这个实验是我上
IE
课做的。我把它做了一遍并按实验报告的方式写了出来,说明的很详细,不是以
show run
形式呈现的,以便大家更容易地看懂。呵呵,写写这些东西花了两个多小时。我觉得这种对于点数少还是比较实用的。如果多的话最好还是用
DM×××
,这样便于以后更好的管理和扩展。
实验目的:
1、掌握点到多点的×××的配置
1、掌握点到多点的×××的配置
2
、让所有
NAT
下的私网都能上
internet
(在
R4
上用
loopback
模拟)
实验要求:
1 、配置 R1—R2 , R1—R3 的 ×××
1 、配置 R1—R2 , R1—R3 的 ×××
2
、
R1--R2
使用
DES
加密,
R1—R3
使用
3DES
加密
3 、让所有 NAT 下的私网都能上 internet
3 、让所有 NAT 下的私网都能上 internet
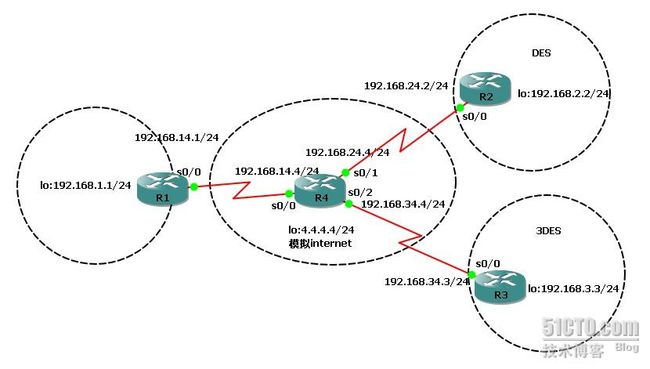
一、拓扑图:
二、实验的详细配置:
1
、配置各路由器的
IP
(略)。为保证网络的连通性,
R1
、
R2
、
R3
配置默认路由:
|
R1(config)#ip route 0.0.0.0 0.0.0.0 192.168.14.4
R2(config)#ip route 0.0.0.0 0.0.0.0 192.168.24.4
R3(config)#ip route 0.0.0.0 0.0.0.0 192.168.34.4
R4(config)#ip route 192.168.1.0 255.255.255.0 192.168.14.1
R4(config)#ip route 192.168.2.0 255.255.255.0 192.168.24.2
R4(config)#ip route 192.168.3.0 255.255.255.0 192.168.34.3
|
2
、根据拓扑配置
R1—R2
、
R1—R3
的点到多点的
×××
,需要说明一下,配置
×××
的时候,按照先定义感兴趣数据流(建议用扩展
ACL
来做,因为普通的
ACL
删掉一项的话会把整个
ACL
全删掉),下一步是配置
ISAKMP
、再就是
IPSEC
的配置,最后关联到加密图里去:
|
R1(config)#ip access-list extended ×××12
(使用扩展
ACL
定义
R1—R2
的感兴趣流)
R1(config-ext-nacl)#permit ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
R1(config-ext-nacl)#exit
R1(config)#ip access-list extended ×××13
(使用扩展
ACL
定义
R1—R3
的感兴趣流)
R1(config-ext-nacl)#permit ip 192.168.1.0 0.0.0.255 192.168.3.0 0.0.0.255
R1(config)#crypto isakmp key 0 CISCO12 address 192.168.24.2 (
定义对
R2
的预共享密钥
)
R1(config)#crypto isakmp key 0 CISCO13 address 192.168.34.3(
定义对
R3
的预共享密钥
)
R1(config)#crypto isakmp policy 12
(定义
R1-R2
的
ISAKMP
策略)
R1(config-isakmp)#authentication pre-share
(采用预共享认证模式)
R1(config-isakmp)#encryption des
(使用
DES
加密)
R1(config-isakmp)#hash md5
R1(config-isakmp)#group 2
(使用
Diffie-Hellman group 2
管理)
R1(config)#crypto isakmp policy 13
(定义
R1-R3
的
ISAKMP
策略)
R1(config-isakmp)#authentication pre-share
R1(config-isakmp)#encryption 3des
R1(config-isakmp)#hash md5
R1(config-isakmp)#group 2
R1(config)#crypto ipsec transform-set ×××12 esp-3des esp-md5-hmac
(配置
R1-R2 IPSEC
变换集)
R1(cfg-crypto-trans)#exit
R1(config)#crypto ipsec transform-set ×××13 esp-3des esp-md5-hmac
(配置
R1-R3 IPSEC
变换集)
R1(config)#crypto map ××× 12 ipsec-isakmp
(针对
R1-R2
的加密图映射表)
R1(config-crypto-map)#set peer 192.168.24.2
(设置对等体)
R1(config-crypto-map)#match add ×××12
(匹配扩展的
ACL
名为
×××12
)
R1(config-crypto-map)#set transform-set ×××12
(引用对
R1-R2
设置的
IPSEC
的变换集)
R1(config-crypto-map)#exit
R1(config)#crypto map ××× 13 ipsec-isakmp
