RE
re-150
- upx脱壳后,程序逻辑十分清晰,但出题人少了一位校验,所以造成题目多解,官网爆破
- 直接写脚本
a = [0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0]
a[0] = 166163712 / 1629056
a[1] = 731332800 / 6771600
a[2] = 357245568 / 3682944
a[3] = 1074393000 / 10431000
a[4] = 489211344 / 3977328
a[5] = 518971936 / 5138336
a[7] = 406741500 / 7532250
a[8] = 294236496 / 5551632
a[9] = 177305856 / 3409728
a[10] = 650683500 / 13013670
a[11] = 298351053 / 6088797
a[12] = 386348487 / 7884663
a[13] = 438258597 / 8944053
a[14] = 249527520 / 5198490
a[15] = 445362764 / 4544518
a[16] = 981182160 /10115280
a[17] = 174988800 / 3645600
a[18] = 493042704 / 9667504
a[19] = 257493600 / 5364450
a[20] = 767478780 / 13464540
a[21] = 312840624 / 5488432
a[22] = 1404511500 / 14479500
a[23] = 316139670 / 6451830
a[24] = 619005024 / 6252576
a[25] = 372641472 / 7763364
a[26] = 373693320 / 7327320
a[27] = 498266640 / 8741520
a[28] = 452465676 / 8871876
a[29] = 208422720 / 4086720
a[30] = 515592000 / 9374400
a[31] = 719890500 / 5759124
flag = ""
for i in a:
if i == 0:
flag+='1'
continue
flag += chr(i)
print flag
- flag{e165421110ba03099a1c039337}
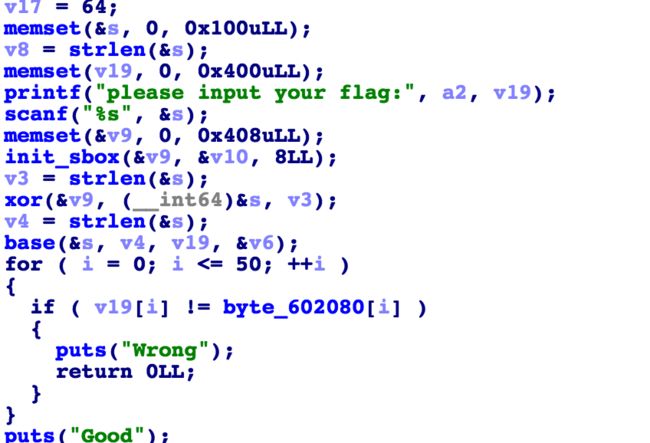
encrypt-300
程序分为三个步骤,最后再与已存储的密文进行比较,第一步为初始化类似s_box,然后再经过变换与输入进行异或,第三部对异或后的密文进行类似base64的变形编码
解密步骤,先将存储的密文解码,再通过初始化好的s_box通过爆破来得到flag
//解密密文
import time
a = 'Z`TzzTrD|fQP[_VVL|yneURyUmFklVJgLasJroZpHRxIUlH\\vZE='
print len(a)
c = []
for i in a:
if i != ' ':
c.append(ord(i)-61)
else:
c.append(0)
d = []
for i in range(0,len(c),4):
a1 = ((c[i]<<2) | (c[i+1]>>4) )&0xff
a2 = ( ((c[i+1]&0x3f)<<4) | (c[i+2]>>2) )&0xff
a3 = ( ((c[i+2]&0x3f)<<6) | c[i+3] )&0xff
d+=[a1,a2,a3]
s = ''
for i in d:
if i!=0:
#print "%02x"%i
s+="%02x"%i
# if len(s)%16 == 0 and len(s)!=8:
# print s[:16]
#print hex(i)
print(s)
