RHCE7 认证考试练习
RHCE7 认证考试练习
写在前面的话:考试练习不等于真实考试考题,里面的数据可能也与您考试练习的数据不一样,请认真仔细。祝愿RHCE取得好成绩!!
文章目录
- RHCE7 认证考试练习
- 模拟考前配置
- 开始考题
- 配置信息
- 参考答案
- 1.配置 YUM
- 2.配置 SELinux
- 3.配置 SSH
- 4.命令别名及IP 转发
- 5.端口转发
- 6.聚合网络
- 7.IPv6 设置
- 8.邮件服务
- 9.Samba 服务
- 10.多用户 samba 挂载
- 11.配置 NFS 服务
- 12.在 server 上配置一个 web 站点 http://server.example.com
- 13.为站点 http://server.example.com 配置 TLS 加密
- 14.在 server 上扩展您的 WEB 服务器
- 15.web 访问控制
- 16.在 server 上实现动态 web 内容
- 17.配置 server 提供一个 iSCSI 共享服务
- 18.配置 desktop 使其能连接在 server 上提供的 iscsi
- 19.编写一个位于/root/program 的 shell 脚本
- 20.写一个创建用户的脚本
- 21.在你的机器上创建一个 mariadb 数据库;
- 22.数据库查询
模拟考前配置
准备前
首先我们要将三台虚拟机开启
classroom是172.25.0.254
desktop是172.25.0.10
server是172.25.0.11
前提是三个主机能互相ping通
然后我们在本地上远程到classroom
[kiosk@foundation0 ~]$ ssh [email protected]
Last login: Sat Jul 6 09:08:15 2019 from 172.25.0.250
[root@classroom ~]#
等待远程过去之后
[root@classroom ~]# tail /etc/httpd/logs/error_log
将那段字母复制(NSS开头,off结尾的那段,具体我也不是带清楚)
[root@classroom ~]# vim /etc/httpd/conf.d/nss.conf
将你复制的那段粘贴到最底部,然后保存并退出
[root@classroom ~]# cd /var/www/html/pub/
[root@classroom pub]# echo "zheshi yige 在 server 上配置一个 web 站点" > example.html
[root@classroom pub]# echo "zheshi yige 在 server 上扩展您的 WEB 服务器" > www.html
[root@classroom pub]# echo "zheshi yige web 访问控制“ > private.html
[root@classroom pub]# vim webapp.wsgi
[root@classroom pub]# cat webapp.wsgi
def application(environ, start_response):
status = '200 OK'
output = 'Hello World!'
response_headers = [('Content-type', 'text/plain'),
('Content-Length', str(len(output)))]
start_response(status, response_headers)
return [output]
[root@classroom pub]# vim user
[root@classroom pub]# cat user
user1
user2
user3
user4
user5
[root@foundation0 ~]# vim /etc/hosts
[root@foundation0 ~]# tail -n 1 /etc/hosts
172.25.0.11 server.example.com alt.example.com www.example.com
[root@foundation0 ~]# ssh [email protected]
Last login: Sat Jul 6 09:08:15 2019 from 172.25.0.10
[root@desktop0 ~]# vim /etc/hosts
[root@desktop0 ~]# tail -n 1 /etc/hosts
172.25.0.11 server.example.com alt.example.com www.example.com
[root@foundation0 ~]# ssh [email protected]
[root@server0 ~]# vim /etc/hosts
[root@desktop0 ~]# tail -n 1 /etc/hosts
172.25.0.11 server.example.com alt.example.com www.example.com
更改网卡在本地切换到root用户(此题需要做后面的链路聚合)
[kiosk@foundation0 ~]$ su -
Password:
[root@foundation0 ~]#
密码是:Asimov
[root@foundation0 ~]# virt-manager
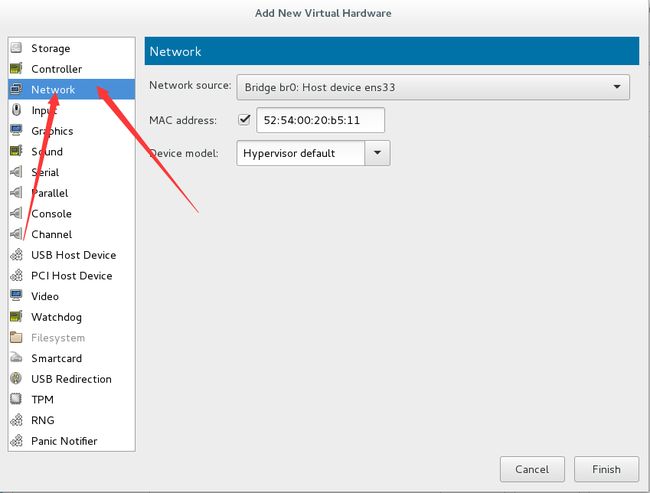
[外链图片转存失败(img-jY86pruv-1563461149295)(https://s2.ax1x.com/2019/07/08/ZDobtA.png)]
按照这种方式,在server 和 desktop两台虚拟机里面添加两块网卡,保证有三快网卡
[root@foundation0 ~]# reboot
然后直接将整个大虚拟机重启
数据库文件因过繁多内容,此处数据库文件请找我进行拷贝。
打开火狐浏览器输入:http://classroom.example.com/
以上是模拟考试前需要做的,真实考试不需要配置以上步骤
下面就开始模拟考题
开始考题
请注意:由于本机环境原因上述模拟考前配置是正式考试前不需要做的,考者切记正式考试是不用做前面的东西
现在正式开始你的考试:
配置信息
您在考试中将使用到两个系统的信息如下:
desktop0.example.com : 作为服务器
server0.example.com : 作为客户端
两个系统的root密码为redhat
系统的IP地址有DHCP提供,您可以视为正常,或者您可以按照一下信息重新设置未静态IP:
server0.example.com : 172.25.0.11/24
desktop0.example.com : 172.25.0.10/24
两个系统均为DNS域example.com的成员。除非特别知名,所有要求配置的网络服务都必须能被该域的系统访问。
classroom.example.com提供了集中认证的服务器为example.com。两个系统desktop0和server0都已经预先配置成此域的客户端。
classroom.example.com 提供了YUM软件仓库,URL是 http://classroom.example.com/content/rhel7.0/x86_64/dvd/ .