(针对
R1-R3
的加密图映射表)
R1(config-crypto-map)#set peer 192.168.34.3
R1(config-crypto-map)#match add ×××13
(匹配扩展的
ACL
名为
×××13
)
R1(config-crypto-map)#set transform-set ×××13
(引用对
R1-R3
设置的
IPSEC
的变换集)
R1(config-crypto-map)#int s0/0
R1(config-if)#crypto map ×××
(挂接加密图到接口)
R2(config)#ip access-list extended ×××12
R2(config-ext-nacl)#permit ip 192.168.2.0 0.0.0.255 192.168.1.0 0.0.0.255
(在
R2
上定义
ACL
)
R2(config)#crypto isakmp key 0 CISCO12 address 192.168.14.1
(定义对
R1
的预共享)
R2(config)#crypto isakmp policy 12 (
同理和
R1
对
R2
设置的对应
)
R2(config-isakmp)#authentication pre-share
R2(config-isakmp)#encryption des
R2(config-isakmp)#hash md5
R2(config-isakmp)#group 2
R2(config-isakmp)#exit
R2(config)#crypto ipsec transform-set ×××12 esp-3des esp-md5-hmac
(
R1
和
R2
间的变换集)
R2(cfg-crypto-trans)#exit
R2(config)#crypto map ××× 12 ipsec-isakmp
(配置加密图映射表)
R2(config-crypto-map)#match add ×××12
(匹配
ACL
)
R2(config-crypto-map)#set transform-set ×××12
(引用之前设置的变换集)
R2(config-ext-nacl)#int s0/0
R2(config-if)#crypto map ×××
(挂接加密图到接口)
R3(config)#ip access-list extended ×××13
R3(config-ext-nacl)#permit ip 192.168.3.0 0.0.0.255 192.168.1.0 0.0.0.255
R3(config)#crypto isakmp key 0 CISCO13 address 192.168.14.1
R3(config)#crypto isakmp policy 13
(同理和
R1
对
R3
一致)
R3(config-isakmp)#authentication pre
R3(config-isakmp)#authentication pre-share
R3(config-isakmp)#en
R3(config-isakmp)#encryption 3des
R3(config-isakmp)#hash md5
R3(config-isakmp)#group 2
R3(config-isakmp)#exit
R3(config)#crypto ipsec transform-set ×××13 esp-3des esp-md5-hmac
(设置
ipsec
变换集)
R3(cfg-crypto-trans)#exit
R3(config)#crypto map ××× 13 IPSec-isakmp
(在
R3
上设置加密图映射表)
R3(config-crypto-map)#set peer 192.168.14.1
(设置对等体)
R3(config-crypto-map)#match add ×××13
(匹配
ACL
)
R3(config-crypto-map)#set transform-set ×××13
(引用之前设置的变换集)
R3(config-crypto-map)#int s0/0
R3(config-if)#crypto map ×××
(挂接加密图到接口)
|
3
、配置完之后,来看一下
×××
的连通性:
|
R1#ping ip
Target IP address: 192.168.2.2
Repeat count [5]:
Datagram size [100]:
Timeout in seconds [2]:
Extended commands [n]: y
Source address or interface: 192.168.1.1
Type of service [0]:
Set DF bit in IP header? [no]:
Validate reply data? [no]:
Data pattern [0xABCD]:
Loose, Strict, Record, Timestamp, Verbose[none]:
Sweep range of sizes [n]:
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.2.2, timeout is 2 seconds:
Packet sent with a source address of 192.168.1.1
.!!!!
