我的博客的地址:http://ilovestudy.wikidot.com/computer-network-security-lab-1
实验背景
入侵检测系统(IDS)是一种对网络传输进行即时监视,在发现可疑传输时发出警报或者采取主动反应措施的网络安全设备。
Suricata是一种较为著名的入侵检测系统,本实验的主要内容是使用 Suricata对给出的pcap文件进行检测,并对pcap文件进行分析。
实验环境
VMware上的Ubuntu虚拟机。已经给出了虚拟机的ovf文件,只需在VMware中将ubuntu.ovf导入即可。虚拟机中已经对相关实验环境进行了配置。用户名和密码均为suricata(全部小写字母)。
实验数据
进入虚拟机系统后,在桌面上的pcapfile文件夹中有三个标号为1、2、3的pcap文件,选择自己学号对3取余后的那一个文件进行检测即可。
(我的学号取余为2,不过老师您不觉得自己这句话有什么问题吗?)
实验命令
cd /home/suricata/Desktop/pcapfile
sudo su
密码输入suricata
suricata –r x.pcap –l ./
vim fast.log
实验前的一些准备
pcap文件
pcap 是 packet capture 的缩写,一般是 tcpdump 或者 wireshark 抓包后存盘的文件。我们这次好像不需要详细了解文件的格式,让suricata自己去分析好了。详细介绍参见这里:https://zrj.me/archives/831。
对于Suricata的简介
Suricata是一种开源的入侵检测系统,特点包括:
- 多线程
- 自动协议检测
(翻译自维基百科)
Suricata的输出
以下内容摘自Suricata的帮助文档:https://suricata.readthedocs.io/en/latest/output/index.html
Eve Json输出
Suricata可以将警告、HTTP事件、DNS事件、TLS事件和文件信息输出到JSON中。通常使用“EVE”(event的缩写)格式将这些信息输出到单独的一个文件中。
输入文件的格式一般如下:
{"timestamp":"2009-11-24T21:27:09.534255","event_type":"TYPE", ...tuple... ,"TYPE":{ ... type specific content ... }}
event_type域表示当前event的类型,分为以下4类:
AlertHTTPDNSTLS
下面分别介绍4种event的格式。
Alert
-
alert.action:可能取值为allowed和blocked,默认为allowed,仅当有一条规则的动作为reject,或Suricata处于IPS模式且有一条规则的动作为drop时为blocked。 -
alert.signature:攻击内容 -
alert.source:可选,攻击发起者的信息 -
alert.target:可选,被攻击者的信息
例子:
{
"timestamp": "2009-11-24T21:27:09.534255",
"event_type": "alert",
"src_ip": "192.168.2.7",
"src_port": 1041,
"dest_ip": "x.x.250.50",
"dest_port": 80,
"proto": "TCP",
"alert": {
"action": "allowed",
"gid": 1,
"signature_id": 1,
"rev": 1,
"app_proto": "http",
"signature": "HTTP body talking about corruption",
"severity": 3,
"source": {
"ip": "192.168.43.32",
"port": 36292
},
"target": {
"ip": "179.60.192.3",
"port": 80
}
}
}
HTTP
-
http.hostname:这一HTTP事件对应的主机域名 -
http.url:主机域名被访问的URL -
http.http_user_agent:被使用的软件的user-agent(没看懂) -
http.http_content_type:返回的数据类型 -
http.cookie
下面是主要的扩展信息项: -
http.length:HTTP正文的内容长度 -
http.status:HTTP状态码 -
http.protocol:协议/HTTP版本 -
http.http_method:HTTP请求(例:GET、POST、HEAD) -
http.http_refer: The referer for this action
除此之外,还可以在suricata.yaml文件中选择打印另外47项信息的日志。
例子(带扩展):
"http": {
"hostname": "direkte.vg.no",
"url":".....",
"http_user_agent": "",
"http_content_type": "application\/json",
"http_refer": "http:\/\/www.vg.no\/",
"http_method": "GET",
"protocol": "HTTP\/1.1",
"status":"200",
"length":310
}
DNS
在各种不同的DNS事件中,可能包括以下域:
-
dns.type:DNS消息类型,可能取值包括answer和query -
dns.id:id -
dns.flags:DNS响应报文标志,16进制(0x是无输出) dns.qrdns.aadns.tcdns.rddns.radns.rcodedns.rrnamedns.rrtypedns.rdatadns.ttl
例子(DNS请求):
"dns": {
"type": "query",
"id": 16000,
"rrname": "twitter.com",
"rrtype":"A"
}
例子(DNS回复):
"dns": {
"type": "answer",
"id":16000,
"flags":"8180",
"qr":true,
"rd":true,
"ra":true,
"rcode":"NOERROR"
"rrname": "twitter.com",
"rrtype":"A",
"ttl":8,
"rdata": "199.16.156.6"
}
TLS
可能包括的域:
tls.subjecttls.issuer-
tls.session_resumed
扩展域: tls.serialtls.fingerprinttls.snitls.versiontls.notbeforetls.notaftertls.certificatetls.chain
fast.log输出
这个文件中,每个Alert事件对应一行输出,给出攻击的端口和对攻击可能的分类。见http://suricata.readthedocs.io/en/latest/configuration/suricata-yaml.html?highlight=fast.log#line-based-alerts-log-fast-log
例子:
10/05/10-10:08:59.667372 [**] [1:2009187:4] ET WEB_CLIENT ACTIVEX iDefense
COMRaider ActiveX Control Arbitrary File Deletion [**] [Classification: Web
