openssl学习笔记--CA及https网站证书配置
一、需求分析:
证书服务器自建CA,网页服务器通过CA创建网页主机证书,以实现网站内容安全传输。
二、拓扑图:

三、相关配置:
1. 证书服务器(ns1)创建自签证书:
[root@ns1 ~]# cd /etc/pki/CA/ [root@ns1 CA]# pwd /etc/pki/CA [root@ns1 CA]# (umask 077; openssl genrsa -out private/cakey.pem 2048) # openssl生成私钥 Generating RSA private key, 2048 bit long modulus ............................+++ .........................+++ e is 65537 (0x10001) [root@ns1 CA]# ls certs crl newcerts private [root@ns1 CA]# ll private/ # 查看私钥 total 4 -rw-------. 1 root root 1675 Jul 20 22:39 cakey.pem [root@ns1 CA]# vi ../tls/openssl.cnf # 查看并修改openssl配置文件 ... # Extra OBJECT IDENTIFIER info: # 使用到的文件及目录 #oid_file = $ENV::HOME/.oid oid_section = new_oids # several ctificates with same subject. new_certs_dir = $dir/newcerts # default place for new certs. certificate = $dir/cacert.pem # The CA certificate serial = $dir/serial # The current serial number # must be commented out to leave a V1 CRL crl = $dir/crl.pem # The current CRL private_key = $dir/private/cakey.pem# The private key RANDFILE = $dir/private/.rand # private random number file x509_extensions = usr_cert # The extentions to add to the cert ... [ req_distinguished_name ] # 修改默认注册信息 countryName_default = CN stateOrProvinceName_default = Shanghai localityName_default = Shanghai 0.organizationName_default = STEPHENZHOU organizationalUnitName_default = Tech [root@ns1 CA]# openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 3650 # 生成自签证书 You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [CN]: State or Province Name (full name) [Shanghai]: Locality Name (eg, city) [Shanghai]: Organization Name (eg, company) [STEPHENZHOU]: Organizational Unit Name (eg, section) [Tech]: Common Name (eg, your name or your server's hostname) []:ca.stephenzhou.net Email Address []:[email protected] [root@ns1 CA]# ls # 查看生成好的自签证书cacert.pem cacert.pem certs crl newcerts private [root@ns1 CA]# touch index.txt # 创建证书索引/数据库 [root@ns1 CA]# echo 01 > serial # 创建版本文件 [root@ns1 CA]# ls cacert.pem certs crl index.txt newcerts private serial
2. 网页服务器(RS01)生成证书签名请求:
[root@RS01 CA]# cat /etc/httpd/conf.d/virtual.conf NameVirtualHost 192.168.2.119:80 <VirtualHost 192.168.2.19:80> ServerName testssl.stephenzhou.net # 将要绑定的主机名 DocumentRoot "/www/stephenzhou.net" CustomLog /var/log/httpd/stephenzhou.net/access_log combined </VirtualHost> [root@RS01 httpd]# mkdir ssl/ [root@RS01 httpd]# cd ssl/ [root@RS01 ssl]# (umask 077; openssl genrsa 1024 > httpd.key) # 生成私钥 Generating RSA private key, 1024 bit long modulus ..........++++++ .....................++++++ e is 65537 (0x10001) [root@RS01 ssl]# ll total 4 -rw-------. 1 root root 887 Jul 9 18:19 httpd.key [root@RS01 ssl]# openssl req -new -key httpd.key -out httpd.csr # 生成证书签名请求文件 You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:CN State or Province Name (full name) []:Shanghai Locality Name (eg, city) [Default City]:Shanghai Organization Name (eg, company) [Default Company Ltd]:STEPHENZHOU Organizational Unit Name (eg, section) []:Tech Common Name (eg, your name or your server's hostname) []:testssl.stephenzhou.net Email Address []: Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []: [root@RS01 ssl]# ls httpd.csr httpd.key [root@RS01 ssl]# scp httpd.csr 192.168.2.41:/tmp/ # 文件传输给CA服务器
3.CA签发证书:
[root@ns1 tmp]# openssl ca -in /tmp/httpd.csr -out /tmp/httpd.crt -days 3650 # 签发证书 Using configuration from /etc/pki/tls/openssl.cnf Check that the request matches the signature Signature ok Certificate Details: Serial Number: 2 (0x2) Validity Not Before: Jul 20 15:50:28 2014 GMT Not After : Jul 17 15:50:28 2024 GMT Subject: countryName = CN stateOrProvinceName = Shanghai organizationName = STEPHENZHOU organizationalUnitName = Tech commonName = testssl.stephenzhou.net X509v3 extensions: X509v3 Basic Constraints: CA:FALSE Netscape Comment: OpenSSL Generated Certificate X509v3 Subject Key Identifier: 72:70:AF:2B:7F:D0:36:A4:A2:5B:1F:9E:33:8B:E7:ED:91:A6:86:CF X509v3 Authority Key Identifier: keyid:AC:92:92:AC:37:F9:C3:2B:09:5A:8D:2F:3C:E5:36:CC:9F:B8:41:F7 Certificate is to be certified until Jul 17 15:50:28 2024 GMT (3650 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated [root@ns1 tmp]# cd /etc/pki/CA/ [root@ns1 CA]# ls cacert.pem certs crl index.txt index.txt.attr index.txt.attr.old index.txt.old newcerts private serial serial.old [root@ns1 CA]# cat index.txt # 查看证书索引/数据库 V 240717150933Z 01 unknown /C=CN/ST=Shanghai/O=STEPHENZHOU/OU=Tech/CN=hello.stephenzhou.net/[email