DEC 06 2018 DAVID CELIS
Back at HashiConf 2017, we announced Sentinel, our embeddable policy-as-code framework. Sentinel enables fine-grained, logic-based policy that can leverage external information sources to make decisions. Terraform Enterprise uses Sentinel to enforce policies on Terraform configurations, states, and plans. Organization owners can define Sentinel policies that are checked between the plan and apply phases of a Terraform run to validate infrastructure changes, applying those changes only if the policies pass.
Previously, Sentinel policies would be enforced on all Terraform runs across all workspaces in an organization. However, applications and components often have multiple environments (such as development, staging, and production) and organizations typically create multiple workspaces for one component, one for each environment. This makes it difficult to write Sentinel policies that target a single environment, as they would run on every workspace in the organization.
For these reasons, Terraform Enterprise users have been asking for a way to enforce policies only on specific workspaces. We're pleased to announce that this is now possible with the addition of Policy Sets to Terraform Enterprise Cloud and the latest version of Private Terraform Enterprise.
Creating and configuring a policy set
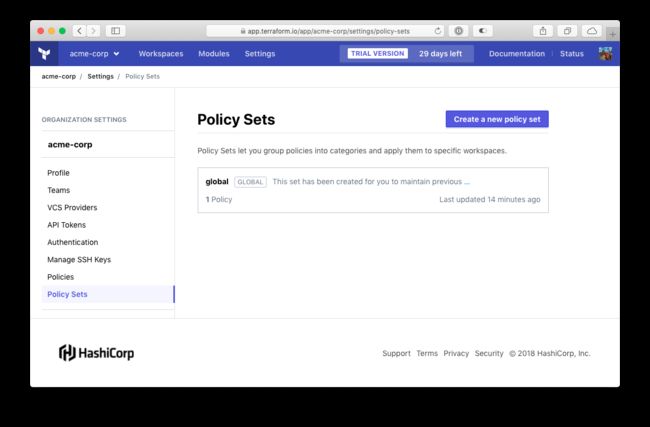
Policy sets, like Sentinel policies, are configured on an organization. Policy sets contain a list of Sentinel policies and can either be applied to specific workspaces or can be applied to all workspaces in the organization. When viewing an organization's settings, you can navigate to the "Policy Sets" item in the sidebar to be presented with a list of the organization's policy sets.
If your organization has already been using Sentinel, you may notice that a policy set has already been created for you. Because policies used to be enforced on every workspace in an organization, you will start off with a global policy set that is populated with any existing Sentinel policies. Regardless of whether or not you have a global policy set, you can now click the button that reads "Create a new policy set" and you will be presented with a form to do so.
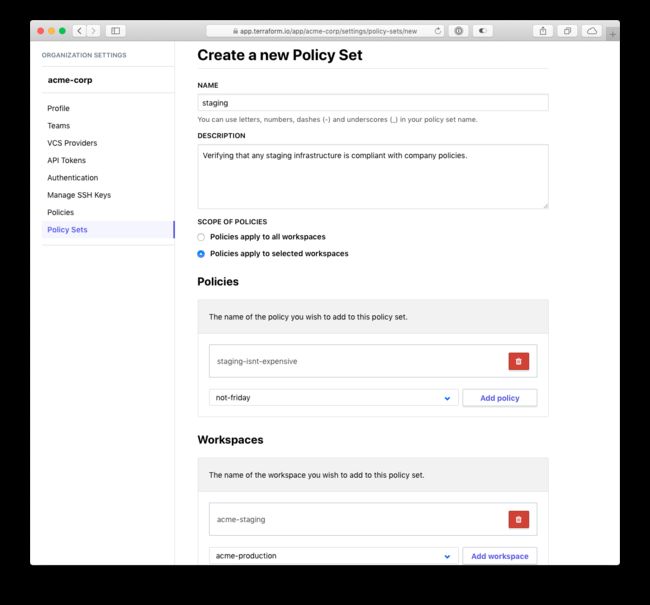
All policy sets need to have a name. In this example, name the policy set "staging" and give it a description so that other organization members can easily see the purpose of a policy set. Because this policy set will only be applied to staging infrastructure, leave the radio button for "Scope of policies" alone. Next, add a relevant policy and workspace. This sample policy validates that no AWS instances bigger than a t3.large will be created in any workspace that handles infrastructure for an application's staging environment:
import "tfplan"
allowed_instance_types = [
"t3.nano",
"t3.micro",
"t3.small",
"t3.medium",
"t3.large",
]
main = rule {
all tfplan.resources.aws_instance as _, instances {
all instances as _, r {
r.applied.instance_type in allowed_instance_types
}
}
}
Lastly, save the policy set.
