冗余接口
对多8个冗余接口对(使用第一添加的接口mac),介质要一样,切换时,新主用接口发免费ARP更新CAM表,冗余接口同时只有一个在工作(浪费资源)。
ASA(config)# int redundant 1 ASA(config-if)# member-interface g0/0 ASA(config-if)# member-interface g0/1 ASA(config-if)# exit ASA(config)# show int redundant 1 Member GigabitEthernet0/0(Active), GigabitEthernet0/1 ASA(config)# int g0/0 //把主口down了 ASA(config-if)# shutdown ASA(config)# show int redundant 1 //备口启用了 Member GigabitEthernet0/1(Active), GigabitEthernet0/1 ASA(config)# int g0/ //把原来的主口 g0/0启用 ASA(config-if)# no shutdown ASA(config)# show int redundant 1 //主备口不具备抢占特性,源主口no shutdown后并没有1切回 Member GigabitEthernet0/1(Active), GigabitEthernet0/0 //任然是在用g0/1 ASA(config-if)# redundant-interface redundant 1 active-member g0/0 //此时可以手动切回g0/0 ASA(config-if)# show int redundant 1 Member GigabitEthernet0/0(Active), GigabitEthernet0/1
EtherChannel
1、最多8个捆绑一组
2、端口功能相同(duplex,speed.....)
3、具有load-balancing和HA功能
4、可以部署交换机间和服务器与交换机间(需要设备支持channel即可--802.3ad--LACP)
5、vPC(virtual port channels) 允许多个设备共享接口(需要设备支持vpc)
6、vpc最大利用了带宽,原由:每个port channel,在spanning-tree 中当作一个接口,也就不存在环路,没有端口被block
ciscoasa(config)# int g0 ciscoasa(config-if)# channel-group 1 mode active //添加接口到 channel组 1 中 ciscoasa(config-if)# int g1 ciscoasa(config-if)# channel-group 1 mode active ciscoasa(config-if)# exit ciscoasa(config)# int port-channel 1 //为这个channel 设置nameif 安全级别 IP ciscoasa(config-if)# nameif DMZ ciscoasa(config-if)# security-level 50 ciscoasa(config-if)# ip address 10.1.1.1 255.255.255.0 ciscoasa(config-if)# exit
ciscoasa# show interface port-channel 1 //查看 Interface Port-channel1 "DMZ", is down, line protocol is down Hardware is EtherChannel/LACP, BW 100 Mbps, DLY 100 usec (Full-duplex), (100 Mbps) Input flow control is unsupported, output flow control is unsupported MAC address 0000.ab9b.9a00, MTU 1500 IP address 10.1.1.1, subnet mask 255.255.255.0 Members in this channel: Inactive: Gi0 Gi1
ciscoasa# show port-channel 1 load-balance //查看负载均衡的方式 EtherChannel Load-Balancing Configuration: src-dst-ip //根据源目ip地址
ciscoasa(config)# int port-channel 1 ciscoasa(config-if)# port-channel load-balance ? interface mode commands/options: dst-ip Dst IP Addr dst-ip-port Dst IP Addr and TCP/UDP Port dst-mac Dst Mac Addr dst-port Dst TCP/UDP Port src-dst-ip Src XOR Dst IP Addr src-dst-ip-port Src XOR Dst IP Addr and TCP/UDP Port src-dst-mac Src XOR Dst Mac Addr src-dst-port Src XOR Dst TCP/UDP Port // 常用 src-ip Src IP Addr src-ip-port Src IP Addr and TCP/UDP Port src-mac Src Mac Addr src-port Src TCP/UDP Port vlan-dst-ip Vlan, Dst IP Addr vlan-dst-ip-port Vlan, Dst IP Addr and TCP/UDP Port vlan-only Vlan vlan-src-dst-ip Vlan, Src XOR Dst IP Addr vlan-src-dst-ip-port Vlan, Src XOR Dst IP Addr and TCP/UDP Port vlan-src-ip Vlan, Src IP Addr vlan-src-ip-port Vlan, Src IP Addr and TCP/UDP Port
