攻防世界--misc--新手区
0x01 this_is_flag
Most flags are in the form flag{xxx}, for example:flag{th1s_!s_a_d4m0_4la9}
flag{th1s_!s_a_d4m0_4la9}
0x02 ext3
今天是菜狗的生日,他收到了一个linux系统光盘
将linux系统光盘放在linux下,在linux光盘目录下使用strings linux|grep flag,查找与flag相关的文件;root模式下使用mount linux /mnt命令将linux光盘挂载在mnt目录下,切换到mnt目录,使用cat O7avZhikgKgbF/flag.txt命令即可对flag内容进行读取,发现是一个base64编码,解密后得到flag.
flag{sajbcibzskjjcnbhsbvcjbjszcszbkzj}
0x03 give_you_flag
菜狗找到了文件中的彩蛋很开心,给菜猫发了个表情包
一个.gif图片,用stegsolve的查看帧的功能模块查看,发现一个缺少三个定位部分的二维码,将其补全,扫一扫即可。
flag{e7d478cf6b915f50ab1277f78502a2c5}
https://cli.im/news/help/10601
https://blog.csdn.net/hk_5788/article/details/50839790
https://zhuanlan.zhihu.com/p/21463650
https://www.jianshu.com/p/8208aad537bb
0x04 pdf
菜猫给了菜狗一张图,说图下面什么都没有
将文件打开,删除掉最外面的图片,flag便显示出来了
flag{security_through_obscurity}
0x05 坚持60s
菜狗发现最近菜猫不爱理他,反而迷上了菜鸡
下载发现是一个.jar的游戏,使用java反编译工具,查看源码,得到flag.
flag{RGFqaURhbGlfSmlud2FuQ2hpamk=}
0x06 如来十三掌
菜狗为了打败菜猫,学了一套如来十三掌。
在“与佛论禅”解密,得到一段疑似base64的编码,如来十三掌,rot13一下,再base64解密即可得到flag.
flag{bdscjhbkzmnfrdhbvckijndskvbkjdsab}
0x07 gif
菜狗截获了一张菜鸡发给菜猫的动态图,却发现另有玄机
打开压缩包发现许多张黑白颜色的图片,将黑白图片分别记为1,0,得到01100110011011000110000101100111011110110100011001110101010011100101111101100111011010010100011001111101,转化为字符串形式即可。
#gif 二进制转字符串
import re
a = ‘01100110011011000110000101100111011110110100011001110101010011100101111101100111011010010100011001111101’
b = re.findall(r’.{8}’,a)
flag = ‘’
for i in b:
flag += chr(int(i,2))
print(flag)
flag{FuN_giF}
0x08 SimpleRAR
菜狗最近学会了拼图,这是他刚拼好的,可是却搞错了一块(ps:双图层)
将压缩包直接解压,发现压缩包损坏,但得到了一个flag.txt,根据提示flag应该在剩余的文件中,将压缩包放在winhex下,根据flag.txt的内容,补齐图片格式再次解压得到一个空白图片,放在winhex下,发现是一个.gif图片,使用stegsolve帧功能模块,得到两张不同的帧图片,调节颜色,得到两张残缺的二维码图片,合并补齐后,扫一扫即可。
flag{yanji4n_bu_we1shi}
0x09 stegano
菜狗收到了图后很开心,玩起了pdf(flag格式为大写)
用google浏览器中打开pdf文件,然后Ctrl+A选中所有文字,在Ctrl+C复制,接着粘贴到一个txt文本中
flag{1NV151BL3M3554G3}
0x10 掀桌子
菜狗截获了一份报文如下c8e9aca0c6f2e5f3e8c4efe7a1a0d4e8e5a0e6ece1e7a0e9f3baa0e8eafae3f9e4eafae2eae4e3eaebfaebe3f5e7e9f3e4e3e8eaf9eaf3e2e4e6f2,生气地掀翻了桌子(╯°□°)╯︵ ┻━┻
通过观察,试着将16进制字符转为字符串,发现不能直接转化,试着将ascii码值减去128再转化,得到flag.
flag{hjzcydjzbjdcjkzkcugisdchjyjsbdfr}
0x11 功夫再高也怕菜刀
菜狗决定用菜刀和菜鸡决一死战
foremost分离文件,得到一个加密的压缩包,点进去查看发现一个flag.txt文件,wireshark下查找flag.txt字符串,追踪TCP流,最终在第1150个包发现一段图片的16进制编码,将其用winhex另存为一个图片,得到压缩包的密码,解压得到flag.
