精通Office 365 云计算管理 Exchange Online 篇
第 1 章 开始使用 Office 365
1.1 域名管理
注册世纪互联 office 365 时会得到一个初始的Office 365的域名: XXX.partner.onmschina.cn
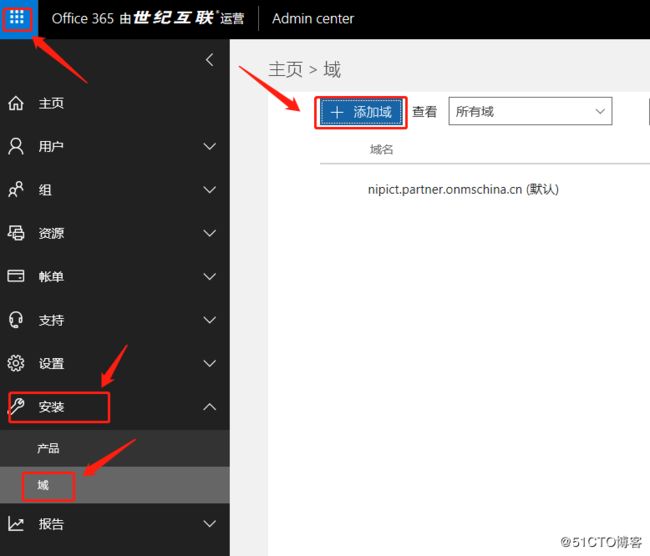
管理员登录 office 365 portal : 左侧“导航栏”--“安装”--"域" -- “添加域”:
https://portal.partner.microsoftOnline.cn
2. 通过PowerShell 管理OFfice 365:
2.1 安装Azure AD Module:
Install-Module AzureAD
Install-Module Msonline
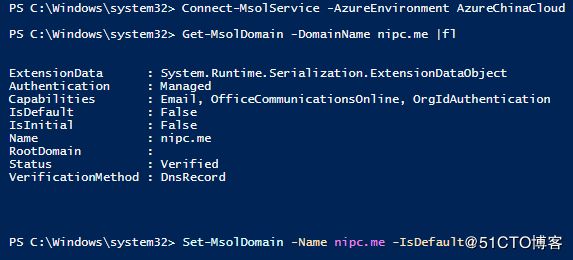
Connect-MsolService -AzureEnvironment AzureChinaCloud
Get-MsolDomain -DomainName nipc.me |fl
设置默认域:
Set-MsolDomain -Name nipc.me -IsDefault
Get-MsolDomain
删除域:
Remove-MsolDomain -DomainName nipc.me
如果自定义的域名在Office 365 全球版上绑定过,即使在Office 365中国版上添加完成,中国版的Exchange管理中心的“接受域”中的也会缺失这个域名,导致邮箱功能不正常。
1.2 用户管理
创建用户:
创建用户的必需属性:
DisplayName 显示名称
UserPrincipalName 用于登录到Office 365服务的用户名 eg: [email protected]
New-MsolUser -DisplayName "Gan Zhiyan" -UserPrincipalName [email protected] -FirstName Gan -LastName Zhiyan -UsageLocation CN -LicenseAssignment reseller-account:O365_BUSINESS_PREMIUM
查询订阅的许可证:
Get-MsolAccountSku
AccountSkuId ActiveUnits WarningUnits ConsumedUnits
------------ ----------- ------------ -------------
reseller-account:O365_BUSINESS_ESSENTIALS 0 0 2
reseller-account:O365_BUSINESS_PREMIUM 2 0 2
批量创建用户:
准备一个CSV文件,其中包含相应的属性:DisplayName,UserPrincipalName,FirstName,LastName,UsageLocation,LicenseAssignment(AccountSkuId)
再通过Powershell 完成批量创建用户:
Import-Csv -Path "C:\users.csv" | foreach {New-MsolUser -DisplayName $_.DisplayName -UserPrincipalName $_.UserPrincipalName -FirstName $_.FirstName -LastName $_.LastName -UsageLocation $_.UsageLocation -LicenseAssignment $_.AccountSkuId} | Export-Csv -Path "C:\Results.csv"
管理员权限角色:
Get-MsolUser | where Displayname -Like "gan*" | sort displayname | select Displayname | more
获取管理员角色名称和描述:
Get-MsolRole | sort name | select Name,Description
Name Description
---- -----------
Application Administrator Can create and manage all aspects of app registrations and enterprise apps.
Application Developer Can create application registrations independent of the 'Users can register applications' setting.
Authentication Administrator Allowed to view, set and reset authentication method information for any non-admin user.
Azure DevOps Administrator Can manage Azure DevOps organization policy and settings.
Azure Information Protection Administrator Can manage all aspects of the Azure Information Protection product.
B2C IEF Keyset Administrator Can manage secrets for federation and encryption in the Identity Experience Framework (IEF).
B2C IEF Policy Administrator Can create and manage trust framework policies in the Identity Experience Framework (IEF).