Application Attack] [Priority: 3] {TCP} xx.xx.232.144:80 -> 192.168.1.4:56068
Wireshark
首先安装Wireshark(https://askubuntu.com/questions/700712/how-to-install-wireshark)。
然后直接打开pcap文件。(https://www.wireshark.org/docs/wsug_html_chunked/ChIOOpenSection.html)
任务
任务1 分析实验结果
任务描述
本实验中给出的pcap文件内容均为DoS攻击的数据包,请根据Suricata的检测结果分析DoS攻击的端口以及服务,并简要描述该服务的内容。
任务结果
1.pcap
suricata -c /etc/suricata/suricata.yaml -r 1.pcap -l ./1
- eve.json
{
"timestamp":"2017-12-03T01:17:04.267748",
"pcap_cnt":6,
"event_type":"alert",
"src_ip":"192.168.234.1",
"src_port":59144,
"dest_ip":"192.168.234.128",
"dest_port":53,
"proto":"UDP",
"alert":{
"action":"allowed",
"gid":1,
"signature_id":2009701,
"rev":2,
"signature":"ET DOS DNS BIND 9 Dynamic Update DoS attempt",
"category":"Attempted Denial of Service",
"severity":2
}
}
{
"timestamp":"2017-12-03T01:17:04.267852",
"pcap_cnt":8,
"event_type":"alert",
"src_ip":"192.168.234.1",
"src_port":59145,
"dest_ip":"192.168.234.128",
"dest_port":53,
"proto":"UDP",
"alert":{
"action":"allowed",
"gid":1,
"signature_id":2009701,
"rev":2,
"signature":"ET DOS DNS BIND 9 Dynamic Update DoS attempt",
"category":"Attempted Denial of Service",
"severity":2
}
}
{
"timestamp":"2017-12-03T01:17:04.267967",
"pcap_cnt":14,
"event_type":"alert",
"src_ip":"192.168.234.1",
"src_port":59147,
"dest_ip":"192.168.234.128",
"dest_port":53,
"proto":"UDP",
"alert":{
"action":"allowed",
"gid":1,
"signature_id":2009701,
"rev":2,
"signature":"ET DOS DNS BIND 9 Dynamic Update DoS attempt",
"category":"Attempted Denial of Service",
"severity":2
}
}
{
"timestamp":"2017-12-03T01:17:04.268004",
"pcap_cnt":16,
"event_type":"alert",
"src_ip":"192.168.234.1",
"src_port":59146,
"dest_ip":"192.168.234.128",
"dest_port":53,
"proto":"UDP",
"alert":{
"action":"allowed",
"gid":1,
"signature_id":2009701,
"rev":2,
"signature":"ET DOS DNS BIND 9 Dynamic Update DoS attempt",
"category":"Attempted Denial of Service",
"severity":2
}
}
{
"timestamp":"2017-12-03T01:17:04.268498",
"pcap_cnt":24,
"event_type":"alert",
"src_ip":"192.168.234.1",
"src_port":59148,
"dest_ip":"192.168.234.128",
"dest_port":53,
"proto":"UDP",
"alert":{
"action":"allowed",
"gid":1,
"signature_id":2009701,
"rev":2,
"signature":"ET DOS DNS BIND 9 Dynamic Update DoS attempt",
"category":"Attempted Denial of Service",
"severity":2
}
}
{
"timestamp":"2017-12-03T01:17:04.268534",
"pcap_cnt":34,
"event_type":"alert",
"src_ip":"192.168.234.1",
"src_port":59149,
"dest_ip":"192.168.234.128",
"dest_port":53,
"proto":"UDP",
"alert":{
"action":"allowed",
"gid":1,
"signature_id":2009701,
"rev":2,
"signature":"ET DOS DNS BIND 9 Dynamic Update DoS attempt",
"category":"Attempted Denial of Service",
"severity":2
}
}
{
"timestamp":"2017-12-03T01:17:04.268567",
"pcap_cnt":45,
"event_type":"alert",
"src_ip":"192.168.234.1",
"src_port":59150,
"dest_ip":"192.168.234.128",
"dest_port":53,
"proto":"UDP",
"alert":{
"action":"allowed",
"gid":1,
"signature_id":2009701,
"rev":2,
"signature":"ET DOS DNS BIND 9 Dynamic Update DoS attempt",
"category":"Attempted Denial of Service",
"severity":2
}
}
{
"timestamp":"2017-12-03T01:17:04.275411",
"pcap_cnt":162,
"event_type":"alert",
"src_ip":"192.168.234.1",
"src_port":59151,
"dest_ip":"192.168.234.128",
"dest_port":53,
"proto":"UDP",
"alert":{
"action":"allowed",
