Boom!!!计算机系统,从理解到爆炸,Bomblab
进入目录下
./bomb
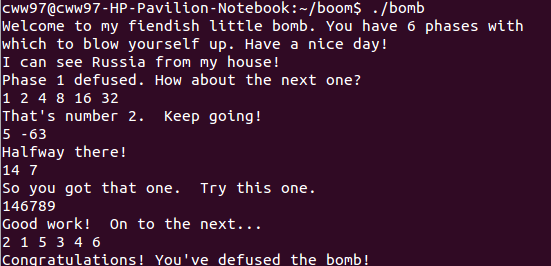
开始运行炸弹
对于炸弹command not found之类的鬼畜情况:
chmod 777 bomb
然后再运行炸弹
objdump -d bomb > bomb.s
把整个代码打到文件里去,也可以进gdb看
gdb>disas phase_1
看第一步的代码
我是bomb_217
第一步直接找按地址寻找字符串
0000000000400ead <phase_1>:
400ead: 48 83 ec 08 sub $0x8,%rsp
400eb1: be b0 23 40 00 mov $0x4023b0,%esi //字符串就存这,x/s 0x4023b0就出来了
//I can see Russia from my house!
400eb6: e8 5c 04 00 00 callq 401317 <strings_not_equal>
400ebb: 85 c0 test %eax,%eax
400ebd: 74 05 je 400ec4 <phase_1+0x17>
400ebf: e8 52 05 00 00 callq 401416 <explode_bomb>
400ec4: 48 83 c4 08 add $0x8,%rsp
400ec8: c3 retq 第二部,输入6个数,我这里是要求是以1开头,公比为2的等比数列
0000000000400ec9 <phase_2>:
400ec9: 55 push %rbp
400eca: 53 push %rbx
400ecb: 48 83 ec 28 sub $0x28,%rsp
400ecf: 64 48 8b 04 25 28 00 mov %fs:0x28,%rax
400ed6: 00 00
400ed8: 48 89 44 24 18 mov %rax,0x18(%rsp)
400edd: 31 c0 xor %eax,%eax
400edf: 48 89 e6 mov %rsp,%rsi
400ee2: e8 51 05 00 00 callq 401438 <read_six_numbers> //read 6 个数字
400ee7: 83 3c 24 01 cmpl $0x1,(%rsp)
400eeb: 74 05 je 400ef2 <phase_2+0x29> //if !=1,爆炸
400eed: e8 24 05 00 00 callq 401416 <explode_bomb>
400ef2: 48 89 e3 mov %rsp,%rbx
400ef5: 48 8d 6c 24 14 lea 0x14(%rsp),%rbp
400efa: 8b 03 mov (%rbx),%eax
400efc: 01 c0 add %eax,%eax //*2
400efe: 39 43 04 cmp %eax,0x4(%rbx) //不等则爆炸,,,猜,六个数,等比数列,get
400f01: 74 05 je 400f08 <phase_2+0x3f>
400f03: e8 0e 05 00 00 callq 401416 <explode_bomb>
400f08: 48 83 c3 04 add $0x4,%rbx
400f0c: 48 39 eb cmp %rbp,%rbx
400f0f: 75 e9 jne 400efa <phase_2+0x31>
400f11: 48 8b 44 24 18 mov 0x18(%rsp),%rax
400f16: 64 48 33 04 25 28 00 xor %fs:0x28,%rax
400f1d: 00 00
400f1f: 74 05 je 400f26 <phase_2+0x5d>
400f21: e8 fa fb ff ff callq 400b20 <__stack_chk_fail@plt>
400f26: 48 83 c4 28 add $0x28,%rsp
400f2a: 5b pop %rbx
400f2b: 5d pop %rbp
400f2c: c3 retq 第三部,
输 x/s 0x40258f 看到”%d %d”,说明输入格式是两个int
switch语句,rax越大要干的事越少,懒一点吧
有多组解。。。。
0000000000400f2d <phase_3>:
400f2d: 48 83 ec 18 sub $0x18,%rsp
400f31: 64 48 8b 04 25 28 00 mov %fs:0x28,%rax
400f38: 00 00
400f3a: 48 89 44 24 08 mov %rax,0x8(%rsp)
400f3f: 31 c0 xor %eax,%eax
400f41: 48 8d 4c 24 04 lea 0x4(%rsp),%rcx
400f46: 48 89 e2 mov %rsp,%rdx
400f49: be 8f 25 40 00 mov $0x40258f,%esi //x/s 0x40258f: "%d %d"
400f4e: e8 8d fc ff ff callq 400be0 <__isoc99_sscanf@plt>
400f53: 83 f8 01 cmp $0x1,%eax
400f56: 7f 05 jg 400f5d <phase_3+0x30>
400f58: e8 b9 04 00 00 callq 401416 <explode_bomb> //if (%eax<=1) 炸
400f5d: 83 3c 24 07 cmpl $0x7,(%rsp)
400f61: 77 5b ja 400fbe <phase_3+0x91> //if (%rsp>7) 炸
400f63: 8b 04 24 mov (%rsp),%eax
400f66: ff 24 c5 00 24 40 00 jmpq *0x402400(,%rax,8) //x/x 0x402400 0x6d %rax=0
//x/x 0x402408 0x74 %rax=1
//x/x 0x402410 0x80 %rax=2
//x/x 0x402418 0x8c %rax=3
//x/x 0x402420 0x96 %rax=4
//x/x 0x402428 0xa0 %rax=5
//x/x 0x402430 0xaa %rax=6 boom 见下面的!!!