flag{3OpWdJ-JP6FzK-koCMAK-VkfWBq-75Un2z}
0x12 base64stego
今天在攻防世界上看见了一道关于base64隐写的题目,题目链接如下:
题目链接
打开压缩包提示需要输入密码,就打开压缩包的详细信息,但是什么都没有,然后就打开binwalk,查看发现没有隐藏文件。
然后想到可能是zip伪加密:
zip文件有三个部分组成:压缩源文件数据区(第一个50 4B)+压缩源文件目录区(第二个50 4B)+压缩源文件目录结束标志(第三个50 4B)
伪加密一般存在于压缩源文件目录区,也就是第二个50 4B之后。
压缩源文件目录区:50 4B 01 02:目录中文件文件头标记
3F 03:压缩使用的 pkware版本
14 03:解压文件所需 pkware 版本
09 00:全局方式位标记(有无加密,这个更改这里进行伪加密,改为00 08打开就会提示有密码了)
使用winhex(或者C32ASM)打开文件后,找到第二个50 4B,往后数第七个和第八个,正常情况下应该是00 08,但这里是09 00;

修改完之后就可以正常解压了 ,打开txt之后,发现内容是base64加密过的
U3RlZ2Fub2dyYXBoeSBpcyB0aGUgYXJ0IGFuZCBzY2llbmNlIG9m
IHdyaXRpbmcgaGlkZGVuIG1lc3NhZ2VzIGluIHN1Y2ggYSB3YXkgdGhhdCBubyBvbmV=
LCBhcGFydCBmcm9tIHRoZSBzZW5kZXIgYW5kIGludGVuZGVkIHJlY2lwaWVudCwgc3VzcGU=
Y3RzIHRoZSBleGlzdGVuY2Ugb2YgdGhlIG1lc3M=
YWdlLCBhIGZvcm0gb2Ygc2VjdXJpdHkgdGhyb3VnaCBvYnNjdXJpdHkuIFS=
aGUgd29yZCBzdGVnYW5vZ3JhcGh5IGlzIG9mIEdyZWVrIG9yaWdpbiBhbmQgbWVhbnMgImNvbmNlYW==
bGVkIHdyaXRpbmciIGZyb20gdGhlIEdyZWVrIHdvcmRzIHN0ZWdhbm9zIG1lYW5pbmcgImNv
dmVyZWQgb3IgcHJvdGVjdGVkIiwgYW5kIGdyYXBoZWluIG1lYW5pbmcgInRvIHc=
cml0ZSIuIFRoZSBmaXJzdCByZWNvcmRlZCB1c2Ugb2YgdGhlIHRlcm0gd2FzIGluIDE0OTkgYnkgSm9o
YW5uZXMgVHJpdGhlbWl1cyBpbiBoaXMgU3RlZ2Fub2dyYXBoaWEsIGEgdHJlYV==
dGlzZSBvbiBjcnlwdG9ncmFwaHkgYW5kIHN0ZWdhbm9ncmFwaHkgZGlzZ8==
dWlzZWQgYXMgYSBib29rIG9uIG1hZ2ljLiBHZW5lcmFsbHksIG1lc3P=
YWdlcyB3aWxsIGFwcGVhciB0byBiZSBzb21ldGhpbmcgZWxzZTogaW1hZ2VzLCBhcnRp
Y2xlcywgc2hvcHBpbmcgbGlzdHMsIG9yIHNvbWUgb3R=
aGVyIGNvdmVydGV4dCBhbmQsIGNsYXNzaWNhbGx5LCB0aGUgaGlkZGVuIG1lc3NhZ2UgbWF5IGJlIGluIGludmm=
c2libGUgaW5rIGJldHdlZW4gdGhlIHZpc2libGUgbGluZXMgb2YgYSBwcml2YXRlIGxldHRlci4NCg0KVGhl
IGFkdmFudGFnZSBvZiBzdGVnYW5vZ3JhcGh5LCBvdmVyIGNy
eXB0b2dyYXBoeSBhbG9uZSwgaXMgdGhhdCBtZXNzYWdlcyBkbyBub3QgYXR0cmFjdCBhdHRlbnRpb25=
IHRvIHRoZW1zZWx2ZXMuIFBsYWlubHkgdmlzaWJsZSBlbmNyeXB0ZWQgbWVzc2FnZXOXbm8gbWF0dGVyIF==
aG93IHVuYnJlYWthYmxll3dpbGwgYXJvdXNlIHN=
dXNwaWNpb24sIGFuZCBtYXkgaW4gdGhlbXNlbHZlcyBiZSBpbmNyaW1pbmF0aW5nIP==
aW4gY291bnRyaWVzIHdoZXJlIGVuY3J5cHRpb24gaXMgaWxsZWdhbC4gVGhlcmVmb3JlLH==
IHdoZXJlYXMgY3J5cHRvZ3JhcGh5IHByb3RlY3RzIHRoZSBjb250ZW50cyBvZj==