"gid":1,
"signature_id":2009701,
"rev":2,
"signature":"ET DOS DNS BIND 9 Dynamic Update DoS attempt",
"category":"Attempted Denial of Service",
"severity":2
}
}
- fast.log
12/03/2017-01:17:04.267748 [**] [1:2009701:2] ET DOS DNS BIND 9 Dynamic Update DoS attempt [**] [Classification: Attempted Denial of Service] [Priority: 2] {UDP} 192.168.234.1:59144 -> 192.168.234.128:53
12/03/2017-01:17:04.267852 [**] [1:2009701:2] ET DOS DNS BIND 9 Dynamic Update DoS attempt [**] [Classification: Attempted Denial of Service] [Priority: 2] {UDP} 192.168.234.1:59145 -> 192.168.234.128:53
12/03/2017-01:17:04.267967 [**] [1:2009701:2] ET DOS DNS BIND 9 Dynamic Update DoS attempt [**] [Classification: Attempted Denial of Service] [Priority: 2] {UDP} 192.168.234.1:59147 -> 192.168.234.128:53
12/03/2017-01:17:04.268004 [**] [1:2009701:2] ET DOS DNS BIND 9 Dynamic Update DoS attempt [**] [Classification: Attempted Denial of Service] [Priority: 2] {UDP} 192.168.234.1:59146 -> 192.168.234.128:53
12/03/2017-01:17:04.268498 [**] [1:2009701:2] ET DOS DNS BIND 9 Dynamic Update DoS attempt [**] [Classification: Attempted Denial of Service] [Priority: 2] {UDP} 192.168.234.1:59148 -> 192.168.234.128:53
12/03/2017-01:17:04.268534 [**] [1:2009701:2] ET DOS DNS BIND 9 Dynamic Update DoS attempt [**] [Classification: Attempted Denial of Service] [Priority: 2] {UDP} 192.168.234.1:59149 -> 192.168.234.128:53
12/03/2017-01:17:04.268567 [**] [1:2009701:2] ET DOS DNS BIND 9 Dynamic Update DoS attempt [**] [Classification: Attempted Denial of Service] [Priority: 2] {UDP} 192.168.234.1:59150 -> 192.168.234.128:53
12/03/2017-01:17:04.275411 [**] [1:2009701:2] ET DOS DNS BIND 9 Dynamic Update DoS attempt [**] [Classification: Attempted Denial of Service] [Priority: 2] {UDP} 192.168.234.1:59151 -> 192.168.234.128:53
- http.log(空的)
- stats.log
-------------------------------------------------------------------
Date: 12/29/2017 -- 00:48:22 (uptime: 0d, 00h 00m 00s)
-------------------------------------------------------------------
Counter | TM Name | Value
-------------------------------------------------------------------
dns.memuse | ReceivePcapFile | 0
dns.memcap_state | ReceivePcapFile | 0
dns.memcap_global | ReceivePcapFile | 0
decoder.pkts | ReceivePcapFile | 101800
decoder.bytes | ReceivePcapFile | 7228122
decoder.invalid | ReceivePcapFile | 0
decoder.ipv4 | ReceivePcapFile | 101793
decoder.ipv6 | ReceivePcapFile | 1
decoder.ethernet | ReceivePcapFile | 101800
decoder.raw | ReceivePcapFile | 0
decoder.sll | ReceivePcapFile | 0
decoder.tcp | ReceivePcapFile | 0
decoder.udp | ReceivePcapFile | 101784
decoder.sctp | ReceivePcapFile | 0
decoder.icmpv4 | ReceivePcapFile | 10
decoder.icmpv6 | ReceivePcapFile | 0
decoder.ppp | ReceivePcapFile | 0
decoder.pppoe | ReceivePcapFile | 0
decoder.gre | ReceivePcapFile | 0
decoder.vlan | ReceivePcapFile | 0
decoder.vlan_qinq | ReceivePcapFile | 0
decoder.teredo | ReceivePcapFile | 0
decoder.ipv4_in_ipv6 | ReceivePcapFile | 0
decoder.ipv6_in_ipv6 | ReceivePcapFile | 0
decoder.avg_pkt_size | ReceivePcapFile | 71
decoder.max_pkt_size | ReceivePcapFile | 157
defrag.ipv4.fragments | ReceivePcapFile | 0
defrag.ipv4.reassembled | ReceivePcapFile | 0
defrag.ipv4.timeouts | ReceivePcapFile | 0
defrag.ipv6.fragments | ReceivePcapFile | 0
