IPSec配置命令及IPSec应用的ACL和NAT应用的ACL的比较
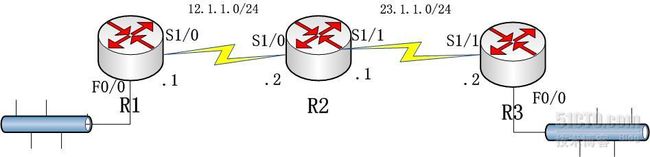
拓扑图:
R1:
int f0/0
ip add 1.1.1.1 255.255.255.0
int s1/0
ip add 12.1.1.1 255.255.255.0
no shut
配置ipsec
1配置crypto policy
crypto isakmp policy 10(自己定义的)
encryption 3des(选择加密算法)
authentication pre-share(选择认证方式)
2配置crypto key
crypto isakmp key 0(选择等级) mykey(密码) address 23.1.1.2(peer ip address) 255.255.255.0(netmask)
3.配置ipsec transform-set
crypto ipsec transform-set mytransformset(起个名字) esp-3des esp-md5-hmac
4.设置access-list
access-list 101 permit ip 1.1.1.0 0.0.0.255 3.3.3.0 0.0.0.255 (定义感兴趣的数据流)
5.设置crypto map
crypto map mymap(名字) 10(设置序列号) ipsec-isakmp
set peer 23.1.1.2
set transform-set mytransformset
match address 101(access-list number)
6.在接口下调用crypto map
int s1/0
crypto map mymap
R2:
int s1/0
ip add 12.1.1.2 255.255.255.0
no shut
int s1/1
ip add 23.1.1.1 255.255.255.0
no shut
R3:
int s1/1
ip add 23.1.1.2 255.255.255.0
no shut
int f0/0
ip add 3.3.3.3 255.255.255.0
crypto isakmp policy 10
encryption 3des
authentication pre-share
crypto isakmp key 0 mykey address 12.1.1.1 255.255.255.0
crypto ipsec transform-set mytransformset esp-3des esp-md5-hmac
access-list 100 permit ip 3.3.3.0 0.0.0.255 1.1.1.0 0.0.0.255
crypto map mymap 10 ipsec-isakmp
set peer 12.1.1.1
set transform-set mytransformset
match address 100
int s1/1
crypto map mymap
特别注意:当在同一个路由器上既定义了NAT的ACL又定义了ipsec的acl时,nat的acl优先与ipsec的acl,所以我们在定义nat的acl时应该拒绝ipsec定义的感兴趣的流量的acl
例如:
在R1上做nat时应该这样做
access-list 101 deny ip 1.1.1.0 0.0.0.255 3.3.3.0 0.0.0.255
access-list 101 permit ip any any
int f0/0
ip nat inside
int s1/0
ip nat outside
ip nat inside source list 101 interface s1/0
如果不拒绝IPSec定义的感兴趣的数据流,ipsec就无法正常使用