IGEgbWVzc2FnZSwgc3RlZ2Fub2dyYXBoeSBjYW4gYmUgc2FpZCB0byBwcm90ZWN0IGJ=
b3RoIG1lc3NhZ2VzIGFuZCBjb21tdW5pY2F0aW5nIHBhcnRpZXMuDQoNClN0ZWdhbm9ncmFwaHkgaW5jbHW=
ZGVzIHRoZSBjb25jZWFsbWVudCBvZiBpbmZvcm1hdGlvbiB3aXRoaW4gY29t
cHV0ZXIgZmlsZXMuIEluIGRpZ2l0YWwgc3RlZ2Fub2dyYXBoeSwgZWxlY3Ryb25pYyBjb21tdW5pY2F0aW9u
cyBtYXkgaW5jbHVkZSBzdGVnYW5vZ3JhcGhpYyBjb2RpbmcgaW5zaZ==
ZGUgb2YgYSB0cmFuc3BvcnQgbGF5ZXIsIHN1Y2ggYXMgYSBkb2N1bWVudCBmaWxlLCBpbWFnZSBmaWx=
ZSwgcHJvZ3JhbSBvciBwcm90b2NvbC4gTWVkaWEg
ZmlsZXMgYXJlIGlkZWFsIGZvciBzdGVnYW5vZ3JhcGhpYyB0cmFuc21pc3Npb+==
biBiZWNhdXNlIG9mIHRoZWlyIGxhcmdlIHNpemUuIEFzIB==
YSBzaW1wbGUgZXhhbXBsZSwgYSBzZW5kZXIgbWlnaHQgc3RhcnQgd2l0aCBh
biBpbm5vY3VvdXMgaW1hZ2UgZmlsZSBhbmQgYWRqdXN0IHRoZSBjb2xvciBvZiBldmVyeSAxMDB0aCBwaXhlbCD=
dG8gY29ycmVzcG9uZCB0byBhIGxldHRlciBpbiB0aGUgYWxwaGFiZXQsIGF=
IGNoYW5nZSBzbyBzdWJ0bGUgdGhhdCBzb21lb25lIG5vdCBzcGVjaWZpY2FsbHkgbG9va2luZyBm
b3IgaXQgaXMgdW5saWtlbHkgdG8gbm90aWNlIGl0Lg0KDQpUaGU=
IGZpcnN0IHJlY29yZGVkIHVzZXMgb2Ygc3RlZ2Fub2dyYXBoeSBjYW4gYmUgdHJ=
YWNlZCBiYWNrIHRvIDQ0MCBCQyB3aGVuIEhlcm9kb3R1cyBtZW50aW9ucyB0d28gZXhhbXBsZXMgb+==
ZiBzdGVnYW5vZ3JhcGh5IGluIFRoZSBIaXN0b3JpZXMgb2Yg
SGVyb2RvdHVzLiBEZW1hcmF0dXMgc2VudCBhIHdhcm5pbmcgYWJvdXQgYSB=
Zm9ydGhjb21pbmcgYXR0YWNrIHRvIEdyZWVjZSBieSB3
cml0aW5nIGl0IGRpcmVjdGx5IG9uIHRoZSB3b29kZW4gYmFja2luZyBvZiBhIHdheCB0YWJsZXQgYmVm
b3JlIGFwcGx5aW5nIGl0cyBiZWVzd2F4IHN1cmZhY2UuIFdheCB0YWJsZXRzIHdlcmUgaW4gY29tbW9uIHVzZV==
IHRoZW4gYXMgcmV1c2FibGUgd3JpdGluZyBzdXJmYWNlcywgc29tZXRpbWX=
cyB1c2VkIGZvciBzaG9ydGhhbmQuIEFub3RoZXIgYW5jaWVudCBleGFtcGxlIGlzIHRoYXQgb9==
ZiBIaXN0aWFldXMsIHdobyBzaGF2ZWQgdGhlIGhlYWQgb2YgaGlzIG1vc3QgdHJ1c3RlZCBz
bGF2ZSBhbmQgdGF0dG9vZWQgYSBtZXNzYWdlIG9uIGl0LiBBZnRlciBoaXMgaGFpciBoYWQgZ5==
cm93biB0aGUgbWVzc2FnZSB3YXMgaGlkZGVuLiBUaGUgcHVycG9zZSB3YXMgdG+=
IGluc3RpZ2F0ZSBhIHJldm9sdCBhZ2FpbnN0IHRoZSBQZXJzaWFucy4NCg0KU3RlZ2Fub2dyYXBoeSBoYXMgYm==
ZWVuIHdpZGVseSB1c2VkLCBpbmNsdWRpbmcgaW4gcmVjZW50IGhpc3RvcmljYWwgdGltZXMgYW5kIHT=
aGUgcHJlc2VudCBkYXkuIFBvc3NpYmxlIHBlcm11dGF0aW9ucyBhcmUgZW5kbGVzcyBhbmT=
