【译】Consul 1.4:多数据中心服务网络
NOV 14 2018 THE CONSUL TEAM
我们很高兴地宣布HashiCorp Consul1.4 将将可广泛使用。Consul 是一个分布式服务网格, 可用于在任何运行平台以及公共或私有云之间的连接、安全和配置服务。此版本引入了一个完全重新设计的 ACL系统和第一个具有多数据中心支持的企业级Consul Connect 功能。特别感谢我们积极的社区成员在 RC期间提供的宝贵反馈。
立即下载
Consul Connect 将可广泛使用 (GA)
我们在今年6月推出了Connect功能, 使Consul 能够对流量进行细分, 并使用基于 TLS 的方法构建零信任网络。自最初发布以来, Consul团队一直专注于 production hardening 和扩展生态系统整合。我们很高兴地宣布Connect在此版本中将可广泛使用。
ACL 重新设计
对 Consul 的 ACL 系统进行了重新设计, 以简化操作和管理。这一变化涵盖了几个不同的领域。
Tokens 和 政策
现在可以使用公共存储器 ID 检索和修改 Token, 这些 ID 不同于用于授权向 Consul 发出请求的秘密 ID ( API 交互中token)。这样可以更安全地管理 ACL Token。
还添加了一个策略数据模型, 该模型可应用于许多Token并可集中管理。这使操作员一个中心位置。可以为一组应用程序、业务单元或其他分组更新特定策略, 并且本次更新将应用于在该策略下创建的所有 Token。
UI
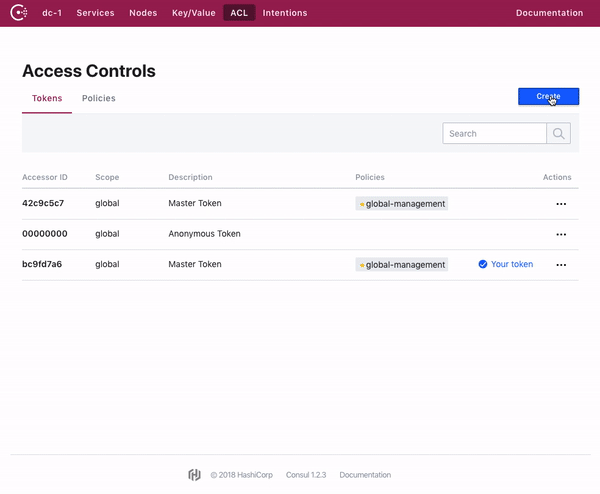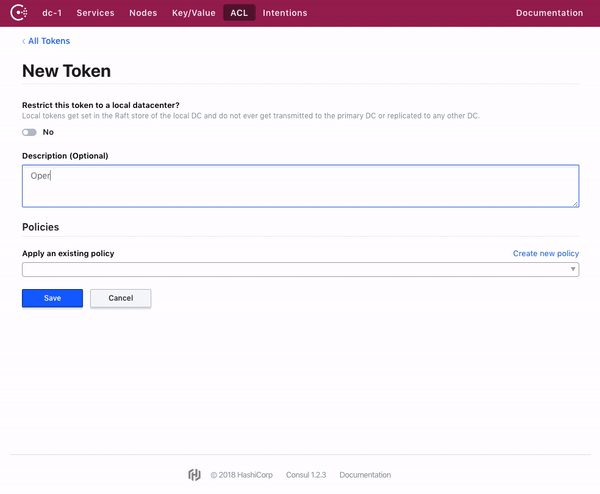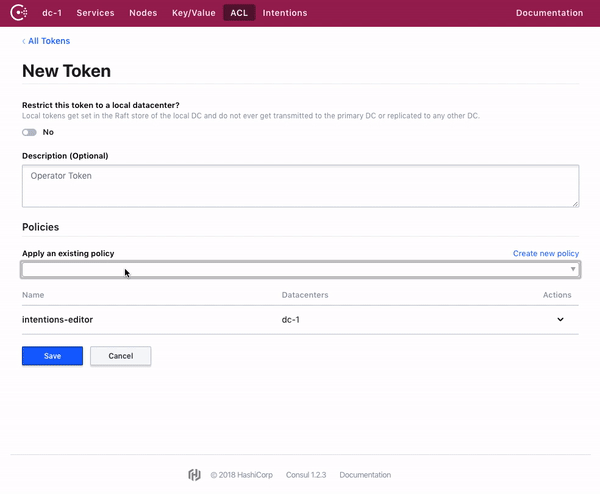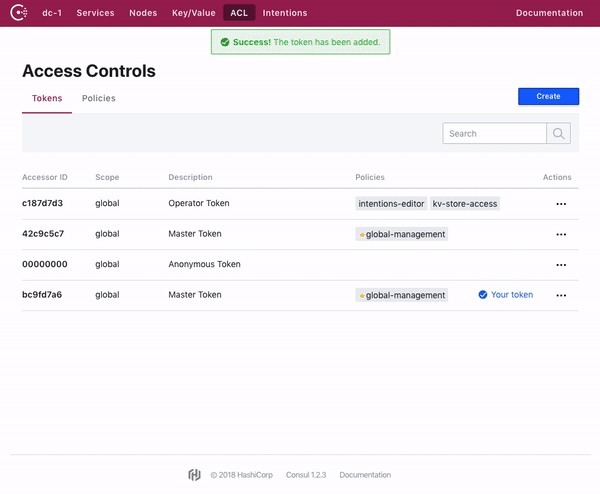
