如何让系统更安全
Linux权限体系, rwx permission denied
作业:
批量添加用户 exam1..exam3,并设置固定的密码1 (要求不能使用循环 for while)
批量添加用户 exam1..exam3,并设置8位随机密码 (要求不能使用循环 for while)
[root@manager ~]$ useradd exam1 ;echo 1 |passwd --stdin exam1
[root@manager ~]$ useradd exam2 ;echo 1 |passwd --stdin exam2
[root@manager ~]$ useradd exam3 ;echo 1 |passwd --stdin exam3
[root@manager /exam]$ ll
total 20
drwxr-xr-x. 3 root root 18 Nov 21 07:18 ceo
-rw-r--r--. 1 root root 465 Nov 21 10:23 fstab
-rw-r--r--. 1 root root 158 Nov 21 10:25 hosts
-rw-r--r--. 1 root root 352 Nov 19 10:51 reg.txt
-rw-r--r--. 1 root root 86 Nov 19 12:29 sed.txt
drwxr-xr-x. 6 root root 4096 Nov 21 10:23 sysconfig
[root@manager /exam]$ ll ceo/
total 0
drwxr-xr-x. 2 root root 24 Nov 21 07:19 yoyo
[root@manager /exam]$ ll -d /exam/
drwxr-xr-x. 4 root root 90 Nov 21 10:30 /exam/添加一个虚拟用户 mysql 指定用户的 uid gid 为12306
[root@manager /exam]$ useradd -u 12306 -s /sbin/nologin -M mysql
[root@manager /exam]$ id mysql
uid=12306(mysql) gid=12306(mysql) groups=12306(mysql)
[root@manager /exam]$ useradd yuyu
[root@manager /exam]$ id yuyu
uid=12307(yuyu) gid=12307(yuyu) groups=12307(yuyu)
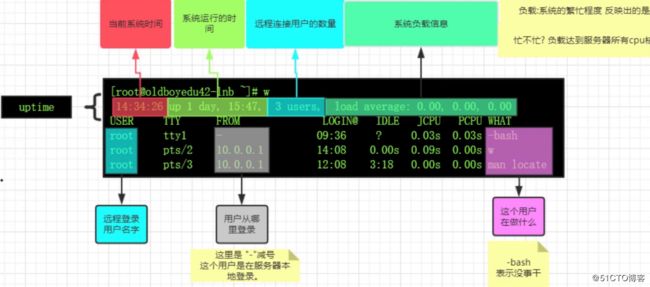
[root@manager /exam]$ w
13:56:04 up 16 min, 1 user, load average: 0.00, 0.01, 0.02
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
root pts/0 10.74.144.165 13:41 4.00s 0.05s 0.01s wdate -s 完整日期时间(YYYY-MM-DD hh:mm[:ss]):修改日期、时间
[root@manager /exam]$ date -s '2019-12-2 19:15:50'
Mon Dec 2 19:15:50 EST 2019
[root@manager /exam]$ date
Mon Dec 2 19:15:53 EST 2019[root@manager /exam]$ w
19:17:20 up 25 min, 1 user, load average: 0.00, 0.01, 0.02
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
root pts/0 10.74.144.165 13:41 0.00s 0.04s 0.00s w
[root@manager /exam]$ uptime
19:17:45 up 25 min, 1 user, load average: 0.00, 0.01, 0.02
[root@manager /exam]$ 自动对比
1、记录文件的指纹 police.md5
[root@manager /exam]$ md5sum exam.txt
924684b0d8ad52fd16ea0030122be50a exam.txt
[root@manager /exam]$ echo uouo >exam.txt
[root@manager /exam]$ md5sum exam.txt
7a9ac8bf65a46efebaf8b81f13124c25 exam.txt[root@manager /exam]$ md5sum exam.txt
924684b0d8ad52fd16ea0030122be50a exam.txt
[root@manager /exam]$ echo uouo >exam.txt
[root@manager /exam]$ md5sum exam.txt
7a9ac8bf65a46efebaf8b81f13124c25 exam.txt
[root@manager /exam]$ md5sum exam.txt >police.md5
[root@manager /exam]$ cat police.md5
7a9ac8bf65a46efebaf8b81f13124c25 exam.txt
[root@manager /exam]$ md5sum exam.txt >>police.md5
[root@manager /exam]$ cat police.md5