protected] V 240717155028Z 02 unknown /C=CN/ST=Shanghai/O=STEPHENZHOU/OU=Tech/CN=testssl.stephenzhou.net [root@ns1 CA]# cat serial # 查看版本号 03 [root@ns1 CA]# cd newcerts/ # 查看新生成的证书 [root@ns1 newcerts]# ls 01.pem 02.pem [root@ns1 newcerts]# cd /tmp/ [root@ns1 tmp]# ls httpd.crt httpd.csr querytest [root@ns1 tmp]# rm httpd.c* -f # 删除临时证书文件、防止他人盗用
4.网页服务器绑定证书:
[root@RS01 ssl]# scp 192.168.2.41:/tmp/httpd.crt ./ # 复制CA签发完成的证书 [root@RS01 ssl]# ls # 确认拷贝完成 httpd.crt httpd.csr httpd.key [root@RS01 conf.d]# yum -y install mod_ssl # 为apache安装ssl模块(此步也可在配置之初完成) [root@RS01 conf.d]# rpm -ql mod_ssl|less # 查看安装生成的文件 /etc/httpd/conf.d/ssl.conf /usr/lib64/httpd/modules/mod_ssl.so /var/cache/mod_ssl /var/cache/mod_ssl/scache.dir /var/cache/mod_ssl/scache.pag /var/cache/mod_ssl/scache.sem [root@RS01 conf.d]# ls README manual.conf php.conf ssl.conf virtual.conf welcome.conf.bak [root@RS01 ssl]# vi ../conf.d/ssl.conf # 修改ssl配置文件 ... <VirtualHost 192.168.2.19:443> ServerName testssl.stephenzhou.net DocumentRoot "/www/stephenzhou.net" SSLCertificateFile /etc/httpd/ssl/httpd.crt SSLCertificateKeyFile /etc/httpd/ssl/httpd.key [root@RS01 conf.d]# httpd -t # 语法错误检查 httpd: Could not reliably determine the server's fully qualified domain name, using RS01.stephenzhou.net for ServerName Syntax OK [root@RS01 conf.d]# service httpd start Starting httpd: httpd: Could not reliably determine the server's fully qualified domain name, using RS01.stephenzhou.net for ServerName [ OK ] [root@RS01 conf.d]# netstat -tnlp Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name ... tcp 0 0 :::443 :::* LISTEN 36190/httpd
5.下载CA证书到客户端,并安装到本地浏览器:
[root@ns1 tmp]# cd /etc/pki/CA/ # 登录CA服务器 [root@ns1 CA]# ls cacert.pem certs crl index.txt index.txt.attr index.txt.attr.old index.txt.old newcerts private serial serial.old [root@ns1 CA]# sz cacert.pem # 上传根证书文件(cacert.pem)到客户端 rz Starting zmodem transfer. Press Ctrl+C to cancel. Transferring cacert.pem... 100% 1 KB 1 KB/sec 00:00:01 0 Errors
注意取到的证书是pem后缀,需要修改成crt后缀:
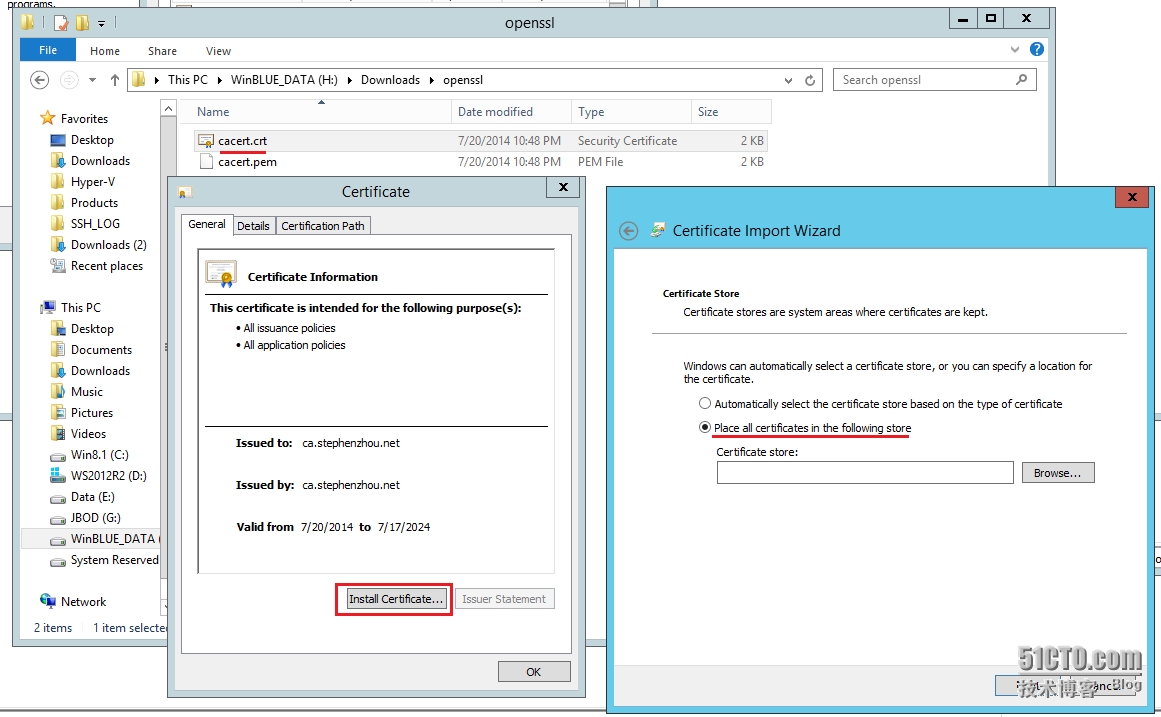
安装到第二项‘受信任的根证书。。。’:

安装完成后,在浏览器中可查看该证书已安装完成:

HOSTS文件绑定主机名与IP地址:
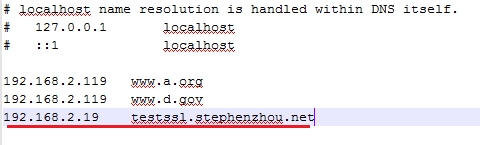
浏览器访问主机(https://testssl.stephenzhou.net):