//爆破flag
import time
middle_encrypt = [0x76,0x35,0xfd,0xf5,0x7d,0x47,0xfe,0x95,0x13,0x7a,0x26,0x59,
0x3f,0xff,0x31,0xa1,0x85,0x7c,0x63,0x02,0x6e,0xbd,0x93,0x6a,0x3e,0x4d,0x8d,0xd7,
0x27,0x73,0x2d,0x5e,0xcc,0x62,0xf2,0xdf,0xe5,0xd2]
s_box = [0x0,0x0,0xb0,0x31,0x75,0x70,0xf8,0xdf,0x07,0x3c,0x78,0x71,
0x50,0x29,0x2c,0x16,0x69,0x12,0xc8,0x2b,0x3b,0x7f,0xb2,0xe7,
0x4b,0x68,0x8c,0xc5,0xa6,0x15,0x03,0x58,0x47,0x04,0x13,0x8d,
0x87,0x26,0x09,0xed,0x17,0x8a,0xc2,0xf2,0x43,0xc0,0xac,0x59,
0x97,0xf5,0x3f,0x67,0x5e,0x39,0x86,0xd5,0x72,0x61,0xda,0xf7,
0x01,0x05,0x8b,0xc3,0xb1,0x77,0xaf,0x1d,0x30,0xc6,0x45,0x0e,
0x5f,0xee,0xae,0xf0,0x28,0xce,0xcd,0xa7,0x9b,0x2a,0x19,0x48,
0x08,0x44,0x20,0xfe,0x6d,0xb5,0x2e,0x6a,0xf1,0x34,0xbc,0x1e,
0x3e,0xcc,0x41,0x92,0xd8,0xbd,0xa5,0xe8,0x4d,0x0a,0x49,0x0d,
0xa2,0xfa,0x62,0x74,0xd4,0x83,0x96,0x94,0x3d,0xcb,0x18,0x63,
0x99,0x46,0xca,0xb7,0x8e,0xcf,0xfb,0xa3,0x6c,0x7e,0x51,0x27,
0x60,0x9a,0x11,0xf3,0x5c,0x6e,0xba,0x42,0x76,0x2f,0xef,0xbf,
0x21,0xaa,0xe4,0xd6,0x1b,0x55,0x7d,0xbe,0xea,0xd3,0x10,0xf4,
0xc7,0x4a,0x23,0x79,0x84,0xa4,0x1c,0xab,0x14,0xdb,0x4c,0x3a,
0xb8,0x52,0xec,0x37,0x38,0xb6,0xd2,0xa0,0x5a,0x5b,0x98,0x66,
0x54,0x9e,0x4e,0x4f,0xb4,0xc4,0xc9,0xd0,0x25,0x9c,0x80,0xde,
0x2d,0x06,0x22,0x0b,0x91,0x6b,0x9f,0xf6,0xe6,0xe2,0xc1,0x0f,
0x93,0x90,0x7b,0x9d,0x8f,0xdd,0xe5,0x65,0x35,0xad,0xa9,0xdc,
0x82,0xbb,0x00,0x53,0xd1,0xa8,0x33,0xe9,0x40,0x1a,0xff,0xa1,
0x95,0x36,0xd9,0xeb,0x89,0xe3,0x7c,0x73,0x85,0x88,0x7a,0xe0,
0xfd,0x64,0x0c,0x57,0x32,0xb3,0xb9,0x1f,0xd7,0xfc,0x81,0xe1,
0x02,0xf9,0x5d,0x56,0x6f,0x24]
v7 = s_box[0]
v8 = s_box[1]
v9 = s_box[2]
flag = ""
for i in range(39):
v7 = (v7+1)&0xff
print "v7:0x%x"%v7
v3 = s_box[v7+s_box.index(v9)]
print "v3:0x%x"%v3
v8 = (v8+v3)&0xff
print "V9: ",hex(v9)
