flag
HDLC:
flag+address+control+data+fcs+flag
CISCO HDLC:
flag+address+control+properietary+data+fcs+flag
PPP:两个子协议
LCP:链路控制协议,负责物理层、链路层参数的协商
NCP:网络控制协议,负责三层的参数的协商
认证:
1、PAP:明文认证,两次握手,被认证者主动发起认证信息
CHAP:密文认证,三次握手,认证者主动发起要认证信息
拓扑图:
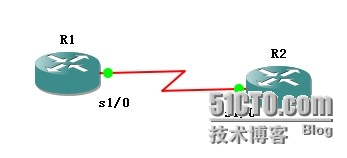
R1上的配置:
interface s1/0
ip address 12.1.1.1 255.255.255.0
no shutdown
encapsulation ppp
ppp authentication pap
exit
username admin password cisco
R2上的配置:
interface s1/0
ip address 12.1.1.2 255.255.255.0
no shutdown
encapsulation ppp
ppp pap sent-username admin password cisco
上图是单向PAP认证
双向认证如下:
R1上的配置
interface s1/0
ip address 12.1.1.1 255.255.255.0
no shutdown
encapsulation ppp
ppp authentication pap
ppp pap sent-username r2 password r2
exit
username r1 password r1
R2上的配置
interface s1/0
ip address 12.1.1.2 255.255.255.0
no shutdown
encapsulation ppp
ppp authentication pap
ppp pap sent-username r1 password r1
exit
username r2 password r1
chap单向认证:
R1:
interface s1/0
ip add 12.1.1.1 255.255.255.0
encapsulation ppp
no shutdown
ppp authentication chap
exit
username r1 password r1
R2:
interface s1/0
ip address 12.1.1.2 255.255.255.0
no shutdown
encapsulation ppp
ppp chap hostname r1(此句可省略)
ppp chap password r1
exit
chap 双向认证:
R1
interface s1/0
ip address 12.1.1.1 255.255.255.0
no shut
encasulation ppp
ppp authentication chap
ppp chap hostname r2
ppp chap password r2
exit
username r1 password r1
R2
interface s1/0
ip address 12.1.1.2 255.255.255.0
no shut
encapsulation ppp
ppp authentication chap
ppp chap hostname r1
ppp chap password r1
exit
username r1 password r1
可以使用主机名进行认证,只需要认证密码就可
R1
interface s1/0
encapsulation ppp
ppp authentication chap
ppp chap password cisco
exit
username R2 password cisco
R2
interface s1/0
encapsulation ppp
ppp authentication chap
ppp chap password cisco
exit
username R1 password cisco
看到了吗,用户名用的是对方的用户名。呵呵,就这么简单
下面做些QOS优化:
int s1/0
encapsulation ppp 封装PPP协议
ppp multilink 设置多链路
ppp multilink group 1 设置多链路组
no shutdown
interface multilink 1 设置多链路接口
ppp multilink
ppp multilink group 1
ppp multilink fragment delay 10 设置分段,每10毫秒一个段
ppp multilink interleave 设置交叉,就是讲高优先级数据交叉放在分段之间
ip address 12.1.1.1 255.255.255.0