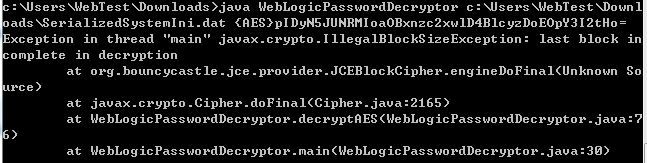
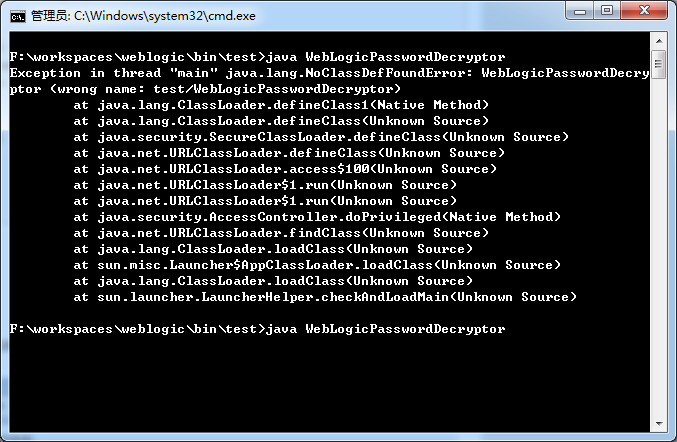
Weblogic解密脚本(无需weblogic环境)
关于解密weblogic AES或DES加密方法,在有weblogic环境下很容易,大家都会。之前有看到无需配置weblogic环境即可解密的文章,Zone里有的小伙伴说编译不通,跑不起来,昨天特意测试了一下,跟大家分享。
解密脚本WebLogicPasswordDecryptor.java
参见https://github.com/NetSPI/WebLogicPasswordDecryptor
直接编译一般会出错。
有两个注意点:
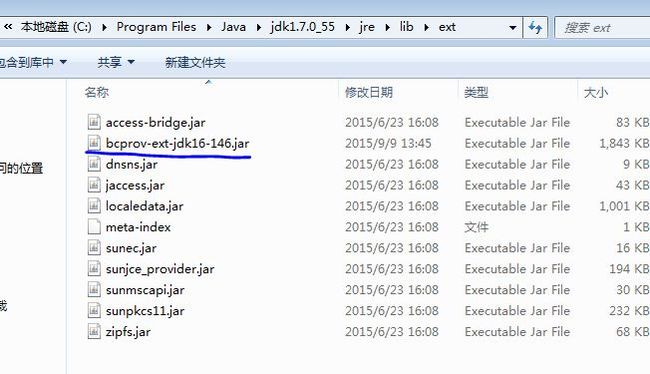
0x01
需要下载一个bcprov-ext-jdk16-146.jar包,拷贝到C:\Program Files\Java\jdk1.7.0_55\jre\lib\ext\
0x02
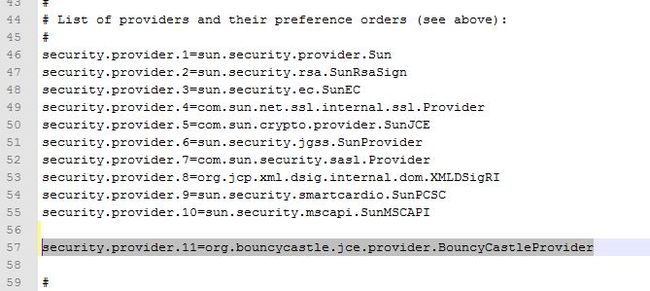
环境配置:修改C:\Program Files\Java\jdk1.7.0_55\jre\lib\security\java.security文件,增加一行
security.provider.11=org.bouncycastle.jce.provider.BouncyCastleProvider
这里为了形象直观,我用了eclipse编译,当然也可以用cmd命令行直接编译。
OK,编译无错误了。
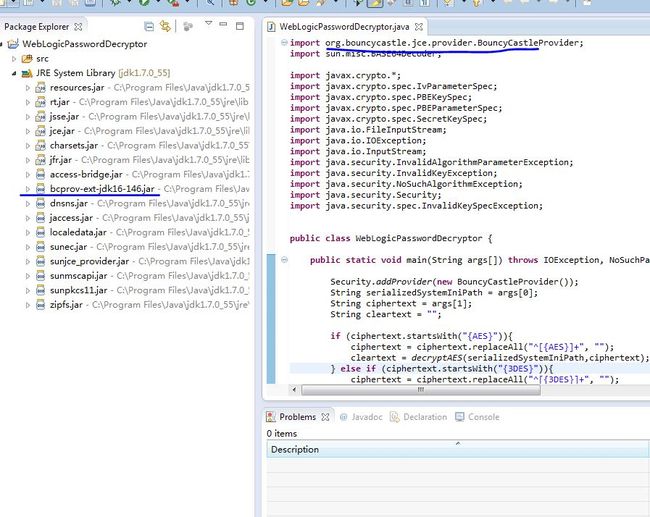
之后就可以直接用编译好的WebLogicPasswordDecryptor.class来解密了
用法:命令行下
解密脚本WebLogicPasswordDecryptor.java
参见https://github.com/NetSPI/WebLogicPasswordDecryptor
import org.bouncycastle.jce.provider.BouncyCastleProvider;
import sun.misc.BASE64Decoder;
import javax.crypto.*;
import javax.crypto.spec.IvParameterSpec;
import javax.crypto.spec.PBEKeySpec;
import javax.crypto.spec.PBEParameterSpec;
import javax.crypto.spec.SecretKeySpec;
import java.io.FileInputStream;
import java.io.IOException;
import java.io.InputStream;
import java.security.InvalidAlgorithmParameterException;
import java.security.InvalidKeyException;
import java.security.NoSuchAlgorithmException;
import java.security.Security;
import java.security.spec.InvalidKeySpecException;
public class WebLogicPasswordDecryptor {
public static void main(String args[]) throws IOException, NoSuchPaddingException, NoSuchAlgorithmException, InvalidKeyException, BadPaddingException, IllegalBlockSizeException, InvalidKeySpecException, InvalidAlgorithmParameterException {
Security.addProvider(new BouncyCastleProvider());
String serializedSystemIniPath = args[0];
String ciphertext = args[1];
String cleartext = "";
if (ciphertext.startsWith("{AES}")){
ciphertext = ciphertext.replaceAll("^[{AES}]+", "");
cleartext = decryptAES(serializedSystemIniPath,ciphertext);
} else if (ciphertext.startsWith("{3DES}")){
ciphertext = ciphertext.replaceAll("^[{3DES}]+", "");
cleartext = decrypt3DES(serializedSystemIniPath, ciphertext);
}
System.out.println(cleartext);
