IPsec-Tools配置之racoon
IPsec-Tools配置之racoon 收藏
IPsec-Tools中的racoon工具实现了IKE的功能,既实现了双向认证,又能建立和维护IPsec SA。下面使用psk的认证方法配置racooon。
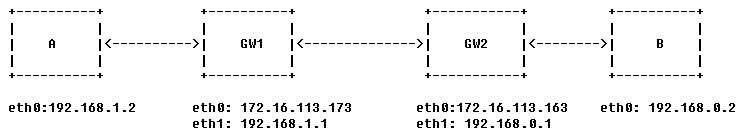
一、网络拓扑
二、配置网络
子网1: 192.168.1.0/24,网关GW1
子网2: 192.168.0.0/24,网关GW2
GW1和GW2已添加到子网2、1的路由。
A和B现在可正常ping 通
三、IPsec配置
1. 客户端A
(1) setkey.conf
[root@localhost ~]# cat /etc/setkey.conf
#flush SAD entries
flush;
#flush SPD entries
spdflush;
#add SA entries
#add SP entries
spdadd 192.168.0.0/24 192.168.1.0/24 any -P in ipsec esp/transport//require esp/transport//require;
spdadd 192.168.1.0/24 192.168.0.0/24 any -P out ipsec esp/transport//require esp/transport//require;
(2) psk.txt
[root@localhost ~]# cat /etc/racoon/psk.txt
192.168.0.2 0x123456
(3)racoon.conf
[root@localhost ~]# cat /etc/racoon/racoon.conf
# Racoon IKE daemon configuration file.
# See 'man racoon.conf' for a description of the format and entries.
path include "/etc/racoon";
path pre_shared_key "/etc/racoon/psk.txt";
path certificate "/etc/racoon/certs";
remote anonymous
{
exchange_mode main;
lifetime time 2 hour;
proposal {
encryption_algorithm 3des;
hash_algorithm sha1;
authentication_method pre_shared_key;
dh_group 2;
}
proposal {
encryption_algorithm aes;
hash_algorithm sha512;
authentication_method pre_shared_key;
dh_group modp2048;
}
}
sainfo anonymous
{
pfs_group 2;
lifetime time 1 hour ;
encryption_algorithm 3des, blowfish 448, rijndael ;
authentication_algorithm hmac_sha1, hmac_md5 ;
compression_algorithm deflate ;
}
2. 客户端B
(1)setkey.conf
[root@localhost ~]# cat /etc/setkey.conf
#flush SAD entries
flush;
#flush SPD entries
spdflush;
#add SA entries
#add SP entries
spdadd 192.168.1.0/24 192.168.0.0/24 any -P in ipsec esp/transport//require esp/transport//require;
spdadd 192.168.0.0/24 192.168.1.0/24 any -P out ipsec esp/transport//require esp/transport//require;
(2) psk.txt
[root@localhost ~]# cat /etc/racoon/psk.txt
192.168.1.2 0x123456
(3) racoon.conf
[root@localhost ~]# cat /etc/racoon/racoon.conf
# Racoon IKE daemon configuration file.
# See 'man racoon.conf' for a description of the format and entries.
path include "/etc/racoon";
path pre_shared_key "/etc/racoon/psk.txt";
path certificate "/etc/racoon/certs";
remote anonymous
{
exchange_mode main;
lifetime time 2 hour;
proposal {
encryption_algorithm 3des;
hash_algorithm sha1;
authentication_method pre_shared_key;
dh_group 2;
}
proposal {
encryption_algorithm aes;
hash_algorithm sha512;
authentication_method pre_shared_key;
dh_group modp2048;
}
}
sainfo anonymous
{
pfs_group 2;
lifetime time 1 hour ;
encryption_algorithm 3des, blowfish 448, rijndael ;
authentication_algorithm hmac_sha1, hmac_md5 ;
compression_algorithm deflate ;
}
四、测试
1.在客户A和B上分别激活setkey.conf和racoon.conf
#setkey –f /etc/setkey.conf
#setkey –f /etc/raccoon/racoon.conf
2. iptables设置
由于iptables会丢弃ESP数据包,ESP在经过GW1和GW2路由时会被丢弃,所以应配置iptables允许ESP数据包通过或简单disable掉iptables.
#service iptables stop
3.在B上ping A,抓包如下:

racoon使用psk认证方法配置成功!