IGtub3duIGV4YW1wbGVzIGluY2x1ZGU6DQoqIEhpZGRlbiBtZXNzYWdlcyB3aXRoaW4gd2F4IHRh
YmxldHM6IGluIGFuY2llbnQgR3JlZWNlLCBwZW9wbGUgd3JvdGUgbWV=
c3NhZ2VzIG9uIHRoZSB3b29kLCB0aGVuIGNvdmVyZWQgaXQgd2l0aCB3YXggdXBvbiB3aGljaCBhbiBpbm5vY2Vu
dCBjb3ZlcmluZyBtZXNzYWdlIHdhcyB3cml0dGVu
Lg0KKiBIaWRkZW4gbWVzc2FnZXMgb24gbWVzc2VuZ2VyJ3MgYm9keTogYWxzbyB1c2VkIGluIGFuY2llbt==
dCBHcmVlY2UuIEhlcm9kb3R1cyB0ZWxscyB0aGUgc3Rvcnkgb1==
ZiBhIG1lc3NhZ2UgdGF0dG9vZWQgb24gYSBzbGF2ZSdzIHNoYXZlZCBoZWFkLCBoaWRkZW4gYnkgdGhl
IGdyb3d0aCBvZiBoaXMgaGFpciwgYW5kIGV4cG9zZWQgYnkgc2hhdmluZyBoaXMgaGVhZM==
IGFnYWluLiBUaGUgbWVzc2FnZSBhbGxlZ2VkbHkgY2FycmllZCBhIHdhcm5pbmcgdG8gR3JlZWNlIGFib5==
dXQgUGVyc2lhbiBpbnZhc2lvbiBwbGFucy4gVGh=
aXMgbWV0aG9kIGhhcyBvYnZpb3VzIGRyYXdiYWNrcyz=
IHN1Y2ggYXMgZGVsYXllZCB0cmFuc21pc3Npb24gd2hpbGUgd2FpdGluZyBmb3IgdGhlIHP=
bGF2ZSdzIGhhaXIgdG8gZ3JvdywgYW5kIHRoZSByZXN0cmljdGlvbnMgb3==
biB0aGUgbnVtYmVyIGFuZCBzaXplIG9mIG1lc3M=
YWdlcyB0aGF0IGNhbiBiZSBlbmNvZGVkIG9uIG9uZSBwZXJzb24=
J3Mgc2NhbHAuDQoqIEluIFdXSUksIHRoZSBGcmVuY2ggUmVzaXN0YW5jZSBzZW50IHNvbWUgbWVzc2FnZXMgd2==
cml0dGVuIG9uIHRoZSBiYWNrcyBvZiBjb3VyaWVycyD=
dXNpbmcgaW52aXNpYmxlIGluay4NCiogSGlkZGVuIG1lc3NhZ2VzIG9uIHBhcGVyIHdy
aXR0ZW4gaW4gc2VjcmV0IGlua3MsIHVuZGVyIG90aGVyIG1lc3NhZ2Vz
IG9yIG9uIHRoZSBibGFuayBwYXJ0cyBvZiBvdGhlct==
IG1lc3NhZ2VzLg0KKiBNZXNzYWdlcyB3cml0dGVuIGluIE1vcnNlIGNvZGUgb24ga25pdHRpbmcgeWFybiBhbmQg
dGhlbiBrbml0dGVkIGludG8gYSBwaWVjZSBvZiBjbG90aGluZyB3b3K=
biBieSBhIGNvdXJpZXIuDQoqIE1lc3NhZ2VzIHdyaXR0ZW4gb24gdGhlIGJhY2sgb5==
ZiBwb3N0YWdlIHN0YW1wcy4NCiogRHVyaW5nIGFuZCBhZnRlcm==
IFdvcmxkIFdhciBJSSwgZXNwaW9uYWdlIGFnZW50cyB1c2VkIHBob3RvZ3JhcGhpY2FsbHkgcO==
cm9kdWNlZCBtaWNyb2RvdHMgdG8gc2VuZCBpbmZvcm1hdGlvbiBiYWNrIGFuZH==
IGZvcnRoLiBNaWNyb2RvdHMgd2VyZSB0eXBpY2FsbHkg
bWludXRlLCBhcHByb3hpbWF0ZWx5IGxlc3MgdGhhbiB0aGUgc2l6ZSBvZiB0aGUgcGVyaW9kIHByb2R=
dWNlZCBieSBhIHR5cGV3cml0ZXIuIFdXSUkgbWljcm9kb3RzIG5lZWRlZCB0byBiZSBlbWJlZGRlZB==
IGluIHRoZSBwYXBlciBhbmQgY292ZXJlZCB3aXRoIGFuIGFkaGVzaXZlIChzdWNoIGFzIGNvbGxvZGlvbikuIFR=
aGlzIHdhcyByZWZsZWN0aXZlIGFuZCB0aHVzIGRldGVjdGFibGUg
Ynkgdmlld2luZyBhZ2FpbnN0IGdsYW5jaW5nIGxpZ2h0LiBBbHRlcm5hdGl2ZSB0ZWNobmlxdWVzIGluY2x1ZGVk