设备冗余
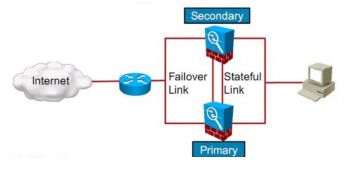
Failover
ASA启动时,开始一个选举的进程
如果它检测到一个正在协商的设备处于FO接口的另一端,此时Primary设备成为Active状态, Secondary设备转到Standby状态
如果它检测到一个Active设备,它就转换成Standby状态
它如果没检测到设备,它将变为Active状态
当它成为active设备之后,检测到了另外一个active设备,那么这两个Active设备将重新协商FO的角色(此时可能会出现网络中断-mac的问题)
ASA出现故障切换时standby继承原active设备的属性(IP、MAC)
无状态化的FO:仅仅是提供硬件冗余
状态化的FO:提供硬件和状态化表项的冗余(也不是所有),两设备间需要一个状态化链路(建议在LAN-FO 之外加一条,流量比较大)
FO或被指定为监控的接口通过hello包确定其他单元的状态
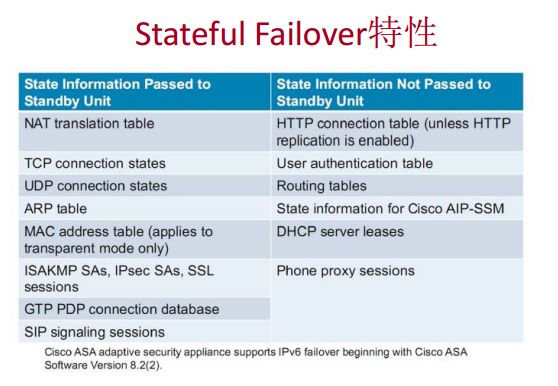
状态化表项复制
部署FO时,考虑如下的部署方针:
可以使用密钥来保护FO通讯
如果状态化链路和FO链路共享接口,需要使用一个可用的高速率的接口,最好不要让状态化链路和普通的数据接口共享一个物理接口
调整FO的各项参数来实现快速切换(默认接口级别25S(每5s一个hello包),心跳线15s(每1s))
在active和standby设备上手动指定MAC地址,来阻止一些可能阻断网络流量的偶然事件(a-a 转 a s的mac问题)
在所有连接防火墙设备的交换机接口上,考虑配置端口快速(PortFast)
配置
primary设备 ! interface GigabitEthernet0 nameif DMZ security-level 50 ip address 10.1.20.11 255.255.255.0 standby 10.1.20.22 ! interface GigabitEthernet1 nameif Inside security-level 100 ip address 10.1.10.11 255.255.255.0 standby 10.1.10.22 ! interface GigabitEthernet2 nameif Outside security-level 0 ip address 10.1.30.11 255.255.255.0 standby 10.1.30.22 ! ASA(config)#int g3 ASA(config-if)# no shu ASA(config)# failover lan unit primary ASA(config)# failover lan interface fo g3 ASA(config)# failover interface ip fo 10.1.1.11 255.255.255.0 standby 10.1.1.22 ASA(config)# failover key cisco ASA(config)# failover Beginning configuration replication: Sending to mate. //会把config 发给mate 同步 primary设备 ciscoasa(config)# int g3 ciscoasa(config-if)# no shu ciscoasa(config-if)# failover lan unit primary ciscoasa(config)# failover lan interface fo g3 ciscoasa(config)# failover key cisco ciscoasa(config)# failover interface ip fo 10.1.1.11 255.255.255.0 standby 10.1.1.22 ciscoasa(config)# failover Beginning configuration replication from mate. //从 mate同步信息,那些做的接口配置什么的都被 当已经发生切换后,ASA FO不支持自动抢占active,需手动配置 ASA(config)# failover active
