Spoofing the ARP Table of Remote Computers on a LAN
http://www.codeproject.com/Articles/6579/Spoofing-the-ARP-Table-of-Remote-Computers-on-a-LA
- Download source files - 28 Kb
- Download demo project - 127 Kb
1. Introduction
1.1 What is ARP spoofing?
ARP spoofing, also called ARP Cache poisoning, is one of the hacking methods to spoof the contents of an ARP table on a remote computer on the LAN. Two addresses are needed for one computer to connect to other computer on an IP/Ether network. One address is the MAC address; the other is the IP address. A MAC address is used on a local area network before packets go out of the gateway; an IP address is used to surf the Internet through a gateway. There is a protocol that asks "who has this MAC address" and answers the question; that is called ARP (Address Resolution Protocol). What the ARP asks the target address for sending is called the ARP Request or ARP who has, and the ARP that responds to the request is called the ARP Request or ARP who has. Although wrong information is inserted into ARP, the computer believes that the information of the ARP is valid and saves the information in own ARP table for a while. This is ARP spoofing.
Fig 1 ARP Spoofing
1.2 WinArpSpoofer Program
WinArpSpoofer is a program to manipulate the ARP table of another computer on a LAN. Especially, by changing the ARP table of a router, this program can in effect pull all packets on the local area network. After pulling and collecting all packets, this has a function that can forward them to the router(gateway). If you run this program and any sniffer program, you can even get and see all user ids/passwords on the switch network. This program needs the WinPcap driver and has been tested on WinNT/2000/XP/2003 etc.
1.3 CBuildPacket Class
CBuildPacket is a class that builds a WinArpSpoofer program. Its general purpose is to easily build a cooked packet throwing into the network. It is hard to understand and use existing libnet libraries and so forth in MS Visual.NET, so I have newly designed this class.
The current version of the CBuildPacket class provides some methods for building and sending an ARP to the network. The future version of this class will provide many various types of network packets for building TCP, IP, icmp, and the like.
WinArpSpoofer has been built based on the current CBuildPacket class. It could pull and collect all packets without users' recognition. The current version, 0.1, has been built for spoofing ARP tables and actually forwarding packets, so we didn't consider a neat and convenient user interface. For the future, when upgrading, that point will be improved.
1.4 Features of WinArpSpoofer
Functions and features of the WinArpSpoofer program are as follows:
- It can pull and collect all the packets on the LAN.
- It can scan and show the active hosts on the LAN within a very short time (~1-2 seconds)
- While spoofing ARP tables, it can act as another gateway (or ip-forwarder) without other users' recognition on the LAN.
- It can collect and forward packets by selecting inbound, outbound, and both to be sent to the Internet.
- An ARP table is recovered automatically in a little time (about 30 seconds). But, this program can keep spoofing continuously with periodic time.
- Although one or more network interface cards are installed on a computer, this program can scan and spoof by selecting one of NICs.
Because most functions are processed through threads, this program is faster than you think. Spoofing itself doesn't allocate much CPU time. So, if there are many active hosts on the LAN, the problem related to CPU time will be different.
2. Environment
2.1 WinArpSpoofer
System environments using WinArpSpoofer are as follows:
- Local OS: All Windows platforms
- Remote OS: All computers and network devices having an ARP table
- Requisite driver: Current version must install WinPcap Driver (as recent as possible)
- Main Memory: 64 Mb or more
- HDD: Free space should be 10 Mb or more
We actually have tested this program on Windows NT/2000/XP/2003. I am not sure that Win 9x/ME can run this program. In addition, this program is later going to be used without the WinPcap driver.
2.2 CBuildPacket
To use the CBuildPacket class, the WinPcap driver is needed; the IPHlpApi library in the Platform SDK also is needed.
3. The Methods for Spoofing an ARP Table
3.1 Notations
A,B,a,b: Active computer entities on network. When programming, this means an Ethernet MAC address.