//x/x 0x402438 0xb4 %rax=7 boom
400f6d: b8 7c 01 00 00 mov $0x17c,%eax
400f72: eb 05 jmp 400f79 <phase_3+0x4c>
400f74: b8 00 00 00 00 mov $0x0,%eax
400f79: 2d de 03 00 00 sub $0x3de,%eax
400f7e: eb 05 jmp 400f85 <phase_3+0x58>
400f80: b8 00 00 00 00 mov $0x0,%eax
400f85: 05 49 01 00 00 add $0x149,%eax
400f8a: eb 05 jmp 400f91 <phase_3+0x64>
400f8c: b8 00 00 00 00 mov $0x0,%eax
400f91: 83 e8 3f sub $0x3f,%eax
400f94: eb 05 jmp 400f9b <phase_3+0x6e>
400f96: b8 00 00 00 00 mov $0x0,%eax //%rax=4 太烦的事我都不太会做
400f9b: 83 c0 3f add $0x3f,%eax
400f9e: eb 05 jmp 400fa5 <phase_3+0x78>
400fa0: b8 00 00 00 00 mov $0x0,%eax //%rax=5 算出来是-0x3f=-63,get,懒惰即美德
400fa5: 83 e8 3f sub $0x3f,%eax
400fa8: eb 05 jmp 400faf <phase_3+0x82>
400faa: b8 00 00 00 00 mov $0x0,%eax
400faf: 83 c0 3f add $0x3f,%eax
400fb2: eb 05 jmp 400fb9 <phase_3+0x8c>
400fb4: b8 00 00 00 00 mov $0x0,%eax //%rax=7,不能太懒啊
400fb9: 83 e8 3f sub $0x3f,%eax
400fbc: eb 0a jmp 400fc8 <phase_3+0x9b>
400fbe: e8 53 04 00 00 callq 401416 <explode_bomb>
400fc3: b8 00 00 00 00 mov $0x0,%eax
400fc8: 83 3c 24 05 cmpl $0x5,(%rsp)
400fcc: 7f 06 jg 400fd4 <phase_3+0xa7> //>5,炸!!!