7a9ac8bf65a46efebaf8b81f13124c25 exam.txt
7a9ac8bf65a46efebaf8b81f13124c25 exam.txt2、根据库指纹进行对比
[root@manager /exam]$ md5sum --check police.md5
exam.txt: OK
exam.txt: OK
[root@manager /exam]$ echo 11111 >>exam.txt
[root@manager /exam]$ md5sum --check police.md5
exam.txt: FAILED
exam.txt: FAILED
md5sum: WARNING: 2 computed checksums did NOT match[root@manager /exam]$ find /exam/ -type f |xargs md5sum
15e2278b038244708bae6cf3468015ff /exam/reg.txt
cd36a10d8421743acd1e2c88ca83de46 /exam/sed.txt
d41d8cd98f00b204e9800998ecf8427e /exam/ceo/yoyo/youyou.txt
8fa3246990109d2ac5f1835bd2a04d2d /exam/sysconfig/ip6tables-config
13f6028cd7c8d8d6400ade9003d219c9 /exam/sysconfig/iptables-config
de08f397138caf0c99bda7e7322b2172 /exam/sysconfig/cbq/avpkt
760fb2971fb9b19e62564169e0bd94f9 /exam/sysconfig/cbq/cbq-0000.example
52b80b4ab7cafb63b53013edb769037c /exam/sysconfig/rdisc
62f39cb6e6ced2b374af6955bda3ed8f /exam/sysconfig/init[root@manager /exam]$ md5sum -c /root/police2.md5
/exam/reg.txt: OK
/exam/sed.txt: OK
/exam/ceo/yoyo/youyou.txt: OK
/exam/sysconfig/ip6tables-config: OK
/exam/sysconfig/iptables-config: OK
/exam/sysconfig/cbq/avpkt: OK
/exam/sysconfig/cbq/cbq-0000.example: OK
/exam/sysconfig/rdisc: OK
/exam/sysconfig/init: OKsodu 给普通用户临时成为 root 的权限,普通用户可以临时以root 身份运行某个命令
sudo -l 查看当前有哪些可以执行的命令
[yuyu@manager /root]$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for yuyu:
Sorry, user yuyu may not run sudo on manager.给yuyu 用户授权两个命令 ls touch
90 ##
91 ## Allow root to run any commands anywhere
92 root ALL=(ALL) ALL
93
94 yuyu ALL=(ALL) /bin/ls, /bin/touch[root@manager /]$ su yuyu
[yuyu@manager /]$
[yuyu@manager /root]$ sudo touch exam
[yuyu@manager /root]$ ls
ls: cannot open directory .: Permission denied
[yuyu@manager /root]$ sudo ls
anaconda-ks.cfg df.txt exam police2.md5
[yuyu@manager /root]$ sudo ll
sudo: ll: command not found
[yuyu@manager /root]$ pwd
/rootvisodu == vi /etc/sudoers
visodu 自带检查功能
[root@manager /]$ visudo
#>>> /etc/sudoers: syntax error near line 93 <<<
What now?
## Allow root to run any commands anywhere
root ALL=(ALL) ALL
给yuyu 用户授权/bin 下所有命令,排除某个命令或参数
yuyu ALL=(ALL) /bin/*
yuyu ALL=(ALL) /bin/* !/bin/mkdir
#yuyu ALL=(ALL) /bin/ls, /bin/touch
!## Allow root to run any commands anywhere
root ALL=(ALL) ALL
yuyu ALL=(ALL) /bin/*
yuyu ALL=(ALL) ALL
yuyu ALL=(ALL) /bin/*, !/bin/rm
yuyu ALL=(ALL) NOPASSWD: ALL
#yuyu ALL=(ALL) /bin/ls, /bin/touch应按需授权,需要什么命令给什么命令
用户 可以在所有服务器使用sudo=(你可以成为谁)
总结:
w 每一部分含义
如何让系统更安全
sudo 临时让用户获得 root权限