v4 = s_box[s_box.index(v9)+v8]
s_box[s_box.index(v9)+v7] = v4
s_box[s_box.index(v9)+v8] = v3
key = s_box[s_box.index(v9)+((v3+v4)&0xff)]
for j in range(0x80):
if j ^ key == middle_encrypt[i]:
flag+=chr(j)
print flag
if chr(j) == '}':
exit()
- flag{e10adc3949ba59abbe56e057f20f883e}
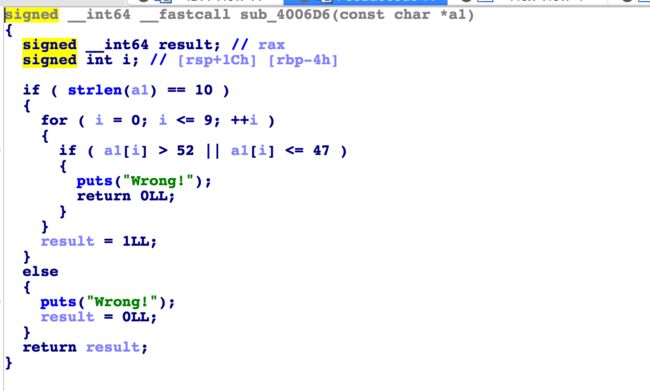
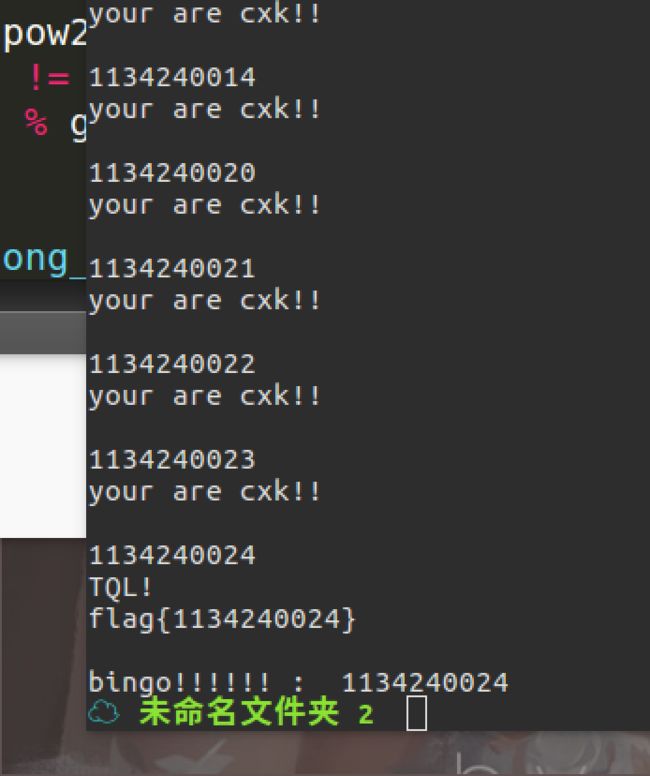
number game-400
- 虽然后面的逻辑较复杂,但是输入限制10位,且是0-4之间,直接写个脚本爆破,大概爆了1个小时吧
import subprocess
from itertools import *
list = '01234'
j = 0
for i in product(list, repeat=10):
input = "".join(i)
obj = subprocess.Popen(["./number_game"], stdin=subprocess.PIPE, stdout=subprocess.PIPE, stderr=subprocess.PIPE)
obj.stdin.write(input)
obj.stdin.close()
cmd_out = obj.stdout.read()
obj.stdout.close()
print input
print cmd_out
if 'cxk' not in cmd_out :
print "bingo!!!!!! : ",input
exit()
- flag{1134240024}
Web
-略
Crypto
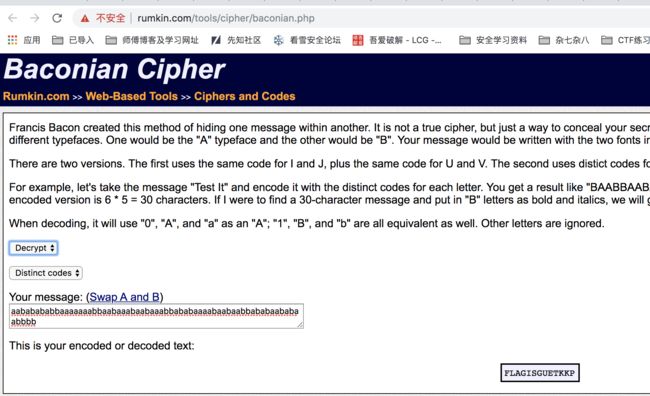
NO SOS-100
- 莫斯电码+培根密码,这里有个坑,需要把字母间隔和单词间隔去掉
- flag{guetkkp}
BabyRsa-200
- 给了p+q,(p+1)(q+1),所以n=pq=(p+1)(q+1)-(p+q)-1
import gmpy2
p_and_q = 0x1232fecb92adead91613e7d9ae5e36fe6bb765317d6ed38ad890b4073539a6231a6620584cea5730b5af83a3e80cf30141282c97be4400e33307573af6b25e2ea
p_1_q_1 = 0x5248becef1d925d45705a7302700d6a0ffe5877fddf9451a9c1181c4d82365806085fd86fbaab08b6fc66a967b2566d743c626547203b34ea3fdb1bc06dd3bb765fd8b919e3bd2cb15bc175c9498f9d9a0e216c2dde64d81255fa4c05a1ee619fc1fc505285a239e7bc655ec6605d9693078b800ee80931a7a0c84f33c851740
e = 0xe6b1bee47bd63f615c7d0a43c529d219
d = 0x2dde7fbaed477f6d62838d55b0d0964868cf6efb2c282a5f13e6008ce7317a24cb57aec49ef0d738919f47cdcd9677cd52ac2293ec5938aa198f962678b5cd0da344453f521a69b2ac03647cdd8339f4e38cec452d54e60698833d67f9315c02ddaa4c79ebaa902c605d7bda32ce970541b2d9a17d62b52df813b2fb0c5ab1a5