400fce: 3b 44 24 04 cmp 0x4(%rsp),%eax
400fd2: 74 05 je 400fd9 <phase_3+0xac>
400fd4: e8 3d 04 00 00 callq 401416 <explode_bomb> //与输入的不等,炸
400fd9: 48 8b 44 24 08 mov 0x8(%rsp),%rax
400fde: 64 48 33 04 25 28 00 xor %fs:0x28,%rax
400fe5: 00 00
400fe7: 74 05 je 400fee <phase_3+0xc1>
400fe9: e8 32 fb ff ff callq 400b20 <__stack_chk_fail@plt>
400fee: 48 83 c4 18 add $0x18,%rsp
400ff2: c3 retq 第四步,递归函数
偷了个懒,地柜函数没有认真看(其实是看哭了)
然后发现了数据很小
第一个数0xe之内,第二个数是7
我们可以用“爆炸穷举法”(自己yy的名字)
把答案搞出来就好了,(智障只能这么乱搞了)
0000000000400ff3 <func4>:
400ff3: 48 83 ec 08 sub $0x8,%rsp
400ff7: 89 d0 mov %edx,%eax
400ff9: 29 f0 sub %esi,%eax
400ffb: 89 c1 mov %eax,%ecx //qnmd递归函数看不懂
400ffd: c1 e9 1f shr $0x1f,%ecx
401000: 01 c8 add %ecx,%eax
401002: d1 f8 sar %eax
401004: 8d 0c 30 lea (%rax,%rsi,1),%ecx
401007: 39 f9 cmp %edi,%ecx
401009: 7e 0c jle 401017 <func4+0x24> //if (%ecx>=%edi)
40100b: 8d 51 ff lea -0x1(%rcx),%edx
40100e: e8 e0 ff ff ff callq 400ff3 <func4>
401013: 01 c0 add %eax,%eax
401015: eb 15 jmp 40102c <func4+0x39> //return
401017: b8 00 00 00 00 mov $0x0,%eax
40101c: 39 f9 cmp %edi,%ecx
40101e: 7d 0c jge 40102c <func4+0x39> // if (%ecx>=%edi)return
401020: 8d 71 01 lea 0x1(%rcx),%esi
401023: e8 cb ff ff ff callq 400ff3 <func4>
401028: 8d 44 00 01 lea 0x1(%rax,%rax,1),%eax
40102c: 48 83 c4 08 add $0x8,%rsp
401030: c3 retq
0000000000401031 <phase_4>:
401031: 48 83 ec 18 sub $0x18,%rsp
401035: 64 48 8b 04 25 28 00 mov %fs:0x28,%rax
40103c: 00 00
40103e: 48 89 44 24 08 mov %rax,0x8(%rsp)
401043: 31 c0 xor %eax,%eax //%eax=0
401045: 48 8d 4c 24 04 lea 0x4(%rsp),%rcx
40104a: 48 89 e2 mov %rsp,%rdx
40104d: be 8f 25 40 00 mov $0x40258f,%esi //x/s 40258f "%d %d"
401052: e8 89 fb ff ff callq 400be0 <__isoc99_sscanf@plt>
401057: 83 f8 02 cmp $0x2,%eax
40105a: 75 06 jne 401062 <phase_4+0x31>// %eax!=2,boom,读入数字数量!=2
40105c: 83 3c 24 0e cmpl $0xe,(%rsp)
401060: 76 05 jbe 401067 <phase_4+0x36> //(%rsp)>e,boom
401062: e8 af 03 00 00 callq 401416 <explode_bomb>
401067: ba 0e 00 00 00 mov $0xe,%edx
40106c: be 00 00 00 00 mov $0x0,%esi//第二个数字是7,第一个数字是e范围内的
401071: 8b 3c 24 mov (%rsp),%edi //穷举吧,哈哈,我懒
401074: e8 7a ff ff ff callq 400ff3 <func4> //14 7,妈的从0开始穷举,累死了
401079: 83 f8 07 cmp $0x7,%eax //%eax!=7,boom
40107c: 75 07 jne 401085 <phase_4+0x54>
40107e: 83 7c 24 04 07 cmpl $0x7,0x4(%rsp)
401083: 74 05 je 40108a <phase_4+0x59> //(%rsp)+4!=7,boom
401085: e8 8c 03 00 00 callq 401416 <explode_bomb>
40108a: 48 8b 44 24 08 mov 0x8(%rsp),%rax
40108f: 64 48 33 04 25 28 00 xor %fs:0x28,%rax
401096: 00 00
401098: 74 05 je 40109f <phase_4+0x6e>
40109a: e8 81 fa ff ff callq 400b20 <__stack_chk_fail@plt>
40109f: 48 83 c4 18 add $0x18,%rsp
4010a3: c3 retq 看到代码这么短,还没有递归
是不是感觉很简单的感觉。。。。
你们啊。NAIVE
恶心,恶心,恶心
输入一个长度为6的字符串
然后要求以其ascii码值最后一位的为*4的数组下标的那个元素,加起来=一个值(我这是2d)
是不是拗口的一笔???
