今天我们进入《精通比特币》第三章,比特币实现参考,以及第四章的第一部分。第四章比较长,所以大家要有耐心,因为真正的学习就是沉下心慢慢看,慢慢品。
本章原文地址
https://github.com/bitcoinbook/bitcoinbook/blob/develop/ch03.asciidoc#compiling-bitcoin-core-from-the-source-code
第四章原文地址
https://github.com/bitcoinbook/bitcoinbook/blob/develop/ch04.asciidoc
相关文章:
《精通比特币》英文版批注导读·第1章
《精通比特币》英文版批注导读•第2章比特币工作原理
第3章比特币实现参考
Bitcoin Core: The Reference Implementation
Bitcoin is an open source project and the source code is available under an open (MIT) license, free to download and use for any purpose. Open source means more than simply free to use. It also means that bitcoin is developed by an open community of volunteers. At first, that community consisted of only Satoshi Nakamoto. By 2016, bitcoin’s source code had more than 400 contributors with about a dozen developers working on the code almost full-time and several dozen more on a part-time basis. Anyone can contribute to the code—including you!
比特币的代码是公开的,由社区共同维护。到2016年,已经有400多位代码贡献者。你也可以给代码提建议(前提是你能看得懂)。
When bitcoin was created by Satoshi Nakamoto, the software was actually completed before the whitepaper reproduced in [satoshi_whitepaper] was written. Satoshi wanted to make sure it worked before writing about it. That first implementation, then simply known as "Bitcoin" or "Satoshi client," has been heavily modified and improved. It has evolved into what is known as Bitcoin Core, to differentiate it from other compatible implementations. Bitcoin Core is the reference implementation of the bitcoin system, meaning that it is the authoritative reference on how each part of the technology should be implemented. Bitcoin Core implements all aspects of bitcoin, including wallets, a transaction and block validation engine, and a full network node in the peer-to-peer bitcoin network.
中本聪是先写完比特币的代码,再写白皮书的。不过比特币最初由中本聪实现的版本,已经大幅修改,并演进成“比特币核心”版本,这也是比特币的参考实现。比特币核心版本实现了比特币的各个方面,包括钱包、交易、块验证引擎、以及比特币网络的全节点。
Warning Even though Bitcoin Core includes a reference implementation of a wallet, this is not intended to be used as a production wallet for users or for applications. Application developers are advised to build wallets using modern standards such as BIP-39 and BIP-32 (see [mnemonic_code_words] and [hd_wallets]). BIP stands for Bitcoin Improvement Proposal.
尽管有比特币参考实现,但是仍然建议采用更新的修正版本,例如BIP-39或者BIP-32.
Bitcoin Core architecture (Source: Eric Lombrozo) shows the architecture of Bitcoin Core.
Figure 1. Bitcoin Core architecture (Source: Eric Lombrozo)
下面讲的就是如何在你的计算机上部署比特币,由于有较多计算机指令,建议读者自行阅读原文,根据指示步骤处理。
https://github.com/bitcoinbook/bitcoinbook/blob/develop/ch03.asciidoc#compiling-bitcoin-core-from-the-source-code
第4章比特币密钥与地址(第一部分)
这一章将进入密码学的范畴。
https://github.com/bitcoinbook/bitcoinbook/blob/develop/ch04.asciidoc
Keys, Addresses
You may have heard that bitcoin is based on cryptography, which is a branch of mathematics used extensively in computer security. Cryptography means "secret writing" in Greek, but the science of cryptography encompasses more than just secret writing, which is referred to as encryption. Cryptography can also be used to prove knowledge of a secret without revealing that secret (digital signature), or prove the authenticity of data (digital fingerprint). These types of cryptographic proofs are the mathematical tools critical to bitcoin and used extensively in bitcoin applications. Ironically, encryption is not an important part of bitcoin, as its communications and transaction data are not encrypted and do not need to be encrypted to protect the funds. In this chapter we will introduce some of the cryptography used in bitcoin to control ownership of funds, in the form of keys, addresses, and wallets.
