[置顶] 从僵尸网络追踪到入侵检测 第4章 Honeyd动态模板防御扫描软件攻击
Honeyd动态模板防御扫描软件攻击
环境准备
1、防御系统RHEL6.4 IP :10.10.10.135
2、攻击系统windows 2008 R2 IP: 10.10.10.134
3、扫描工具:SuperScan 4.0
步骤:
1、动态模板配置
[root@MIGUANG ~]# cat /etc/test.config
create default
set default default tcp action block
set default default udp action block
set default default icmp action block
create invisible
set invisible default tcp action block
set invisible default udp action block
set invisible default icmp action block
create linux
set linux personality "Linux 2.4.20"
set linux ethernet "dell"
set linux default tcp action reset
add linux tcp port 21 open
add linux tcp port 80 open
dhcp linux on eth0
##--动态模板
dynamic magichost
set magichost personality "FreeBSD 4.6"
##--指纹名称根据指纹库来定的这里是虚拟一个FreeBSD的操作系统
set magichost ethernet "dell"
##--给网卡取个名字
add magichost use invisible if source ip = 10.10.10.134
##--invisible if source ip 不让指定地址看到
add magichost otherwise use default
##--其他的default默认模板使用
dhcp magichost on eth0
2、运行Honeyd服务
[root@MIGUANG ~]# honeyd -d -f /etc/test.config
Honeyd V1.5c Copyright (c) 2002-2007 Niels Provos
honeyd[2715]: started with -d -f /etc/test.config
Warning: Impossible SI range in Class fingerprint "IBM OS/400 V4R2M0"
Warning: Impossible SI range in Class fingerprint "Microsoft Windows NT 4.0 SP3"
honeyd[2715]: listening promiscuously on eth0: (arp or ip proto 47 or (udp and src port 67 and dst port 68) or (ip )) and not ether src 00:0c:29:0b:cf:2a
honeyd[2715]: [eth0] trying DHCP
honeyd[2715]: [eth0] trying DHCP
honeyd[2715]: Demoting process privileges to uid 99, gid 99
honeyd[2715]: [eth0] got DHCP offer: 10.10.10.168
honeyd[2715]: Updating ARP binding: 00:c0:4f:6a:28:99 -> 10.10.10.168
honeyd[2715]: [eth0] got DHCP offer: 10.10.10.169
honeyd[2715]: Updating ARP binding: 00:c0:4f:b0:38:6e -> 10.10.10.169
honeyd[2715]: arp reply 10.10.10.169 is-at 00:c0:4f:b0:38:6e
3、攻击系统windows 2008 R2 使用工具进行扫描honeyd防御系统虚拟出来的IP
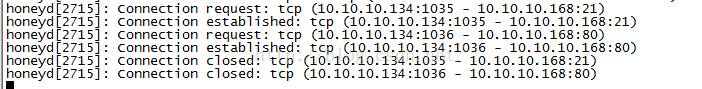
4、查看honeyd防御系统中的信息
![[置顶] 从僵尸网络追踪到入侵检测 第4章 Honeyd动态模板防御扫描软件攻击_第1张图片](http://img.e-com-net.com/image/info5/f6698213495f4a6a9656dd10e9adfb16.png)
![[置顶] 从僵尸网络追踪到入侵检测 第4章 Honeyd动态模板防御扫描软件攻击_第2张图片](http://img.e-com-net.com/image/info5/f68cda1ccc5842679c32c5338707ad52.png)
![[置顶] 从僵尸网络追踪到入侵检测 第4章 Honeyd动态模板防御扫描软件攻击_第3张图片](http://img.e-com-net.com/image/info5/9d3c9afb7df44b5385a656baffbcbc30.png)
![[置顶] 从僵尸网络追踪到入侵检测 第4章 Honeyd动态模板防御扫描软件攻击_第4张图片](http://img.e-com-net.com/image/info5/7ed3ee8e615f4df98b5ab52ae4dcc678.png)