defrag.ipv6.reassembled | ReceivePcapFile | 0
defrag.ipv6.timeouts | ReceivePcapFile | 0
defrag.max_frag_hits | ReceivePcapFile | 0
tcp.sessions | Detect | 0
tcp.ssn_memcap_drop | Detect | 0
tcp.pseudo | Detect | 0
tcp.invalid_checksum | Detect | 0
tcp.no_flow | Detect | 0
tcp.reused_ssn | Detect | 0
tcp.memuse | Detect | 0
tcp.syn | Detect | 0
tcp.synack | Detect | 0
tcp.rst | Detect | 0
dns.memuse | Detect | 0
dns.memcap_state | Detect | 0
dns.memcap_global | Detect | 0
tcp.segment_memcap_drop | Detect | 0
tcp.stream_depth_reached | Detect | 0
tcp.reassembly_memuse | Detect | 0
tcp.reassembly_gap | Detect | 0
http.memuse | Detect | 0
http.memcap | Detect | 0
detect.alert | Detect | 8
flow_mgr.closed_pruned | FlowManagerThread | 0
flow_mgr.new_pruned | FlowManagerThread | 1
flow_mgr.est_pruned | FlowManagerThread | 0
flow.memuse | FlowManagerThread | 6116224
flow.spare | FlowManagerThread | 10000
flow.emerg_mode_entered | FlowManagerThread | 0
flow.emerg_mode_over | FlowManagerThread | 0
下面我们来分析fast.log。
首先可以看出,攻击的类型是DoS(拒绝服务攻击,https://zh.wikipedia.org/wiki/%E9%98%BB%E6%96%B7%E6%9C%8D%E5%8B%99%E6%94%BB%E6%93%8A;如果是分布式就变成很有名的DDoS了),攻击的端口是53,攻击类型是BIND 9 Dynamic Update DoS Security Update,被攻击的服务是DNS记录更新。
但是BIND 9 Dynamic Update DoS Security Update是什么呢?看起来好像是2009年发现的各种Linux和Windows域名服务器使用的named软件中的一个漏洞。以下内容翻译自https://www.cyberciti.biz/tips/bind-dynamic-update-dos.html
BIND 9是DNS协议的一种实现。和很多其他操作系统一样,UNIX也使用named daemon(一个DNS软件)作为互联网域名服务器。(?)可能会发送动态更新消息来更新域名服务器主区域中的记录,当named程序受到了一个精心构造的动态更新消息时,一个内部断言会被触发,因此程序会退出。因此,一个能够向一个域名服务器发送DNS请求的攻击者可以导致域名服务器退出,进行一次拒绝服务攻击(Denial of Service)。仅仅将named配置为忽略动态更新是不足以保护它免于此类攻击的。
2.pcap
suricata -c /etc/suricata/suricata.yaml -r 2.pcap -l ./2
- eve.json
{
"timestamp":"2017-12-03T01:12:30.455015",
"pcap_cnt":1,
"event_type":"alert",
"src_ip":"192.168.234.1",
"src_port":57611,
"dest_ip":"192.168.234.128",
"dest_port":69,
"proto":"UDP",
"alert":{
"action":"allowed",
"gid":1,
"signature_id":0,
"rev":0,
"signature":"ET DOS Possible SolarWinds TFTP Server Read Request Denial Of Service Attempt",
"category":"",
"severity":3
}
}
{
"timestamp":"2017-12-03T01:12:30.455355",
"pcap_cnt":3,
"event_type":"alert",
"src_ip":"192.168.234.1",
"src_port":57613,
"dest_ip":"192.168.234.128",
"dest_port":69,
"proto":"UDP",
"alert":{
"action":"allowed",
"gid":1,
"signature_id":0,
"rev":0,
"signature":"ET DOS Possible SolarWinds TFTP Server Read Request Denial Of Service Attempt",
"category":"",
"severity":3
}
}
{
"timestamp":"2017-12-03T01:12:30.455407",
"pcap_cnt":5,
"event_type":"alert",
"src_ip":"192.168.234.1",
"src_port":57614,
"dest_ip":"192.168.234.128",
"dest_port":69,
"proto":"UDP",
"alert":{
"action":"allowed",
"gid":1,
"signature_id":0,
"rev":0,
"signature":"ET DOS Possible SolarWinds TFTP Server Read Request Denial Of Service Attempt",
"category":"",
"severity":3
}
}
{
"timestamp":"2017-12-03T01:12:30.455443",
"pcap_cnt":7,
"event_type":"alert",
"src_ip":"192.168.234.1",
"src_port":57612,
"dest_ip":"192.168.234.128",
"dest_port":69,
"proto":"UDP",
"alert":{
"action":"allowed",
"gid":1,
"signature_id":0,
"rev":0,
"signature":"ET DOS Possible SolarWinds TFTP Server Read Request Denial Of Service Attempt",
"category":"",
"severity":3
}
}
{
"timestamp":"2017-12-03T01:12:30.455480",
"pcap_cnt":9,