- Target: a target computer against spoofing attack
- Attacker: an attacker's computer
- aIP,bIP: IP address of A,B
- aMAC,bMAC: MAC address of A,B
- TargetMAC: MAC address of the target computer
- TargetIP: IP address of the target computer
- AttackerMAC: MAC address of the attacker
- AttackerIP: IP address of the attacker
- ARPrequest: A---> B with (aIP,aMAC,bIP,bMAC): In a ARP packet meaing "ARP who has", to put (IP address of ARP Source A, MAC address of ARP Source A, IP address of ARP Target b, MAC address of ARP Target b) and to transfer A to B
- ARPreply: A---> B with (aIP,aMAC,bIP,bMAC): a reponsive packet of ARPrequest
3.2 How to spoof an ARP table
- ARPrequest: Attacker ---> Target with (aIP, AttackerMAC, TargetIP,TargetMAC)
or
- ARPreply: Attacker ---> Target with (aIP, AttackerMAC, TargetIP,TargetMAC)
If you do as shown above, an ARPrequest with the wrong information is sent to a target computer and the the target computer knows that the MAC address of A is the Attacker's MAC addres in the ARP table. Therefore, all the packets that the target sends to A are sent to the Attacker.
ARPreply packets are used to keep ARP spoofing. Likewise, the target knows that the MAC address of A is the MAC address of the Attacker in an ARP table. Therefore, all the packets that Target sends to A are sent to Attacker.
3.3 How to recognize that there is the same IP address on the network
- ARPreply: Attacker ---> Target with (TargetIP, aMAC, TargetIP,TargetMAC)
or
- ARPrequest: Attacker ---> Target with (TargetIP, aMAC, TargetIP,TargetMAC)
If you do as above, a target computer recognizes that there is the same IP address on the local area network, so the target computer will show "collision of network ip address".
3.4 how to recover spoofing (Unspoofing)
- ARPreply: Attacker --->Target with (aIP, aMAC, TargetIP,TargetMAC)
If a correct ARPreply packet to the target is sent to the target as above, the spoofed ARP table should be recovered.
4. How to Use WinArpSpoofer
This section describes the installation and usage of the WinARpSpoofer program.
4.1 Software requirement
- To download the WinPcap Driver: http://winpcap.polito.it/
- To download WinArpSpoofer: http://www.nextsecurity.net/
4.2 Installation
- Install the WinPcap driver.
- Run WinArpSpoofer.
4.3 Using WinArpSpoofer
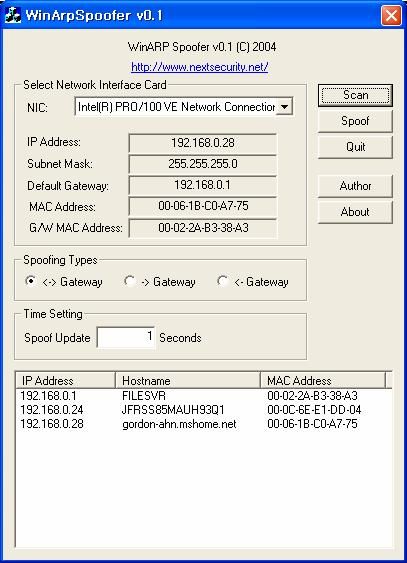
Figure 2 is the user interface of the WinArpSpoofer program; this section describes the function of the buttons as follows.
4.3.1 Function descriptions
Figure 2: WinArpSpoofer Screen Snapshot
| Button | Description |
| Scans the active computer hosts on the Local Area Network. It can scan C Class, 255 hosts at one time. By thread processing, the results are displayed on a ListBox in a short time (~1-2 seconds). After you click the scan button, you click the "Spoof" button. | |
| Spoofs the ARP tables of the computers displayed in the ListBox. As to the poisoning of the ARP cache against the remote computers, the MAC address of the gateway is changed to the attacker's MAC address. The method to prove this is to type "arp -a" on the target computer. This function has also the features that this program acts as a router while spoofing and pulling all the packets on the LAN. Because of this, although ARP spoofing happens on the LAN, Internet use of the target computer is no problem. While spoofing, the text of button shows "Unspoof". | |
| If the "Spoof" button is pressed, the text of the button will be changed to "Unspoof". While "Unspoof" is shown on the button, it keeps spoofing. The "Unspoof" function recovers the spoofed ARP table. Although the "Unspoof" function isn't run, most of ARP tables are recovered in a normal time (about 30 seconds). In addition, while "Unspoof" is shown, the "Scan" and "Quit" buttons can't be pressed. | |
| Quits the WinArpSpoofer program. | |
| Shows the author's name and e-mail address. | |
| Describes the features and the basic system requirements. | |
| As one of the spoofing types by default, intercepts and forwards all the packets to and from the gateway. | |
| As one of the spoofing types, intercepts and forwards all the packets to the gateway. | |
| As one of the spoofing types, intercepts all the packets from the gateway and forwards them to the target computer. |
5. Using the CBuildPacket Class
5.1 Overview
CBuildPacket is designed to send the built ARP, TCP, and ICMP packets to the network. There are many libraries or components such as Libnet and so forth on the Internet, but they have some weak points such as decreasing readability. I will open the source of CBuildPacket.