防火墙是默认打开的,在您认为适当的时候可以关闭。其他防火墙的设置可能在单独的要求中。
my133.org(172.13.0.0/24)作为不可信网络。
》 》 》 》 》》》》》》》》》》》》》》》》》》》》》》》》
参考答案
1.配置 YUM
配置yum源考试时候是不作为考题的,需要考者自己去阅读配置文档,里面有说明
- 分别在 server 和 desktop 上配置 YUM,指向:
server0
[root@server0 ~]# vim /etc/yum.repos.d/rhce.repo
[root@server0 ~]# cat /etc/yum.repos.d/rhce.repo
[rhce]
name=http://classroom.example.com/content/rhel7.0/x86_64/dvd/
baseurl=http://classroom.example.com/content/rhel7.0/x86_64/dvd/
enabled=1
gpgcheck=0
[root@server0 ~]#
desktop0
[root@desktop0 ~]# vim /etc/yum.repos.d/rhce.repo
[root@desktop0 ~]# cat /etc/yum.repos.d/rhce.repo
[rhce]
name=http://classroom.example.com/content/rhel7.0/x86_64/dvd/
baseurl=http://classroom.example.com/content/rhel7.0/x86_64/dvd/
enabled=1
gpgcheck=0
这一题是在真实考试中不做考题,您需要自己配置,yum源就在文中的信息当中,包括后面的各个域名的所归属的网段。您需要去阅读配置信息,这里配置信息在本博客开头部分。
2.配置 SELinux
- SElinux 有三种模式,请将 server 与 desktop 运行于强制模式
server0
[root@server0 ~]# vim /etc/selinux/config
[root@server0 ~]# cat /etc/selinux/config | grep SELINUX=en
SELINUX=enforcing
[root@server0 ~]# reboot
desktop0
[root@desktop0 ~]# vim /etc/selinux/config
[root@desktop0 ~]# cat /etc/selinux/config | grep SELINUX=en
SELINUX=enforcing
[root@desktop0 ~]# reboot
其实可以不用reboot重启虚拟机,两边改完配置文件之后
我们可以这样
[root@desktop0 ~]# setenforce 1 [root@desktop0 ~]# getenforce Enforcing配置文件也改为enforcing
同样我们也临时获取到Enforcing权限
接下来可不要忘记了另外一台虚拟机了哦
[root@server0 ~]# setenforce 1 [root@server0 ~]# getenforce Enforcing
3.配置 SSH
- 用户能够从域 example.com 内的客户端通过 SSH 访问您的两个虚拟机系统
- 在域 my133t.org 内的客户端不能访问您的两个虚拟机系统
server0
[root@server0 ~]# systemctl stop iptables ebtables
[root@server0 ~]# systemctl disable iptables ebtables
[root@server0 ~]# systemctl mask iptables ebtables
ln -s '/dev/null' '/etc/systemd/system/iptables.service'
ln -s '/dev/null' '/etc/systemd/system/ebtables.service'
[root@server0 ~]# systemctl restart firewalld
[root@server0 ~]# systemctl enable firewalld
[root@server0 ~]# firewall-cmd --remove-service=ssh --permanent
success
[root@server0 ~]# firewall-cmd --add-rich-rule 'rule family=ipv4 source address=172.25.0.0/24 service name=ssh accept' --permanent
success
[root@server0 ~]# firewall-cmd --reload
success
desktop0
[root@desktop0 ~]# systemctl stop iptables ebtables
[root@desktop0 ~]# systemctl disable iptables ebtables
[root@desktop0 ~]# systemctl mask iptables ebtables
ln -s '/dev/null' '/etc/systemd/system/iptables.service'
ln -s '/dev/null' '/etc/systemd/system/ebtables.service'
[root@desktop0 ~]# systemctl restart firewalld
[root@desktop0 ~]# systemctl enable firewalld
[root@desktop0 ~]# firewall-cmd --remove-service=ssh --permanent
success
[root@desktop0 ~]# firewall-cmd --add-rich-rule 'rule family=ipv4 source address=172.25.0.0/24 service name=ssh accept' --permanent
success
[root@desktop0 ~]# firewall-cmd --reload
success
做完这些操作之后,我们可以列出来查看一下,看看是否与我们想的一致
[root@server0 ~]# firewall-cmd --list-all public (default, active) interfaces: eth0 sources: services: dhcpv6-client ports: masquerade: no forward-ports: icmp-blocks: rich rules: rule family="ipv4" source address="172.25.0.0/24" service name="ssh" accept从此处我们可以看出ssh这个服务没有了,从而添加上了允许172.25.0.0/24这个网段的主机去访问,与我们所想的一致,接下来看看另外一个
[root@desktop0 ~]# firewall-cmd --list-all public (default, active) interfaces: eth0 sources: services: dhcpv6-client ports: masquerade: no forward-ports: icmp-blocks: rich rules: rule family="ipv4" source address="172.25.0.0/24" service name="ssh" accept
4.命令别名及IP 转发
1)在系统 server 和 desktop 上创建自定义命令为 tk,此自定义命令将执行/bin/ps aux,此命令对系统中所有用户有效
server0
[root@desktop0 ~]# vim /etc/bashrc
[root@desktop0 ~]# tail -n 1 /etc/bashrc
alias tk='/bin/ps aux'
[root@desktop0 ~]# bash
[root@desktop0 ~]# which tk
alias tk='/bin/ps aux'
/bin/ps
desktop0
[root@server0 ~]# vim /etc/bashrc
[root@server0 ~]# tail -n 1 /etc/bashrc
alias tk='/bin/ps aux'
[root@server0 ~]# bash
[root@server0 ~]# which tk
alias tk='/bin/ps aux'
/bin/ps
此题过于简单,这里就不过多解释
2)开启 IP 转发功能
server0
[root@server0 ~]# cat /etc/sysctl.conf
# System default settings live in /usr/lib/sysctl.d/00-system.conf.
# To override those settings, enter new settings here, or in an
.........................................
[root@server0 ~]# vim /usr/lib/sysctl.d/00-system.conf
[root@server0 ~]# cat /usr/lib/sysctl.d/00-system.conf
........................................
net.bridge.bridge-nf-call-arptables = 0
net.ipv4.ip_forward = 1 #在此处添加
........................................