密码学的英文单词的希腊语含义是“秘密书写”,也就是所谓的加密。除了加密,还能可以在不泄密的情况下证明自己掌握了秘密(签名)以及证明数据真实性(电子指纹)。加密不是比特币中的重要属性,因为比特币中的交易公开,并不需要通过加密来保证其安全性。本章将介绍比特币中采用的密码技术。
Introduction
Ownership of bitcoin is established through digital keys, bitcoin addresses, and digital signatures. The digital keys are not actually stored in the network, but are instead created and stored by users in a file, or simple database, called a wallet. The digital keys in a user’s wallet are completely independent of the bitcoin protocol and can be generated and managed by the user’s wallet software without reference to the blockchain or access to the internet. Keys enable many of the interesting properties of bitcoin, including decentralized trust and control, ownership attestation, and the cryptographic-proof security model.
比特币的所有权是通过电子密钥、比特币地址以及电子签名构成。电子密钥不保存在比特币网络,仅仅存在用户的钱包中,而且不需要连网或者连区块链就能访问到。
Most bitcoin transactions require a valid digital signature to be included in the blockchain, which can only be generated with a secret key; therefore, anyone with a copy of that key has control of the bitcoin. The digital signature used to spend funds is also referred to as a witness, a term used in cryptography. The witness data in a bitcoin transaction testifies to the true ownership of the funds being spent.
大部分比特币交易需要有效数字签名,这个签名只能由用户密钥完成。我们可以把用户私钥签名的过程,想象成红头文件盖的章,签名其实和盖章一样。一般人拿不到公章,于是当你看到公章的时候,你就知道这是经过授权的。
Keys come in pairs consisting of a private (secret) key and a public key. Think of the public key as similar to a bank account number and the private key as similar to the secret PIN, or signature on a check, that provides control over the account. These digital keys are very rarely seen by the users of bitcoin. For the most part, they are stored inside the wallet file and managed by the bitcoin wallet software.
用户的密钥往往是由一对密钥组成,一个是公钥,一个是私钥。公钥就是公开的字符串,网上任何人都可以查到,有点像我们的银行账号一样,公布出去才能收到别人给我们的转账。私钥就像账号的密码,只有你才有。在比特币当中,大部分情况下用户不接触私钥,被保存在比特币钱包软件中。
In the payment portion of a bitcoin transaction, the recipient’s public key is represented by its digital fingerprint, called a bitcoin address, which is used in the same way as the beneficiary name on a check (i.e., "Pay to the order of"). In most cases, a bitcoin address is generated from and corresponds to a public key. However, not all bitcoin addresses represent public keys; they can also represent other beneficiaries such as scripts, as we will see later in this chapter. This way, bitcoin addresses abstract the recipient of funds, making transaction destinations flexible, similar to paper checks: a single payment instrument that can be used to pay into people’s accounts, pay into company accounts, pay for bills, or pay to cash. The bitcoin address is the only representation of the keys that users will routinely see, because this is the part they need to share with the world.
在比特币的支付过程中,收方的公钥由一串数字指纹公开表示,被称作比特币地址。大多数情况比特币地址是由收方的公钥生成,但是并不是所有的比特币地址都如此,有的也可以由脚本来代替。这样一个比特币的地址就可以有多种功能,比如说,向个人账户支付、向公司的账户支付、支付账单或者支付现金等。
First, we will introduce cryptography and explain the mathematics used in bitcoin. Next, we will look at how keys are generated, stored, and managed. We will review the various encoding formats used to represent private and public keys, addresses, and script addresses. Finally, we will look at advanced use of keys and addresses: vanity, multisignature, and script addresses and paper wallets.
Public Key Cryptography and Cryptocurrency
Public key cryptography was invented in the 1970s and is a mathematical foundation for computer and information security.