B2C User Flow Administrator Can create and manage all aspects of user flows.
B2C User Flow Attribute Administrator Can create and manage the attribute schema available to all user flows.
Billing Administrator Can perform common billing related tasks like updating payment information.
Cloud Application Administrator Can create and manage all aspects of app registrations and enterprise apps except App Proxy.
Cloud Device Administrator Full access to manage devices in Azure AD.
Company Administrator Can manage all aspects of Azure AD and Microsoft services that use Azure AD identities.
Compliance Administrator Can read and manage compliance configuration and reports in Azure AD and Office 365.
Compliance Data Administrator Creates and manages compliance content.
Conditional Access Administrator Can manage conditional access capabilities.
CRM Service Administrator Can manage all aspects of the Dynamics 365 product.
Customer LockBox Access Approver Can approve Microsoft support requests to access customer organizational data.
Desktop Analytics Administrator Can access and manage Desktop management tools and services.
Device Administrators Device Administrators
Device Join Device Join
Device Managers Deprecated - Do Not Use.
Device Users Device Users
Directory Readers Can read basic directory information. Commonly used to grant directory read access to applications and guests.
Directory Synchronization Accounts Only used by Azure AD Connect service.
Directory Writers Can read and write basic directory information. For granting access to applications, not intended for users.
Exchange Service Administrator Can manage all aspects of the Exchange product.
External Identity Provider Administrator Can configure identity providers for use in direct federation.
Global Reader Can read everything that a global admin can read but not update anything.
Groups Administrator Members of this role can create/manage groups, create/manage groups settings like naming and expiration policies, and view ...
Guest Inviter Can invite guest users independent of the 'members can invite guests' setting.
Helpdesk Administrator Can reset passwords for non-administrators and Helpdesk Administrators.
Intune Service Administrator Can manage all aspects of the Intune product.
Kaizala Administrator Can manage settings for Microsoft Kaizala.
License Administrator Can manage product licenses on users and groups.
Lync Service Administrator Can manage all aspects of the Skype for Business product.
Message Center Privacy Reader Can read security messages and updates in Office 365 Message Center only.
Message Center Reader Can read messages and updates for their organization in Office 365 Message Center only.
Office Apps Administrator Can manage Office apps cloud services, including policy and settings management, and manage the ability to select, unselect...
Partner Tier1 Support Do not use - not intended for general use.
Partner Tier2 Support Do not use - not intended for general use.
Password Administrator Can reset passwords for non-administrators and Password Administrators.
Power BI Service Administrator Can manage all aspects of the Power BI product.
Printer Administrator Can manage all aspects of printers and printer connectors.
Printer Technician Can manage all aspects of printers and printer connectors.
Privileged Authentication Administrator Allowed to view, set and reset authentication method information for any user (admin or non-admin).
Privileged Role Administrator Can manage role assignments in Azure AD, and all aspects of Privileged Identity Management.
Reports Reader Can read sign-in and audit reports.
Search Administrator Can create and manage all aspects of Microsoft Search settings.
Search Editor Can create and manage the editorial content such as bookmarks, Q and As, locations, floorplan.
Security Administrator Security Administrator allows ability to read and manage security configuration and reports.
Security Operator Creates and manages security events.
Security Reader Can read security information and reports in Azure AD and Office 365.
Service Support Administrator Can read service health information and manage support tickets.
SharePoint Service Administrator Can manage all aspects of the SharePoint service.
Teams Communications Administrator Can manage calling and meetings features within the Microsoft Teams service.
Teams Communications Support Engineer Can troubleshoot communications issues within Teams using advanced tools.
Teams Communications Support Specialist Can troubleshoot communications issues within Teams using basic tools.
Teams Service Administrator Can manage the Microsoft Teams service.
User Account Administrator Can manage all aspects of users and groups, including resetting passwords for limited admins.