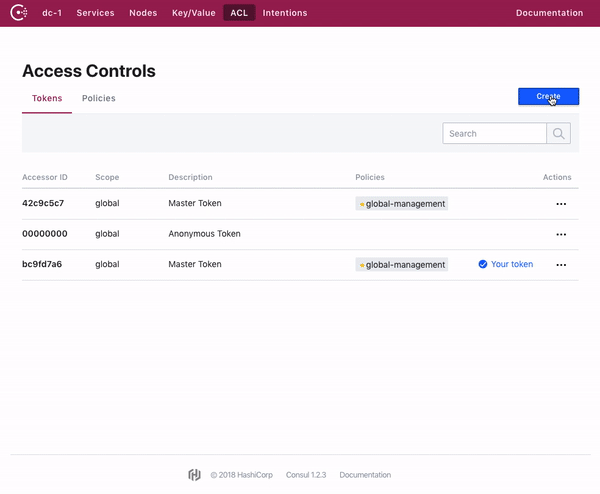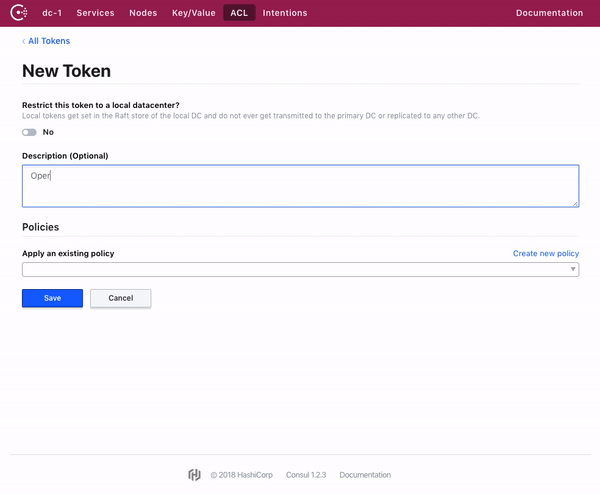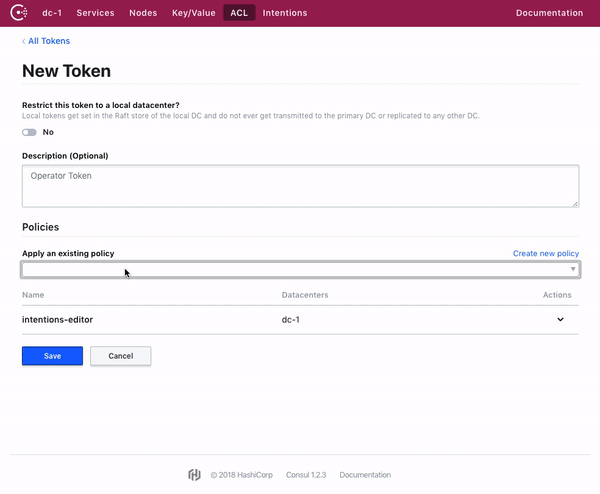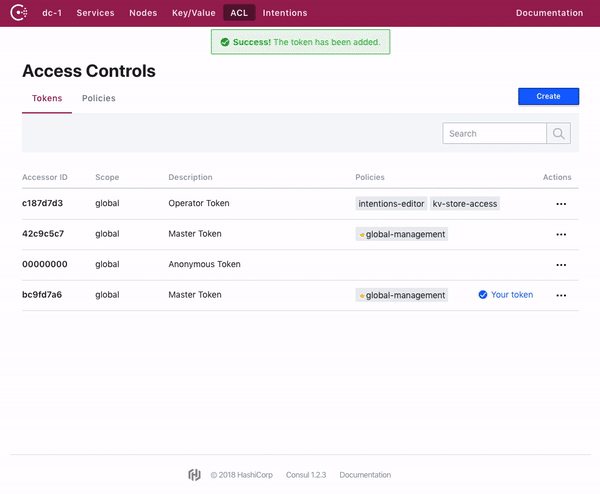
Consul web UI 允许对 Token 和策略进行全面管理。
CLI
新的 ACL 系统包括一个新的 CLI 来管理 Token、策略和升级。这即可用于自动化也可用于手动管理。
在此示例中, 将创建一个新策略, 然后是附加到该策略的 Token。
$ consul acl policy create -name "example" -description "Example policy" -rules @rules.hcl
ID: ca44555b-a2d8-94de-d763-88caffdaf11f
Name: example
Description: Example policy
Datacenters:
Rules:
service_prefix "marketing-" {
policy = "read"
}
$ consul acl token create -description "www-app" -policy-id ca44555b
AccessorID: 986193b5-e2b5-eb26-6264-b524ea60cc6d
SecretID: ec15675e-2999-d789-832e-8c4794daa8d7
Description: www-app
Local: false
Create Time: 2018-10-22 15:33:39.01789 -0400 EDT
Policies:
ca44555b-a2d8-94de-d763-88caffdaf11f - example
访问 ACL command 文档, 了解完整的示例及所有可用命令。
升级
我们设计了这个新系统, 允许来自旧 ACL 系统的就地升级, 旧系统将在自动迁移的同时为启用 ACL 的 clusters 的当前 API Token 保留兼容性。阅读完整的升级指南.