Using policy sets
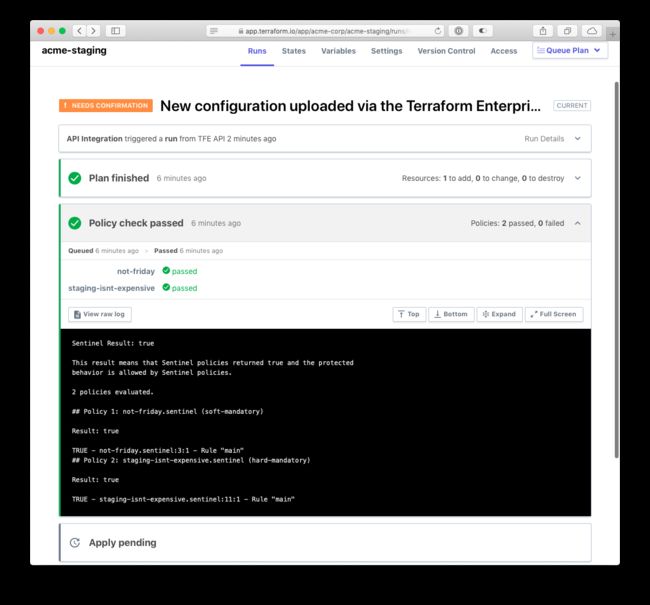
Now that you have a policy set applied to your staging workspace, queue a run in that workspace.
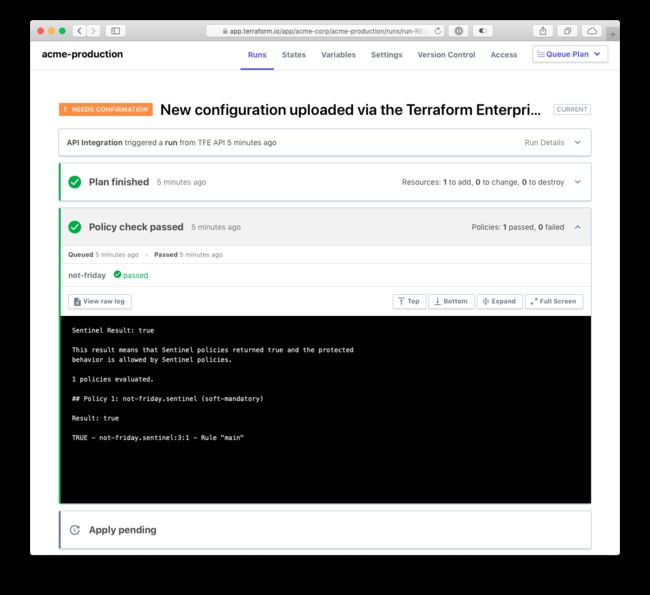
You can see from the run's policy check that the new AWS policy has been enforced and passed. If you try queueing a run in any other workspace, you'll notice that the AWS policy is not checked.
Summary
Policy sets allow you to enforce Sentinel policies on the workspaces of your choice and are available in both Terraform Enterprise Cloud and the latest version of Private Terraform Enterprise. If you're already using Terraform Enterprise, try out the example above to get started with policy sets. To learn more and get started with Terraform Enterprise or request a free trial, visit https://www.hashicorp.com/products/terraform.