制作一个仪表盘
1. 数据库配置
添加一个mysql数据库:
例如macos本机docker环境下 sqlalchemy uri:mysql+mysqldb://root:[email protected]:3306/test?charset=utf8。
测试连接成功后可以看到数据表。
数据库的元数据在这里编辑:
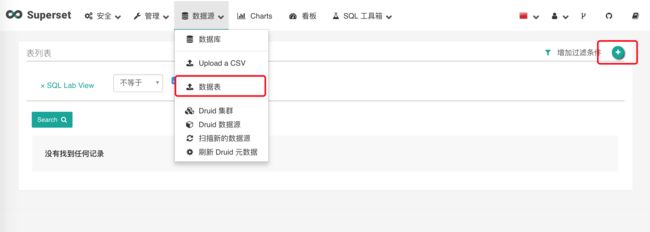
2. 数据表配置
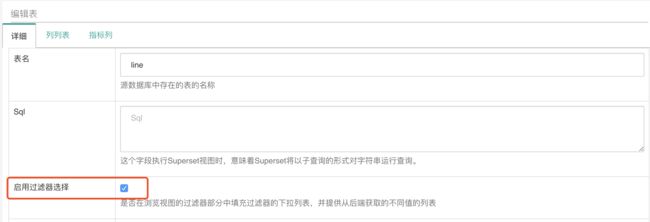
输入信息后保存:
数据表的元数据可以点这里进行编辑:
列列表里的过滤器开关:
3. 数据表使用
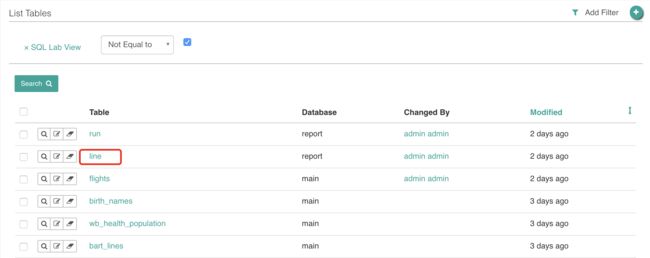
在数据表列表直接点击名称:
进入一个数据表操作界面:
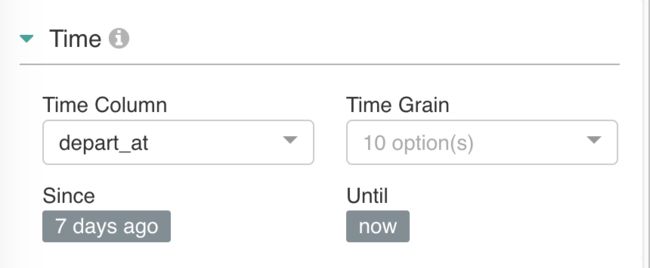
选择数据表和类型
日期时间型过滤,
Is temporal 控制是否下拉列表可见。
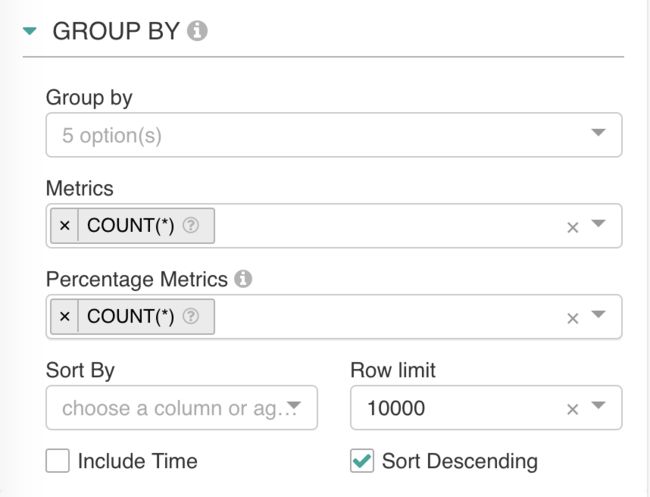
GROUP BY 专门用于聚合数据展示。
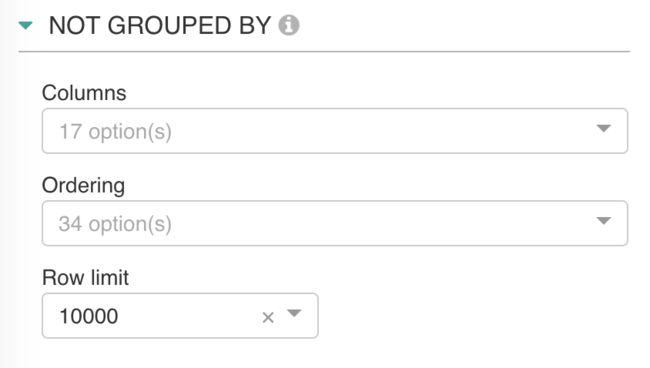
GROUP BY 和
NOT GROUPED BY 不可同时使用。
NOT GROUPED BY用于简单列表数据展示。
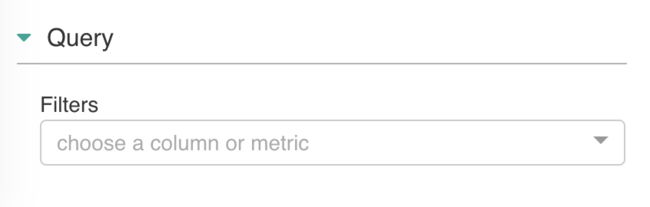
自定义查询条件。
切片
In Superset, a saved query is called a Slice.