公钥密码学于20世纪70年代发明,是信息安全的数学基础。
Since the invention of public key cryptography, several suitable mathematical functions, such as prime number exponentiation and elliptic curve multiplication, have been discovered. These mathematical functions are practically irreversible, meaning that they are easy to calculate in one direction and infeasible to calculate in the opposite direction. Based on these mathematical functions, cryptography enables the creation of digital secrets and unforgeable digital signatures. Bitcoin uses elliptic curve multiplication as the basis for its cryptography.
公钥密码学最开始是一种概念设想,之后数学家们找到了合适的数学模型用于实现。比如素数的指数运算以及椭圆曲线乘法的数学特性被相继用来构造数学函数,这些函数的一个特点是计算不可逆。不可逆的意思是,函数正向运算比较简单,逆运算却非常困难。基于这样单向不对等性,才能构造出密码学的算法安全性。比特币采用了椭圆曲线乘法作为密码学的基础。
In bitcoin, we use public key cryptography to create a key pair that controls access to bitcoin. The key pair consists of a private key and—derived from it—a unique public key. The public key is used to receive funds, and the private key is used to sign transactions to spend the funds.
There is a mathematical relationship between the public and the private key that allows the private key to be used to generate signatures on messages. This signature can be validated against the public key without revealing the private key.
比特币用公私钥对来进行安全控制。公钥拿来收钱,私钥在花钱时拿来签名。签名了以后可以用公钥验证真伪,这样私钥也不会泄露。
When spending bitcoin, the current bitcoin owner presents her public key and a signature (different each time, but created from the same private key) in a transaction to spend those bitcoin. Through the presentation of the public key and signature, everyone in the bitcoin network can verify and accept the transaction as valid, confirming that the person transferring the bitcoin owned them at the time of the transfer.
花钱的时候,手里拿着钱的人,就要把自己的公钥以及经过签名的交易信息公布出来。签名相当于依据私钥和待签名的交易,生成一个字符串,这样,每次的签名都不一样。
Tip: In most wallet implementations, the private and public keys are stored together as a key pair for convenience. However, the public key can be calculated from the private key, so storing only the private key is also possible.
大多数钱包会把公钥与私钥存在一块,实际上,根据私钥可以算出公钥。所以其实只存私钥也够。
Private and Public Keys
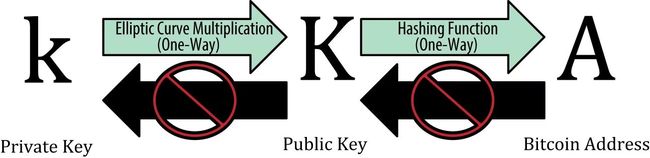
A bitcoin wallet contains a collection of key pairs, each consisting of a private key and a public key. The private key (k) is a number, usually picked at random. From the private key, we use elliptic curve multiplication, a one-way cryptographic function, to generate a public key (K). From the public key (K), we use a one-way cryptographic hash function to generate a bitcoin address (A). In this section, we will start with generating the private key, look at the elliptic curve math that is used to turn that into a public key, and finally, generate a bitcoin address from the public key. The relationship between private key, public key, and bitcoin address is shown in Private key, public key, and bitcoin address.
比特币中,私钥P是随机选择的一个数,公钥K由私钥根据椭圆曲线算法生成,比特币地址是根据公钥随机生成的一串字符。
Figure 1. Private key, public key, and bitcoin address
Why Use Asymmetric Cryptography (Public/Private Keys)?
Why is asymmetric cryptography used in bitcoin? It’s not used to "encrypt" (make secret) the transactions. Rather, the useful property of asymmetric cryptography is the ability to generate digital signatures. A private key can be applied to the digital fingerprint of a transaction to produce a numerical signature. This signature can only be produced by someone with knowledge of the private key. However, anyone with access to the public key and the transaction fingerprint can use them to verify the signature. This useful property of asymmetric cryptography makes it possible for anyone to verify every signature on every transaction, while ensuring that only the owners of private keys can produce valid signatures.