enc_flag = 0x50ae00623211ba6089ddfae21e204ab616f6c9d294e913550af3d66e85d0c0693ed53ed55c46d8cca1d7c2ad44839030df26b70f22a8567171a759b76fe5f07b3c5a6ec89117ed0a36c0950956b9cde880c575737f779143f921d745ac3bb0e379c05d9a3cc6bf0bea8aa91e4d5e752c7eb46b2e023edbc07d24a7c460a34a9a
n = p_1_q_1 - p_and_q - 1
plain = gmpy2.powmod(enc_flag,d,n)
print hex(plain)[2:].decode('hex')
- flag{cc7490e-78ab-11e9-b422-8ba97e5da1fd}
Uncle Sam-300
from Crypto.Util.number import *
import sys
def gcd(a, b):
if a < b:
a, b = b, a
while b != 0:
temp = a % b
a = b
b = temp
return a
def generkey(k):
p, q = getPrime(k), getPrime(k)
pubkey = p**2 * q
n = pubkey
l = (p-1)*(q-1) / gcd(p-1, q-1)
privkey = inverse(n, l)
return pubkey, privkey
def encrypt(m, pubkey):
return pow(bytes_to_long(m), pubkey, pubkey)
pubkey = 2188967977749378274223515689363599801320698247938997135947965550196681836543275429767581633044354412195352229175764784503562989045268075431206876726265968368605210824232207290410773979606662689866265612797103853982014198455433380266671856355564273196151136025319624636805659505233975208570409914054916955097594873702395812044506205943671404203774360656553350987491558491176962018842708476009578127303566834534914605109859995649555122751891647040448980718882755855420324482466559223748065037520788159654436293431470164057490350841209872489538460060216015196875136927502162027562546316560342464968237957692873588796640619530455268367136243313422579857823529592167101260779382665832380054690727358197646512896661216090677033395209196007249594394515130315041760988292009930675192749010228592156047159029095406021812884258810889225617544404799863903982758961208187042972047819358256866346758337277473016068375206319837317222523597