Workplace Device Join Workplace Device Join
为账户分配角色:
Add-MsolRoleMember -RoleMemberEmailAddress [email protected] -RoleName "Exchange Service Administrator"
为多个用户分配角色:
创建一个如下的CSV文件,包括显示名称DisplayName和角色名称RoleName
DisplayName,RoleName
"Gan Zhiyan","Exchange Service Administrator"
"Joe Xiao","SharePoint Service Administrator "
"Eric Yan","Helpdesk Administrator"
接下来运行如下命令:
Import-Csv -Path "C:\RoleAdd.csv" | foreach {Add-MsolRoleMember -RoleMemberEmailAddress (Get-MsolUser | Where DisplayName -eq $_.DisplayName).UserPrincipalName -RoleName $_.RoleName } | Export-Csv -Path "C:\RoleAddResults.csv"
注意:只能为用户分配管理员角色,不能为组分配管理员角色。
1.2.2 删除用户:
删除单一用户:
Remove-MsolUser -UserPrincipalName [email protected]
无需提示确认:
Remove-MsolUser -UserPrincipalName [email protected] -Force
如果是目录同步的账户,删除后下次同步还是会还原到活动用户中,因此,对于目录同步的用户,最好的办法就是从本地删除或者不同步这个用户对象。
一次性删除所有用户:
$users=get-msoluser
$users | Remove-MsolUser –Force
$users=Get-MsolUser -All -ReturnDeletedUsers
$users | Remove-MsolUser -RemoveFromRecycleBin -force
移除用户许可证:
Get-MsolAccountSku
Get-MsolUser -All | select UserPrincipalName,Licenses
从现有用户中移除许可证,用Set-MsolUserLicense 带参数 -RemoveLicenses 多个许可证用逗号隔开。
Set-MsolUserLicense -UserPrincipalName [email protected] -RemoveLicenses "reseller-account:O365_BUSINESS_PREMIUM","reseller-account:O365_BUSINESS_ESSENTIALS"
软删除和硬删除用户
软删除用户存放在“已删除的用户”中,在永久删除用户数据前30天内,还可以还原并分配许可,用户仍然可以正常访问数据和服务。
硬删除是用户邮箱已经软删除超过30天,并关联的Office 365用户已经硬删除。将永久删除所有邮箱内容,如电子邮件,联系人和文件。
用以下Powershell 连接到Exchange Online:
$USerCredential = Get-Credential
$Session = New-PSSession -ConfigurationName Microsoft.Exchange -ConnectionUri https://partner.outlook.cn/PowerShell-LiveID/ -Credential $USerCredential -Authentication Basic -AllowRedirection
Import-PSSession $Session
获取软删除邮箱的信息:
Get-Mailbox -SoftDeletedMailbox | Select-Object Name, ExchangeGuid
恢复邮箱:
New-MailboxRestoreRequest -SourceMailbox
查看恢复结果:
Get-MailboxRestoreRequest
管理用户许可证
获取当前组织中的许可计划以及每个计划中包含的服务及顺序(索引号)
(Get-MsolAccountSku | where {$_.AccountSkuid -eq 'reseller-account:O365_BUSINESS_PREMIUM' }).ServiceStatus
ServicePlan ProvisioningStatus
----------- ------------------
Microsoft Bookings Success
SHAREPOINTWAC Success
SHAREPOINTSTANDARD Success
OFFICE_BUSINESS Success
MCOSTANDARD Success
EXCHANGE_S_STANDARD Success
如果只想让用户只使用Exchange Online 其他的服务禁用,然后再给用户分配。
首先定义一个许可证变量,
$LO = New-MsolLicenseOptions -AccountSkuId 'reseller-account:O365_BUSINESS_PREMIUM' -DisabledPlans 'Microsoft Bookings','SHAREPOINTWAC','SHAREPOINTSTANDARD','MCOSTANDARD'
New-MsolUser -UserPrincipalName [email protected] -DisplayName "Gan" -LicenseAssignment "reseller-account:O365_BUSINESS_PREMIUM" -LicenseOptions $LO -UsageLocation CN
如果是多个用户,可创建一个txt 文件,每一行包含一个用户账号:
批量操作如下:
Get-Content "C:\Accounts.txt" | foreach {Set-MsolUserLicense -UserPrincipalName $_ -LicenseOptions $LO}
1.2.4 Office 365 中的多重身份认证(MFA):
“活动用户” 选择 “更多”下拉列表中的“多重身份验证设置”
当用户MFA 后,同时也需要在Exchange Online 中启用新式验证。Exchange Online PowerShell:
Get-OrganizationConfig | ft -Auto Name,OAuth*
看OAuth2ClientProfileEnabled是否为Ture
如果结果为False 通过下列命令改为Ture:
Set-OrganizationConfig -OAuth2ClientProfileEnabled $true
第2章 Exchange Online 管理
2.1 收件人
收件人是可以传递或将邮件路由到的任何已启用邮件的对像。
每种收件人类型在Exchange Online PowerShell 的RecipientTypeDetails 属性中具有有唯一值
2.1.1 用户邮箱
1.创建用户邮箱:
活动用户在分配Exchange online 许可证时自动创建用户邮箱。
2.删除邮箱
Remove-Mailbox -Identity [email protected]
永久删除用户邮箱,删除后无法恢复:
Remove-MsolUser -UserPrincipalName [email protected] -RemoveFromRecycleBin
邮箱删除后,可以通过 Get-Mailbox
邮箱删除后,在未启用诉讼保留或就地保留时,Exchange Online 将保留邮箱及所有内容30天,30天后将永久删除无法恢复。
如果邮箱是通过取消Exchange Online许可删除的,可以在30天内重新分配许可就可以恢复邮箱,
如果是通过“活动用户”进行删除的,则可在30天内从“已删除的用户”中还原用户来恢复邮箱。
3.管理邮件地址:
管理员可以为同一个用户邮箱添加一个"主SMTP地址"和多个"别名"的"代理地址"(最多400个)。