注意,在密码学里有对称密码与非对称密码(公钥密码)的区分。对称密码就是传统中的加密,把一段信息用各种变换方法,转换成密文,在没有密码的情况下,你无法知道信息。这里加密和解密都采用同样的密码。非对称密码有一个特点,就是会有两个密钥,一公一私。公的可以公开,私的保密,仅供使用者所有。而用私钥签名就是,用只有你掌握的信息生成一串数字签名,这串数字签名,任何其他人无法生成;而且其他人可以根据这串签名,用你的公钥验证,这的确是你签的。
这个有点类似,你去银行取钱,你只要掌握了你的银行卡密码,任何工作人员验证了是你,就可以给你钱,而不需要和你认识。
推荐阅读一篇清华大学关于王小云教授的报道清华人物 | 解密王小云院士
Private Keys
A private key is simply a number, picked at random. Ownership and control over the private key is the root of user control over all funds associated with the corresponding bitcoin address. The private key is used to create signatures that are required to spend bitcoin by proving ownership of funds used in a transaction. The private key must remain secret at all times, because revealing it to third parties is equivalent to giving them control over the bitcoin secured by that key. The private key must also be backed up and protected from accidental loss, because if it’s lost it cannot be recovered and the funds secured by it are forever lost, too.
私钥的保密就意味着全部。谁掌握了私钥,谁就掌握了私钥对应的所有钱。如果你丢失了私钥,那这笔钱你也永远拿不回来。如果你要生成私钥,可以随机选择一个数字,或者扔256次硬币。
Tip: The bitcoin private key is just a number. You can pick your private keys randomly using just a coin, pencil, and paper: toss a coin 256 times and you have the binary digits of a random private key you can use in a bitcoin wallet. The public key can then be generated from the private key.
Generating a private key from a random number
The first and most important step in generating keys is to find a secure source of entropy, or randomness. Creating a bitcoin key is essentially the same as "Pick a number between 1 and 2256." The exact method you use to pick that number does not matter as long as it is not predictable or repeatable. Bitcoin software uses the underlying operating system’s random number generators to produce 256 bits of entropy (randomness). Usually, the OS random number generator is initialized by a human source of randomness, which is why you may be asked to wiggle your mouse around for a few seconds.
More precisely, the private key can be any number between 0 and n - 1 inclusive, where n is a constant (n = 1.1578 * 1077, slightly less than 2256) defined as the order of the elliptic curve used in bitcoin (see Elliptic Curve Cryptography Explained). To create such a key, we randomly pick a 256-bit number and check that it is less than n. In programming terms, this is usually achieved by feeding a larger string of random bits, collected from a cryptographically secure source of randomness, into the SHA256 hash algorithm, which will conveniently produce a 256-bit number. If the result is less than n, we have a suitable private key. Otherwise, we simply try again with another random number.
私钥的选取就是在1到 2的256次方中,随机选择一个小于n的数。为了确保足够随机,会再做一些处理;同时,还需要满足椭圆曲线的基本要求。
Warning: Do not write your own code to create a random number or use a "simple" random number generator offered by your programming language. Use a cryptographically secure pseudorandom number generator (CSPRNG) with a seed from a source of sufficient entropy. Study the documentation of the random number generator library you choose to make sure it is cryptographically secure. Correct implementation of the CSPRNG is critical to the security of the keys.
这里要注意的是,不要随便用简单的随机数生成器生成随机数,安全性可能会受到影响。
The following is a randomly generated private key (k) shown in hexadecimal format (256 bits shown as 64 hexadecimal digits, each 4 bits):
Tip : The size of bitcoin’s private key space, (2^256) is an unfathomably large number. It is approximately 10^77 in decimal. For comparison, the visible universe is estimated to contain 10^80 atoms.