看下面的注释吧,要看数组元素 ,x/x 0x402440@16 。。好像是这个,,忘了
下面有个for循环,就是取字符串每一位
根据看到的数组里面元素,把字符串凑出来就好了
00000000004010a4 <phase_5>:
4010a4: 53 push %rbx
4010a5: 48 89 fb mov %rdi,%rbx
4010a8: e8 4c 02 00 00 callq 4012f9 <string_length>
4010ad: 83 f8 06 cmp $0x6,%eax
4010b0: 74 05 je 4010b7 <phase_5+0x13> //%eax=6=length
4010b2: e8 5f 03 00 00 callq 401416 <explode_bomb>
4010b7: 48 89 d8 mov %rbx,%rax
4010ba: 48 8d 7b 06 lea 0x6(%rbx),%rdi
4010be: b9 00 00 00 00 mov $0x0,%ecx
4010c3: 0f b6 10 movzbl (%rax),%edx //for
4010c6: 83 e2 0f and $0xf,%edx//字符的16进制最后一位,对应下面的数组中元素(16进制)
4010c9: 03 0c 95 40 24 40 00 add 0x402440(,%rdx,4),%ecx //array={2,a,6,1,c,10,9,3,4,7,e,5,b,8,f,d}
4010d0: 48 83 c0 01 add $0x1,%rax
4010d4: 48 39 f8 cmp %rdi,%rax //rax=rdi break
4010d7: 75 ea jne 4010c3 <phase_5+0x1f> //endfor
4010d9: 83 f9 2d cmp $0x2d,%ecx //we need ecx=2d
4010dc: 74 05 je 4010e3 <phase_5+0x3f>
4010de: e8 33 03 00 00 callq 401416 <explode_bomb>
4010e3: 5b pop %rbx
4010e4: c3 retq 最后一步,,卧艹艹艹艹艹艹艹艹艹艹艹艹
怎么可以这么长!!!!!!
大体就是输入6个数,1到6范围,不重复
最后对应的数组元素递减(其实是链表辣,数组好理解一点是不是)
x/x 0x6032f0,,,数组就出来了
然后排序吧,
00000000004010a4 <phase_5>:
4010a4: 53 push %rbx
4010a5: 48 89 fb mov %rdi,%rbx
4010a8: e8 4c 02 00 00 callq 4012f9 <string_length>
4010ad: 83 f8 06 cmp $0x6,%eax
4010b0: 74 05 je 4010b7 <phase_5+0x13> //%eax=6=length
4010b2: e8 5f 03 00 00 callq 401416 <explode_bomb>
4010b7: 48 89 d8 mov %rbx,%rax
4010ba: 48 8d 7b 06 lea 0x6(%rbx),%rdi
4010be: b9 00 00 00 00 mov $0x0,%ecx
4010c3: 0f b6 10 movzbl (%rax),%edx //for
4010c6: 83 e2 0f and $0xf,%edx //字符的16进制最后一位,对应下面的数组中元素(16进制)
4010c9: 03 0c 95 40 24 40 00 add 0x402440(,%rdx,4),%ecx //array={2,a,6,1,c,10,9,3,4,7,e,5,b,8,f,d}
4010d0: 48 83 c0 01 add $0x1,%rax
4010d4: 48 39 f8 cmp %rdi,%rax //rax=rdi break
4010d7: 75 ea jne 4010c3 <phase_5+0x1f> //endfor
4010d9: 83 f9 2d cmp $0x2d,%ecx //we need ecx=2d
4010dc: 74 05 je 4010e3 <phase_5+0x3f>
4010de: e8 33 03 00 00 callq 401416 <explode_bomb>
4010e3: 5b pop %rbx
4010e4: c3 retq
00000000004010e5 <phase_6>:
4010e5: 41 55 push %r13
4010e7: 41 54 push %r12
4010e9: 55 push %rbp
4010ea: 53 push %rbx
4010eb: 48 83 ec 68 sub $0x68,%rsp
4010ef: 64 48 8b 04 25 28 00 mov %fs:0x28,%rax
4010f6: 00 00
4010f8: 48 89 44 24 58 mov %rax,0x58(%rsp)
4010fd: 31 c0 xor %eax,%eax
4010ff: 48 89 e6 mov %rsp,%rsi
401102: e8 31 03 00 00 callq 401438 <read_six_numbers> //6 nums
401107: 49 89 e4 mov %rsp,%r12
40110a: 41 bd 00 00 00 00 mov $0x0,%r13d
401110: 4c 89 e5 mov %r12,%rbp