"event_type":"alert",
"src_ip":"192.168.234.1",
"src_port":57615,
"dest_ip":"192.168.234.128",
"dest_port":69,
"proto":"UDP",
"alert":{
"action":"allowed",
"gid":1,
"signature_id":0,
"rev":0,
"signature":"ET DOS Possible SolarWinds TFTP Server Read Request Denial Of Service Attempt",
"category":"",
"severity":3
}
}
{
"timestamp":"2017-12-03T01:12:30.455568",
"pcap_cnt":17,
"event_type":"alert",
"src_ip":"192.168.234.1",
"src_port":57616,
"dest_ip":"192.168.234.128",
"dest_port":69,
"proto":"UDP",
"alert":{
"action":"allowed",
"gid":1,
"signature_id":0,
"rev":0,
"signature":"ET DOS Possible SolarWinds TFTP Server Read Request Denial Of Service Attempt",
"category":"",
"severity":3
}
}
{
"timestamp":"2017-12-03T01:12:30.455578",
"pcap_cnt":21,
"event_type":"alert",
"src_ip":"192.168.234.1",
"src_port":57617,
"dest_ip":"192.168.234.128",
"dest_port":69,
"proto":"UDP",
"alert":{
"action":"allowed",
"gid":1,
"signature_id":0,
"rev":0,
"signature":"ET DOS Possible SolarWinds TFTP Server Read Request Denial Of Service Attempt",
"category":"",
"severity":3
}
}
{
"timestamp":"2017-12-03T01:12:30.466858",
"pcap_cnt":253,
"event_type":"alert",
"src_ip":"192.168.234.1",
"src_port":57618,
"dest_ip":"192.168.234.128",
"dest_port":69,
"proto":"UDP",
"alert":{
"action":"allowed",
"gid":1,
"signature_id":0,
"rev":0,
"signature":"ET DOS Possible SolarWinds TFTP Server Read Request Denial Of Service Attempt",
"category":"",
"severity":3
}
}
- fast.log
12/03/2017-01:12:30.455015 [**] [1:0:0] ET DOS Possible SolarWinds TFTP Server Read Request Denial Of Service Attempt [**] [Classification: (null)] [Priority: 3] {UDP} 192.168.234.1:57611 -> 192.168.234.128:69
12/03/2017-01:12:30.455355 [**] [1:0:0] ET DOS Possible SolarWinds TFTP Server Read Request Denial Of Service Attempt [**] [Classification: (null)] [Priority: 3] {UDP} 192.168.234.1:57613 -> 192.168.234.128:69
12/03/2017-01:12:30.455407 [**] [1:0:0] ET DOS Possible SolarWinds TFTP Server Read Request Denial Of Service Attempt [**] [Classification: (null)] [Priority: 3] {UDP} 192.168.234.1:57614 -> 192.168.234.128:69
12/03/2017-01:12:30.455443 [**] [1:0:0] ET DOS Possible SolarWinds TFTP Server Read Request Denial Of Service Attempt [**] [Classification: (null)] [Priority: 3] {UDP} 192.168.234.1:57612 -> 192.168.234.128:69
12/03/2017-01:12:30.455480 [**] [1:0:0] ET DOS Possible SolarWinds TFTP Server Read Request Denial Of Service Attempt [**] [Classification: (null)] [Priority: 3] {UDP} 192.168.234.1:57615 -> 192.168.234.128:69
12/03/2017-01:12:30.455568 [**] [1:0:0] ET DOS Possible SolarWinds TFTP Server Read Request Denial Of Service Attempt [**] [Classification: (null)] [Priority: 3] {UDP} 192.168.234.1:57616 -> 192.168.234.128:69
12/03/2017-01:12:30.455578 [**] [1:0:0] ET DOS Possible SolarWinds TFTP Server Read Request Denial Of Service Attempt [**] [Classification: (null)] [Priority: 3] {UDP} 192.168.234.1:57617 -> 192.168.234.128:69
12/03/2017-01:12:30.466858 [**] [1:0:0] ET DOS Possible SolarWinds TFTP Server Read Request Denial Of Service Attempt [**] [Classification: (null)] [Priority: 3] {UDP} 192.168.234.1:57618 -> 192.168.234.128:69
- http.log(空文件)
- stats.log
-------------------------------------------------------------------
Date: 12/29/2017 -- 00:48:33 (uptime: 0d, 00h 00m 02s)