多数据中心服务细分 (企业版功能)
Consul 企业版增加了一个新的主要功能, 以扩展 connect 的功能, 使其超出单个群集用例的范围。Consul connect 现在支持在数据中心之间的意图复制和联合证书管理。这允许在任何数据中心的源服务和目标服务之间进行安全、授权的连接。意图的实时复制还可确保将一致的安全策略应用于服务, 无论服务驻留在原地或迁移到何处。
其他增强功能
除了新的 UI外, 此版本还提供了新的特性、增强功能和bug修复。其中一些主要功能特性包括:
- 新的
consul debug命令, 该命令收集有关目标代理和群集的信息, 以帮助解决 incidents 和调试问题 - dns 支持前缀查找, 例如
lb-*以匹配服务lb-001或lb-service-007
了解更多信息
欲了解更多信息, 请访问 Consul 项目页面。我们希望你喜欢 Consul 1.4!
【原文】Consul 1.4: Multi-Data Center Service Mesh
NOV 14 2018 THE CONSUL TEAM
We are excited to announce the general availability of HashiCorp Consul 1.4. Consul is a distributed service mesh to connect, secure, and configure services across any runtime platform and public or private cloud. This release introduces a completely redesigned ACL system and the first enterprise Consul Connect feature with multi-data center support. A special thanks to our active community members for their valuable feedback during the RC period.
Download Now
Consul Connect General Availability (GA)
We introduced the Connect feature in June this year, which enabled Consul to segment traffic and use a TLS-based approach to do zero trust networking. Since the initial release, the Consul team has focused on production hardening and expanding the ecosystem integration. We are pleased to announce the general availability of Connect in this release.
ACL Redesign
The ACL system in Consul has been redesigned to simplify operations and management. This change covered several different areas.
Tokens & Policies
Tokens can now be retrieved and modified using public accessor IDs, which are different than the secret ID (token in API interactions) used for authorizing requests to Consul. This allows for more secure management of ACL tokens.
A policy data model was also added, which can be applied to many tokens and managed centrally. This gives operators a central place to update a specific policy for a set of applications, business unit, or other groupings that will apply to all tokens created under that policy.
UI
The Consul web UI allows for full management of tokens and policies.
image
CLI
The new ACL system includes a new CLI to manage tokens, policies, and upgrades. This can be used in automation or for manual management.
In this example, a new policy is created, followed by a token which is attached to that policy.
$ consul acl policy create -name "example" -description "Example policy" -rules @rules.hcl
ID: ca44555b-a2d8-94de-d763-88caffdaf11f
Name: example
Description: Example policy
Datacenters:
Rules:
service_prefix "marketing-" {
policy = "read"
}
$ consul acl token create -description "www-app" -policy-id ca44555b
AccessorID: 986193b5-e2b5-eb26-6264-b524ea60cc6d
SecretID: ec15675e-2999-d789-832e-8c4794daa8d7
Description: www-app
Local: false
Create Time: 2018-10-22 15:33:39.01789 -0400 EDT
Policies:
ca44555b-a2d8-94de-d763-88caffdaf11f - example
Visit the ACL command documentation for a full set of examples and all the commands available.
Upgrading
We've designed this new system to allow for in-place upgrades coming from the old ACL system that will automatically migrate while retaining compatibility for current API tokens for clusters where ACLs are enabled. Read the full upgrade guide.
Multi-Data Center Service Segmentation (Enterprise Feature)
Consul Enterprise added a new major feature to extend Connect's capabilities beyond the single cluster use case. Consul Connect now supports replication of intentions and federated certificate management between data centers. This allows secure, authorized connections between source and destination services in any data center. The real-time replication of intentions also ensures that consistent security policies are applied to a service regardless of where it resides or migrates to.
Other Enhancements
In addition to the new UI, this release also delivers new features, enhancements and bug fixes. Some of the major features include:
- A new
consul debugcommand which gathers information about the target agent and cluster to help resolve incidents and debug issues - DNS supports prefix lookups, such as
lb-*to match serviceslb-001orlb-service-007
Learn More
For more information, please visit the Consul project page. We hope you enjoy Consul 1.4!