背景:
在普通站点到站点×××中,我们通常要考虑一个问题,那就是NAT对×××产生的影响。一般的企业中,由一台路由器或防火墙即充当了×××设备,将两个站点连接起来,又充当了将公司内网的私有地址转换成公网IP地址的作用,这样一来,×××就会产生问题。这种情况只会对普通的站点到站点×××产生影响,不会对隧道模式的×××产生影响,如VTI和GRE Over IPSec。下面来演示问题的产生和解决方法:
实验环境:
IOS:Version 12.4(15)T5
ASA 8.4版本
拓扑图如下:
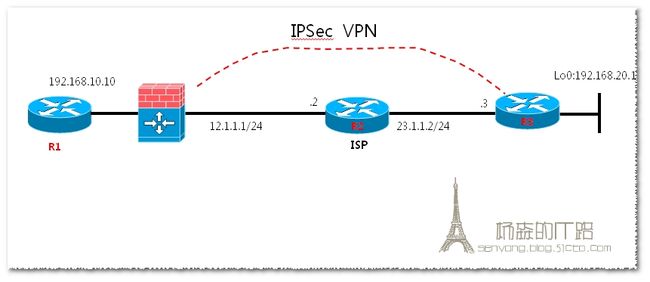 在上面的拓扑图中,使用ASA和R3模拟总部和分支的两台×××设备,R2模拟运营商的路由器,R1模拟总部身后的网络。在ASA和R3这两台设备上,即要使用×××功能,也要使用NAT功能,分别将身后的192.168.10.0/24和192.168.20.0/24的网络转换成公网IP地址,能够访问R2身后的网络2.2.2.2。
在上面的拓扑图中,使用ASA和R3模拟总部和分支的两台×××设备,R2模拟运营商的路由器,R1模拟总部身后的网络。在ASA和R3这两台设备上,即要使用×××功能,也要使用NAT功能,分别将身后的192.168.10.0/24和192.168.20.0/24的网络转换成公网IP地址,能够访问R2身后的网络2.2.2.2。
基础配置如下(读者可直接粘贴):
R1:
en
conf t
host R1
int f0/0
ip add 192.168.10.10 255.255.255.0
no shut
ip route 0.0.0.0 0.0.0.0 192.168.10.1
ASA:
interface GigabitEthernet0
nameif inside
security-level 100
ip address 192.168.10.1 255.255.255.0
ciscoasa(config)# sh run int g1
!
interface GigabitEthernet1
nameif outside
security-level 0
ip address 12.1.1.1 255.255.255.0
!
route outside 0.0.0.0 0.0.0.0 12.1.1.2
R2:
interface FastEthernet1/0
ip address 12.1.1.2 255.255.255.0
no shutdown
!
interface FastEthernet2/0
ip address 23.1.1.2 255.255.255.0
no shutdown
!
interface Loopback0
ip address 2.2.2.2 255.255.255.0
R3:
interface FastEthernet2/0
ip address 23.1.1.3 255.255.255.0
no shutdown
!
interface Loopback0
ip address 192.168.20.1 255.255.255.0
!
ip route 0.0.0.0 0.0.0.0 23.1.1.2
在防火墙上ping R3进行测试:
ciscoasa# ping 23.1.1.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 23.1.1.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 10/20/50 ms
×××配置:
ASA ×××配置:
crypto ikev1 enable outside
crypto ikev1 policy 10
authentication pre-share
encryption des
hash md5
group 1
lifetime 86400
tunnel-group 23.1.1.3 type ipsec-l2l
tunnel-group 23.1.1.3 ipsec-attributes
ikev1 pre-shared-key cisco
crypto ipsec ikev1 transform-set trans esp-des esp-md5-hmac
access-list 100 extended permit ip 192.168.10.0 255.255.255.0 192.168.20.0 255.255.255.0
crypto map cisco 10 match address 100
crypto map cisco 10 set peer 23.1.1.3
crypto map cisco 10 set ikev1 transform-set trans
crypto map cisco interface outside
R3 ×××配置:
crypto isakmp policy 10
hash md5
authentication pre-share
crypto isakmp key cisco address 12.1.1.1
!
crypto ipsec transform-set trans esp-des esp-md5-hmac
!
crypto map cisco 10 ipsec-isakmp
set peer 12.1.1.1
set transform-set trans
match address 100
!
access-list 100 permit ip 192.168.20.0 0.0.0.255 192.168.10.0 0.0.0.255
!