ASA(config)# show runn failover failover failover lan unit primary failover lan interface fo GigabitEthernet3 failover polltime unit 2 holdtime 10 failover polltime interface 3 holdtime 15 failover key ***** failover mac address GigabitEthernet1 0001.0001.0001 0001.0001.0002 failover mac address GigabitEthernet0 0001.0002.0001 0001.0002.0002 failover mac address GigabitEthernet2 0001.0003.0001 0001.0003.0002 failover interface ip fo 10.1.1.11 255.255.255.0 standby 10.1.1.22
切换时间的调整
ASA(config)# failover polltime unit 2 holdtime 10 //更改心跳线的hello包为2s 超时时间为10s ASA(config)# failover polltime interface 3 holdtime 15 //更改接口hello包为3s 超时15s
配置固定的MAC地址
ASA(config)# failover mac address inside 1.1.1 1.1.2 //前面是active 后面是standby ASA(config)# failover mac address dmz 1.2.1 1.2.2 ASA(config)# failover mac address outside 1.3.1 1.3.2
更改切换触发条件
ASA(config)# monitor-interface Inside (针对某个接口启用健康监控,若受监控的接口fail,切换触发. ) ASA(config)# failover interface-policy 2 (针对具体的接口数目来定义切换条件(范围是1‐250),默认是1个就切换 ) ASA(config)# failover interface-policy 50% (针对接口总数的百分比来定义切换条件(范围1‐100%) )
同步状态化信息
ASA(config)# failover link fo GigabitEthernet3 //会同步状态化信息 ASA(config)# failover active //随便切换,一些需要状态表的连接不会断(如:Telnet,nat)
状态化信息
ASA(config)# show failover Failover On Failover unit Primary Failover LAN Interface: fo GigabitEthernet3 (up) Unit Poll frequency 2 seconds, holdtime 10 seconds Interface Poll frequency 3 seconds, holdtime 15 seconds Interface Policy 1 Monitored Interfaces 3 of 60 maximum Version: Ours 8.4(2), Mate 8.4(2) Last Failover at: 11:55:46 UTC Jul 5 2016 This host: Primary - Active Active time: 6076 (sec) Interface DMZ (10.1.20.11): Normal (Monitored) Interface Inside (10.1.10.11): Normal (Monitored) Interface Outside (10.1.30.11): Normal (Monitored) Other host: Secondary - Standby Ready Active time: 346 (sec) Interface DMZ (10.1.20.22): Normal (Monitored) Interface Inside (10.1.10.22): Normal (Monitored) Interface Outside (10.1.30.22): Normal (Monitored) Stateful Failover Logical Update Statistics Link : fo GigabitEthernet3 (up) Stateful Obj xmit xerr rcv rerr General 101 0 95 0 sys cmd 91 0 91 0 up time 0 0 0 0 RPC services 0 0 0 0 TCP conn 6 0 4 0 UDP conn 0 0 0 0 ARP tbl 3 0 0 0 Xlate_Timeout 0 0 0 0 IPv6 ND tbl 0 0 0 0 ××× IKEv1 SA 0 0 0 0 ××× IKEv1 P2 0 0 0 0 ××× IKEv2 SA 0 0 0 0 ××× IKEv2 P2 0 0 0 0 ××× CTCP upd 0 0 0 0 ××× SDI upd 0 0 0 0 ××× DHCP upd 0 0 0 0 SIP Session 0 0 0 0 Route Session 0 0 0 0 User-Identity 1 0 0 0 Logical Update Queue Information Cur Max Total Recv Q: 0 2 510 Xmit Q: 0 2 484
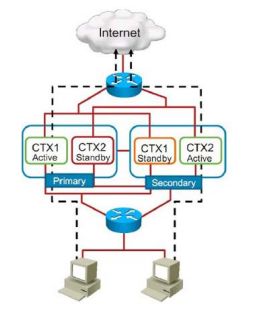
A/A Failover
两个设备在彼此互为备份同时,也能同时转发流量(负载均衡)
注意:负载均衡是通过相邻的路由器来实现的,且必须基于流的负载均衡(基于包的会有问题,表项难以建立).