IGluc2VydGluZyBtaWNyb2RvdHMgaW50byBzbGl0cyBjdXQgaW50byB0aGUgZWRnZSBvZv==
IHBvc3QgY2FyZHMuDQoqIER1cmluZyBXb3JsZCBXYXIgSUksIGEgc3B5IGZvciB=
SmFwYW4gaW4gTmV3IFlvcmsgQ2l0eSwgVmVsdmFsZWW=
IERpY2tpbnNvbiwgc2VudCBpbmZvcm1hdGlvbiB0byBhY2NvbW1vZGF0aW9=
biBhZGRyZXNzZXMgaW4gbmV1dHJhbCBTb3V0aCBBbWVyaWO=
YS4gU2hlIHdhcyBhIGRlYWxlciBpbiBkb2xscywgYW5kIG==
aGVyIGxldHRlcnMgZGlzY3Vzc2VkIGhvdyBtYW55IG9mIHRoaXMgb3IgdGhhdCBkb2xs
IHRvIHNoaXAuIFRoZSBzdGVnb3RleHQgd2FzIHRoZSBkb2xsIG9yZGVycywgd2hpbGUgdGhl
IGNvbmNlYWxlZCAicGxhaW50ZXh0IiB3YXMgaXRzZWxmIGVuY2+=
ZGVkIGFuZCBnYXZlIGluZm9ybWF0aW9uIGFib3V0IHNoaXAgbW92ZW1lbnRzLF==
IGV0Yy4gSGVyIGNhc2UgYmVjYW1lIHNvbWV3aGF0IGZh
bW91cyBhbmQgc2hlIGJlY2FtZSBrbm93biBhcyB0aGX=
IERvbGwgV29tYW4uDQoqIENvbGQgV2FyIGNvdW50
ZXItcHJvcGFnYW5kYS4gSW4gMTk2OCwgY3JldyBtZW1iZW==
cnMgb2YgdGhlIFVTUyBQdWVibG8gKEFHRVItMikgaW50ZWxsaWdlbmNlIHNoaXAgaGVsZCBhcyBwcm==
aXNvbmVycyBieSBOb3J0aCBLb3JlYSwgY29tbXVuaWNhdGVkIGluIHNpZ25=
IGxhbmd1YWdlIGR1cmluZyBzdGFnZWQgcGhvdG8gb3Bwb3J0
dW5pdGllcywgaW5mb3JtaW5nIHRoZSBVbml0ZWQgU3RhdGVzIHRoZXkg
d2VyZSBub3QgZGVmZWN0b3JzIGJ1dCByYXRoZXIgd2VyZSBiZWluZyBoZWxkIGNh
cHRpdmUgYnkgdGhlIE5vcnRoIEtvcmVhbnMuIEluIG90aGVyIHBob3Rv
cyBwcmVzZW50ZWQgdG8gdGhlIFVTLCBjcmV3IG1lbWJlcnMgZ2F2ZSAidGhlIGZpbmdlciIgdG8g
dGhlIHVuc3VzcGVjdGluZyBOb3J0aCBLb3JlYW5zLCBpbiBhbiBhdHRlbXB0IHRvIE==
ZGlzY3JlZGl0IHBob3RvcyB0aGF0IHNob3dlZCB0aGVtIHNtaQ==
bGluZyBhbmQgY29tZm9ydGFibGUuDQoNCi0tDQpodHRwOi8vZW4ud2lraXBlZGlhLm9yZw==
L3dpa2kvU3RlZ2Fub2dyYXBoeQ0K
解密之后发现是一篇关于介绍隐写术的文章:
Steganography is the art and science of writing hidden messages in
such a way that no one, apart from the sender and intended recipient,
suspeage,
a form of security through obscurity. The word
steganography is of Greek origin and means “concealed writing” from
the Greek words steganos meaning
“covered or protected”, and
graphein meaning “to write”. The first recorded use of the term was in
1499 by Johannes Trithemius in his Steganographia,
a treatise on
cryptography and steganography disguised as a book on magic.