注意2的256次方是非常大的样本空间,接近10^77次方,目前观测到的宇宙的包括的原子数是10^80个。
本节的以下部分主要讲了怎么在系统上查看自己的私钥。
To generate a new key with the Bitcoin Core client (see [ch03_bitcoin_client]), use the getnewaddress command. For security reasons it displays the public key only, not the private key. To ask bitcoind to expose the private key, use the dumpprivkey command. The dumpprivkey command shows the private key in a Base58 checksum-encoded format called the Wallet Import Format (WIF), which we will examine in more detail in Private key formats. Here’s an example of generating and displaying a private key using these two commands:
The dumpprivkey command opens the wallet and extracts the private key that was generated by the getnewaddress command. It is not possible for bitcoind to know the private key from the public key unless they are both stored in the wallet.
Tip The dumpprivkey command does not generate a private key from a public key, as this is impossible. The command simply reveals the private key that is already known to the wallet and which was generated by the getnewaddress command.
You can also use the Bitcoin Explorer command-line tool (see [appdx_bx]) to generate and display private keys with the commands seed, ec-new, and ec-to-wif:
Public Keys
The public key is calculated from the private key using elliptic curve multiplication, which is irreversible: K = k * G, where k is the private key, G is a constant point called the generator point, and K is the resulting public key. The reverse operation, known as "finding the discrete logarithm"—calculating k if you know K—is as difficult as trying all possible values of k, i.e., a brute-force search. Before we demonstrate how to generate a public key from a private key, let’s look at elliptic curve cryptography in a bit more detail.
在椭圆曲线上有一种称作“点乘”的运算,可以用公式 K = k * G表示。G就是椭圆曲线上的一个点,k就是随机选择的一个私钥。椭圆曲线有这样一个性质,从小写的k算出大写K很容易,但是由大写K反推小写k有难度。这种反推就叫做“求离散对数”,这个问题在计算上是很难的。这种数学上的特性,就是构造公钥密码学的基石,也是比特币用来证明货币归属的重要技术手段。
Tip Elliptic curve multiplication is a type of function that cryptographers call a "trap door" function: it is easy to do in one direction (multiplication) and impossible to do in the reverse direction (division). The owner of the private key can easily create the public key and then share it with the world knowing that no one can reverse the function and calculate the private key from the public key. This mathematical trick becomes the basis for unforgeable and secure digital signatures that prove ownership of bitcoin funds.
Elliptic Curve Cryptography Explained
Elliptic curve cryptography is a type of asymmetric or public key cryptography based on the discrete logarithm problem as expressed by addition and multiplication on the points of an elliptic curve.
椭圆曲线密码学是一种非对称的公钥密码学,依托有限域上的离散对数问题。在椭圆曲线上,运算是通过点的加法与标量乘法来实现。椭圆曲线有非常遥远的历史,可以追溯到数论里的整除的问题。这部分我们先不展开,你可以理解为一个二元三次方程对应在坐标轴上绘出的曲线。
An elliptic curve is an example of an elliptic curve, similar to that used by bitcoin.
Figure 2. An elliptic curve
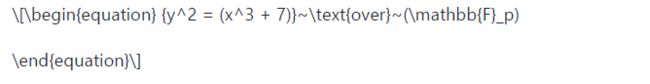
Bitcoin uses a specific elliptic curve and set of mathematical constants, as defined in a standard called secp256k1, established by the National Institute of Standards and Technology (NIST). The secp256k1 curve is defined by the following function, which produces an elliptic curve:
比特币采用了以下参数的椭圆曲线y^2 = (x^3 + 7),这里读者应该能对接上高中的数学知道了。
or
这里作者加了一个模操作,模在数学里是一个很有张力的特性。模p就是把一个数除以p,然后取余数,于是得到的结果无非就是从0到p-1。所以把上面的方程求模,本质上就映射到了一个有限的离散域上,当变成了离散的数以后,就不能画出曲线,而是一个又一个的点了。更多知识涉及到了抽象代数的概念,这里先不展开了。
Because this curve is defined over a finite field of prime order instead of over the real numbers, it looks like a pattern of dots scattered in two dimensions, which makes it difficult to visualize. However, the math is identical to that of an elliptic curve over real numbers. As an example, Elliptic curve cryptography: visualizing an elliptic curve over F(p), with p=17 shows the same elliptic curve over a much smaller finite field of prime order 17, showing a pattern of dots on a grid. The secp256k1 bitcoin elliptic curve can be thought of as a much more complex pattern of dots on a unfathomably large grid.