R1#ping ip
Target IP address: 192.168.3.3
Repeat count [5]:
Datagram size [100]:
Timeout in seconds [2]:
Extended commands [n]: y
Source address or interface: 192.168.1.1
Type of service [0]:
Set DF bit in IP header? [no]:
Validate reply data? [no]:
Data pattern [0xABCD]:
Loose, Strict, Record, Timestamp, Verbose[none]:
Sweep range of sizes [n]:
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.3.3, timeout is 2 seconds:
Packet sent with a source address of 192.168.1.1
.!!!!
|
4
、配置
R1
、
R2
、
R3
的
NAT
,让它们都能上
internet(
用
R4
上的
loopback
接口模拟出来的网段
)
,在此要注意一下:
A
:数据包流入路由器的处理过程:
ACL—×××
的解密
—NAT—
策略路由
—
标准路由
B
:数据包流出路由器的处理过程:
NAT—×××
的加密
—ACL—
所以在配置
NAT
的时候一定要
deny
掉定义的
×××
数据流,不然的话数据流会先走
NAT
,
overload
之后
×××
将会不通:
|
R1(config)#ip access-list extended NAT
R1(config-ext-nacl)#deny ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
R1(config-ext-nacl)#deny ip 192.168.1.0 0.0.0.255 192.168.3.0 0.0.0.255
R1(config-ext-nacl)#permit ip 192.168.1.0 0.0.0.255 any
R1(config-ext-nacl)#exit
R1(config)#ip nat inside source list NAT interface s0/0 overload
R1(config)#int s0/0
R1(config-if)#ip nat outside
R1(config-if)#int lo0
R1(config-if)#ip nat inside
R2(config)#ip access-list extended NAT
R2(config-ext-nacl)#deny ip 192.168.2.0 0.0.0.255 192.168.1.0 0.0.0.255
R2(config-ext-nacl)#permit ip 192.168.2.0 0.0.0.255 any
R2(config)#ip nat inside source list NAT interface s0/0 overload
R2(config)#int s0/0
R2(config-if)#ip nat outside
R2(config-if)#int lo0
R2(config-if)#ip nat inside
R3(config)#ip access-list extended NAT
R3(config-ext-nacl)#deny ip 192.168.3.0 0.0.0.255 192.168.1.0 0.0.0.255
R3(config-ext-nacl)#permit ip 192.168.3.0 0.0.0.255 any
R3(config)#ip nat inside source list NAT interface s0/0 overload
R3(config)#int s0/0
R3(config-if)#ip nat outside
R3(config-if)#int lo0
R3(config-if)#ip nat inside
|
5
、再来看一下各路由器的私网能否上
internet
:
|
R1#ping ip
Target IP address: 4.4.4.4
Repeat count [5]:
Datagram size [100]:
Timeout in seconds [2]:
Extended commands [n]: y
Source address or interface: 192.168.1.1
Type of service [0]:
Set DF bit in IP header? [no]:
Validate reply data? [no]:
Data pattern [0xABCD]:
Loose, Strict, Record, Timestamp, Verbose[none]:
Sweep range of sizes [n]:
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 4.4.4.4, timeout is 2 seconds:
Packet sent with a source address of 192.168.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 8/37/84 ms
R1#
R2#ping ip
Target IP address: 4.4.4.4
Repeat count [5]:
Datagram size [100]:
Timeout in seconds [2]:
Extended commands [n]: y
Source address or interface: 192.168.2.2
Type of service [0]:
Set DF bit in IP header? [no]:
Validate reply data? [no]:
Data pattern [0xABCD]:
Loose, Strict, Record, Timestamp, Verbose[none]:
Sweep range of sizes [n]:
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 4.4.4.4, timeout is 2 seconds:
Packet sent with a source address of 192.168.2.2
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 8/38/76 ms
R2#
R3#ping ip
Target IP address: 4.4.4.4
Repeat count [5]:
Datagram size [100]:
Timeout in seconds [2]:
Extended commands [n]: y
Source address or interface: 192.168.3.3
Type of service [0]:
Set DF bit in IP header? [no]:
Validate reply data? [no]:
Data pattern [0xABCD]:
Loose, Strict, Record, Timestamp, Verbose[none]:
Sweep range of sizes [n]:
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 4.4.4.4, timeout is 2 seconds:
Packet sent with a source address of 192.168.3.3
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 4/34/76 ms
R3#
|