公司最近增加一台CISCO ASA 5510-K8 防火墙设备,也算是初次接触吧,一波三折,折腾了一个多星期也算基本摸清,现为这一个多星期的折腾记录一下,日后少做一些无用功。这次ASA主要用于远程接入及一部分服务器外网访问,按此需求也列出以下ASA需配置的项目:
1、远程接入,IPSec *** 或SSL *** ,因购买此型号的防火墙SSL ***授权只有两个,只有选择IPsec ***使用了;
2、做NAT 实现外网访问,相关ACL控制指定服务器连接外网;
3、端口映射,把相关需要使用的服务器端口映射到公网使用,如25、110等。
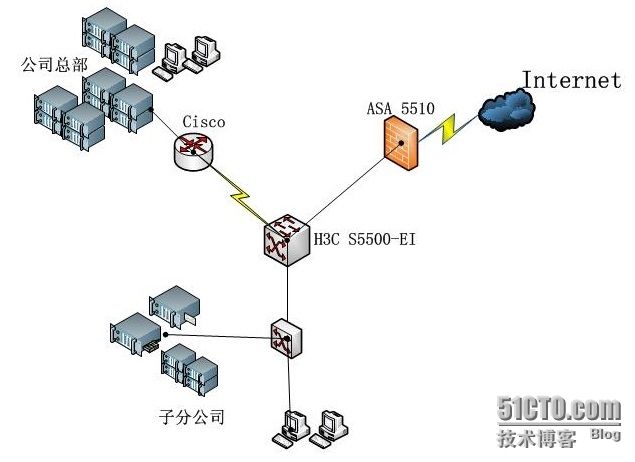
简单拓扑图如下:
h3c s5500-ei 配置主要点:
ip route-static 0.0.0.0 0.0.0.0 172.65.3.1 description to asa
ip route-static 10.0.0.0 255.0.0.0 192.168.193.1 description to qq
ip route-static 172.0.0.0 255.0.0.0 192.168.193.1 description overto qq
ip route-static 192.0.0.0 255.0.0.0 192.168.193.1 description to qq
ASA配置:
ciscoasa(config)# sh run
: Saved
:
ASA Version 8.2(5)
!
hostname ciscoasa
enable password 2KFQnbNIdI.2KYOU encrypted
passwd 2KFQnbNIdI.2KYOU encrypted
names
!
interface Ethernet0/0
nameif outside
security-level 0
ip address xxx.xxx.xxx.xxx 255.255.255.248 \\外网接口IP
!
interface Ethernet0/1
nameif inside
security-level 100
ip address 172.65.3.1 255.255.255.0 \\内网接口IP
!
interface Ethernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface Management0/0
shutdown
no nameif
no security-level
no ip address
!
ftp mode passive
clock timezone CST 8
access-list test***_splitTunnelAcl standard permit 172.65.0.0 255.255.0.0
\\***接入时上述IP流量做隧道分割,如不开启隧道分割技术***接入的用户就不能使用本地internet了。这里需注意的
access-list permitwww extended permit ip host 172.65.12.24 any \\控制部分服务器访问外网
access-list permitwww extended permit icmp any any \\icmp 流量容许通过
access-list inside_nat0_outbound extended permit ip 172.65.0.0 255.255.0.0 172.65.3.0 255.255.255.0 \\nat免除,表示从172.65.0.0/16网段通过172.65.3.0/24时不进行nat转换
pager lines 24
logging enable
logging asdm informational
mtu outside 1500
mtu inside 1500
ip local pool ipsecpool 172.65.3.100-172.65.3.200 mask 255.255.255.0 \\接入***客户端地址池
icmp unreachable rate-limit 1 burst-size 1
asdm p_w_picpath disk0:/asdm-645.bin \\asdm 加载镜像,asdm是个好东西,把asa配置简化了好多
no asdm history enable
arp timeout 14400
global (outside) 1 interface \\配置单个地址为outside接口地址,如有多个公网IP也可以配置为一个地址池
nat (inside) 0 access-list inside_nat0_outbound
nat (inside) 1 172.65.0.0 255.255.0.0 \\与上述 global对应使用,即把172.65.0.0/16这个网段的地址转换为外网接口IP地址。
access-group permitwww in interface inside \\控制部分服务器外网访问,此条access-list 在inside