Figure 3. Elliptic curve cryptography: visualizing an elliptic curve over F(p), with p=17
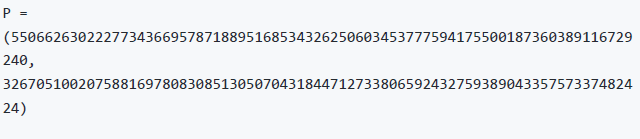
So, for example, the following is a point P with coordinates (x,y) that is a point on the secp256k1 curve:
这里举了一个例子,在曲线上选择了一个点,代入到方程里正好等式成立。你可以用参数自己在计算机上算一下。
Using Python to confirm that this point is on the elliptic curve shows how you can check this yourself using Python:
Example 1. Using Python to confirm that this point is on the elliptic curve
In elliptic curve math, there is a point called the "point at infinity," which roughly corresponds to the role of zero in addition. On computers, it’s sometimes represented by x = y = 0 (which doesn’t satisfy the elliptic curve equation, but it’s an easy separate case that can be checked).
椭圆曲线上有一个“无穷远点”,有点像加法中的0一样。也有一个加的运算,就和我们小学学的数的加法一样。
There is also a + operator, called "addition," which has some properties similar to the traditional addition of real numbers that gradeschool children learn. Given two points P1 and P2 on the elliptic curve, there is a third point P3 = P1 + P2, also on the elliptic curve.
Geometrically, this third point P3 is calculated by drawing a line between P1 and P2. This line will intersect the elliptic curve in exactly one additional place. Call this point P3' = (x, y). Then reflect in the x-axis to get P3 = (x, –y).
There are a couple of special cases that explain the need for the "point at infinity."
假设有P3 = P1 + P2,,那么P3的结果就是,连接P1和P2点的线,与椭圆曲线的交点,再取x轴的对称点。当然,如果P1和P2是同一个点,那么这条线就变成了曲线的切线,也就代表了此处的斜率。
If P1 and P2 are the same point, the line "between" P1 and P2 should extend to be the tangent on the curve at this point P1. This tangent will intersect the curve in exactly one new point. You can use techniques from calculus to determine the slope of the tangent line. These techniques curiously work, even though we are restricting our interest to points on the curve with two integer coordinates!
In some cases (i.e., if P1 and P2 have the same x values but different y values), the tangent line will be exactly vertical, in which case P3 = "point at infinity."
If P1 is the "point at infinity," then P1 + P2 = P2. Similarly, if P2 is the point at infinity, then P1 + P2 = P1. This shows how the point at infinity plays the role of zero.
如果P1和P2关于x轴对称,那连接P1和P2的点就变成垂线,斜率无穷大,P3就会是“无穷远”点。
It turns out that + is associative, which means that (A + B) + C = A + (B + C). That means we can write A + B + C without parentheses and without ambiguity.
在这里,点的加法满足结合律,所以A+B+C不需要通过括号来框定优先级。
Now that we have defined addition, we can define multiplication in the standard way that extends addition. For a point P on the elliptic curve, if k is a whole number, then kP = P + P + P + … + P (k times). Note that k is sometimes confusingly called an "exponent" in this case.
把k个P相加,用一个乘法表示,于是就中kP,这就是标量乘法,k也可以称作是指数。
Generating a Public Key
Starting with a private key in the form of a randomly generated number k, we multiply it by a predetermined point on the curve called the generator point G to produce another point somewhere else on the curve, which is the corresponding public key K. The generator point is specified as part of the secp256k1 standard and is always the same for all keys in bitcoin:
where k is the private key, G is the generator point, and K is the resulting public key, a point on the curve. Because the generator point is always the same for all bitcoin users, a private key k multiplied with G will always result in the same public key K. The relationship between k and K is fixed, but can only be calculated in one direction, from k to K. That’s why a bitcoin address (derived from K) can be shared with anyone and does not reveal the user’s private key (k).