}
public static String decryptAES(String SerializedSystemIni, String ciphertext) throws NoSuchAlgorithmException, InvalidKeySpecException, NoSuchPaddingException, InvalidAlgorithmParameterException, InvalidKeyException, BadPaddingException, IllegalBlockSizeException, IOException {
byte[] encryptedPassword1 = new BASE64Decoder().decodeBuffer(ciphertext);
byte[] salt = null;
byte[] encryptionKey = null;
String key = "0xccb97558940b82637c8bec3c770f86fa3a391a56";
char password[] = new char[key.length()];
key.getChars(0, password.length, password, 0);
FileInputStream is = new FileInputStream(SerializedSystemIni);
try {
salt = readBytes(is);
int version = is.read();
if (version != -1) {
encryptionKey = readBytes(is);
if (version >= 2) {
encryptionKey = readBytes(is);
}
}
} catch (IOException e) {
}
SecretKeyFactory keyFactory = SecretKeyFactory.getInstance("PBEWITHSHAAND128BITRC2-CBC");
PBEKeySpec pbeKeySpec = new PBEKeySpec(password, salt, 5);
SecretKey secretKey = keyFactory.generateSecret(pbeKeySpec);
PBEParameterSpec pbeParameterSpec = new PBEParameterSpec(salt, 0);
Cipher cipher = Cipher.getInstance("PBEWITHSHAAND128BITRC2-CBC");
cipher.init(Cipher.DECRYPT_MODE, secretKey, pbeParameterSpec);
SecretKeySpec secretKeySpec = new SecretKeySpec(cipher.doFinal(encryptionKey), "AES");
byte[] iv = new byte[16];
System.arraycopy(encryptedPassword1, 0, iv, 0, 16);
int encryptedPasswordlength = encryptedPassword1.length - 16 ;
byte[] encryptedPassword2 = new byte[encryptedPasswordlength];
System.arraycopy(encryptedPassword1, 16, encryptedPassword2, 0, encryptedPasswordlength);
IvParameterSpec ivParameterSpec = new IvParameterSpec(iv);
Cipher outCipher = Cipher.getInstance("AES/CBC/PKCS5Padding");
outCipher.init(Cipher.DECRYPT_MODE, secretKeySpec, ivParameterSpec);
byte[] cleartext = outCipher.doFinal(encryptedPassword2);
return new String(cleartext, "UTF-8");
}
public static String decrypt3DES(String SerializedSystemIni, String ciphertext) throws NoSuchAlgorithmException, InvalidKeySpecException, NoSuchPaddingException, InvalidAlgorithmParameterException, InvalidKeyException, BadPaddingException, IllegalBlockSizeException, IOException {
byte[] encryptedPassword1 = new BASE64Decoder().decodeBuffer(ciphertext);