[root@server0 ~]# sysctl -p /usr/lib/sysctl.d/00-system.conf
net.bridge.bridge-nf-call-ip6tables = 0
net.bridge.bridge-nf-call-iptables = 0
net.bridge.bridge-nf-call-arptables = 0
net.ipv4.ip_forward = 1 #有这个表示成功
kernel.shmmax = 4294967295
kernel.shmall = 268435456
同样在desktop 这台虚拟机上也要做,此处不做过多演示
[root@desktop0 ~]# cat /etc/sysctl.conf
# System default settings live in /usr/lib/sysctl.d/00-system.conf.
# To override those settings, enter new settings here, or in an /etc/sysctl.d/.conf file
#
# For more information, see sysctl.conf(5) and sysctl.d(5).
[root@desktop0 ~]# vim /usr/lib/sysctl.d/00-system.conf
[root@desktop0 ~]# sysctl -p /usr/lib/sysctl.d/00-system.conf
net.bridge.bridge-nf-call-ip6tables = 0
net.bridge.bridge-nf-call-iptables = 0
net.bridge.bridge-nf-call-arptables = 0
net.ipv4.ip_forward = 1
kernel.shmmax = 4294967295
kernel.shmall = 268435456
[root@desktop0 ~]#
5.端口转发
- 在 server 上配置端口转发,在 172.25.0.0/24 中的系统,访问 server 的本地端口 9527 将被转发到 80,此设置永久生效
server0
[root@server0 ~]# firewall-cmd --add-rich-rule 'rule family=ipv4 source address=172.25.0.0/24 forward-port port=9527 protocol=tcp to-port=80' --permanent
success
[root@server0 ~]# firewall-cmd --reload
success
可以用
firewall-cmd --list-all命令来查看是否添加上去[root@server0 ~]# firewall-cmd --list-all public (default, active) interfaces: eth0 sources: services: dhcpv6-client ports: masquerade: no forward-ports: icmp-blocks: rich rules: rule family="ipv4" source address="172.25.0.0/24" forward-port port="9527" protocol="tcp" to-port="80" rule family="ipv4" source address="172.25.0.0/24" service name="ssh" accept切记:此题需要之在server0上面操作,而且考试中题目需要你在那操作就在那操作,切勿心急盲目
6.聚合网络
在 server 和 desktop 之间配置链路聚合
此链路使用接口 slave1 和 slave2
此链路在一个接口失效后,仍然能工作
此链路在 server 上使用地址 192.168.0.1/24
此链路在 desktop 上使用地址 192.168.0.2/24
此链路在系统重启后依然保持正常状态
server0
[root@server0 ~]# nmcli device
DEVICE TYPE STATE CONNECTION
eth0 ethernet connected System eth0
eth1 ethernet disconnected --
eth2 ethernet disconnected --
lo loopback unmanaged --
[root@server0 ~]# nmcli connection add type team con-name team0 ifname team0 config '{"runner":{"name":"activebackup"}}'
Connection 'team0' (f816c00c-0488-455e-8d17-d66004112ef7) successfully added.
[root@server0 ~]# nmcli connection modify team0 ipv4.addresses "192.168.0.1/24" ipv4.method manual connection.autoconnect yes
[root@server0 ~]# nmcli connection add type team-slave con-name slave1 ifname eth1 master team0
Connection 'slave1' (5276955f-cbd6-4ec3-82dc-daf6b0073998) successfully added.
[root@server0 ~]# nmcli connection add type team-slave con-name slave2 ifname eth2 master team0
Connection 'slave2' (26009b44-7428-4cb4-a2b6-41d5aa5f3cac) successfully added.
[root@server0 ~]# nmcli connection up team0
Connection successfully activated (D-Bus active path: /org/freedesktop/NetworkManager/ActiveConnection/4)
[root@server0 ~]# systemctl restart network
desktop
[root@desktop0 ~]# nmcli device
DEVICE TYPE STATE CONNECTION
eth0 ethernet connected System eth0
eth1 ethernet disconnected --
eth2 ethernet disconnected --
lo loopback unmanaged --
[root@desktop0 ~]# nmcli connection add type team con-name team0 ifname team0 config '{"runner":{"name":"activebackup"}}'
[root@desktop0 ~]# nmcli connection modify team0 ipv4.addresses "192.168.0.2/24" ipv4.method manual connection.autoconnect yes
[root@desktop0 ~]# nmcli connection add type team-slave con-name slave1 ifname eth1 master team0
Connection 'slave1' (5c6c05b2-63b9-4aca-b991-ab570f4e23bd) successfully added.
[root@desktop0 ~]# nmcli connection add type team-slave con-name slave2 ifname eth2 master team0
Connection 'slave2' (546bc410-6a94-4fff-9bef-398e54b2feff) successfully added.
[root@desktop0 ~]# nmcli connection up team0
Connection successfully activated (D-Bus active path: /org/freedesktop/NetworkManager/ActiveConnection/4)
[root@desktop0 ~]# systemctl restart network
最后我们验证以下
[root@desktop0 ~]# ping 192.168.0.1 PING 192.168.0.1 (192.168.0.1) 56(84) bytes of data. 64 bytes from 192.168.0.1: icmp_seq=1 ttl=64 time=1.17 ms 64 bytes from 192.168.0.1: icmp_seq=2 ttl=64 time=0.301 ms然后我们断掉一个接口
[root@desktop0 ~]# nmcli connection down slave1 [root@desktop0 ~]# ping 192.168.0.1 PING 192.168.0.1 (192.168.0.1) 56(84) bytes of data. 64 bytes from 192.168.0.1: icmp_seq=1 ttl=64 time=0.582 ms ^C --- 192.168.0.1 ping statistics --- 1 packets transmitted, 1 received, 0% packet loss, time 0ms rtt min/avg/max/mdev = 0.582/0.582/0.582/0.000 ms我们down掉其中一个接口,还能ping通
7.IPv6 设置
在您的考试系统上配置接口,在你的默认网卡上使用如下 IPv6 地址
server 上的 IP 地址应该是 fd00:ba5e:ba11:10::1/64
desktop 上的 IP 地址应该是 fd00:ba5e:ba11:10::2/64
两个系统必须能与网络 fd00:ba5e:ba11:10::cc 内的系统通信
地址必须在重启后依然生效
两个系统保持当前的 IPv4 地址并能通信
server0
[root@server0 ~]# nmcli connection show
NAME UUID TYPE DEVICE
slave1 5276955f-cbd6-4ec3-82dc-daf6b0073998 802-3-ethernet eth1
team0 f816c00c-0488-455e-8d17-d66004112ef7 team team0
System eth0 5fb06bd0-0bb0-7ffb-45f1-d6edd65f3e03 802-3-ethernet eth0
slave2 26009b44-7428-4cb4-a2b6-41d5aa5f3cac 802-3-ethernet eth2
[root@server0 ~]# nmcli connection modify "System eth0" ipv6.addresses fd00:ba5e:ba11:10::1/64 ipv6.method manual connection.autoconnect yes
[root@server0 ~]# systemctl restart network
desktop
[root@desktop0 ~]# nmcli connection show