返回流量需要做特殊处理,否则会出现异步路由问题(去与回不同路,而回路上的子墙是没有状态化表项,可能会阻止)
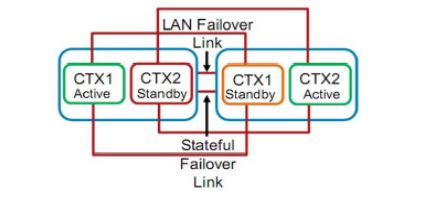
状态FO链路:FO口确定设备状态同步配置
独立接口 传递状态化信息
其他注意事项:
A/A的FO只有设备是多模模式才可使用
– 不支持动态路由协议
– 不支持组播IP路由
– 不支持威胁检测
– 不支持×××
– 不支持电话代理
ASA5505不支持A/A的Failover
A/A配置
步骤
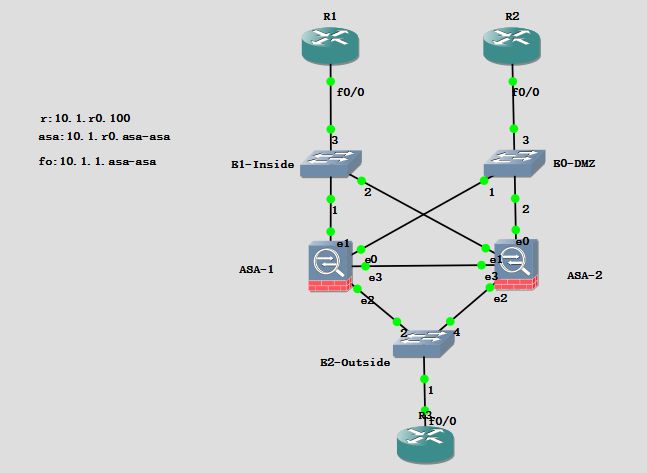
1、初始化工作
inside //IP和路由设置 ! interface FastEthernet0/0 ip address 10.1.10.100 255.255.255.0 ip route 0.0.0.0 0.0.0.0 10.1.10.11 DMZ interface FastEthernet0/0 ip address 10.1.20.100 255.255.255.0 ip route 0.0.0.0 0.0.0.0 10.1.20.11 outside R3(config)#int f0/0 R3(config-if)#no shutdown R3(config-if)#exit R3(config)#int f0/0.10 R3(config-subif)#encapsulation dot1Q 10 R3(config-subif)#ip address 10.1.30.100 255.255.255.0 R3(config-subif)no shutdown R3(config-subif)#exit R3(config)#int f0/0.20 R3(config-subif)#encapsulation dot1Q 20 R3(config-subif)#ip address 10.1.40.100 255.255.255.0 R3(config-subif)no shutdown R3(config-subif)#exit R3(config)#ip route 10.1.10.0 255.255.255.0 10.1.30.11 R3(config)#ip route 10.1.20.0 255.255.255.0 10.1.40.11 ASA1 ciscoasa(config)# int g0 ciscoasa(config-if)# no shutdown ciscoasa(config-if)# int g1 ciscoasa(config-if)# no shutdown ciscoasa(config-if)# int g2 ciscoasa(config-if)# no shutdown ciscoasa(config-if)# int g3 ciscoasa(config-if)# no shutdown ciscoasa(config-if)# exit ciscoasa(config)# int g2.10 ciscoasa(config-subif)# vlan 10 ciscoasa(config-subif)# exit ciscoasa(config)# int g2.20 ciscoasa(config-subif)# vlan 20 ciscoasa(config-subif)# exit
2、子墙创建
ASA-1 配置
创建failover组,标明primary或second,以及设置抢夺 ciscoasa(config)# show runn failover no failover failover group 1 secondary preempt failover group 2 primary preempt ------------------------------------------------------------------------ ciscoasa(config)# show runn context admin-context admin //创建子墙,指定配置文件路径 context admin config-url disk0:/admin.cfg ! context c1 allocate-interface GigabitEthernet0 //为子墙添加端口 allocate-interface GigabitEthernet2.10 config-url disk0:/c1.cfg join-failover-group 1 //指定加入的failover 组 ! context c2 allocate-interface GigabitEthernet1 allocate-interface GigabitEthernet2.20 config-url disk0:/c2.cfg join-failover-group 2 ! ----------------------------------------------------------------------- ASA(config)# changeto c1 //配置 ASA c1接口 ASA/c1(config)# show runn interface ! interface GigabitEthernet0 nameif inside security-level 100 ip address 10.1.10.11 255.255.255.0 standby 10.1.10.22 ! interface GigabitEthernet2.10 nameif ouside security-level 0 ip address 10.1.30.11 255.255.255.0 standby 10.1.30.22 ----------------------------------------------------------------------- ASA(config)# changeto c2 //配置 ASA c1接口 ASA/c2(config)# show runn interface ! interface GigabitEthernet1 nameif inside security-level 100 ip address 10.1.20.11 255.255.255.0 standby 10.1.20.22 ! interface GigabitEthernet2.20 nameif outside security-level 0 ip address 10.1.40.11 255.255.255.0 standby 10.1.40.22 -------------------------------------------------------------------- ASA/c2(config)# changeto system ASA(config)# show running-config failover // 配置failover system信息 no failover //主要是 lan 链路(心跳线)、key failover lan unit primary //和link链路(状态化同步) failover lan interface fo GigabitEthernet3 failover polltime unit 2 holdtime 10 failover polltime interface 3 holdtime 15 failover key cisco failover interface ip fo 10.1.1.11 255.255.255.0 standby 10.1.1.22 failover link fo GigabitEthernet3 //这个fo 得和上面一样才能表示共用g3 failover group 1 secondary preempt failover group 2 primary preempt ASA(config)# failover //最后激活 ---------------------------------------------------------------------------------------
ASA-2 配置
配置key lan link即可 ASA(config)# no failover ASA(config)# int g3 ASA(config-if)# shutdown ASA(config-if)# exit ASA(config)# failover lan unit secondary //指定设备为secondary ASA(config)# failover key cisco ASA(config)# failover lan interface fo g3 ASA(config)# failover link fo g3 ASA(config)# failover interface ip fo 10.1.1.11 255.255.255.0 standby 10.1.1.22 failover group 1 primary secondary preempt failover group 2 secondary preempt ASA(config)# failover -----------------------------------------------------------------
ASA(config)# prompt hostname context state priority //方便看当前信息
这个实并不完全成功:
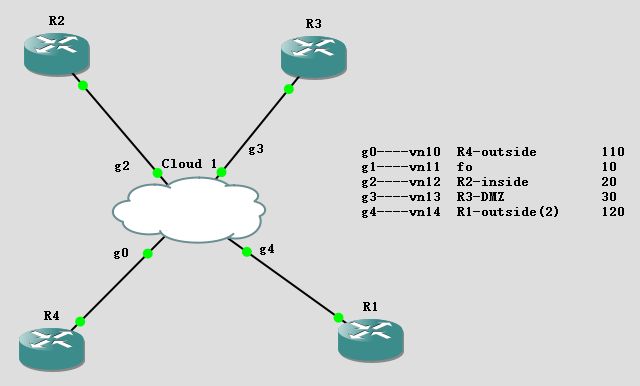
原先用的是QEMU,卡的不行,有时两个ASA同时运行会直接少一个接口,但一个ASA子接口是没问题的
换了vm的ASA,在子接口的通信有问题,由于划分了vlan,这个vm内置的交换机(姑且这么认为)
居然不转发带VLAN标签的包,这我也没办法配置,换了桥接,然并没有用,不传带vlan标签的包就没事,故把实验改了点,全用接口而不用子接口
之后我们任意切换failover,或者down任意一台ASA都不会中断会话(感觉还是会卡一下,不过不会断)
ciscoasa/c1/act/pri(config)# show conn //在primaryASA的c1子墙中有会话信息 5 in use, 5 most used TCP outside 192.168.110.50:23 inside 192.168.20.50:50642, idle 0:09:20, bytes 116, flags UIO ciscoasa/c1/stby/sec# show conn //在secondaryASA的c1子墙也有 7 in use, 7 most used TCP outside 192.168.110.50:23 inside 192.168.20.50:33702, idle 0:00:09, bytes 248, flags UIO
当监控的接口出现问题是,s会抢a,但实际另一个子墙ASA没有问题,又会被抢回去,形成拉锯,现网出现概率不大,但要防止,可以禁止改接口的监控
做到这里还是有点成就感...
解决异步路由问题
其实很简单,把从ASA出去的口,和异步回来进入ASA的口放到一个asr-group中即可,当然路由和策略要可达
ciscoasa/stby/sec(config)# changeto context c2 //进入不同子墙,把异步出去回来的接口划入一个group中 ciscoasa/c2/act/sec(config)# int g3 ciscoasa/c2/act/sec(config-if)# asr-group 1
ASA完结了