Generally, messages will appear to be something else: images,
articles,
shopping lists, or some other covertext and,
classically, the hidden message may be in invisible ink between the
visible lines of a private letter. The advantage of steganography,
over cryptography alone, is that messages do not attract attention to
themselves. Plainly visible encrypted messages
no matter how
unbreakable will arouse suspicion, and may in themselves be
incriminating in countries where encryption is illegal. Therefore,
whereas
cryptography protects the contents of a message,
steganography can be said to protect both messages and communicating
parties. Steganography includes the concealment of information within
computer files. In digital steganography, electronic communications
may include steganographic
coding inside of a transport layer,
such as a document file, image filn because of their large size. As a
simple example, a sender might start with
an innocuous image file
and adjust the color of every 100th pixel to correspond to a letter in
the alphabet, a change so subtle that someone not
specifically
looking for it is unlikely to notice it. The first recorded uses of
steganography can be traced back to 440 BC when Herodotus mentions two
examples of steganography in The Histories
of Herodotus. Demaratus
sent a warning about a forthcoming attack to Greece by writing it
directly on the wooden backing of a wax tablet before
applying its
beeswax surface. Wax tablets were in common use then as reusable
writing surfaces, sometimes used for shorthand. Another ancient
example is that of Histiaeus, who shaved the head of his most
trusted slave and tattooed a message on it. After his hair had grown
the message
was hidden. The purpose was to instigate a revolt
against the Persians. Steganography has been widely used, including in
recent historical times and the present day. Possible permutations are
endless and known examples include:
- Hidden messages within wax tablets: in ancient Greece, people wrote messages on the wood, then covered it with wax upon which an
innocent
covering message was written
- Hidden messages on messenger’s body: also used in ancient Greece. Herodotus tells the story of a message tattooed on a slave’s shaved
head,
hidden by the growth of his hair, and exposed by shaving his
head again. The message allegedly carried a warning to Greece abois
method has
obvious drawbacks, such as delayed transmission while
waiting for the sn the number and size of messages that can be encoded
on one person’s scalp.
- In WWII, the French Resistance sent some messages written on the backs of couriers using invisible ink.
- Hidden messages on paper written in secret inks, under other messages or on the blank parts of other messages.
- Messages written in Morse code on knitting yarn and then knitted into a piece of clothing worn by a courier.
- Messages written on the back of postage stamps.
- During and after World War II, espionage agents used photographically produced microdots to send information back and
forth. Microdots
were typically minute, approximately less than
the size of the period produced by a typewriter. WWII microdots needed
to be embedded in
the paper and covered with an adhesive (such as
collodion). This was reflective and thus detectable by viewing against
glancing light.
Alternative techniques included inserting
microdots into slits cut into the edge of post cards.
- During World War II, a spy for Japan in New York City, Velvalee Dickinson, sent information to accommodation addresses in neutral
South America.
She was a dealer in dolls, and her letters
discussed how many of this or that doll to ship. The stegotext was the
doll orders, while the
concealed “plaintext” was itself encoded
and gave information about ship movements, etc. Her case became
somewhat famous and she became
known as the Doll Woman.
