win64使用openssl生成ca证书
一、准备工作:
1、 下载win64的Openssl,可到http://slproweb.com/products/Win32OpenSSL.html下载,这里下载1.0.1j版本。同时在该地址下载Visual C++ 2008Redistributables (x64)。如下图:
先安装Visual C++ 2008Redistributables (x64),然后安装Win64 OpenSSL v1.0.1j。这里我安装到D:\OpenSSL-Win64\目录下。
2、 下载Openssl源码,去官网http://www.openssl.org/下载即可。如下图:
解压openssl-1.0.1j.tar.gz,找到\openssl-1.0.1j\apps目录,拷贝demoCA目录和openssl.cnf文件到Openssl的安装目录下的bin目录下(即D:\OpenSSL-Win64\bin\)。
3、在D:\OpenSSL-Win64\bin目录下,创建ca、jks、server、client四个目录。
二、开始生成证书:
打开命令提示行(cmd.exe),----如果是win7环境需要以管理员身份运行cmd.exe(一般在C:\Windows\System32下查找到cmd.exe右建以管理员身份运行),
并切换到Openssl安装目录的bin目录下。如下图:
依次执行下述命令。
(一)生成CA证书
1.创建私钥:
D:\OpenSSL-Win64\bin>opensslgenrsa -out ca/ca-key.pem 1024
2.创建证书请求:
D:\OpenSSL-Win64\bin>opensslreq -new -out ca/ca-req.csr -key ca/ca-key.pem -config openssl.cnf
-----
Country Name (2 letter code) [AU]:CN
State or Province Name (full name) [Some-State]:BJ
Locality Name (eg, city) []:BJ
Organization Name (eg, company) [Internet Widgits PtyLtd]:ple
Organizational Unit Name (eg, section) []:live
Common Name (eg, YOUR name) []:root
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
3.自签署证书:
D:\OpenSSL-Win64\bin>opensslx509 -req -in ca/ca-req.csr -out ca/ca-cert.pem -signkey ca/ca-key.pem -days3650
4.将证书导出成浏览器支持的.p12格式:
D:\OpenSSL-Win64\bin>opensslpkcs12 -export -clcerts -in ca/ca-cert.pem -inkey ca/ca-key.pem -out ca/ca.p12
密码:passca
(二)生成server证书
1.创建私钥:
D:\OpenSSL-Win64\bin>opensslgenrsa -out server/server-key.pem 1024
2.创建证书请求:
D:\OpenSSL-Win64\bin>opensslreq -new -out server/server-req.csr -key server/server-key.pem -config openssl.cnf
-----
Country Name (2 letter code) [AU]:CN
State or Province Name (full name) [Some-State]:BJ
Locality Name (eg, city) []:BJ
Organization Name (eg, company) [Internet Widgits PtyLtd]:ple
Organizational Unit Name (eg, section) []:live
Common Name (eg, YOUR name) []:localhost 注释:一定要写服务器所在的ip地址//红色这里是本机测试,所以我写localhost
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
3.自签署证书:
D:\OpenSSL-Win64\bin>opensslx509 -req -in server/server-req.csr -out server/server-cert.pem -signkeyserver/server-key.pem -CA ca/ca-cert.pem -CAkey ca/ca-key.pem -CAcreateserial-days 3650
4.将证书导出成浏览器支持的.p12格式:
D:\OpenSSL-Win64\bin>opensslpkcs12 -export -clcerts -in server/server-cert.pem -inkey server/server-key.pem-out server/server.p12
密码:passca
(三)生成client证书
1.创建私钥:
D:\OpenSSL-Win64\bin>opensslgenrsa -out client/client-key.pem 1024
2.创建证书请求:
D:\OpenSSL-Win64\bin>opensslreq -new -out client/client-req.csr -key client/client-key.pem -config openssl.cnf
-----Country Name (2 letter code) [AU]:CN
State or Province Name (full name) [Some-State]:BJ
Locality Name (eg, city) []:BJ
Organization Name (eg, company) [Internet Widgits PtyLtd]:ple
Organizational Unit Name (eg, section) []:live
Common Name (eg, YOUR name) []:client
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
3.自签署证书:
D:\OpenSSL-Win64\bin>opensslx509 -req -in client/client-req.csr -out client/client-cert.pem -signkeyclient/client-key.pem -CA ca/ca-cert.pem -CAkey ca/ca-key.pem -CAcreateserial-days 3650
4.将证书导出成浏览器支持的.p12格式:
D:\OpenSSL-Win64\bin>opensslpkcs12 -export -clcerts-in client/client-cert.pem -inkey client/client-key.pem -out client/client_err.p12
密码:passca
5. 生成客户端证书导出成浏览器支持的.p12格式(用于导入浏览器):
D:\OpenSSL-Win64\bin>opensslpkcs12 -export -clcerts -in ca/ca-cert.pem -inkey ca/ca-key.pem -outclient/client.p12
密码:passca
(四)根据ca证书生成jks文件
D:\OpenSSL-Win64\bin>keytool -keystore D:/OpenSSL-Win64/bin/jks/truststore.jks -keypass 222222-storepass 222222 -alias ca -import -trustcacerts -file D:/OpenSSL-Win64/bin/ca/ca-cert.pem
(五)配置tomcat ssl
修改conf/server.xml。配置如下。xml 代码
<Connectorport="8443" protocol="org.apache.coyote.http11.Http11Protocol"SSLEnabled="true" maxThreads="150" scheme="https"secure="true" connectionTimeout="20000" clientAuth="true"sslProtocol="TLS" useBodyEncodingForURI="true"enableLookups="false" acceptorThreadCount="2"socketBuffer="18000" maxHttpHeaderSize="262144" keystoreFile="server.p12"keystorePass="passca" keystoreType="PKCS12" truststoreFile="truststore.jks"truststorePass="222222" truststoreType="JKS" SSLCertificateFile="../bin/server-cert.pem" SSLCertificateKeyFile="../bin/server-key.pem" />
这里使用到了四个文件,各个文件都是在前面的步骤中生成的。
蓝色标识的server.p12和truststore.jks这两个文件需要放在tomcat的根目录下(如C:\Venustech\TSOC\webserver)。
红色的server-cert.pem和server-key.pem默认是放在tomcat的bin文件夹下的(如C:\Venustech\TSOC\webserver\bin)。
☆绿色部分为必须的,否则证书不生效。
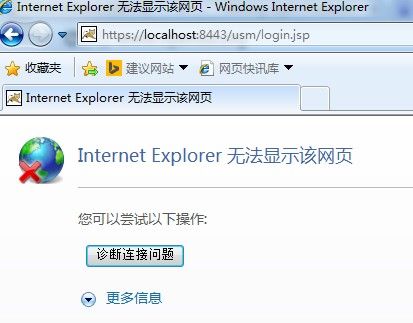
(六)验证ssl配置是否正确
访问系统http://localhost :8443/usm。如图:
(七)导入证书
将ca/ca.p12,client/client.p12分别导入到IE中去(打开IE->;Internet选项->内容->证书)。
ca.p12导入至受信任的根证书颁发机构,client.p12导入至个人。
重新访问系统。
注:1、细心的不难发现生成client.p12跟ca.p12是一样的,我测试时发现导入正常方式的client_err.p12不能正常访问系统,导入ca.p12能正常访问,有了解的大神帮助解决下。