NAME UUID TYPE DEVICE
slave1 5c6c05b2-63b9-4aca-b991-ab570f4e23bd 802-3-ethernet eth1
team0 8ccca14c-7275-4996-9d06-9bfd33cf7b3e team team0
System eth0 5fb06bd0-0bb0-7ffb-45f1-d6edd65f3e03 802-3-ethernet eth0
slave2 546bc410-6a94-4fff-9bef-398e54b2feff 802-3-ethernet eth2
[root@desktop0 ~]# nmcli connection modify "System eth0" ipv6.addresses "fd00:ba5e:ba11:10::2/64" ipv6.method manual connection.autoconnect yes
[root@desktop0 ~]# systemctl restart network
验证
[root@desktop0 ~]# ping6 fd00:ba5e:ba11:10::1 PING fd00:ba5e:ba11:10::1(fd00:ba5e:ba11:10::1) 56 data bytes 64 bytes from fd00:ba5e:ba11:10::1: icmp_seq=1 ttl=64 time=4.55 ms 64 bytes from fd00:ba5e:ba11:10::1: icmp_seq=2 ttl=64 time=0.413 ms ^C --- fd00:ba5e:ba11:10::1 ping statistics --- 2 packets transmitted, 2 received, 0% packet loss, time 1003ms rtt min/avg/max/mdev = 0.413/2.485/4.558/2.073 ms有好多考者都在思考这么一个问题,
两个系统必须能与网络 fd00:ba5e:ba11:10::cc 内的系统通信
请问:你电脑能平通自己的网段吗,考题说的是能与这个网络里面得系统
8.邮件服务
在 server 上配置邮件服务
这些系统不接受外部发来的邮件
在这些系统上本地发送任何邮件都会被路由到 server1.example.com
从这些系统上发送的邮件显示来自于 example.com
您可以通过发送邮件到 harry 来测试您的配置
您可以通过访问 http://server1.example.com/email/harry 来验证您的配置(模拟环境上面没有这个地址,所以此题验证不了)
发给 harry 的邮件同时能被 natasha 收到
server0
[root@server0 ~]# vim /etc/postfix/main.cf
myorigin = example.com #大概在99行
inet_interfaces = localhost #大概在117行,默认是localhost
mydestination = #大概在165行,将=号后面的删掉
mynetworks = 127.0.0.0/8 #大概在265行,仅需要127.0.0.0/8
relayhost = [server1.example.com] #大概在319行
#保存并退出
[root@server0 ~]# vim /etc/aliases
[root@server0 ~]# tail -n 1 /etc/aliases
harry: harry,natasha
[root@server0 ~]# useradd harry
[root@server0 ~]# useradd natasha
[root@server0 ~]# systemctl restart postfix.service
[root@server0 ~]# systemctl enable postfix.service
[root@server0 ~]# firewall-cmd --add-service=smtp --permanent
success
[root@server0 ~]# firewall-cmd --reload
success
因为环境原因此题无法验证,真实考试环境中是可以验证的具体验证如下
[root@server0 ~]# echo "hello" | mail -s testmail harry [root@server0 ~]# curl http://server1.example.com/email/harry然后在最下面可以看到一个hello
配置文件具体解释:
myorigin = example.com #来自哪里
mynetworks = 127.0.0.0/8 # 邮件信息仅本地环回
relayhost = [server1.example.com] # 类似中间站,例如B在A和C的中间,A发给C的消息B就会收到。
9.Samba 服务
在 server 上配置 SAMBA 服务
您的 samba 服务器必须是 STAFF 工作组的一个成员
共享/common 目录,共享名为 common
只有 example.com 域内的客户端可以访问 common 共享
common 必须是可以浏览的
用户 natasha 必须能够读取共享中的内容,如果需要的话,验证密码是:tangkai
server0
[root@server0 ~]# yum install -y samba*
[root@server0 ~]# systemctl restart smb nmb
[root@server0 ~]# systemctl enable smb nmb
[root@server0 ~]# mkdir /common
[root@server0 ~]# vim /etc/samba/smb.conf
#找到:
[global]
workgroup = STAFF #将=后面改为STAFF
..................
..................
#在最下面,新加入:
[common]
path = /common
browseable = yes
valid users = natasha
# 保存并退出
[root@server0 ~]# getsebool -a | grep samba
samba_create_home_dirs --> off
samba_domain_controller --> off
samba_enable_home_dirs --> off
samba_export_all_ro --> off
samba_export_all_rw --> off
samba_portmapper --> off
samba_run_unconfined --> off
samba_share_fusefs --> off
samba_share_nfs --> off
sanlock_use_samba --> off
use_samba_home_dirs --> off
virt_sandbox_use_samba --> off
virt_use_samba --> off
[root@server0 ~]# setsebool -P samba_enable_home_dirs 1
[root@server0 ~]# chcon -Rt samba_share_t /common/
[root@server0 ~]# firewall-cmd --add-rich-rule 'rule family=ipv4 source address=172.25.0.0/24 service name=samba accept' --permanent
success
[root@server0 ~]# firewall-cmd --add-rich-rule 'rule family=ipv4 source address=172.25.0.0/24 service name=samba-client accept' --permanent
success
[root@server0 ~]# firewall-cmd --reload
success
[root@server0 ~]# id natasha
uid=1002(natasha) gid=1002(natasha) groups=1002(natasha)
[root@server0 ~]# smbpasswd -a natasha
New SMB password:
Retype new SMB password:
Added user natasha.
[root@server0 ~]# systemctl restart smb nmb
[root@server0 ~]# systemctl enable smb nmb
我们要养成一种习惯,不管之前有没有加入启动项,在每次重启之后,我们都要顺手把他加入到开机启动项里面
验证:需要到desktop0里面验证
[root@desktop0 ~]# yum install -y cifs-util* [root@desktop0 ~]# mount -t cifs -o username=natasha,password=tangkai //172.25.0.11/common /media/ [root@desktop0 ~]# df -h Filesystem Size Used Avail Use% Mounted on /dev/vda1 10G 3.1G 7.0G 31% / devtmpfs 906M 0 906M 0% /dev tmpfs 921M 80K 921M 1% /dev/shm tmpfs 921M 17M 904M 2% /run tmpfs 921M 0 921M 0% /sys/fs/cgroup //172.25.0.11/common 10G 3.1G 7.0G 31% /media
10.多用户 samba 挂载
在 server 上通过 samba 共享目录/storage
共享名为 share
共享目录只能被 example.com 域内的客户端使用
共享目录 share 必须可以被浏览
用户 sarah 能以读的方式访问此共享,访问密码是 tangkai
用户 kitty 能以读写的方式访问此共享,访问密码是 tangkai
此共享永久挂载在 desktop 上的/mnt/dev 目录,并使用用户 sarah 进行认证,任何用户可临时通过 kitty 来获得读写权限
server0
[root@server0 ~]# vim /etc/samba/smb.conf
[root@server0 ~]# tail n 6 /etc/samba/smb.conf
[share]
path = /storage
browseable = yes
valid users = sarah,kitty
writable = no
write list = kitty
[root@server0 ~]# systemctl restart smb nmb
[root@server0 ~]# systemctl enable smb nmb
[root@server0 ~]# mkdir /storage
[root@server0 ~]# useradd sarah
[root@server0 ~]# useradd kitty
[root@server0 ~]# chcon -Rt samba_share_t /storage/
[root@server0 ~]# setfacl -m u:sarah:r-x /storage/
[root@server0 ~]# setfacl -m u:kitty:rwx /storage/
[root@server0 ~]# smbpasswd -a sarah
New SMB password:
Retype new SMB password:
Added user sarah.