- Cold War counter-propaganda. In 1968, crew members of the USS Pueblo (AGER-2) intelligence ship held as prisoners by North Korea,
communicated in sign language during staged photo opportunities,
informing the United States they were not defectors but rather
were
being held captive by the North Koreans. In other photos
presented to the US, crew members gave “the finger” to the
unsuspecting
North Koreans, in an attempt to discredit photos that
showed them smiling and comfortable.
http://en.wikipedia.org/wiki/Steganography
在线翻译了一下:
隐写术是一门艺术和科学,它以一种除了发送者和预期接收者之外,任何人都无法通过隐藏的方式来书写隐藏的信息。“隐写术”一词源于希腊语,意为“隐藏的写作”,
源于希腊语单词steganos,意为“覆盖或保护”,而graphein意为“写作”。1499年,约翰内斯·特里特米乌斯(Johannes
Trithemius)在他的《隐写术》(Steganographia)一书中首次使用了这个词。
一般情况下,信息会以其他形式出现:图像、文章、购物清单或其他一些隐藏文本,通常,隐藏的信息可能是私人信件可见行之间的隐形墨水。
与密码学相比,隐写术的优势在于,消息本身不会引起注意。显而易见的加密信息,无论多么牢不可破,都会引起怀疑,而且在加密非法的国家,这些信息本身就可能构成犯罪。
因此,虽然密码学保护消息的内容,但是隐写术可以同时保护消息和通信方。
隐写术包括在计算机文件中隐藏信息。在数字隐写术中,由于传输层(如文档文件、图像文件)的大尺寸,电子通信可能包括传输层内部的隐写编码。举个简单的例子,
发送者可能从一个无害的图像文件开始,每100个像素调整一次颜色,使之与字母表中的一个字母相对应,这种变化如此细微,以至于没有专门查找它的人不太可能注意到它。
有记录的第一次使用隐写术可以追溯到公元前440年,希罗多德在他的历史中提到了两个隐写术的例子。德玛拉图斯在涂上蜂蜡表面之前,直接把它写在一块蜡板的木制底座上,
警告希腊即将受到攻击。蜡片当时普遍用作可重复使用的书写表面,有时也用于速记。另一个古老的例子是希斯提厄斯,他剃光了他最信任的奴隶的头,并在上面纹了一条信息。
他的头发长了以后,这条信息就被藏了起来。目的是煽动对波斯人的起义。
隐写术已被广泛应用,包括在最近的历史时期和今天。可能的排列是无穷无尽的,已知的例子包括:
*蜡版内的隐藏信息:在古希腊,人们把信息写在木头上,然后用蜡把木头盖上,在上面写上一个无辜的信息
*信使身体上的隐藏信息:也用于古希腊。希罗多德讲了一个故事,一个奴隶剃光了头,上面纹着一条信息,隐藏在他的头发后面,再剃一次头就露出来了。
据称,这条信息带有向希腊发出警告的信息,abois方法有明显的缺陷,比如在等待sn时传输延迟。sn是可以在一个人的头皮上编码的信息的数量和大小。
*二战期间,法国抵抗运动用隐形墨水在信使的背上写了一些信息。
*用秘密墨水写在纸上的隐藏信息,在其他信息下面或其他信息的空白部分。
*用莫尔斯电码写在针织纱线上的信息,然后编织成快递员穿的衣服。 写在邮票背面的信息。
*在第二次世界大战期间和之后,间谍人员使用照相制作的微粒来来回传送信息。微粒通常是微小的,大约比打字机产生的周期的大小还要小。第二次世界大战的微粒需要嵌入在纸上,
并覆盖上粘合剂(如胶棉)。这是反射的,因此可以通过对光的观察来检测。其他的技术包括将微粒插入明信片边缘的缝隙中。
*第二次世界大战期间,驻纽约的日本间谍维瓦利·迪金森(Velvalee Dickinson)将信息发送到中立的南美的住宿地址。她是一个玩偶经销商,她在信中讨论了要运送多少个这样或那样的玩偶。
隐写文本是娃娃的命令,而隐藏的“明文”本身是编码的,并提供有关船只移动等信息。她的情况变得有点出名,她成为众所周知的娃娃女人。
*冷战反宣传。1968年,被朝鲜扣押的美国普韦布洛号(USS Pueblo, AGER-2)号情报舰的船员在拍照时用手语交流,告知美国他们不是叛逃者,而是被朝鲜扣押的。在提交给美国的其他照片中,
机组人员向毫无戒心的朝鲜人竖起了“手指”,试图抹掉他们微笑和舒适的照片。
–
http://en.wikipedia.org/wiki/Steganography
之后就没有思路了,然后看了wp,发现需要写一个base64解密的脚本,我晕,解密工具果然还是有不足之处的。
下面就是关于base64隐写的介绍了:
大家可以从上面的图片看到一个字母A对应的ascll值有八位,而base64的一个字母只占6位(原因如下: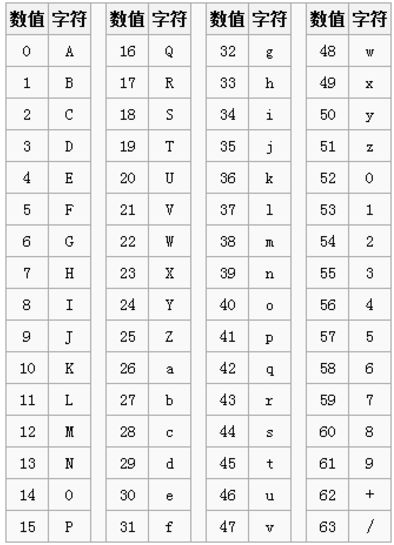 大家可以看到base64的所有加密后的内容也就这63个字符,也就是说用二进制的话6位就足够了!!)