5.2 Member functions
OpenAdapter( ): Opens an adapter of the local computerBuildARP( ): Builds an ARP packetSendPacket( ): Sends the built packet to the networkCloseAdapter( ): Closes the opened adapterConvertMACStrToHex( ): Converts a string MAC address to a 6-byte MAC hexed value
5.2 ARP Spoofing code by using CBuildPacket
#include <packet32.h> #include <BuildPacket.h>
CString Target; // Ethernet Address of Target CString Attacker; // Ethernet Address of Attacker CString Gateway; // Ethernet Address of Gateway CString TargetIP; // IP Address of Target CString AttackerIP; // IP Address of Attacker CString GatewayIP; // IP Address of Gateway CString TargetMAC; // MAC Address of Target CString AttackerMAC; // MAC Address of Attacker CString GatewayMAC; // MAC Address of Gateway . . . void SpoofApp::SpoofTarget() { CBuildPacket *arpPacket = new CBuildPacket; arpPacket.OpenAdapter( AdapterName ); // To open an adapter arpPacket.BuildARP( // To build a ARP // packet Attacker, Target, ARPOP_REQUEST // for Transmission on // MAC layer GatewayIP, AttackerMAC, // Spoof IP address of // Gateway to // Attacker IP. TargetIP, TargetMAC // ); arpPacket.SendPacket(); // Send a packet to network arpPacket.CloseAdapter(); // To close the adapter }
5.3 Causing the same IP address to collide by using CBuildPacket
void SpoofApp::CollideTargetIP() { CBuildPacket *arpPacket = new CBuildPacket; arpPacket.OpenAdapter( AdapterName ); // To open an adapter arpPacket.BuildARP( // To build an ARP // packet Attacker, Target, ARPOP_REQUEST // for Transmission // on MAC layer TargetIP, AttackerMAC, // Collision because // source TargetIP is // dest TargetIP TargetIP, TargetMAC // ); arpPacket.SendPacket(); // Send a packet to network arpPacket.CloseAdapter(); // To close the adapter }
5.4 Unspoofing code by using CBuildPacket
void SpoofApp::UnspoofTarget () { CBuildPacket *arpPacket = new CBuildPacket; arpPacket.OpenAdapter( AdapterName ); // To open an adapter arpPacket.BuildARP( // To build a ARP packet Attacker, Target, ARPOP_REPLY // for Transmission on MAC // layer GatewayIP, GatewayMAC, // To recover spoofed ARP // Table TargetIP, TargetMAC // ); arpPacket.SendPacket(); // Send a packet to network arpPacket.CloseAdapter(); // To close the adapter }
6. Conclusion
This article has explained what ARP Spoof is and how to use WinArpSpoof based on CBuildPacket. The WinArpSpoof program is a strong Windows-based ARP spoofer program with GUI.
References
- http://www.nextsecurity.net/
- http://winpcap.polito.it/
- http://www.ietf.org/rfc/rfc0826.txt
License
This article has no explicit license attached to it but may contain usage terms in the article text or the download files themselves. If in doubt please contact the author via the discussion board below.
A list of licenses authors might use can be found here
About the Author
| Gorden Member |
I works at http://www.Softahead.com , This site provides Free Software Downloads and Pay-Per-Install Service . Can you exchange website link with us? You can submit yours to our resource page here |