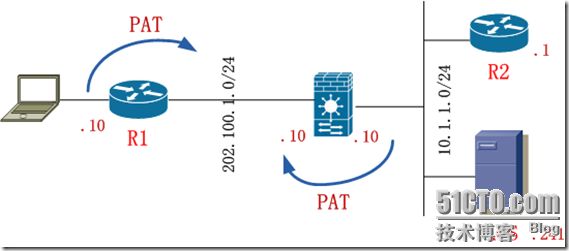
L2TP OVER IPSEC 使用radius做认证
- ASA上做nat global
- 在ASA上定义到3A,3A建立两个用户用于测试.可以用tacacs+,但是强烈用radius。因为tacacs+不支持ms-chap-v2
- 在ASA上定义一个L2TP pool ip local pool ippool 123.1.1.100-123.1.1.200
- 基于第一步和第四步,pc访问到内网用的是123的地址。而R1返回的包肯定是要做成不转换的,所以做个nonat
- ASA配置IPSEC,实现要外部接口激活crypto isakmp enable outside
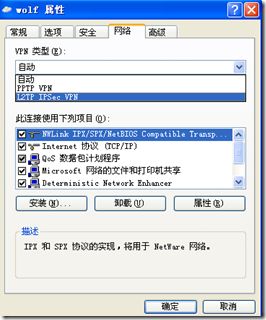
- 微软支持的ip策略
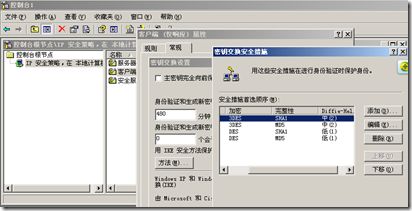
- ASA的配置(3des、sha1、group2)
- 注意GRE OVER IPSEC 是transport mode 。l2tp也是transport mode。配置模式
- 远程拨号***,使用的是动态map:crypto dynamic-map dy-map 10 set transform-set trans
- 动态map需要静态map来调用 crypto map cry-map 10 ipsec-isakmp dynamic dy-map
- 静态map调用在接口crypto map cry-map interface Outside(这个必须敲成大写0)
- ASA上默认没用nat-t(ASA上有三种方法启用nat-t,还有over udp 、over tcp)crypto isakmp nat-traversal 300
- Group-policy 必须有这个
- 默认远程类型的组
- 还有这个
- ppp相关的认证策略(可选)
- 正式修改
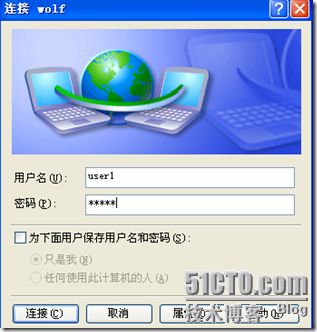
- 测试pc开始测试
- ping内网地址是通的,说明做的nat 免除是有效的
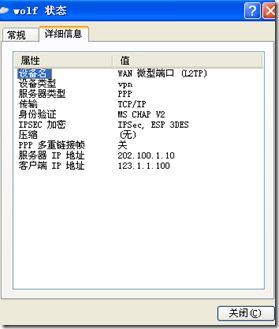
- ASA上查看
access-list nonat extended permit ip 10.1.1.0 255.255.255.0 123.1.1.0 255.255.255.0
nat (Inside) 0 access-list nonat
crypto isakmp policy 10
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto ipsec transform-set trans esp-3des esp-md5-hmac
crypto ipsec transform-set trans mode transport
group-policy DfltGrpPolicy internal
group-policy DfltGrpPolicy attributes
***-tunnel-protocol IPSec l2tp-ipsec web***(不仅要有l2tp,还要有ipsec.默认就好使)
tunnel-group DefaultRAGroup type remote-access
tunnel-group DefaultRAGroup general-attributes
no address-pool默认的地址池,要改成先前定义的地址池
authentication-server-group LOCAL 这个也很关键
default-group-policy DfltGrpPolicy 这个是调用的默认组策略
tunnel-group DefaultRAGroup ipsec-attributes
no pre-shared-key (ipsec相关的这个要设置成预共享密钥
tunnel-group DefaultRAGroup ppp-attributes
no authentication pap
authentication chap
authentication ms-chap-v1
no authentication ms-chap-v2
tunnel-group DefaultRAGroup general-attributes
address-pool ippool
authentication-server-group 3A
tunnel-group DefaultRAGroup ipsec-attributes
pre-shared-key cisco
tunnel-group DefaultRAGroup ppp-attributes
authentication ms-chap-v2(可选)
C:\>ping 10.1.1.1
Pinging 10.1.1.1 with 32 bytes of data:
Reply from 10.1.1.1: bytes=32 time=9ms TTL=255
Reply from 10.1.1.1: bytes=32 time=11ms TTL=255
Reply from 10.1.1.1: bytes=32 time=8ms TTL=255
Reply from 10.1.1.1: bytes=32 time=11ms TTL=255
Ping statistics for 10.1.1.1:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 8ms, Maximum = 11ms, Average = 9ms
ASA# sh crypto ipsec sa
interface: Outside
Crypto map tag: dy-map, seq num: 10, local addr: 202.100.1.10
local ident (addr/mask/prot/port): (202.100.1.10/255.255.255.255/17/1701)L2TP在里面,IPSEC在外边、L2TP使用的udp 1701
remote ident (addr/mask/prot/port): (202.100.1.1/255.255.255.255/17/0)
current_peer: 202.100.1.1, username: user1和pc连接的peer以及用户名
dynamic allocated peer ip: 123.1.1.100给***的地址
#pkts encaps: 33, #pkts encrypt: 33, #pkts digest: 33加密和解密都有
#pkts decaps: 64, #pkts decrypt: 64, #pkts verify: 64
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 33, #pkts comp failed: 0, #pkts decomp failed: 0
#post-frag successes: 0, #post-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 202.100.1.10/4500, remote crypto endpt.: 202.100.1.1/4500本地和远程使用nat-t也就是4500
path mtu 1500, ipsec overhead 66, media mtu 1500
current outbound spi: 0F85E953
inbound esp sas:
spi: 0x38E2E672 (954394226)SPI
transform: esp-3des esp-md5-hmac none
in use settings ={RA, Transport, NAT-T-Encaps, }使用的是远程类型、透明模式、NAT-T
slot: 0, conn_id: 4096, crypto-map: dy-map
sa timing: remaining key lifetime (kB/sec): (231927/3398)
IV size: 8 bytes
replay detection support: Y
outbound esp sas:
spi: 0x0F85E953 (260434259)SPI
transform: esp-3des esp-md5-hmac none
in use settings ={RA, Transport, NAT-T-Encaps, }使用的是远程类型、透明模式、NAT-T
slot: 0, conn_id: 4096, crypto-map: dy-map
sa timing: remaining key lifetime (kB/sec): (231931/3397)
IV size: 8 bytes
replay detection support: Y