OSPF实验:OSPF认证完整总结1
OSPF实验:OSPF认证完整总结1
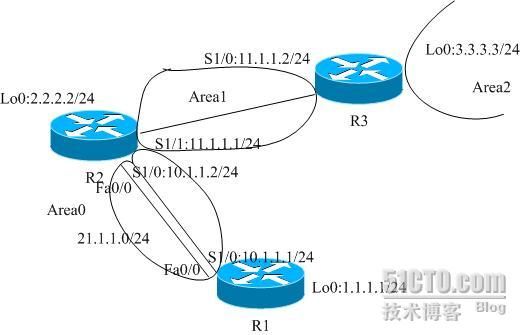
实验说明:
OSPF
的认证有
2
种类型(确切说是
3
种),其中
type0
表示无认证,
type1
表示明文认证,
type2
表示
MD5
认证。明文认证发送密码进行认证,而
MD5
认证发送的是报文摘要。
有关
MD5
的详细信息,可以参阅
RFC1321.
OSPF
的认证可以在链路上进行,也可以在整个区域内进行认证。另外虚链路同样也可以进行认证。
实验基本配置:
R1:
interface Loopback0
ip address 1.1.1.1 255.255.255.0
!
interface FastEthernet0/0
ip address 21.1.1.1 255.255.255.0
duplex half
!
router ospf 10
router-id 1.1.1.1
log-adjacency-changes
network 10.1.1.0 0.0.0.255 area 0
network 21.1.1.0 0.0.0.255 area 0
R2
:
interface Loopback0
ip address 2.2.2.2 255.255.255.0
!
interface FastEthernet0/0
ip address 21.1.1.2 255.255.255.0
duplex half
!
interface Serial1/0
ip address 10.1.1.2 255.255.255.0
serial restart-delay 0
!
interface Serial1/1
ip address 11.1.1.1 255.255.255.0
serial restart-delay 0
!
router ospf 10
router-id 2.2.2.2
log-adjacency-changes
area 1 virtual-link 3.3.3.3
network 10.1.1.0 0.0.0.255 area 0
network 11.1.1.0 0.0.0.255 area 1
network 21.1.1.0 0.0.0.255 area 0
R3
:
interface Loopback0
ip address 3.3.3.3 255.255.255.0
!
interface Serial1/0
ip address 11.1.1.2 255.255.255.0
serial restart-delay 0
!
router ospf 10
router-id 3.3.3.3
log-adjacency-changes
area 1 virtual-link 2.2.2.2
network 3.3.3.0 0.0.0.255 area 2
network 11.1.1.0 0.0.0.255 area 1
认证配置:
1.
在
R1
和
R2
的串行链路上进行
OSPF
明文认证:
首先先在
R1
上做如下配置,看在
R1
配置完认证,
R2
还没有配置认证的时候的情况:
R1(config)#int s1/0
R1(config-if)#ip ospf authentication
(启用认证)
R1(config-if)#ip ospf authentication-key cisco
(配置密码)
通过
debug
工具我们可以看到如下信息:
*Aug 15 22:51:54.275: OSPF: Rcv pkt from 10.1.1.2, Serial1/0 : Mismatch Authentication type. Input packet specified type 0, we use type 1
这里的
type0
是指对方没有启用认证,
type1
是明文认证。
在
R2
上配置认证,使得邻居关系恢复。
R2(config)#int s1/0
R2(config-if)#ip ospf authentication
R2(config-if)#ip ospf authentication-key cisco
*Aug 15 22:54:55.815: %OSPF-5-ADJCHG: Process 10, Nbr 1.1.1.1 on Serial1/0 from LOADING to FULL, Loading Done
2.
在
R2
和
R3
的串行链路上进行
MD5
认证的:
R2(config)#int s1/1
R2(config-if)#ip ospf authentication message-digest
(定义认证类型为MD5
)
R2(config-if)#ip ospf message-digest-key 1 md5 cisco
(定义key
和密码)
R3(config)#int s1/0
R3(config-if)#ip ospf authentication message-digest
R3(config-if)#ip ospf message-digest-key 1 md5 cisco
R3(config-if)#
*Aug 15 22:59:44.175: %OSPF-5-ADJCHG: Process 10, Nbr 2.2.2.2 on Serial1/0 from LOADING to FULL, Loading Done
R3#show ip ospf int s1/0
Serial1/0 is up, line protocol is up
Internet Address 11.1.1.2/24, Area 1
Process ID 10, Router ID 3.3.3.3, Network Type POINT_TO_POINT, Cost: 64
Transmit Delay is 1 sec, State POINT_TO_POINT,
Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5
oob-resync timeout 40
Hello due in 00:00:05
Index 1/1, flood queue length 1
Next 0x648352C8(13)/0x0(0)
Last flood scan length is 1, maximum is 2
Last flood scan time is 0 msec, maximum is 0 msec
Flood pacing timer due in 0 msec
Neighbor Count is 1, Adjacent neighbor count is 1
Adjacent with neighbor 2.2.2.2
Suppress hello for 0 neighbor(s)
Message digest authentication enabled
Youngest key id is 1
3.
修改
R2
和
R3
上串行链路的
MD5
认证的密码:
在
R2
原有的配置上加上下面这条命令:
R2(config-if)#ip ospf message-digest-key 2 md5 gairuhe
R2#sho ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
3.3.3.3 0 FULL/ - - 11.1.1.2 OSPF_VL0
1.1.1.1 1 FULL/BDR 00:00:34 21.1.1.1 FastEthernet0/0
1.1.1.1 0 FULL/ - 00:00:37 10.1.1.1 Serial1/0
3.3.3.3 0 FULL/ - 00:00:31 11.1.1.2 Serial1/1
我们发现邻居关系没有丢失。
R2#show ip ospf interface s1/1
Serial1/1 is up, line protocol is up
Internet Address 11.1.1.1/24, Area 1
Process ID 10, Router ID 2.2.2.2, Network Type POINT_TO_POINT, Cost: 64
Transmit Delay is 1 sec, State POINT_TO_POINT,
Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5
oob-resync timeout 40
Hello due in 00:00:01
Index 1/3, flood queue length 0
Next 0x0(0)/0x0(0)
Last flood scan length is 1, maximum is 1
Last flood scan time is 4 msec, maximum is 4 msec
Neighbor Count is 1, Adjacent neighbor count is 1
Adjacent with neighbor 3.3.3.3
Suppress hello for 0 neighbor(s)
Message digest authentication enabled
Youngest key id is 2
Rollover in progress, 1 neighbor(s) using the old key(s):
key id 1
这里我们可以看到两个
key
都在使用。
所以要修改链路的
MD5
认证的密码时,可以先将新的密码配置到启用认证的路由器后在将原来的密码删除,这样的话可以保证在修改配置的时候邻居关系依然存在。