401113: 41 8b 04 24 mov (%r12),%eax
401117: 83 e8 01 sub $0x1,%eax
40111a: 83 f8 05 cmp $0x5,%eax
40111d: 76 05 jbe 401124 <phase_6+0x3f>
40111f: e8 f2 02 00 00 callq 401416 <explode_bomb> //num!=6,boom
401124: 41 83 c5 01 add $0x1,%r13d
401128: 41 83 fd 06 cmp $0x6,%r13d
40112c: 74 3d je 40116b <phase_6+0x86>
40112e: 44 89 eb mov %r13d,%ebx
401131: 48 63 c3 movslq %ebx,%rax
401134: 8b 04 84 mov (%rsp,%rax,4),%eax
401137: 39 45 00 cmp %eax,0x0(%rbp)
40113a: 75 05 jne 401141 <phase_6+0x5c>
40113c: e8 d5 02 00 00 callq 401416 <explode_bomb> //>6,boom
401141: 83 c3 01 add $0x1,%ebx
401144: 83 fb 05 cmp $0x5,%ebx
401147: 7e e8 jle 401131 <phase_6+0x4c>
401149: 49 83 c4 04 add $0x4,%r12
40114d: eb c1 jmp 401110 <phase_6+0x2b>
40114f: 48 8b 52 08 mov 0x8(%rdx),%rdx
401153: 83 c0 01 add $0x1,%eax
401156: 39 c8 cmp %ecx,%eax
401158: 75 f5 jne 40114f <phase_6+0x6a>
40115a: 48 89 54 74 20 mov %rdx,0x20(%rsp,%rsi,2)
40115f: 48 83 c6 04 add $0x4,%rsi
401163: 48 83 fe 18 cmp $0x18,%rsi
401167: 75 07 jne 401170 <phase_6+0x8b>
401169: eb 19 jmp 401184 <phase_6+0x9f>
40116b: be 00 00 00 00 mov $0x0,%esi
401170: 8b 0c 34 mov (%rsp,%rsi,1),%ecx
401173: b8 01 00 00 00 mov $0x1,%eax
401178: ba f0 32 60 00 mov $0x6032f0,%edx //array
40117d: 83 f9 01 cmp $0x1,%ecx
401180: 7f cd jg 40114f <phase_6+0x6a>
401182: eb d6 jmp 40115a <phase_6+0x75>
401184: 48 8b 5c 24 20 mov 0x20(%rsp),%rbx
401189: 48 8d 44 24 20 lea 0x20(%rsp),%rax
40118e: 48 8d 74 24 48 lea 0x48(%rsp),%rsi
401193: 48 89 d9 mov %rbx,%rcx
401196: 48 8b 50 08 mov 0x8(%rax),%rdx
40119a: 48 89 51 08 mov %rdx,0x8(%rcx)
40119e: 48 83 c0 08 add $0x8,%rax
4011a2: 48 89 d1 mov %rdx,%rcx
4011a5: 48 39 f0 cmp %rsi,%rax
4011a8: 75 ec jne 401196 <phase_6+0xb1>
4011aa: 48 c7 42 08 00 00 00 movq $0x0,0x8(%rdx)
4011b1: 00
4011b2: bd 05 00 00 00 mov $0x5,%ebp
4011b7: 48 8b 43 08 mov 0x8(%rbx),%rax
4011bb: 8b 00 mov (%rax),%eax
4011bd: 39 03 cmp %eax,(%rbx)
4011bf: 7e 05 jle 4011c6 <phase_6+0xe1>
4011c1: e8 50 02 00 00 callq 401416 <explode_bomb> //若递增,boom
4011c6: 48 8b 5b 08 mov 0x8(%rbx),%rbx
4011ca: 83 ed 01 sub $0x1,%ebp
4011cd: 75 e8 jne 4011b7 <phase_6+0xd2>
4011cf: 48 8b 44 24 58 mov 0x58(%rsp),%rax
4011d4: 64 48 33 04 25 28 00 xor %fs:0x28,%rax
4011db: 00 00
4011dd: 74 05 je 4011e4 <phase_6+0xff>
4011df: e8 3c f9 ff ff callq 400b20 <__stack_chk_fail@plt>
4011e4: 48 83 c4 68 add $0x68,%rsp
4011e8: 5b pop %rbx
4011e9: 5d pop %rbp
4011ea: 41 5c pop %r12
4011ec: 41 5d pop %r13
4011ee: c3 retq 累死了,,,,
感谢LJL的支持