route outside 0.0.0.0 0.0.0.0 xxx.xxx.xxx.xxx 1 \\公网网关 ,默认路由且只有一跳
route inside 172.65.0.0 255.255.0.0 172.65.3.254 1 \\内网网关
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
aaa authentication http console LOCAL \\设置AAA验证方式。此处为LOCAL本地用户验证
aaa authentication telnet console LOCAL \\同上
aaa authentication serial console LOCAL \\同上
http server enable \\开启http服务
http 172.65.0.0 255.255.0.0 inside \\充许此网段通过http连接上来
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set pfs group1
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map outside_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map outside_map interface outside
crypto ca trustpoint _SmartCallHome_ServerCA
crl configure
crypto ca certificate chain _SmartCallHome_ServerCA
certificate ca 6ecc7aa5a7032009b8cebcf4e952d491
quit
crypto isakmp enable outside
crypto isakmp policy 10
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
telnet 172.65.0.0 255.255.0.0 inside \\允许此网段进行telnet管理
telnet timeout 5 \\超时限制
ssh 172.65.0.0 255.255.0.0 inside \\允许此网段进行ssh登录管理
ssh timeout 5 \\超时限制
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
threat-detection statistics tcp-intercept rate-interval 30 burst-rate 400 average-rate 200
web*** \\进入web*** 模式
group-policy test*** internal \\设置一个名为test*** 的策略组,选项为internal
group-policy test*** attributes \\设置组策略属性
dns-server value 172.65.0.10 172.65.0.11 \\***接入的客户端的dns设置
***-tunnel-protocol IPSec
split-tunnel-policy tunnelspecified \\启用隧道分离,且只有访问公司内网时才用。隧道分离有三种方式,这是其中一种。tunnelspecified:允许客户端访问客户端本地网络以及internet,只有到公司内网的数据流才走分离隧道;excludespecified :仅允许客户端访问客户端本地的网络,internet和到公司内网的数据流都走分离隧道;tunnelall: 客户端所有所有流量都走分离隧道
split-tunnel-network-list value test***_splitTunnelAcl \\隧道分离保护的数据, 此处test***_splitTunnelAcl为上面定义的隧道分离列访问列表
default-domain value test.com
username admin password sadP6m1bnmnzbmnX encrypted
username test password c2I40Rrw1iizALuA encrypted privilege 0 \\接入***用户名
username test attributes
***-group-policy test***
tunnel-group test*** type remote-access
tunnel-group test*** general-attributes
address-pool ipsecpool
default-group-policy test***
tunnel-group test*** ipsec-attributes
pre-shared-key *****