Security
Superset的权限设计基于Flask AppBuilder (FAB).
FAB is a “Simple and rapid application development framework, built on top of Flask.”
FAB provides authentication, user management, permissions and roles. Please read its Security documentation.
内置基础角色
不建议对内置角色进行更改,因为随着Superset升级,这些内置角色的元数据会被 superset init 还原。
建议 compose 基础角色和自定义角色 来构建自己的权限体系。
Admin
最高权限。
Admins have all possible rights, including granting or revoking rights from other users and altering other people’s slices and dashboards.
Alpha
数据管理者。
Alpha have access to all data sources, but they cannot grant or revoke access from other users. They are also limited to altering the objects that they own. Alpha users can add and alter data sources.
Gamma
数据消费者。
They can only consume data coming from data sources they have been given access to through another complementary role. They only have access to view the slices and dashboards made from data sources that they have access to. Currently Gamma users are not able to alter or add data sources. We assume that they are mostly content consumers, though they can create slices and dashboards.
sql_lab
sql_lab使用者。
The sql_lab role grants access to SQL Lab. Note that while Admin users have access to all databases by default, both Alpha and Gamma users need to be given access on a per database basis.
Public
公共访问者。
It’s possible to allow logged out users to access some Superset features.
By setting PUBLIC_ROLE_LIKE_GAMMA = True in your superset_config.py, you grant public role the same set of permissions as for the GAMMA role. This is useful if one wants to enable anonymous users to view dashboards. Explicit grant on specific datasets is still required, meaning that you need to edit the Public role and add the Public data sources to the role manually (这里对public进行了修改).
granter
定制化
The permissions exposed by FAB are very granular and allow for a great level of customization. FAB creates many permissions automagically for each model that is create (can_add, can_delete, can_show, can_edit, …) as well as for each view. On top of that, Superset can expose more granular permissions like all_datasource_access.
We do not recommend altering the 3 base roles as there are a set of assumptions that Superset build upon. It is possible though for you to create your own roles, and union them to existing ones.
Permissions categories
Roles are composed of a set of permissions, and Superset has many categories of permissions. Here are the different categories of permissions:
Model & action:
models are entities like Dashboard, Slice, or User. Each model has a fixed set of permissions, like can_edit, can_show, can_delete, can_list, can_add, and so on. By adding can_delete on Dashboard to a role, and granting that role to a user, this user will be able to delete dashboards.
Views:
views are individual web pages, like the explore view or the SQL Lab view. When granted to a user, he/she will see that view in the its menu items, and be able to load that page.
Data source:
For each data source, a permission is created. If the user does not have the all_datasource_access permission granted, the user will only be able to see Slices or explore the data sources that are granted to them
Database:
Granting access to a database allows for the user to access all data sources within that database, and will enable the user to query that database in SQL Lab, provided that the SQL Lab specific permission have been granted to the user
Customizing
The permissions exposed by FAB are very granular and allow for a great level of customization. FAB creates many permissions automagically for each model that is create (can_add, can_delete, can_show, can_edit, …) as well as for each view. On top of that, Superset can expose more granular permissions like all_datasource_access.
We do not recommend altering the 3 base roles as there are a set of assumptions that Superset build upon. It is possible though for you to create your own roles, and union them to existing ones.
Permissions
Roles are composed of a set of permissions, and Superset has many categories of permissions. Here are the different categories of permissions:
- Model & action:
models are entities like Dashboard, Slice, or User. Each model has a fixed set of permissions, like can_edit, can_show, can_delete, can_list, can_add, and so on. By adding can_delete on Dashboard to a role, and granting that role to a user, this user will be able to delete dashboards. - Views:
views are individual web pages, like the explore view or the SQL Lab view. When granted to a user, he/she will see that view in the its menu items, and be able to load that page. - Data source:
For each data source, a permission is created. If the user does not have the all_datasource_access permission granted, the user will only be able to see Slices or explore the data sources that are granted to them - Database:
Granting access to a database allows for the user to access all data sources within that database, and will enable the user to query that database in SQL Lab, provided that the SQL Lab specific permission have been granted to the user
Restricting access to a subset of data sources
Restricting the access to some metrics
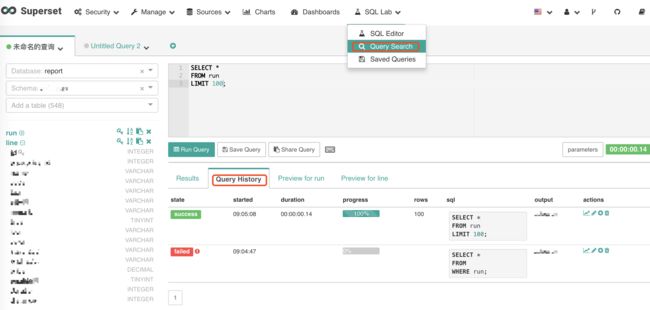
SQL Lab
SQL Lab is a modern, feature-rich SQL IDE written in React.
Connects to just about any database backend
A multi-tab environment to work on multiple queries at a time
A smooth flow to visualize your query results using Superset’s rich visualization capabilities
Browse database metadata: tables, columns, indexes, partitions
Support for long-running queries
- uses the Celery distributed queue to dispatch query handling to workers
- supports defining a “results backend” to persist query results
A search engine to find queries executed in the past
Supports templating using the Jinja templating language which allows for using macros in your SQL code
参考文章:
Python模块学习 - jinja2
使用SQLAlchemy
架构
https://segmentfault.com/a/1190000005083953