CCNP实验四:EIGRP认证
1. EIGRP认证
1.1. EIGRP认证原理概述
EIGRP
启用认证,用于防止恶意路由进入
EIGRP
自治系统导致路由攻击。
EIGRP
认证原理采用“密码比对”的形式,在接口受到
EIGRP
数据包后,检查认证类型、认证密码等字段,如果与本地接口定义的密码串匹配,那么接收该数据包,否则丢弃。
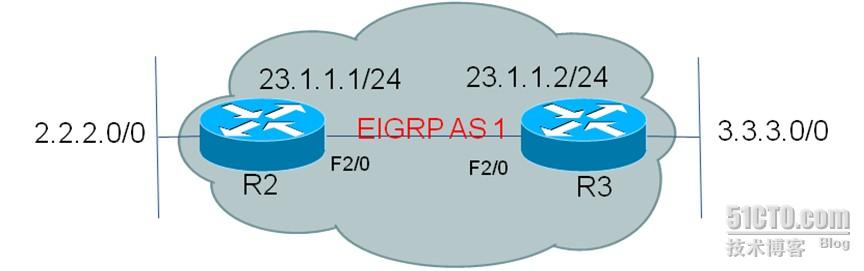
1.2. EIGRP认证实验拓扑
说明:
R2
与
R3
同处于
AS 1
,都使用
f2/0
连接,并都使用
lo 1
作测试使用。
1.3. 实验过程
1.3.1. 连通性、EIGRP基本配置
R2
、
R3
按照拓扑配置
IP
、
EIGRP
。
R2
接口
R2#sh ip int b
Interface IP-Address OK? Method Status Protocol
FastEthernet0/0 unassigned YES unset administratively down down
FastEthernet0/1 unassigned YES unset administratively down down
FastEthernet1/0 unassigned YES unset administratively down down
FastEthernet2/0 23.1.1.2 YES manual up up
FastEthernet3/0 unassigned YES unset administratively down down
FastEthernet4/0 unassigned YES unset administratively down down
Loopback1 2.2.2.2 YES manual up up
R3
接口
R3#sh ip int b
Interface IP-Address OK? Method Status Protocol
FastEthernet0/0 unassigned YES unset administratively down down
FastEthernet1/0 unassigned YES unset administratively down down
FastEthernet2/0 23.1.1.3 YES manual up up
FastEthernet3/0 unassigned YES unset administratively down down
FastEthernet4/0 unassigned YES unset administratively down down
Loopback1 3.3.3.3 YES manual up up
R2
路由表
R2#sh ip route
Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
Gateway of last resort is not set
2.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 2.2.2.0/24 is directly connected, Loopback1
D 2.0.0.0/8 is a summary, 00:00:13, Null0
D 3.0.0.0/8 [90/156160] via 23.1.1.3, 00:00:13, FastEthernet2/0
23.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 23.1.1.0/24 is directly connected, FastEthernet2/0
D 23.0.0.0/8 is a summary, 00:00:13, Null0
R3
路由表
R3#sh ip route
*May 12 16:15:02.719: %SYS-5-CONFIG_I: Configured from console by console
Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
Gateway of last resort is not set
D 2.0.0.0/8 [90/156160] via 23.1.1.2, 00:00:36, FastEthernet2/0
3.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 3.3.3.0/24 is directly connected, Loopback1
D 3.0.0.0/8 is a summary, 00:00:06, Null0
23.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 23.1.1.0/24 is directly connected, FastEthernet2/0
D 23.0.0.0/8 is a summary, 00:00:06, Null0
1.4. 配置EIGRP认证
1.4.1. EIGRP认证
R3
配置
R3(config)#key chain wolfbeing
R3(config-keychain)#key 1
R3(config-keychain-key)#key-string cisco
R3(config)#int f2/0
R3(config-if)#ip authentication key-chain eigrp 1 wolfbeing
//
命令输入后,出现提示说因为密码串启用导致邻居
down
了,然后再提示说该邻居又
up
起来了
*May 12 16:17:26.543: %DUAL-5-NBRCHANGE: IP-EIGRP(0) 1: Neighbor 23.1.1.2 (FastEthernet2/0) is down: keychain changed