-------------------------------------------------------------------
Counter | TM Name | Value
-------------------------------------------------------------------
dns.memuse | ReceivePcapFile | 0
dns.memcap_state | ReceivePcapFile | 0
dns.memcap_global | ReceivePcapFile | 0
decoder.pkts | ReceivePcapFile | 114435
decoder.bytes | ReceivePcapFile | 7552930
decoder.invalid | ReceivePcapFile | 0
decoder.ipv4 | ReceivePcapFile | 114431
decoder.ipv6 | ReceivePcapFile | 0
decoder.ethernet | ReceivePcapFile | 114435
decoder.raw | ReceivePcapFile | 0
decoder.sll | ReceivePcapFile | 0
decoder.tcp | ReceivePcapFile | 0
decoder.udp | ReceivePcapFile | 114421
decoder.sctp | ReceivePcapFile | 0
decoder.icmpv4 | ReceivePcapFile | 10
decoder.icmpv6 | ReceivePcapFile | 0
decoder.ppp | ReceivePcapFile | 0
decoder.pppoe | ReceivePcapFile | 0
decoder.gre | ReceivePcapFile | 0
decoder.vlan | ReceivePcapFile | 0
decoder.vlan_qinq | ReceivePcapFile | 0
decoder.teredo | ReceivePcapFile | 0
decoder.ipv4_in_ipv6 | ReceivePcapFile | 0
decoder.ipv6_in_ipv6 | ReceivePcapFile | 0
decoder.avg_pkt_size | ReceivePcapFile | 66
decoder.max_pkt_size | ReceivePcapFile | 94
defrag.ipv4.fragments | ReceivePcapFile | 0
defrag.ipv4.reassembled | ReceivePcapFile | 0
defrag.ipv4.timeouts | ReceivePcapFile | 0
defrag.ipv6.fragments | ReceivePcapFile | 0
defrag.ipv6.reassembled | ReceivePcapFile | 0
defrag.ipv6.timeouts | ReceivePcapFile | 0
defrag.max_frag_hits | ReceivePcapFile | 0
tcp.sessions | Detect | 0
tcp.ssn_memcap_drop | Detect | 0
tcp.pseudo | Detect | 0
tcp.invalid_checksum | Detect | 0
tcp.no_flow | Detect | 0
tcp.reused_ssn | Detect | 0
tcp.memuse | Detect | 0
tcp.syn | Detect | 0
tcp.synack | Detect | 0
tcp.rst | Detect | 0
dns.memuse | Detect | 0
dns.memcap_state | Detect | 0
dns.memcap_global | Detect | 0
tcp.segment_memcap_drop | Detect | 0
tcp.stream_depth_reached | Detect | 0
tcp.reassembly_memuse | Detect | 0
tcp.reassembly_gap | Detect | 0
http.memuse | Detect | 0
http.memcap | Detect | 0
detect.alert | Detect | 8
flow_mgr.closed_pruned | FlowManagerThread | 0
flow_mgr.new_pruned | FlowManagerThread | 0
flow_mgr.est_pruned | FlowManagerThread | 0
flow.memuse | FlowManagerThread | 6115840
flow.spare | FlowManagerThread | 10000
flow.emerg_mode_entered | FlowManagerThread | 0
flow.emerg_mode_over | FlowManagerThread | 0
下面我们来分析fast.log。
SolarWinds TFTP 服务器10.4.0.10及之前的版本可能会受到拒绝服务攻击。通过发送读请求netascii及一个特殊构造的文件名,远程攻击者可以令服务器的进程崩溃,因而导致拒绝服务攻击。
(参见https://www.rapid7.com/db/modules/auxiliary/dos/windows/tftp/solarwinds和https://www.vulnerabilitycenter.com/#!vul=25904)
3.pcap
suricata -c /etc/suricata/suricata.yaml -r 3.pcap -l ./3
于是打出来了若干个文件。
- eve.json
{
"timestamp":"2017-12-03T01:13:59.506103",
"pcap_cnt":3,
"event_type":"alert",
"src_ip":"192.168.234.1",
"src_port":52322,
"dest_ip":"192.168.234.128",
"dest_port":123,
"proto":"UDP",
"alert":{
"action":"allowed",
"gid":1,
"signature_id":2019016,
"rev":3,
"signature":"ET DOS Possible NTP DDoS Inbound attack",
"category":"Attempted Denial of Service",
"severity":2
}
}
- fast.log
12/03/2017-01:13:59.506103 [**] [1:2019016:3] ET DOS Possible NTP DDoS Inbound attack [**] [Classification: Attempted Denial of Service] [Priority: 2] {UDP} 192.168.234.1:52322 -> 192.168.234.128:123
- http.log(空的)
- stats.log