[root@server0 ~]# smbpasswd -a kitty
New SMB password:
Retype new SMB password:
Added user kitty.
desktop
[root@desktop0 ~]# vim /etc/fstab
[root@desktop0 ~]# tail -n 1 /etc/fstab
//172.25.0.11/share /mnt/dev cifs multiuser,username=sarah,password=tangkai,sec=ntlmssp 0 0
[root@desktop0 ~]# mkdir /mnt/dev
[root@desktop0 ~]# mount -a
[root@desktop0 ~]# df -h
Filesystem Size Used Avail Use% Mounted on
/dev/vda1 10G 3.1G 7.0G 31% /
devtmpfs 906M 0 906M 0% /dev
tmpfs 921M 80K 921M 1% /dev/shm
tmpfs 921M 17M 904M 2% /run
tmpfs 921M 0 921M 0% /sys/fs/cgroup
//172.25.0.11/common 10G 3.1G 7.0G 31% /media
//172.25.0.11/share 10G 3.1G 7.0G 31% /mnt/dev
11.配置 NFS 服务
1.) 在 server 上配置 NFS
以只读的方式共享/public,同时只能被 example.com 内用户访问
以读写的方式共享/protected 能被 example.com 内用户访问
访问/protected 需要通过 kerberos 安全加密,您可以使用下边链接的秘钥: http://classroom.example.com/pub/keytabs/server0.keytab
目录/protected 应该包含名为 project 拥有人为 ldapuser12 的子目录
用户 ldapuser12 能以读写的方式访问/protected/project
server0
[root@server0 ~]# vim /etc/exports
[root@server0 ~]# cat /etc/exports
/public 172.25.0.0/24(ro)
/protected 172.25.0.0/24(rw,sec=krb5p)
[root@server0 ~]# mkdir /public
[root@server0 ~]# mkdir /protected
[root@server0 ~]# mkdir /protected/project
# 这一栏的步骤有可能考试不需要你操作,但我们要以防万一
[root@server0 ~]# yum install -y krb5* sssd* authconfig*
[root@server0 ~]# cd /etc/openldap/
[root@server0 openldap]# ls
certs ldap.conf schema
[root@server0 openldap]# mkdir cacerts
[root@server0 openldap]# cd cacerts/
[root@server0 cacerts]# wget http://classroom.example.com/pub/example-ca.crt
[root@server0 cacerts]# authconfig-tui
# 过程在考rhcse的时候有描述,这里就不再介绍
[root@server0 cacerts]# su - ldapuser12
su: warning: cannot change directory to /home/guests/ldapuser12: No such file or directory
mkdir: cannot create directory '/home/guests': Permission denied
-bash-4.2$
[root@server0 ~]# chown ldapuser12 /protected/project
[root@server0 ~]# wget -O /etc/krb5.keytab http://classroom.example.com/pub/keytabs/server0.keytab
[root@server0 ~]# vim /etc/sysconfig/nfs
RPCNFSDARGS="-V 4.2" # 在第13行,引号里面加入-V 4.2
[root@server0 ~]# systemctl enable nfs-secure nfs-secure-server nfs-server
ln -s '/usr/lib/systemd/system/nfs-secure.service' '/etc/systemd/system/nfs.target.wants/nfs-secure.service'
ln -s '/usr/lib/systemd/system/nfs-secure-server.service' '/etc/systemd/system/nfs.target.wants/nfs-secure-server.service'
ln -s '/usr/lib/systemd/system/nfs-server.service' '/etc/systemd/system/nfs.target.wants/nfs-server.service'
[root@server0 ~]# systemctl start nfs-secure nfs-secure-server nfs-server
[root@server0 ~]# firewall-cmd --add-rich-rule 'rule family=ipv4 source address=172.25.0.0/24 service name=nfs accept' --permanent
success
[root@server0 ~]# firewall-cmd --add-rich-rule 'rule family=ipv4 source address=172.25.0.0/24 service name=rpc-bind accept' --permanent
success
[root@server0 ~]# firewall-cmd --reload
success
2.)
在 desktop 上挂载来自于 server0 的 NFS 共享
/public 挂载在目录/mnt/nfsmount 上
/protected 挂载在目录/mnt/nfssecure,并使用安全的方式,秘钥:
http://classroom.example.com/pub/keytabs/desktop0.keytab
用户 ldapuser12 能在/mnt/nfssecure/project 上创建文件
这些文件系统在系统启动时自动挂载
desktop
[root@desktop0 ~]# mkdir /mnt/nfsmount
[root@desktop0 ~]# mkdir /mnt/nfssecure
# 这一栏的步骤有可能考试不需要你操作,但我们要以防万一
[root@desktop0 ~]# yum install sssd* krb5* authconfig* -y
[root@desktop0 ~]# cd /etc/openldap/
[root@desktop0 openldap]# ls
certs ldap.conf
[root@desktop0 openldap]# mkdir cacerts
[root@desktop0 openldap]# cd cacerts/
[root@desktop0 cacerts]# wget http://classroom.example.com/pub/example-ca.crt
[root@desktop0 cacerts]# authconfig-tui
# 过程在考rhcse的时候有描述,这里就不再介绍
[root@desktop0 cacerts]# su - ldapuser12
su: warning: cannot change directory to /home/guests/ldapuser12: No such file or directory
mkdir: cannot create directory '/home/guests': Permission denied
-bash-4.2$
[root@desktop0 ~]# wget -O /etc/krb5.keytab http://classroom.example.com/pub/keytabs/desktop0.keytab
[root@desktop0 ~]# vim /etc/sysconfig/nfs
RPCNFSDARGS="-V 4.2" # 在第13行,引号里面加入-V 4.2
[root@desktop0 ~]# systemctl enable nfs-secure
ln -s '/usr/lib/systemd/system/nfs-secure.service' '/etc/systemd/system/nfs.target.wants/nfs-secure.service'
[root@desktop0 ~]# systemctl start nfs-secure
[root@desktop0 ~]# vim /etc/fstab
[root@desktop0 ~]# tail -n 2 /etc/fstab
172.25.0.11:/public /mnt/nfsmount nfs ro,v4.2 0 0
172.25.0.11:/protected /mnt/nfssecure nfs defaults,v4.2,sec=krb5p 0 0
[root@desktop0 ~]# mount -a
12.在 server 上配置一个 web 站点 http://server.example.com
从http://classroom.example.com/pub/example.html 下载文件,
并重命名为 index.html,不要修改文件内容。
将文件 index.html 拷贝到您的 DocumentRoot 目录下
来自于 example.com 的客户端可以访问该 web 服务器
来自于 my133t.org 的客户端的访问会被拒绝
server
[root@server0 ~]# yum install httpd -y
[root@server0 ~]# cd /var/www/html/
[root@server0 html]# ls
[root@server0 html]# wget -O index.html http://classroom.example.com/pub/example.html
[root@server0 html]# ls
index.html
[root@server0 html]# systemctl restart httpd
[root@server0 html]# systemctl enable httpd
ln -s '/usr/lib/systemd/system/httpd.service' '/etc/systemd/system/multi-user.target.wants/httpd.service'
[root@server0 html]# firewall-cmd --add-rich-rule 'rule family=ipv4 source address=172.25.0.0/24 service name=http accept' --permanent
success
[root@server0 html]# firewall-cmd --reload
success
验证
[root@server0 html]# curl http://server.example.com zheshi yige 在 server 上配置一个 web 站点
13.为站点 http://server.example.com 配置 TLS 加密
已签名证书从 http://classroom.example.com/pub/tls/certs/server0.crt 获取