interface FastEthernet2/0
ip address 23.1.1.3 255.255.255.0
crypto map cisco
使用R1 ping R3的192.168.20.1来进行测试:
R1#ping 192.168.20.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.20.1, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 52/66/80 ms
查看×××加解密:
R3#show crypto engine connections active
Crypto Engine Connections
ID Interface Type Algorithm Encrypt Decrypt IP-Address
5 Fa2/0 IPsec DES+MD5 0 4 23.1.1.3
6 Fa2/0 IPsec DES+MD5 4 0 23.1.1.3
1002 Fa2/0 IKE MD5+DES 0 0 23.1.1.3
说明加解密正常。
配置NAT:
在R3上进行配置NAT转换,将192.168.20.0/24的地址转换成外网接口的公网IP地址,让R3身后的网络可以访问互联网。
首先在没有配置之前测试R3身后的网络是否可以访问公网地址2.2.2.2(使用带源PING进行测试)
R3#ping 2.2.2.2 source lo 0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 2.2.2.2, timeout is 2 seconds:
Packet sent with a source address of 192.168.20.1
.....
Success rate is 0 percent (0/5)
发现无法ping通,因为没有做NAT。
在R3上配置NAT:
R3(config)#access-list 101 permit ip 192.168.20.0 0.0.0.255 any
R3(config)#int lo 0
R3(config-if)#ip nat inside
R3(config)#int f2/0
R3(config-if)#ip nat outside
R3(config)#ip nat inside source list 101 interface f2/0 overload
R3#ping 2.2.2.2 source lo 0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 2.2.2.2, timeout is 2 seconds:
Packet sent with a source address of 192.168.20.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 4/16/60 ms
NAT配置已经成功了。
再次测试×××功能:
R1#ping 192.168.20.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.20.1, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
在R3上进行测试并查看加解密数:
R3#show crypto engine connections active
Crypto Engine Connections
ID Interface Type Algorithm Encrypt Decrypt IP-Address
5 Fa2/0 IPsec DES+MD5 0 9 23.1.1.3
6 Fa2/0 IPsec DES+MD5 4 0 23.1.1.3
1002 Fa2/0 IKE MD5+DES 0 0 23.1.1.3
R3#ping 192.168.10.10 source 192.168.20.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.10.10, timeout is 2 seconds:
Packet sent with a source address of 192.168.20.1
U.U.U
Success rate is 0 percent (0/5)
R3#show crypto engine connections active
Crypto Engine Connections
ID Interface Type Algorithm Encrypt Decrypt IP-Address
5 Fa2/0 IPsec DES+MD5 0 9 23.1.1.3
6 Fa2/0 IPsec DES+MD5 4 0 23.1.1.3
1002 Fa2/0 IKE MD5+DES 0 0 23.1.1.3
发现通过×××的连接已经无法ping通了,问题现在已经出来了。并且可以看到在ping前后的加解密数量是一样的,数据包根本没有经过加解密。
分析问题:
造成这个问题的原因是由于路由器设备在处理由内到外的流量的时候,NAT技术是优于加密技术的。当源是192.168.20.1的包去往192.168.10.10的时候,192.168.20.1已经被转换成了23.1.1.3,而转换后的流量不再满足感兴趣流,因而这个数据包会被转发到互联网。当数据包到达互联网后(即R2模拟),发现路由表中没有192.168.20.0的路由器,于是返回一个主机不可达的消息给R3。
问题解决:
在一台设备即做NAT又做×××的情况下,将×××的流量进行bypass处理,让它不必经过NAT处理即可。
R3(config)#ip access-list extended 101
R3(config-ext-nacl)#5 deny ip 192.168.20.0 0.0.0.255 192.168.10.0 0.0.0.255
R3#ping 192.168.10.10 source 192.168.20.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.10.10, timeout is 2 seconds:
Packet sent with a source address of 192.168.20.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 60/95/140 ms
发现可以ping通了。
ASA的NAT和××× bypass:
ASA8.4之前使用NAT 0:
ASA8.4之后使用twice NAT:
object network PAT
subnet 0.0.0.0 0.0.0.0
object network PAT
nat (inside,outside) dynamic interface
//以上命令意思是对inside接口去往Outside接口的流量进行动态地址转换
object network ×××-Inside
subnet 192.168.10.0 255.255.255.0
object network ×××-Outside
subnet 192.168.20.0 255.255.255.0
nat (inside,outside) source static ×××-Inside ×××-Inside destination static ×××-Outside ×××-Outside
//以上命令意思是对×××流量进行NAT转换,源还转换成源,目标IP还转换成目标IP,相当于没有转换,其实就是旁路×××流量
policy-map global_policy
class inspection_default
inspect icmp //对ping流量进行检测,否则ASA身后网络无法ping出去
验证:
R1#ping 2.2.2.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 2.2.2.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/27/68 ms
R1#ping 192.168.20.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.20.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 52/94/132 ms
R1即通ping通互联网上的地址2.2.2.2,也能ping通R3分站上的地址。