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect ip-options
inspect netbios
inspect rsh
inspect rtsp
inspect skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect tftp
inspect sip
inspect xdmcp
!
service-policy global_policy global
prompt hostname context
call-home reporting anonymous
call-home
profile CiscoTAC-1
no active
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination address email [email protected]
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
Cryptochecksum:54014531b7373a1bcfb4b3700064302e
: end
ASDM设置ipsec 操作步骤(配置asa大多数在asdm下进行,有必要对其有一定的了解)
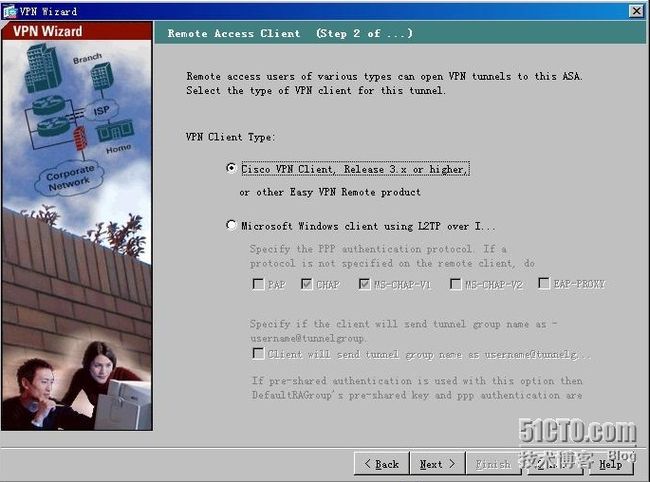
1、Remote Access ***设置:
2、
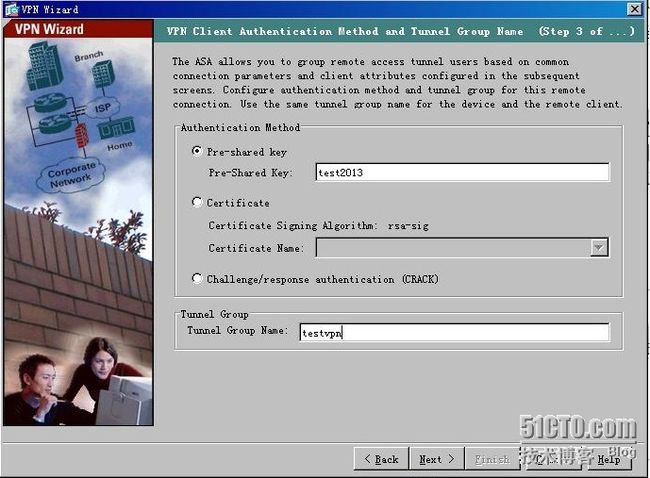
3、共享密钥,及组策略名
4、选择验证方式
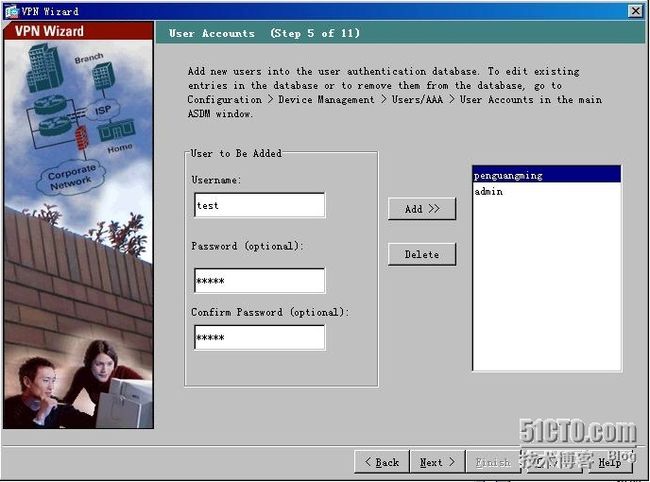
5、新增用户
6、***地址池
7、***连接客户端dns等配置
8、默认K8版本是没有3DES选项的,需到cisco官网去激活开启,详细可以查看用户操作说明书说明:
9、开启隧道分离技术
10、完成前确认:
结束!
***client 设置:
1、connection Entry 为自己自定义名称,host为asa外网ip,group authentication name 为*** group 名:test***,password为共享密钥。
2、点击连接
3、输入***用户名密码。
附录:
部分ASA初始化的基本配置:
1、安全级别:
outside 默认为0安全性级别最低,最不信任的!
inside 默认为100 最信任的安全级别最高
DMZ 1-99安全级别
2、防火墙的默认策略:
Outbound (由高往底) 的流量默认允许 ,如inside到outside
Inbound (由底往高)的流量默认禁止
3、初始化防火墙:
int g0
ip add 202.100.1.10 255.255.255.0
no sh
nameif outside
其它inside 及DMZ接口同理
4、配置ASDM
ASA(config)#username ccie password ccie // 配置用户名和密码
ASA(config)#http server enable //启用https功能
ASA(config)#aaa authentication http console LOCAL //HTTPS认证类型为本地认证
ASA(config)#http 172.16.1.0 255.255.255.0 inside // 允许来排自inside的流量通过HTTPS网管ASA
5、基本NAT介绍
ASA(config)#object network Inside.traffic //创建一个内部地址名称traffic
ASA(config-network-object)#subnet 172.16.1.0 255.255.255.0 //定义其地址范围
ASA(config-network-object)#nat (inside,outside) dynamic interface //完成nat转换
例:创建一个outside telnet 到DMZ里的http服务器nat
ASA(config)#object network Inside.telnet //创建一个内部地址名称DMZ.telnet
ASA(config-network-object)#subnet host 192.168.1.100 //定义DMZ.telnet的主机地址
ASA(config)#object network Outside.telnet //创建一个内部地址名称outside.telnet
ASA(config-network-object)#subnet host 202.100.1.100 //定义outside.telnet的主机地址
ASA(config-network-object)#nat (DMZ,outside) static Outside.telnet service tcp telnet telnet //完成nat转换,安全级别需从高流向低