证书的秘钥从 http://classroom.example.com/pub/tls/private/server0.key 获取
证书的签名授权信息从 http://classroom.example.com/pub/tls/certs/www0.crt 获取
[root@server0 html]# yum -y install mod_ssl.x86_64
[root@server0 html]# cd /etc/httpd/conf.d/
[root@server0 conf.d]# vim ssl.conf
#到120行左右
SSLCertificateFile /etc/pki/tls/certs/localhost.crt
SSLCertificateKeyFile /etc/pki/tls/private/localhost.key
#SSLCACertificateFile /etc/pki/tls/certs/ca-bundle.crt
#将这三个的后面的文件名改掉,然后将最后一个的#号去掉,效果如下:
SSLCertificateFile /etc/pki/tls/certs/server0.crt
SSLCertificateKeyFile /etc/pki/tls/private/server0.key
SSLCACertificateFile /etc/pki/tls/certs/www0.crt
# 记住这三个路径之后保存并退出
[root@server0 conf.d]# cd /etc/pki/tls/certs/
[root@server0 certs]# wget http://classroom.example.com/pub/tls/certs/server0.crt
[root@server0 certs]# cd /etc/pki/tls/private/
[root@server0 private]# wget http://classroom.example.com/pub/tls/private/server0.key
[root@server0 private]# cd /etc/pki/tls/certs/
[root@server0 certs]# wget http://classroom.example.com/pub/tls/certs/www0.crt
[root@server0 certs]# systemctl restart httpd.service
[root@server0 certs]# systemctl enable httpd.service
[root@server0 certs]# firewall-cmd --add-rich-rule 'rule family=ipv4 source address=172.25.0.0/24 service name=https accept' --permanent
success
[root@server0 certs]# firewall-cmd --reload
success
验证
[root@server0 certs]# curl -k https://server.example.com zheshi yige 在 server 上配置一个 web 站点 [root@server0 certs]# curl http://server.example.com zheshi yige 在 server 上配置一个 web 站点
14.在 server 上扩展您的 WEB 服务器
- 为站点 http://www.example.com 创建一个虚拟主机
- 设置 DocumentRoot 为/var/www/virtual
- 从 http://classroom.example.com/pub/www.html 下载文件,并重命名为 index.html,不要修改文件内容。
- 将文件 index.html 拷贝到 DocumentRoot 目录下
- 确保 floyd 用户能够在/var/www/virtual 下创建文件
server
[root@server0 ~]# find / -name *vhosts.conf
/usr/share/doc/httpd-2.4.6/httpd-vhosts.conf
[root@server0 ~]# cp /usr/share/doc/httpd-2.4.6/httpd-vhosts.conf /etc/httpd/conf.d/
[root@server0 ~]# cd /etc/httpd/conf.d/
[root@server0 conf.d]# vim httpd-vhosts.conf
[root@server0 conf.d]# tail -n 8 httpd-vhosts.conf
<VirtualHost *:80>
DocumentRoot "/var/www/html"
ServerName server.example.com
</VirtualHost>
<VirtualHost *:80>
DocumentRoot "/var/www/virtual"
ServerName www.example.com
</VirtualHost>
[root@server0 ~]# mkdir /var/www/virtual
oot@server0 ~]# cd /var/www/virtual/
[root@server0 virtual]# wget -O index.html http://classroom.example.com/pub/www.html
[root@server0 conf.d]# useradd floyd
[root@server0 conf.d]# setfacl -m u:floyd:rwx /var/www/virtual
[root@server0 conf.d]# systemctl restart httpd.service
[root@server0 conf.d]# systemctl enable httpd.service
验证
[root@server0 conf.d]# curl www.example.com zheshi yige 在 server 上扩展您的 WEB 服务器 [root@server0 conf.d]# curl -k https://server.example.com zheshi yige 在 server 上配置一个 web 站点 [root@server0 conf.d]# curl http://server.example.com zheshi yige 在 server 上配置一个 web 站点
15.web 访问控制
在您 server 上的 web 服务器的 DocumentRoot 目录下创建一个名为 private 的目录
从http://classroom.example.com/pub/private.html 下载文件到这个目录,并重命名为index.html,不要修改文件内容
从 server 上,任何人都可以浏览 private 的内容,但是从其他系统不能访问这个目录的内容
[root@server0 conf.d]# cd /var/www/html/
[root@server0 html]# mkdir private
[root@server0 html]# cd private/
[root@server0 private]# wget -O index.html http://classroom.example.com/pub/private.
[root@server0 private]# vim /etc/httpd/conf/httpd.conf
#搜索Requ,复制
<Directory />
AllowOverride none
Require all denied
</Directory>
[root@server0 private]# vim /etc/httpd/conf.d/httpd-vhosts.conf
<VirtualHost *:80>
DocumentRoot "/var/www/html"
ServerName server.example.com
#验证
[root@server0 private]# curl server.example.com/private/ zheshi yige web 访问控制 # 然后我们用客户端去访问 root@desktop0 ~]# curl server.example.com/private/ <!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN"> <html><head> <title>403 Forbidden</title> </head><body> <h1>Forbidden</h1> <p>You don't have permission to access /private/ on this server.</p> </body></html>
16.在 server 上实现动态 web 内容
动态内容由名为 alt.example.com 的虚拟主机提供虚拟主机侦听端口为 8909
从 http://classroom.example.com/pub/webapp.wsgi 下载一个脚本,然后放在适当的位置,不要修改文件内容
客户端访问 http://alt.example.com:8909 时,应该接收到动态生成的 web 页面此 http://alt.example.com:8909 必须能被 example.com 内所有的系统访问
server
[root@server0 private]# yum install mod_wsgi.x86_64 -y
[root@server0 private]# cd /var/www/
[root@server0 www]# mkdir wsgi
[root@server0 www]# cd wsgi/
[root@server0 wsgi]# wget http://classroom.example.com/pub/webapp.wsgi
[root@server0 wsgi]# vim /etc/httpd/conf.d/httpd-vhosts.conf
[root@server0 wsgi]# tail -n 5 /etc/httpd/conf.d/httpd-vhosts.conf
Listen 8909
<VirtualHost *:8909>
WSGIScriptAlias / "/var/www/wsgi/webapp.wsgi"
ServerName alt.example.com:8909
</VirtualHost>
[root@server0 wsgi]# firewall-cmd --add-rich-rule 'rule family=ipv4 port port=8909 protocol=tcp accept' --permanent
success
[root@server0 wsgi]# firewall-cmd --reload
success
[root@server0 wsgi]# curl alt.example.com:8909
curl: (7) Failed connect to alt.example.com:8909; Connection refused
[root@server0 wsgi]# semanage port -l | grep http
http_cache_port_t tcp 8080, 8118, 8123, 10001-10010
http_cache_port_t udp 3130
http_port_t tcp 80, 81, 443, 488, 8008, 8009, 8443, 9000
pegasus_http_port_t tcp 5988
pegasus_https_port_t tcp 5989
[root@server0 wsgi]# semanage port -a -t http_port_t -p tcp 8909
[root@server0 wsgi]# systemctl restart httpd.service
[root@server0 wsgi]# systemctl enable httpd.service
验证
[root@server0 wsgi]# curl http://alt.example.com:8909 Hello World!