byte[] salt = null;
byte[] encryptionKey = null;
String PW = "0xccb97558940b82637c8bec3c770f86fa3a391a56";
char password[] = new char[PW.length()];
PW.getChars(0, password.length, password, 0);
FileInputStream is = new FileInputStream(SerializedSystemIni);
try {
salt = readBytes(is);
int version = is.read();
if (version != -1) {
encryptionKey = readBytes(is);
if (version >= 2) {
encryptionKey = readBytes(is);
}
}
} catch (IOException e) {
}
SecretKeyFactory keyFactory = SecretKeyFactory.getInstance("PBEWITHSHAAND128BITRC2-CBC");
PBEKeySpec pbeKeySpec = new PBEKeySpec(password, salt, 5);
SecretKey secretKey = keyFactory.generateSecret(pbeKeySpec);
PBEParameterSpec pbeParameterSpec = new PBEParameterSpec(salt, 0);
Cipher cipher = Cipher.getInstance("PBEWITHSHAAND128BITRC2-CBC");
cipher.init(Cipher.DECRYPT_MODE, secretKey, pbeParameterSpec);
SecretKeySpec secretKeySpec = new SecretKeySpec(cipher.doFinal(encryptionKey),"DESEDE");
byte[] iv = new byte[8];
System.arraycopy(salt, 0, iv, 0, 4);
System.arraycopy(salt, 0, iv, 4, 4);
IvParameterSpec ivParameterSpec = new IvParameterSpec(iv);
Cipher outCipher = Cipher.getInstance("DESEDE/CBC/PKCS5Padding");
outCipher.init(Cipher.DECRYPT_MODE, secretKeySpec, ivParameterSpec);
byte[] cleartext = outCipher.doFinal(encryptedPassword1);
return new String(cleartext, "UTF-8");
}
public static byte[] readBytes(InputStream stream) throws IOException {
int length = stream.read();
byte[] bytes = new byte[length];
int in = 0;
int justread;
while (in < length) {
justread = stream.read(bytes, in, length - in);
if (justread == -1) {
break;
}
in += justread;
}
return bytes;
}
}
直接编译一般会出错。
有两个注意点:
0x01
需要下载一个bcprov-ext-jdk16-146.jar包,拷贝到C:\Program Files\Java\jdk1.7.0_55\jre\lib\ext\

0x02
环境配置:修改C:\Program Files\Java\jdk1.7.0_55\jre\lib\security\java.security文件,增加一行
security.provider.11=org.bouncycastle.jce.provider.BouncyCastleProvider

这里为了形象直观,我用了eclipse编译,当然也可以用cmd命令行直接编译。
OK,编译无错误了。

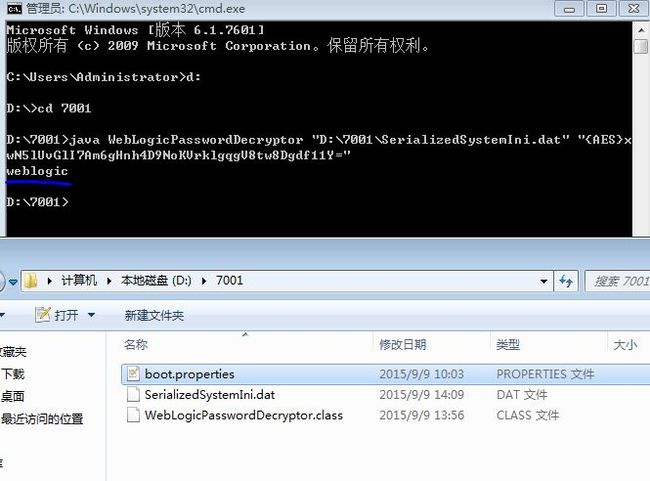
之后就可以直接用编译好的WebLogicPasswordDecryptor.class来解密了
用法:命令行下
Java WebLogicPasswordDecryptor "SerializedSystemIni.dat文件物理路径" "{AES}或{DES}加密内容"





![)J]9TW(Y[IF9U_9P({JAGWG.png](http://img.e-com-net.com/image/info5/a1d667087c0f4733ba448748a05984cf.png)