-------------------------------------------------------------------
Date: 12/29/2017 -- 00:46:31 (uptime: 0d, 00h 00m 00s)
-------------------------------------------------------------------
Counter | TM Name | Value
-------------------------------------------------------------------
dns.memuse | ReceivePcapFile | 0
dns.memcap_state | ReceivePcapFile | 0
dns.memcap_global | ReceivePcapFile | 0
decoder.pkts | ReceivePcapFile | 104423
decoder.bytes | ReceivePcapFile | 6370023
decoder.invalid | ReceivePcapFile | 0
decoder.ipv4 | ReceivePcapFile | 104417
decoder.ipv6 | ReceivePcapFile | 0
decoder.ethernet | ReceivePcapFile | 104423
decoder.raw | ReceivePcapFile | 0
decoder.sll | ReceivePcapFile | 0
decoder.tcp | ReceivePcapFile | 0
decoder.udp | ReceivePcapFile | 104407
decoder.sctp | ReceivePcapFile | 0
decoder.icmpv4 | ReceivePcapFile | 10
decoder.icmpv6 | ReceivePcapFile | 0
decoder.ppp | ReceivePcapFile | 0
decoder.pppoe | ReceivePcapFile | 0
decoder.gre | ReceivePcapFile | 0
decoder.vlan | ReceivePcapFile | 0
decoder.vlan_qinq | ReceivePcapFile | 0
decoder.teredo | ReceivePcapFile | 0
decoder.ipv4_in_ipv6 | ReceivePcapFile | 0
decoder.ipv6_in_ipv6 | ReceivePcapFile | 0
decoder.avg_pkt_size | ReceivePcapFile | 61
decoder.max_pkt_size | ReceivePcapFile | 89
defrag.ipv4.fragments | ReceivePcapFile | 0
defrag.ipv4.reassembled | ReceivePcapFile | 0
defrag.ipv4.timeouts | ReceivePcapFile | 0
defrag.ipv6.fragments | ReceivePcapFile | 0
defrag.ipv6.reassembled | ReceivePcapFile | 0
defrag.ipv6.timeouts | ReceivePcapFile | 0
defrag.max_frag_hits | ReceivePcapFile | 0
tcp.sessions | Detect | 0
tcp.ssn_memcap_drop | Detect | 0
tcp.pseudo | Detect | 0
tcp.invalid_checksum | Detect | 0
tcp.no_flow | Detect | 0
tcp.reused_ssn | Detect | 0
tcp.memuse | Detect | 0
tcp.syn | Detect | 0
tcp.synack | Detect | 0
tcp.rst | Detect | 0
dns.memuse | Detect | 0
dns.memcap_state | Detect | 0
dns.memcap_global | Detect | 0
tcp.segment_memcap_drop | Detect | 0
tcp.stream_depth_reached | Detect | 0
tcp.reassembly_memuse | Detect | 0
tcp.reassembly_gap | Detect | 0
http.memuse | Detect | 0
http.memcap | Detect | 0
detect.alert | Detect | 1
flow_mgr.closed_pruned | FlowManagerThread | 0
flow_mgr.new_pruned | FlowManagerThread | 0
flow_mgr.est_pruned | FlowManagerThread | 0
flow.memuse | FlowManagerThread | 6115840
flow.spare | FlowManagerThread | 10000
flow.emerg_mode_entered | FlowManagerThread | 0
flow.emerg_mode_over | FlowManagerThread | 0
下面我们来分析fast.log。
很显然,攻击的端口是123,而攻击类型是NTP amplification attack,被攻击的服务是NTP(Network Time Protocol
)。
在这类攻击中,攻击者对公开的NTP服务器进行攻击,使对方的UDP流量过大。
NTP是最老的网络协议之一,连接到互联网的电脑用这一协议来同步时钟。除了同步时钟之外,旧版本的NTP支持一种管理服务,使得管理员能够查询某个NTP服务器的流量。这个命令的名称为monlist,会将与被查询的服务器连接的最近的600个主机返回。
在最基础的NTP amplification attack中,攻击者会不断向一个NTP服务器发送get monlist指令,同时将发送者的IP地址伪装成NTP服务器的地址。于是,NTP服务器向伪装过的IP地址发送回复,这一回复的大小比请求大得多,使得指向目标服务器的流量显著增多,最终导致服务器无法及时回应正常请求。
任务2 分析pcap文件内容
任务描述
使用包分析软件(如Wireshark)对你检测的pcap文件进行分析,找出主要的源IP、源端口、目的IP、目的端口、包的内容等。
任务结果
1.pcap
包分成如下几类:
| 编号 | 源IP | 源端口 | 目标IP | 目标端口 | 协议类型 | 包的内容 |
|---|---|---|---|---|---|---|
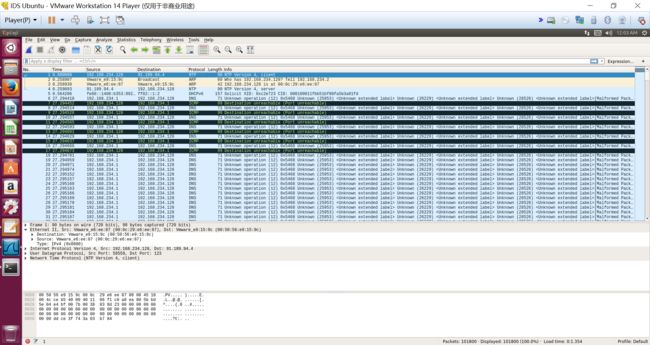
| 1 | 192.188.234.128 | 58559 | 91.189.94.4 | 123 | NTP | NTP version 4, client |
| 2 | Vmware_e9:15:9c | - | Broadcast | - | ARP | Who has 192.168.234.128? Tell 192.168.234.2 |