17.配置 server 提供一个 iSCSI 共享服务
磁盘名为 iqn.2014-09.com.example:server
服务端口为 3260
使用 iscsi_store 作为其后端卷其大小为 3G
此服务只能被 desktop.example.com 访问
server
[root@server0 wsgi]# yum install targetcli* -y
[root@server0 wsgi]# lsblk
NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINT
vda 253:0 0 10G 0 disk
└─vda1 253:1 0 10G 0 part /
vdb 253:16 0 10G 0 disk
[root@server0 wsgi]# fdisk /dev/vdb
Command (m for help): n
Partition type:
p primary (0 primary, 0 extended, 4 free)
e extended
Select (default p): p
Partition number (1-4, default 1):
First sector (2048-20971519, default 2048):
Last sector, +sectors or +size{K,M,G} (2048-20971519, default 20971519): +3G
Command (m for help): w
[root@server0 wsgi]# partprobe
[root@server0 wsgi]# lsblk
NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINT
vda 253:0 0 10G 0 disk
└─vda1 253:1 0 10G 0 part /
vdb 253:16 0 10G 0 disk
└─vdb1 253:17 0 3G 0 part
[root@server0 wsgi]# targetcli
/> ls
o- / ................................................ [...]
o- backstores ..................................... [...]
| o- block ........................................ [Storage Objects: 0]
| o- fileio ....................................... [Storage Objects: 0]
| o- pscsi ........................................ [Storage Objects: 0]
| o- ramdisk ...................................... [Storage Objects: 0]
o- iscsi .......................................... [Targets: 0]
o- loopback ....................................... [Targets: 0]
/> cd /backstores/block
/backstores/block> create iscsi_store /dev/vdb1
Created block storage object iscsi_store using /dev/vdb1.
/backstores/block> cd /iscsi
/iscsi> create iqn.2014-09.com.example:server
Created target iqn.2014-09.com.example:server.
Created TPG 1.
/iscsi> ls
o- iscsi ........................................... [Targets: 1]
o- iqn.2014-09.com.example:server ................ [TPGs: 1]
o- tpg1 ........................................ [no-gen-acls, no-auth]
o- acls ...................................... [ACLs: 0]
o- luns ...................................... [LUNs: 0]
o- portals ................................... [Portals: 0]
/iscsi> cd iqn.2014-09.com.example:server/tpg1/acls
/iscsi/iqn.20...ver/tpg1/acls> create iqn.2014-09.com.example:desktop
Created Node ACL for iqn.2014-09.com.example:desktop
/iscsi/iqn.20...ver/tpg1/acls> cd /iscsi/iqn.2014-09.com.example:server/tpg1/luns
/iscsi/iqn.20...ver/tpg1/luns> create /backstores/block/iscsi_store
Created LUN 0.
Created LUN 0->0 mapping in node ACL iqn.2014-09.com.example:desktop
/iscsi/iqn.20...ver/tpg1/luns> cd /iscsi/iqn.2014-09.com.example:server/tpg1/portals
/iscsi/iqn.20.../tpg1/portals> create 172.25.0.11 3260
Using default IP port 3260
Created network portal 172.25.0.11:3260.
/iscsi/iqn.20.../tpg1/portals> exit
Global pref auto_save_on_exit=true
Last 10 configs saved in /etc/target/backup.
Configuration saved to /etc/target/saveconfig.json
[root@server0 wsgi]# firewall-cmd --add-rich-rule 'rule family="ipv4" source address="172.25.0.0/24" port port=3260 protocol=tcp accept' --permanent
success
[root@server0 wsgi]# firewall-cmd --reload
success
[root@server0 wsgi]# systemctl restart target
[root@server0 wsgi]# systemctl enable target
ln -s '/usr/lib/systemd/system/target.service' '/etc/systemd/system/multi-user.target.wants/target.service'
这一题的验证是下一题
18.配置 desktop 使其能连接在 server 上提供的 iscsi
iSCSI 设备在系统启动的期间自动加载
块设备 iSCSI 上包含一个大小 1500MiB 的分区,并格式化为 ext4
此分区挂载在/mnt/netdev 上同时在系统启动的期间自动加载
desktop
[root@desktop0 ~]# yum install -y iscsi-init*
[root@desktop0 ~]# mkdir /mnt/netdev
[root@desktop0 ~]# vim /etc/iscsi/initiatorname.iscsi
[root@desktop0 ~]# cat /etc/iscsi/initiatorname.iscsi
InitiatorName=iqn.2014-09.com.example:desktop
[root@desktop0 ~]# systemctl restart iscsi iscsid
[root@desktop0 ~]# systemctl enable iscsi iscsid
ln -s '/usr/lib/systemd/system/iscsid.service' '/etc/systemd/system/multi-user.target.wants/iscsid.service'
[root@desktop0 ~]# iscsiadm -m discovery -t st -p 172.25.0.11
172.25.0.11:3260,1 iqn.2014-09.com.example:server
[root@desktop0 ~]# iscsiadm -m node -l
Logging in to [iface: default, target: iqn.2014-09.com.example:server, portal: 172.25.0.11,3260] (multiple)
Login to [iface: default, target: iqn.2014-09.com.example:server, portal: 172.25.0.11,3260] successful.
[root@desktop0 ~]# lsblk
NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINT
sda 8:0 0 3G 0 disk
vda 253:0 0 10G 0 disk
└─vda1 253:1 0 10G 0 part /
vdb 253:16 0 10G 0 disk
[root@desktop0 ~]# fdisk /dev/sda
Command (m for help): n
Partition type:
p primary (0 primary, 0 extended, 4 free)
e extended
Select (default p): p
Partition number (1-4, default 1):
First sector (8192-6291455, default 8192):
Last sector, +sectors or +size{K,M,G} (8192-6291455, default 6291455): +1500M
Command (m for help): w
[root@desktop0 ~]# partprobe
[root@desktop0 ~]# mkfs.ext4 /dev/sda1
[root@desktop0 ~]# blkid | grep sda
/dev/sda1: UUID="142c6ec3-0d06-4f89-91e3-8201e8186d37" TYPE="ext4"
[root@desktop0 ~]# vim /etc/fstab
[root@desktop0 ~]# tail -n 1 /etc/fstab
UUID="142c6ec3-0d06-4f89-91e3-8201e8186d37" /mnt/netdev ext4 defaults,_netdev 0 0
[root@desktop0 ~]# mount -a
[root@desktop0 ~]# df -h
/dev/vda1 10G 3.1G 7.0G 31% /
devtmpfs 906M 0 906M 0% /dev
tmpfs 921M 80K 921M 1% /dev/shm
.............................