比特币生成公钥,是通过一确定的生成子G,乘以随机选择的私钥 k 达成的效果。知道私钥可以生成公钥,反之却不行,这是前文已经介绍过的特性。
Tip A private key can be converted into a public key, but a public key cannot be converted back into a private key because the math only works one way.
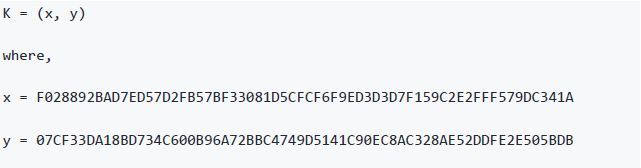
Implementing the elliptic curve multiplication, we take the private key k generated previously and multiply it with the generator point G to find the public key K:
Public key K is defined as a point K = (x,y):
To visualize multiplication of a point with an integer, we will use the simpler elliptic curve over real numbers—remember, the math is the same. Our goal is to find the multiple kG of the generator point G, which is the same as adding G to itself, k times in a row. In elliptic curves, adding a point to itself is the equivalent of drawing a tangent line on the point and finding where it intersects the curve again, then reflecting that point on the x-axis.
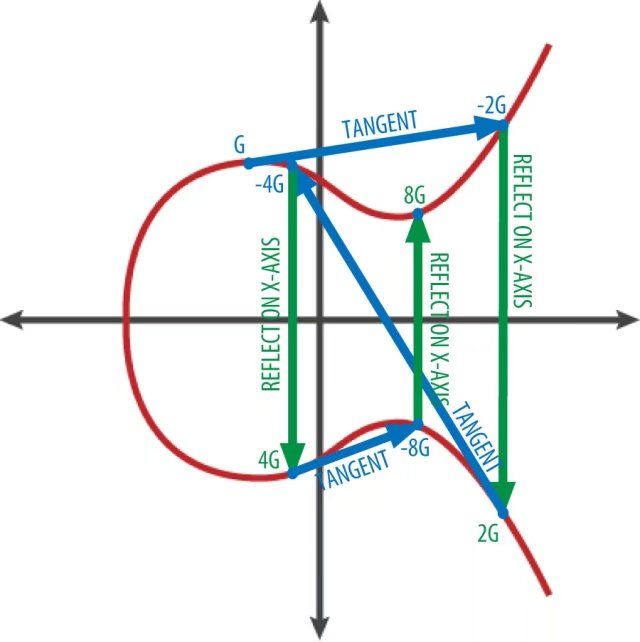
Elliptic curve cryptography: visualizing the multiplication of a point G by an integer k on an elliptic curve shows the process for deriving G, 2G, 4G, as a geometric operation on the curve.
这里作者用可视化的方式,展示了椭圆曲线上加法的过程。
从G算到8G就是
G+G=2G,2G+2G=4G,4G+4G=8G这样演示的。
Tip Most bitcoin implementations use the OpenSSL cryptographic library to do the elliptic curve math. For example, to derive the public key, the function EC_POINT_mul() is used.
利用OpenSSL密码库可以做椭圆曲线的运算。我在大学的时候玩过这个密码库的源码。
Figure 4. Elliptic curve cryptography: visualizing the multiplication of a point G by an integer k on an elliptic curve
后面讲的深入很多,本来想一次全部推送完的,但是公众号字数限制了,下一篇再接着推。
欢迎大家关注我的新号,“刻意学习区块链”,我会把我所有关于区块链和比特币学习解析的文章,汇总在上面便于检索,这是ScalersTalk成长持续论的一个分叉。 搜索“刻意学习区块链”关注。