| 3 | Vmware_e6:ee:87 | - | Vmware_e9:15:9c | - | ARP | 192.168.234.128 is at 00:0c:29:e6:ee:87 |
| 4 | 91.189.94.4 | 123 | 192.168.234.128 | 58559 | NTP | NTP Version 4, server |
| 5 | fe80::1408:b353:892f:9160 | 546 | ff02::1:2 | 547 | DHCPv6 | Solicit XID: 0xc2e723 CID: 000100011fbb51bf80fa5b3a01fd |
| 6, 8, 10, 12, 14, 16, 18, 19, ..., 101794 | 192.168.234.1 | 59144, 59145, 59147, 59146, 59148, ... | 192.168.234.128 | 53 | DNS | Unknown operation (12) 0x5468 Unknown (25953) |
| 7, 9, 11, 13, 15, 17 | 192.168.234.128 | 59144, 59145, 59147, 59146 | 192.168.234.1 | 53 | ICMP | Destination unreachable (Port unreachable) |
| 101795 | Vmware_c0:00:08 | - | Vmware_e6:ee:87 | - | ARP | Who has 192.168.234.128? Tell 192.168.234.1 |
| 101796 | Vmware_e6:ee:87 | - | Vmware_c0:00:08 | - | ARP | 192.168.234.128 is at 00:0c:29:e6:ee:87 |
| 101797 | Vmware_e6:ee:87 | - | Vmware_c0:00:08 | - | ARP | Who has 192.168.234.1? Tell 192.168.234.128 |
| 101798 | Vmware_c0:00:08 | - | Vmware_e6:ee:87 | - | ARP | 192.168.234.1 is at 00:50:56:c0:00:08 |
| 101799 | 192.168.234.128 | 44533 | 91.189.94.4 | 123 | NTP | NTP Version 4, client |
| 101800 | 91.189.94.4 | 123 | 192.168.234.128 | 44533 | NTP | NTP Version 4, server |
总之,就是不断向域名服务器发起构造的DNS请求。按理说服务器应该会不断把named重启,但是显然此处根本没有收到请求。
(这里也和3.pcap一样,用到了NTP协议,但这里的协议就是version 4的,3中用到的就是version 2,因为是旧协议所以对3才能进行攻击。)
2.pcap
包分成如下几类:
| 编号 | 源IP | 源端口 | 目标IP | 目标端口 | 协议类型 | 包的内容 |
|---|---|---|---|---|---|---|
| 1, 3, 5, 7, 9, 11, 13, 14, …, 114431 | 192.168.234.1 | 57611, 57613, 57614, ... | 192.168.234.128 | 69 | TFTP | Destination unreachable (Port unreachable) |
| 2, 4, 6, 8, 10, 12 | 192.168.234.128 | 57611, 57613, 57614, 57612, 57615 | 192.168.234.1 | 69 | ICMP | Destination unreachable (Port unreachable) |
| 114432 | Vmware_e6:ee:87 | ? | Vmware_c0:00:08 | ? | ARP | Who has 192.168.234.1? Tell 192.168.234.128 |
| 114433 | Vmware_c0:00:08 | ? | Vmware_e6:ee:87 | ? | ARP | 192.168.234.1 is at 00:50:56:c0:00:08 |
| 114434 | Vmware_c0:00:08 | ? | Vmware_e6:ee:87 | ? | ARP | Who has 192.168.234.128? Tell 192.168.234.1 |
| 114435 | Vmware_e6:ee:87 | ? | Vmware_c0:00:08 | ? | ARP | 192.168.234.128 is at 00:0c:29:e6:ee:87 |
就是,在不断地发送TFTP请求。
3.pcap
包分成如下几类:
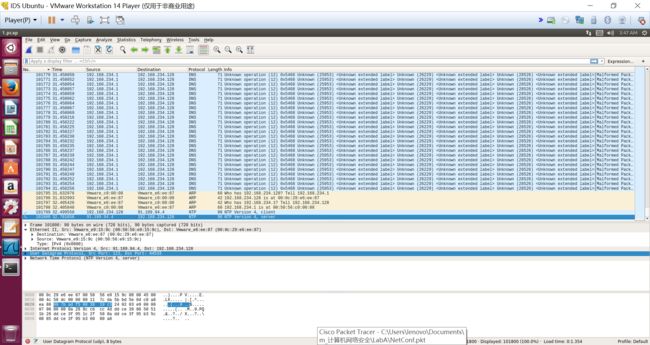
| 编号 | 源IP | 源端口 | 目标IP | 目标端口 | 协议类型 | 包的内容 |
|---|---|---|---|---|---|---|
| 1, 3, 5, 7, 9, 11, 13, 14, …, 104419 | 192.168.234.1 | 52321, 52322, 52324, 52325, 52326, 52327, ... | 192.168.234.128 | 123 | NTP | NTP version 2, server |
| 2, 4, 6, 8, 10, 12 | 192.168.234.128 | 52321, 52324, 52325 | 192.168.234.1 | 123 | ICMP | Destination unreachable (Port unreachable) |
| 104420 | Vmware_c0:00:08 | - | Vmware_e6:ee:87 | - | ARP | Who has 192.168.234.128? Tell 192.168.234.1 |
| 104421 | Vmware_e6:ee:87 | - | Vmware_c0:00:08 | - | ARP | 192.168.234.128 is at 00:0c:29:e6:ee:87 |
| 104422 | Vmware_e6:ee:87 | - | Vmware_c0:00:08 | - | ARP | Who has 192.168.234.1? Tell 192.168.234.128 |
| 104423 | Vmware_c0:00:08 | - | Vmware_e6:ee:87 | - | ARP | 192.168.234.1 is at 00:50:56:c0:00:08 |
可以看出,整个pcap文件主要是192.168.234.1在向192.168.234.128:123发送NTP请求,进行攻击。开始时,192.168.234.128回复了一些ICMP消息(大概是根本就没有连接上?),用来传输出错信息,后来就不回复了。最后有一些ARP表项。
附录
很高兴老师给我们延期到了1月1日。
其实我还是没有搞明白pcap文件是怎么来的(是编程写出来的,还是Wireshark的实际抓包?),以及Suricata怎么分析pcap文件得出这是什么攻击。看来Suricata还是很厉害。
实验中有几个亮点。