/dev/sda1 1.5G 4.5M 1.4G 1% /mnt/netdev
19.编写一个位于/root/program 的 shell 脚本
当执行/root/program tang 时,终端显示 kai
当执行/root/program kai 时,终端显示 tang
当仅执行/root/program 不加参数,或者加上其他参数时,终端显示标准错误输出/root/program tang|kai
server
[root@server0 ~]# vim /root/program
[root@server0 ~]# cat /root/program
#!/bin/bash
case $1 in
tang)
echo "kai"
;;
kai)
echo "tang"
;;
*)
echo "/root/program tang|kai"
;;
esac
[root@server0 ~]# chmod +x /root/program
[root@server0 ~]# /root/program tang
kai
[root@server0 ~]# /root/program kai
tang
[root@server0 ~]# /root/program
/root/program tang|kai
20.写一个创建用户的脚本
脚本名为/root/mkuser,脚本执行时需要添加一个参数,
请在 http://classroom.example.com/pub/user 下载下来,这个 user 就是参数
如果没有参数,将提示:Usage:/root/mkuser
如果参数为不存在的文件,则提示:Input file not found
如果存在,则创建用户,用户不需要设置密码,用户的 shell 为/bin/flase
server
[root@server0 ~]# vim /root/mkuser
[root@server0 ~]# cat /root/mkuser
#!/bin/bash
if [ $# -eq 0 ];then
echo "Usage:/root/mkuser"
else
if [ -f $1 ];then
for user in $(cat $1);do
useradd -s /bin/flase $user
done
else
echo "Input file not found"
fi
fi
[root@server0 ~]# chmod +x /root/mkuser
[root@server0 ~]# cd /root
[root@server0 ~]# wget http://classroom.example.com/pub/user
[root@server0 ~]# /root/mkuser
Usage:/root/mkuser
[root@server0 ~]# /root/mkuser dfs
Input file not found
[root@server0 ~]# /root/mkuser user
[root@server0 ~]# id user1
uid=1001(user1) gid=1001(user1) groups=1001(user1)
[root@server0 ~]# id user2
uid=1002(user2) gid=1002(user2) groups=1002(user2)
[root@server0 ~]# id user3
uid=1003(user3) gid=1003(user3) groups=1003(user3)
[root@server0 ~]# cat user
user1
user2
user3
user4
user5
[root@server0 ~]#
21.在你的机器上创建一个 mariadb 数据库;
数据库名为 contacts
数据库应该包含来自数据库复制的内容。复制文件的 URL 为
http://classroom.example.com/pub/user.mdb
数据库只能被 localhost 访问
除了 root 用户,此数据库只能被用户 raikon 查询,此用户密码为 redhat
root 用户密码为 redhat,同时不允许空密码登陆
server
[root@server0 ~]# yum install mariadb* -y
[root@server0 ~]# systemctl restart mariadb
[root@server0 ~]# systemctl enable mariadb
ln -s '/usr/lib/systemd/system/mariadb.service' '/etc/systemd/system/multi-user.target.wants/mariadb.service'
[root@server0 ~]# mysql_secure_installation
Set root password? [Y/n] y
New password: #redhat
Re-enter new password: #redhat
Password updated successfully!
Remove anonymous users? [Y/n] y
... Success!
Disallow root login remotely? [Y/n] n
... skipping.
Remove test database and access to it? [Y/n] y
- Dropping test database...
... Success!
Reload privilege tables now? [Y/n] y
... Success!
[root@server0 ~]# wget http://classroom.example.com/pub/users.mdb
[root@server0 ~]# mysql -uroot -predhat
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 11
Server version: 5.5.35-MariaDB MariaDB Server
Copyright (c) 2000, 2013, Oracle, Monty Program Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> create database Contacts;
Query OK, 1 row affected (0.00 sec)
MariaDB [(none)]> use Contacts;
Database changed
MariaDB [Contacts]> source /root/user.mdb;
MariaDB [Contacts]> grant select on Contacts .* to 'raikon@localhost' identified by 'redhat';
MariaDB [Contacts]> flush privileges;
MariaDB [Contacts]> exit
22.数据库查询
密码是 123456 的人的名字?
[root@server0 ~]# mysql -uroot -predhat
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| contacts |
| mysql |
| performance_schema |
+--------------------+
4 rows in set (0.00 sec)
MariaDB [(none)]> use contacts;
MariaDB [contacts]> show tables;
+--------------------+
| Tables_in_contacts |
+--------------------+
| user |
+--------------------+
1 row in set (0.00 sec)
MariaDB [contacts]> desc user;
+-----------+-------------+------+-----+---------+-------+
| Field | Type | Null | Key | Default | Extra |
+-----------+-------------+------+-----+---------+-------+
| usernamer | varchar(50) | YES | | NULL | |
| password | varchar(50) | YES | | NULL | |
| live | varchar(50) | YES | | NULL | |
+-----------+-------------+------+-----+---------+-------+
3 rows in set (0.00 sec)
MariaDB [contacts]> select usernamer from user where password = '123456';
+-----------+
| usernamer |
+-----------+
| harry |
+-----------+
1 row in set (0.00 sec)
有多少人的姓名是 barbara,同时居住在 sunnyvale ?
MariaDB [contacts]> desc user;
+-----------+-------------+------+-----+---------+-------+
| Field | Type | Null | Key | Default | Extra |
+-----------+-------------+------+-----+---------+-------+
| usernamer | varchar(50) | YES | | NULL | |
| password | varchar(50) | YES | | NULL | |
| live | varchar(50) | YES | | NULL | |
+-----------+-------------+------+-----+---------+-------+
3 rows in set (0.00 sec)
MariaDB [contacts]> select count(1) from user where usernamer = 'barbara' and live ='sunnyvale';
+----------+
| count(1) |
+----------+
| 2 |
+----------+
1 row in set (0.00 sec)
在这里,考者请切记,查询之后的答案记住一定要填写到所填写的正确地方。
不要忘记填写进去
》》》》》》》》》》》》》》》》》》》》》》
以上就是本次RHCE 7 版本的认证考试参考答案,如有错误请联系博主进行更改,最后祝愿大家RHCE认证取得好成绩!!!!