privkey = 1430375790065574721602196196929651174572674429040725535698217207301881161695296519567051246290199551982286327831985649037584885137134580625982555634409225551121712376849579015320947279716204424716566222721338735256648873164510429206991141648646869378141312253135997851908862030990576004173514556541317395106924370019574216894560447817319669690140544728277302043783163888037836675290468320723215759693903569878293475447370766682477726453262771004872749335257953507469109966448126634101604029506006038527612917418016783711729800719387298398848370079742790126047329182349899824258355003200173612567191747851669220766603
enc = 1491421391364871767357931639710394622399451019824572362288458431186299231664459957755422474433520889084351841298056066100216440853409346006657723086501921816381226292526490195810903459483318275931326433052468863850690793659405367902593999395060606972100169925074005992478583035226026829214443008941631771292291305226470216430735050944285543542354459162474346521327649934512511202470099020668235115245819634762067338432916012664452035696422865651002305445711778476072004708256200872226475346448360491248823843688268126341094612981308791499434770936360676087490303951728563482686307164877000300082742316368597958297217061375140696272398140310043942637287763946305961019518639745426370821124559939597559475362769382796386720030343305889701616194279058139516811941262747298761646317383112470923295543635754747288259324745583689440061956478083777663996487389553238481759103908588004219390662578446313004404784835263543083088327198
n = pubkey
d = privkey
pow2 = pow(2, n*d, n)
assert pow2 != 2
g = gcd(pow2 - 2, n)
assert g != 1 and g != n
assert n % g == 0
pq = g
print [long_to_bytes(pow(enc, d, pq))]