大家可以看到base64的所有加密后的内容也就这63个字符,也就是说用二进制的话6位就足够了!!)
所以一一对应过去我们发现每一个字母都多出来了两个空位,又因为3*8=4*6,所以一班base64都是用四个一组表示三个字母,如果字母不足三个,比如上上图的BC我们用base64表示就是QkM=,就是因为空出来的地方用‘=’表示了。在知道了这些之后呢我们就进入了正题。
在这里如果我们想隐藏一些内容需要怎么办呢?大家应该知道,base64在解码的时候是根据等号的个数进行的。也就是说我有一个等号,我就会去掉八个0-------------例如:上图的A对应的二进制位为01000001,补全之后为01000001 0000,对应的base64的编码为QQ(010000 010000),所以之后有两个‘=’。在解码的时候我就要在去掉=对应的6个零的同时在去掉4个0,也就是解码的时候会解析01000001而不是010000010000。这时候我们会发现了,我们去掉的这四个0是不是可以用来隐藏信息???反正解码的时候会被裁剪掉,那我干脆就在后面做一些手脚,用base64来混淆视听。
hhhh讲到这里大家是不是有所领悟呢?也就是说我前面放的txt内容其实都是被混淆过的!!所以想得到真正的base64就应该把题目中的密文解密然后在加密。对比后就得到了隐藏内容。
下面放上py脚本
def get_base64_diff_value(s1, s2):
base64chars = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/'
res = 0
for i in xrange(len(s1)):
if s1[i] != s2[i]:
return abs(base64chars.index(s1[i]) - base64chars.index(s2[i]))
return res
def solve_stego():
with open("D:/CTF Practice/stego.txt", "rb") as f:
file_lines = f.readlines()
bin_str = ''
for line in file_lines:
steg_line = line.replace('\n', '')
norm_line = line.replace('\n', '').decode('base64').encode('base64').replace('\n', '')
diff = get_base64_diff_value(steg_line, norm_line)
pads_num = steg_line.count('=')
if diff:
bin_str += bin(diff)[2:].zfill(pads_num * 2)
else:
bin_str += '0' * pads_num * 2
res_str = ''
for i in xrange(0, len(bin_str), 8):
res_str += chr(int(bin_str[i:i+8], 2))
print res_str
solve_stego()
这个脚本也是git上的,不是我原创的哈(声明下)。
我在这里解释下这个脚本。
steg_line = line.replace('\n', '')
norm_line = line.replace('\n', '').decode('base64').encode('base64').replace('\n', '')
这个是我们应该第一个注意的地方,第二个norm_line为何先decode又encode??这就是我刚才提到的解密后去掉多余0,然后加密后真正的base64就还原了。之后才可以对比
def get_base64_diff_value(s1, s2):
这个函数就是用来比较差异然后得出来差异的位数的。比如加密之后的最后一位是g,原密码为m,这个函数就得出来m与g相差6,也就是110.之后在主函数里在110前面补上一个0,补的原理是把=个数乘2,得到位数。例如:2*2=4,那么110前面就要补一个0编程0110
嗯。。。。这里就讲完了这次比赛的一道题。我是有所收获的,希望带给大家一些灵感。谢谢~~
Made By Pinging!!!~~
BXS Come On~~~!!!!
因为菜,所以仍在努力。