*May 12 16:17:26.995: %DUAL-5-NBRCHANGE: IP-EIGRP(0) 1: Neighbor 23.1.1.2 (FastEthernet2/0) is up: new adjacency
R2
不启用认证
查看
R2 EIGRP
邻居表
R2#sh ip ei neighbors
IP-EIGRP neighbors for process 1
H Address Interface Hold Uptime SRTT RTO Q Seq
(sec) (ms) Cnt Num
0 23.1.1.3 Fa2/0 14 00:00:18 110 660 0 17
两台路由器之间的邻居关系依然建立
这时我们再将
R3
的
EIGRP
认证设为
MD5
加密
R3(config-if)#ip authentication mode eigrp 1 md5
这时
R3
路由器提示认证方式已经修改。
*May 12 16:29:56.331: %DUAL-5-NBRCHANGE: IP-EIGRP(0) 1: Neighbor 23.1.1.2 (FastEthernet2/0) is down: authentication mode changed
我们再来查看
R2
情况
R2
出现以下提示,说认证失败,因为我们已经将
R3 EIGRP
认证启用,但是
R2
并没有启用认证。
*May 12 16:41:55.407: %DUAL-5-NBRCHANGE: IP-EIGRP(0) 1: Neighbor 23.1.1.3 (FastEthernet2/0) is down: Auth failure
R2
邻居包这时也因为发出
HELLO
包后,没能收到对方的
HELLO
,所有没能建立邻居关系,导致邻居表为空。
R2
启用
EIGRP
认证
R2(config)#key chain itc
R2(config-keychain)#key 1
R2(config-keychain-key)#key-string wolfbeing
//
这时我们使用错误的密码
R2(config-if)#ip authentication mode eigrp 1 md5
这时我们在
R3
上打开
bebug eigrp packet ,
查看
EIGRP
数据包情况。
接收
Hello
包时,本地接口的判断
*May 12 16:47:22.575: EIGRP: Received HELLO on Loopback1 nbr 3.3.3.3
*May 12 16:47:22.579: AS 1, Flags 0x0, Seq 0/0 idbQ 0/0
*May 12 16:47:22.579: EIGRP: Packet from ourselves ignored
*May 12 16:47:22.703: EIGRP: pkt key id = 1, authentication mismatch//
可以看出
R3
使用密码串中的第一个密码进行匹配
*May 12 16:47:22.703: EIGRP: FastEthernet2/0: ignored packet from 23.1.1.2, opcode = 5 (invalid authentication)
发出
hello
包时,对方接口的判断
*May 12 16:47:25.487: EIGRP: Sending HELLO on FastEthernet2/0
*May 12 16:47:25.487: AS 1, Flags 0x0, Seq 0/0 idbQ 0/0 iidbQ un/rely 0/0
*May 12 16:47:27.503: EIGRP: pkt key id = 1, authentication mismatch//
可以看出
R3
使用密码串中的第一个密码进行匹配
*May 12 16:47:27.507: EIGRP: FastEthernet2/0: ignored packet from 23.1.1.2, opcode = 5 (invalid authentication)
发送和接收都出现认证不匹配,说明
EIGRP
认证是在接口下接收
Hello
包时进行检查的。
我们这时再将
R2
的密码改为正确的
”wolfbeing”
。
R2(config)#key chain itc
R2(config-keychain)#key 1
R2(config-keychain-key)#key-string cisco
//
重新修改为
cisco
这时我们查看
R3
路由器,可以看到
*May 12 16:47:59.967: %DUAL-5-NBRCHANGE: IP-EIGRP(0) 1: Neighbor 23.1.1.2 (FastEthernet2/0) is up: new adjacency//
邻居关系建立
R3
上邻居表为
R3#sh ip ei neighbors
IP-EIGRP neighbors for process 1
H Address Interface Hold Uptime SRTT RTO Q Seq
(sec) (ms) Cnt Num
0 23.1.1.2 Fa2/0 11 02:35:25 132 792 0 20
这时
EIGRP
认证实验完成
1.5. 结言
通过以上配置,我们可以得知配置
EIGRP
有以下注意事项:
一、
EIGRP
使用时密码串作为验证密码,我们需要定义并指定正确的密码串。
二、
在
Cisco IOS 11.3
之后
EIGRP
只支持
MD5
认证,如果不使用
ip authentication mode eigrp 100 md5
命令,认证默认不起作用。
三、
EIGRP
认证是基于接口下对接收到的
Hello
包进行验证。