- flag{61e19444-7afb-11e9-b704-4ccc6adfc6f0}
MISC
KO-50
- Ook编码
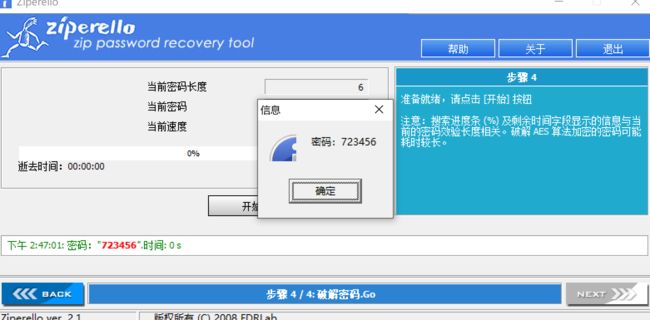
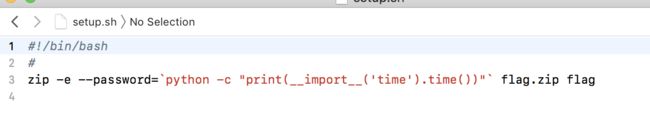
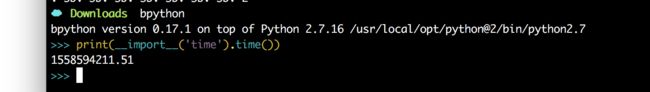
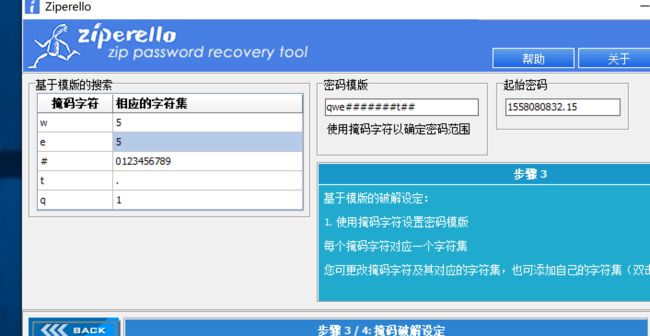
zips-300
先修复压缩包文件头
然后爆破222.zip的密码
- 然后111.zip伪加密弄出来
- 大概知道密码形式了,用掩码攻击
- flag{fkjabPqnLawhvuikfhgzyffj}
520的暗示
- dat文件需要与0x33异或后,得到一张图片,
- 根据LTE可以定位基站地址http://www.gpsspg.com/bs.htm
- 那么flag就是flag{桂林电子科技大学花江校区}
gadness
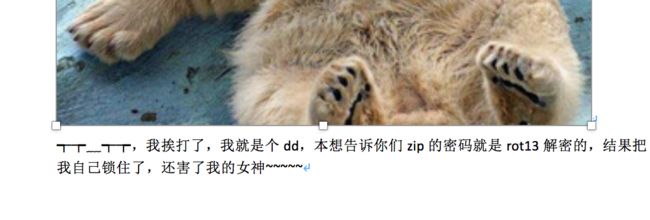
- 提示密码是6位字母,并且经过rot13加密,再在压缩包的十六进制末尾发现6位字母于是rot13解密后打开压缩包,有个doc文件与图片,但是图片损坏,word有个dd,于是跟520的暗示一个套路,异或
import subprocess
obj = subprocess.Popen(["./a.out","gadness.png","a.png","\xdd"], stdin=subprocess.PIPE, stdout=subprocess.PIPE, stderr=subprocess.PIPE)
cmd_out = obj.stdout.read()
obj.stdout.close()
print cmd_out
- 得到png图片后,用lsb获取隐藏文件,解密脚本, 相关用法介绍
- flag{72226ef09cf65b883508b2d9a8bec3a8}
MISC
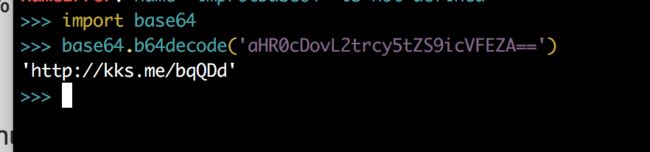
- 压缩包密码是密码(中文二字), 别问怎么知道的,问就出题人的锅,打开压缩包得到一张png图片,有个向下的箭头,修改图片高度
- flag{http://kks.me/bqQDd}
soul sipse
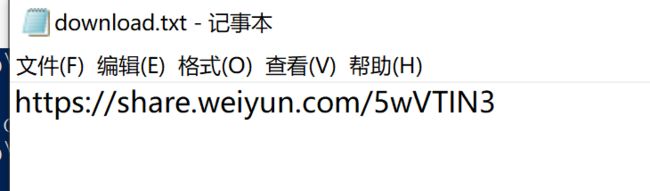
- 拿到音频文件,Audacity打开分析一下,在频谱图看到
- 于是需要寻找两个数字,用steghide可以提取出东西,密码是空密码
- 打开是个地址
- 访问地址下载的是一张损坏的图片,修复文件头
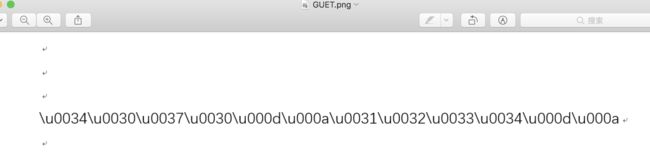
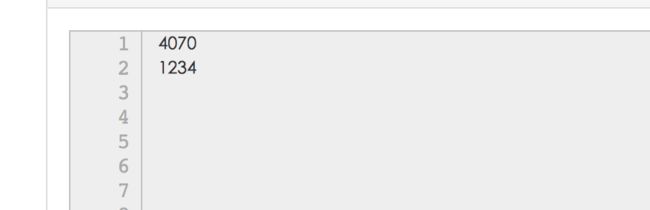
- 打开图片是unicode编码, 解码后得到两个数字
- flag{5304}
虚假的压缩包
- 虚假的压缩包是伪加密,数学题rsa的答案是5,所以真实的压缩包密码是答案是5
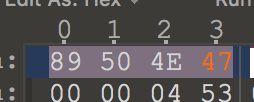
- 得到一张图片和一个文件,查看图片十六进制发现还是png,所以依旧改改高度
- 发现有个异或5的标志,与前面的异或加密是一个思路,不过这是单个字符异或
- 异或脚本
f1 = open('./cipher','r')
xor_data = f1.read()
f1.close()
dec_data = ""
for i in xor_data:
tmp = int(i,16) ^ 5
dec_data += hex(tmp)[2:]
f2 = open('./data.doc','wb')
f2.write(dec_data.decode('hex'))
f2.close()
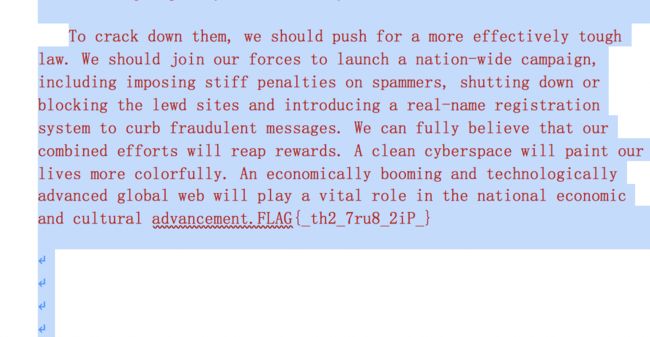
- 打开doc,将文字颜色调整一下
- FLAG{th2_7ru8_2iP}